
Privilege escalation
Encyclopedia
Privilege escalation is the act of exploiting a bug
, design flaw or configuration oversight in an operating system
or software application to gain elevated access to resources
that are normally protected from an application or user
. The result is that an application with more privileges
than intended by the application developer
or system administrator
can perform unauthorized
actions.
mean what a user is permitted to do. Common privileges including viewing and editing files, or modifying system files.
Privilege escalation means a user receives privileges they are not entitled to. These privileges can be used to delete files, view private information, or install unwanted programs such as viruses. It usually occurs when a system has a bug
that allows security to be bypassed or, alternatively, has flawed design assumptions about how it will be used. Privilege escalation occurs in two forms:
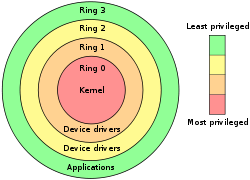 This type of privilege escalation occurs when the user or process is able to obtain a higher level of access than an administrator or system developer intended, possibly by performing kernel-level
This type of privilege escalation occurs when the user or process is able to obtain a higher level of access than an administrator or system developer intended, possibly by performing kernel-level
operations.
or jail
in UNIX-like
operating systems or bypassing digital rights management
(DRM). In the former case, it allows the user to see files outside of the filesystem that the administrator intends to make available to the application or user in question. In the context of DRM, this allows the user to run arbitrarily defined code on DRM-encumbered devices as well as break out of chroot-like restrictions. DRM-encumbered devices such as the Xbox
, PSP
, iPhone
, iPod touch
and iPad
have repeatedly been subject to jailbreaks, allowing the execution of arbitrary code, but have had those jailbreaks disabled by vendor updates.
The iPhone in particular has been a fertile battle ground
. The iOS hacking community however, responds to the newest vendor updates by creating new ways to enable third party apps almost immediately. It was only in the wake of the popularity of the iPhone that the term jailbreaking became well known in popular culture worldwide.. iOS jailbreaking tools include the option to install Cydia
, a third-party alternative to the App Store
, as a way to find and install system tweaks and binaries. To prevent iOS jailbreaking, Apple has made the device boot ROM execute checks for SHSH blobs
in order to disallow uploads of custom kernels and prevent software downgrades to earlier, jailbreakable firmwares. In an "untethered" jailbreak, the iBoot environment is changed to execute a boot ROM exploit and allow submission of a patched low level bootloader or hack the kernel to submit the jailbroken kernel after the SHSH check.
A similar method of jailbreaking exists for S60 Platform
smartphones, which involves installing softmod
-style patches which involves patching certain ROM files while loaded in RAM or edited firmware (similar to the M33 hacked firmware used for the PlayStation Portable
) to circumvent restrictions on unsigned code
. Nokia
has since issued updates to curb unauthorised jailbreaking, in a manner similar to Apple.
In the case of gaming consoles, jailbreaking is often used to execute homebrew games
. In 2011, Sony
, with assistance from law firm Kilpatrick Stockton, sued 21 year old George Hotz
and associates of the group fail0verflow for jailbreaking the Playstation 3
.
Charges filed included:
On April 11, 2011, it was revealed that Hotz and Sony had reached a settlement out of court. This included a permanent injunction against Hotz doing any more hacking work on any Sony products to prevent any future firmwares from being decrypted.
which normally would have been protected from an application or user
. The result is that the application performs actions with the same but different security context than intended by the application developer
or system administrator
; this is effectively a limited form of privilege escalation (specifically, the unauthorized assumption of the capability of impersonating other users).
This malicious activity may be possible due to common web application weaknesses or vulnerabilities.
Potential web application vulnerabilities or situations that may lead to this condition include:
Software bug
A software bug is the common term used to describe an error, flaw, mistake, failure, or fault in a computer program or system that produces an incorrect or unexpected result, or causes it to behave in unintended ways. Most bugs arise from mistakes and errors made by people in either a program's...
, design flaw or configuration oversight in an operating system
Operating system
An operating system is a set of programs that manage computer hardware resources and provide common services for application software. The operating system is the most important type of system software in a computer system...
or software application to gain elevated access to resources
Resource (computer science)
A resource, or system resource, is any physical or virtual component of limited availability within a computer system. Every device connected to a computer system is a resource. Every internal system component is a resource...
that are normally protected from an application or user
User (computing)
A user is an agent, either a human agent or software agent, who uses a computer or network service. A user often has a user account and is identified by a username , screen name , nickname , or handle, which is derived from the identical Citizen's Band radio term.Users are...
. The result is that an application with more privileges
Privilege (Computing)
In computing, privilege is defined as the delegation of authority over a computer system. A privilege is a permission to perform an action. Examples of various privileges include the ability to create a file in a directory, or to read or delete a file, access a device, or have read or write...
than intended by the application developer
Programmer
A programmer, computer programmer or coder is someone who writes computer software. The term computer programmer can refer to a specialist in one area of computer programming or to a generalist who writes code for many kinds of software. One who practices or professes a formal approach to...
or system administrator
System administrator
A system administrator, IT systems administrator, systems administrator, or sysadmin is a person employed to maintain and operate a computer system and/or network...
can perform unauthorized
Authorization
Authorization is the function of specifying access rights to resources, which is related to information security and computer security in general and to access control in particular. More formally, "to authorize" is to define access policy...
actions.
Background
Most computer systems are designed for use with multiple users. PrivilegesPrivilege (Computing)
In computing, privilege is defined as the delegation of authority over a computer system. A privilege is a permission to perform an action. Examples of various privileges include the ability to create a file in a directory, or to read or delete a file, access a device, or have read or write...
mean what a user is permitted to do. Common privileges including viewing and editing files, or modifying system files.
Privilege escalation means a user receives privileges they are not entitled to. These privileges can be used to delete files, view private information, or install unwanted programs such as viruses. It usually occurs when a system has a bug
Software bug
A software bug is the common term used to describe an error, flaw, mistake, failure, or fault in a computer program or system that produces an incorrect or unexpected result, or causes it to behave in unintended ways. Most bugs arise from mistakes and errors made by people in either a program's...
that allows security to be bypassed or, alternatively, has flawed design assumptions about how it will be used. Privilege escalation occurs in two forms:
- Vertical privilege escalation, also known as privilege elevation, where a lower privilege user or application accesses functions or content reserved for higher privilege users or applications (e.g. Internet Banking users can access site administrative functions or the password for smartphone can be bypassed.)
- Horizontal privilege escalation, where a normal user accesses functions or content reserved for other normal users (e.g. Internet Banking User A accesses the Internet bank account of User B)
Vertical privilege escalation

Ring (computer security)
In computer science, hierarchical protection domains, often called protection rings, are a mechanism to protect data and functionality from faults and malicious behaviour . This approach is diametrically opposite to that of capability-based security.Computer operating systems provide different...
operations.
Examples of vertical privilege escalation
In some cases a high-privilege application assumes that it will only be provided with input that matches its interface specification, and doesn't validate the input. An attacker may then be able to exploit this assumption so that unauthorized code is run with the application's privileges:- Some Windows serviceWindows ServiceOn Microsoft Windows operating systems, a Windows service is a long-running executable that performs specific functions and which is designed not to require user intervention. Windows services can be configured to start when the operating system is booted and run in the background as long as...
s are configured to run under the Local SystemSuperuserOn many computer operating systems, the superuser is a special user account used for system administration. Depending on the operating system, the actual name of this account might be: root, administrator or supervisor....
user account. A vulnerability such as a buffer overflowBuffer overflowIn computer security and programming, a buffer overflow, or buffer overrun, is an anomaly where a program, while writing data to a buffer, overruns the buffer's boundary and overwrites adjacent memory. This is a special case of violation of memory safety....
may be used to execute arbitrary code with privilege elevated to Local SystemSuperuserOn many computer operating systems, the superuser is a special user account used for system administration. Depending on the operating system, the actual name of this account might be: root, administrator or supervisor....
. Alternatively, a system service that is impersonating a lesser user can elevate that user's privileges if errors are not handled correctly while the user is being impersonated (e.g. if the user has introduced a malicious error handlerException handlingException handling is a programming language construct or computer hardware mechanism designed to handle the occurrence of exceptions, special conditions that change the normal flow of program execution....
) - Under some legacy versions of the Microsoft WindowsMicrosoft WindowsMicrosoft Windows is a series of operating systems produced by Microsoft.Microsoft introduced an operating environment named Windows on November 20, 1985 as an add-on to MS-DOS in response to the growing interest in graphical user interfaces . Microsoft Windows came to dominate the world's personal...
operating system, the All Users screensaverScreensaverA screensaver is a type of computer program initially designed to prevent phosphor burn-in on CRT and plasma computer monitors by blanking the screen or filling it with moving images or patterns when the computer is not in use...
runs under the Local SystemSuperuserOn many computer operating systems, the superuser is a special user account used for system administration. Depending on the operating system, the actual name of this account might be: root, administrator or supervisor....
account - any account that can replace the current screensaver binaryExecutableIn computing, an executable file causes a computer "to perform indicated tasks according to encoded instructions," as opposed to a data file that must be parsed by a program to be meaningful. These instructions are traditionally machine code instructions for a physical CPU...
in the file system or RegistryWindows registryThe Windows Registry is a hierarchical database that stores configuration settings and options on Microsoft Windows operating systems. It contains settings for low-level operating system components as well as the applications running on the platform: the kernel, device drivers, services, SAM, user...
can therefore elevate privileges. - In certain versions of the Linux kernelLinux kernelThe Linux kernel is an operating system kernel used by the Linux family of Unix-like operating systems. It is one of the most prominent examples of free and open source software....
it was possible to write a program that would set its current directory to/etc/cron.d, request that a core dumpCore dumpIn computing, a core dump consists of the recorded state of the working memory of a computer program at a specific time, generally when the program has terminated abnormally...
be performed in case it crashes and then have itself killedKill (Unix)In computing, kill is a command that is used in several popular operating systems to send signals to running processes, for example to request the termination of this process.-Unix and Unix-like:...
by another process. The core dump file would have been placed at the program's current directory, that is,/etc/cron.d, andcronwould have treated it as a text file instructing it to run programs on schedule. Because the contents of the file would be under attacker’s control, the attacker would be able to execute any program with rootCronCron is a time-based job scheduler in Unix-like computer operating systems. Cron enables users to schedule jobs to run periodically at certain times or dates...SuperuserOn many computer operating systems, the superuser is a special user account used for system administration. Depending on the operating system, the actual name of this account might be: root, administrator or supervisor....
privileges. - Cross Zone Scripting is a type of privilege escalation attack in which a website subverts the security model of web browsers so that it can run malicious code on client computers.
- There are also situations where an application can use other high privilege services and has incorrect assumptions about how a client could manipulate its use of these services. An application that can execute Command line or shellUnix shellA Unix shell is a command-line interpreter or shell that provides a traditional user interface for the Unix operating system and for Unix-like systems...
commands could have a Shell InjectionCode injectionCode injection is the exploitation of a computer bug that is caused by processing invalid data. Code injection can be used by an attacker to introduce code into a computer program to change the course of execution. The results of a code injection attack can be disastrous...
vulnerability if it uses unvalidated input as part of an executed command. An attacker would then be able to run system commands using the application's privileges. - Texas InstrumentsTexas InstrumentsTexas Instruments Inc. , widely known as TI, is an American company based in Dallas, Texas, United States, which develops and commercializes semiconductor and computer technology...
calculators (particularly the TI-85TI-85The TI-85 was a graphing calculator made by Texas Instruments based around the Zilog Z80 microprocessor. Designed in 1992 as TI's second graphing calculator , it has since been replaced by the TI-86, which has also been discontinued....
and TI-82TI-82The TI-82 is a graphing calculator made by Texas Instruments. The TI-82 was designed in 1993 as a stripped down, more user friendly version of the TI-85, and as a replacement for the TI-81. It was the direct predecessor of the TI-83. It shares with the TI-85 a 6 MHz Zilog Z80 microprocessor...
) were originally designed to use only interpreted programs written in dialects of TI-BASICTI-BASICTI-BASIC is the unofficial name of a BASIC-like language built into Texas Instruments 's graphing calculators, including the TI-83 series, TI-84 Plus series, TI-89 series, TI-92 series , TI-73, and TI-Nspire...
; however, after users discovered bugs that could be exploited to allow native Z-80 code to run on the calculator hardware, TI released programming data to support third-party development. (This did not carry on to the ARMARM architectureARM is a 32-bit reduced instruction set computer instruction set architecture developed by ARM Holdings. It was named the Advanced RISC Machine, and before that, the Acorn RISC Machine. The ARM architecture is the most widely used 32-bit ISA in numbers produced...
-based TI-Nspire, for which jailbreaks have been found but are still actively fought against by Texas Instruments.) - Some versions of the iPhoneIPhoneThe iPhone is a line of Internet and multimedia-enabled smartphones marketed by Apple Inc. The first iPhone was unveiled by Steve Jobs, then CEO of Apple, on January 9, 2007, and released on June 29, 2007...
allow an unauthorised user to access the phone while it is locked.
Jailbreaking
A jailbreak is the act or tool used to perform the act of breaking out of a chrootChroot
A chroot on Unix operating systems is an operation that changes the apparent root directory for the current running process and its children. A program that is run in such a modified environment cannot name files outside the designated directory tree. The term "chroot" may refer to the chroot...
or jail
FreeBSD Jail
The FreeBSD jail mechanism is an implementation of operating system-level virtualization that allows administrators to partition a FreeBSD-based computer system into several independent mini-systems called jails....
in UNIX-like
Unix-like
A Unix-like operating system is one that behaves in a manner similar to a Unix system, while not necessarily conforming to or being certified to any version of the Single UNIX Specification....
operating systems or bypassing digital rights management
Digital rights management
Digital rights management is a class of access control technologies that are used by hardware manufacturers, publishers, copyright holders and individuals with the intent to limit the use of digital content and devices after sale. DRM is any technology that inhibits uses of digital content that...
(DRM). In the former case, it allows the user to see files outside of the filesystem that the administrator intends to make available to the application or user in question. In the context of DRM, this allows the user to run arbitrarily defined code on DRM-encumbered devices as well as break out of chroot-like restrictions. DRM-encumbered devices such as the Xbox
Xbox
The Xbox is a sixth-generation video game console manufactured by Microsoft. It was released on November 15, 2001 in North America, February 22, 2002 in Japan, and March 14, 2002 in Australia and Europe and is the predecessor to the Xbox 360. It was Microsoft's first foray into the gaming console...
, PSP
PlayStation Portable
The is a handheld game console manufactured and marketed by Sony Corporation Development of the console was announced during E3 2003, and it was unveiled on , 2004, at a Sony press conference before E3 2004...
, iPhone
IPhone
The iPhone is a line of Internet and multimedia-enabled smartphones marketed by Apple Inc. The first iPhone was unveiled by Steve Jobs, then CEO of Apple, on January 9, 2007, and released on June 29, 2007...
, iPod touch
IPod touch
The iPod Touch is a portable media player, personal digital assistant, handheld game console, and Wi-Fi mobile device designed and marketed by Apple Inc. The iPod Touch adds the multi-touch graphical user interface to the iPod line...
and iPad
IPad
The iPad is a line of tablet computers designed, developed and marketed by Apple Inc., primarily as a platform for audio-visual media including books, periodicals, movies, music, games, and web content. The iPad was introduced on January 27, 2010 by Apple's then-CEO Steve Jobs. Its size and...
have repeatedly been subject to jailbreaks, allowing the execution of arbitrary code, but have had those jailbreaks disabled by vendor updates.
The iPhone in particular has been a fertile battle ground
History of iOS jailbreaking
iOS jailbreaking, or simply jailbreaking, is the process of removing the limitations imposed by Apple on devices running the iOS operating system through use of custom kernels. Such devices include the iPhone, iPod Touch, iPad, and 2nd Gen Apple TV...
. The iOS hacking community however, responds to the newest vendor updates by creating new ways to enable third party apps almost immediately. It was only in the wake of the popularity of the iPhone that the term jailbreaking became well known in popular culture worldwide.. iOS jailbreaking tools include the option to install Cydia
Cydia
Cydia is a large genus of tortrix moths, belonging to the tribe Grapholitini of subfamily Olethreutinae. Its distinctness from and delimitation versus the tribe's type genus Grapholita requires further study....
, a third-party alternative to the App Store
App Store
The App Store is a digital application distribution platform for iOS developed and maintained by Apple Inc.The service allows users to browse and download applications from the iTunes Store that were developed with the iOS SDK or Mac SDK and published through Apple Inc.. Depending on the...
, as a way to find and install system tweaks and binaries. To prevent iOS jailbreaking, Apple has made the device boot ROM execute checks for SHSH blobs
SHSH blob
SHSH blobs is a Hash signature system made by Apple inc. to prevent software downgrades on iPhones, iPads and iPod touches meant for Jailbreaking. An SHSH is created by an SHSH formula with 3 or 4 TSS keys- The device , the firmware signed SHSH blobs is a Hash signature system (Signature HaSH...
in order to disallow uploads of custom kernels and prevent software downgrades to earlier, jailbreakable firmwares. In an "untethered" jailbreak, the iBoot environment is changed to execute a boot ROM exploit and allow submission of a patched low level bootloader or hack the kernel to submit the jailbroken kernel after the SHSH check.
A similar method of jailbreaking exists for S60 Platform
S60 platform
The S60 Platform is a software platform for mobile phones that runs on Symbian OS. It was created by Nokia, who made the platform open source and contributed it to the Symbian Foundation. S60 has been used by mobile device manufacturers including Siemens mobile, Lenovo, LG Electronics, Panasonic...
smartphones, which involves installing softmod
Softmod
A softmod is a method of using software to modify the intended behaviour of hardware, such as video cards, sound cards, or game consoles in a way that can overcome restrictions of the firmware, or install custom firmware.-Video card softmods:...
-style patches which involves patching certain ROM files while loaded in RAM or edited firmware (similar to the M33 hacked firmware used for the PlayStation Portable
PlayStation Portable
The is a handheld game console manufactured and marketed by Sony Corporation Development of the console was announced during E3 2003, and it was unveiled on , 2004, at a Sony press conference before E3 2004...
) to circumvent restrictions on unsigned code
Unsigned code
Unsigned code refers to an application which has not been signed with the secret key required for it to load on a console.In the video game console business, most console games have to be signed with a secret key designed by the console maker or the game will not load on the console...
. Nokia
Nokia
Nokia Corporation is a Finnish multinational communications corporation that is headquartered in Keilaniemi, Espoo, a city neighbouring Finland's capital Helsinki...
has since issued updates to curb unauthorised jailbreaking, in a manner similar to Apple.
In the case of gaming consoles, jailbreaking is often used to execute homebrew games
Homebrew (video games)
Homebrew is a term frequently applied to video games or other software produced by consumers to target proprietary hardware platforms not typically user-programmable or that use proprietary storage methods...
. In 2011, Sony
Sony
, commonly referred to as Sony, is a Japanese multinational conglomerate corporation headquartered in Minato, Tokyo, Japan and the world's fifth largest media conglomerate measured by revenues....
, with assistance from law firm Kilpatrick Stockton, sued 21 year old George Hotz
Sony Computer Entertainment America v. George Hotz
SCEA v. Hotz is a lawsuit in the United States by Sony Computer Entertainment of America against George Hotz and associates of the group fail0verflow for jailbreaking and reverse engineering the Playstation 3.-Timeline:...
and associates of the group fail0verflow for jailbreaking the Playstation 3
PlayStation 3
The is the third home video game console produced by Sony Computer Entertainment and the successor to the PlayStation 2 as part of the PlayStation series. The PlayStation 3 competes with Microsoft's Xbox 360 and Nintendo's Wii as part of the seventh generation of video game consoles...
.
Charges filed included:
- Violating the Digital Millenium Copyright Act
- Violating the Computer Fraud and Abuse ActComputer Fraud and Abuse ActThe Computer Fraud and Abuse Act is a law passed by the United States Congress in 1986, intended to reduce cracking of computer systems and to address federal computer-related offenses...
- Contributory copyright infringement
- Violating California Comprehensive Computer Data Access and Fraud ActCalifornia Comprehensive Computer Data Access and Fraud ActThe California Comprehensive Computer Data Access and Fraud Act is in §502 of the California Penal Code.According to the State Administrative Manual of California, the purposes is as follows:...
(§ 502) - Breach of ContractBreach of contractBreach of contract is a legal cause of action in which a binding agreement or bargained-for exchange is not honored by one or more of the parties to the contract by non-performance or interference with the other party's performance....
(related to the PlayStation Network User AgreementTerms of serviceTerms of service are rules which one must agree to abide by in order to use a service. Unless in violation of consumer protection laws, such terms are usually legally binding...
) - Tortious interferenceTortious interferenceTortious interference, also known as intentional interference with contractual relations, in the common law of tort, occurs when a person intentionally damages the plaintiff's contractual or other business relationships...
- MisappropriationMisappropriationIn law, misappropriation is the intentional, illegal use of the property or funds of another person for one's own use or other unauthorized purpose, particularly by a public official, a trustee of a trust, an executor or administrator of a dead person's estate or by any person with a responsibility...
- Tresspass
On April 11, 2011, it was revealed that Hotz and Sony had reached a settlement out of court. This included a permanent injunction against Hotz doing any more hacking work on any Sony products to prevent any future firmwares from being decrypted.
Mitigation strategies
Operating systems and users can use the following strategies to reduce the risk of privilege escalation:- Data Execution PreventionData Execution PreventionData Execution Prevention is a security feature included in modern operating systems.It is known to be available in Linux, Mac OS X, and Microsoft Windows operating systems and is intended to prevent an application or service from executing code from a non-executable memory region. This helps...
- Address space layout randomizationAddress space layout randomizationAddress space layout randomization is a computer security method which involves randomly arranging the positions of key data areas, usually including the base of the executable and position of libraries, heap, and stack, in a process's address space.- Benefits :Address space randomization hinders...
(to make it harder for buffer overrunsBuffer overflowIn computer security and programming, a buffer overflow, or buffer overrun, is an anomaly where a program, while writing data to a buffer, overruns the buffer's boundary and overwrites adjacent memory. This is a special case of violation of memory safety....
to execute privileged instructions at known addresses in memory) - Running applications with least privilegePrinciple of least privilegeIn information security, computer science, and other fields, the principle of least privilege, also known as the principle of minimal privilege or just least privilege, requires that in a particular abstraction layer of a computing environment, every module must be able to access only the...
(for example by running Internet ExplorerInternet ExplorerWindows Internet Explorer is a series of graphical web browsers developed by Microsoft and included as part of the Microsoft Windows line of operating systems, starting in 1995. It was first released as part of the add-on package Plus! for Windows 95 that year...
with the Administrator SIDSecurity IdentifierIn the context of the Microsoft Windows NT line of operating systems, a Security Identifier is a unique name which is assigned by a Windows Domain controller during the log on process that is used to identify a subject, such as a user or a group of users in a network of NT/2000...
disabled in the process tokenSession (computer science)In computer science, in particular networking, a session is a semi-permanent interactive information interchange, also known as a dialogue, a conversation or a meeting, between two or more communicating devices, or between a computer and user . A session is set up or established at a certain point...
) in order to reduce the ability of buffer overrun exploitsExploit (computer security)An exploit is a piece of software, a chunk of data, or sequence of commands that takes advantage of a bug, glitch or vulnerability in order to cause unintended or unanticipated behavior to occur on computer software, hardware, or something electronic...
to abuse the privileges of an elevated user. - Requiring kernel mode code to be digitally signed.
- Use of up-to-date antivirus softwareAntivirus softwareAntivirus or anti-virus software is used to prevent, detect, and remove malware, including but not limited to computer viruses, computer worm, trojan horses, spyware and adware...
- PatchingPatch (computing)A patch is a piece of software designed to fix problems with, or update a computer program or its supporting data. This includes fixing security vulnerabilities and other bugs, and improving the usability or performance...
- Use of compilerCompilerA compiler is a computer program that transforms source code written in a programming language into another computer language...
s that trap buffer overruns - Encryption of software and/or firmwareFirmwareIn electronic systems and computing, firmware is a term often used to denote the fixed, usually rather small, programs and/or data structures that internally control various electronic devices...
components.
Horizontal privilege escalation
Horizontal privilege escalation occurs when an application allows the attacker to gain access to resourcesResource (computer science)
A resource, or system resource, is any physical or virtual component of limited availability within a computer system. Every device connected to a computer system is a resource. Every internal system component is a resource...
which normally would have been protected from an application or user
User (computing)
A user is an agent, either a human agent or software agent, who uses a computer or network service. A user often has a user account and is identified by a username , screen name , nickname , or handle, which is derived from the identical Citizen's Band radio term.Users are...
. The result is that the application performs actions with the same but different security context than intended by the application developer
Programmer
A programmer, computer programmer or coder is someone who writes computer software. The term computer programmer can refer to a specialist in one area of computer programming or to a generalist who writes code for many kinds of software. One who practices or professes a formal approach to...
or system administrator
System administrator
A system administrator, IT systems administrator, systems administrator, or sysadmin is a person employed to maintain and operate a computer system and/or network...
; this is effectively a limited form of privilege escalation (specifically, the unauthorized assumption of the capability of impersonating other users).
Examples of horizontal privilege escalation
This problem often occurs in web applications. Consider the following example:- User A has access to his/her bank account in an Internet Banking application.
- User B has access to his/her bank account in the same Internet Banking application.
- The vulnerability occurs when User A is able to access User B's bank account by performing some sort of malicious activity.
This malicious activity may be possible due to common web application weaknesses or vulnerabilities.
Potential web application vulnerabilities or situations that may lead to this condition include:
- Predictable session IDSession IDIn computer science, a session identifier, session ID or session token is a piece of data that is used in network communications to identify a session, a series of related message exchanges. Session identifiers become necessary in cases where the communications infrastructure uses a stateless...
's in the user's HTTP cookieHTTP cookieA cookie, also known as an HTTP cookie, web cookie, or browser cookie, is used for an origin website to send state information to a user's browser and for the browser to return the state information to the origin site... - Session fixationSession fixationIn computer network security, session fixation attacks attempt to exploit the vulnerability of a system which allows one person to fixate another person's session identifier...
- Cross-site ScriptingCross-site scriptingCross-site scripting is a type of computer security vulnerability typically found in Web applications that enables attackers to inject client-side script into Web pages viewed by other users. A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same...
- Easily guessable passwordPasswordA password is a secret word or string of characters that is used for authentication, to prove identity or gain access to a resource . The password should be kept secret from those not allowed access....
s - Theft or hijacking of session cookiesHTTP cookieA cookie, also known as an HTTP cookie, web cookie, or browser cookie, is used for an origin website to send state information to a user's browser and for the browser to return the state information to the origin site...
- Keystroke loggingKeystroke loggingKeystroke logging is the action of tracking the keys struck on a keyboard, typically in a covert manner so that the person using the keyboard is unaware that their actions are being monitored...
See also
- Hacking of consumer electronicsHacking of consumer electronicsHacking has expanded from applying strictly to computers to consumer electronics in general. Hacking provides users with the ability to customize and modify their devices...
- Principle of least privilegePrinciple of least privilegeIn information security, computer science, and other fields, the principle of least privilege, also known as the principle of minimal privilege or just least privilege, requires that in a particular abstraction layer of a computing environment, every module must be able to access only the...
- Privilege separationPrivilege separationIn computer programming and computer security, privilege separation is a technique in which a program is divided into parts which are limited to the specific privileges they require in order to perform a specific task...
- Privilege revocationPrivilege revocationPrivilege revocation is the act of an entity giving up some, or all of, the privileges they possess, or some authority taking those rights away.- Information theory :...
- Defensive programmingDefensive programmingDefensive programming is a form of defensive design intended to ensure the continuing function of a piece of software in spite of unforeseeable usage of said software. The idea can be viewed as reducing or eliminating the prospect of Murphy's Law having effect...
- World Wide Web security
- GetAdminGetAdminA computer security utility going by the name GetAdmin was released in early July, 1997. The utility exploited a flaw in the Microsoft Windows NT 4 operating system in order to escalate privileges of an arbitrary specified account. GetAdmin will no longer work on newer versions of Windows operation...
- Illegal numberIllegal numberAn illegal number is a number that represents information which is illegal to possess, utter or propagate. Any information that can be represented in binary format is representable as a number, and therefore if the information itself is illegal in some way, the pure number itself may be...
- Rooting (Android OS)Rooting (Android OS)Rooting is a process that allows users of mobile phones and other devices running the Android operating system to attain privileged control within Android's Linux subsystem with the goal of overcoming limitations that carriers and manufacturers put on some devices...

