ID-based cryptography
Encyclopedia
ID-based encryption is an important primitive of ID-based cryptography
. As such it is a type of public-key encryption in which the public key of a user is some unique information about the identity of the user (e.g. a user's email address). This can use the text-value of the name or domain name as a key or the physical IP address it translates to.
The first implementation of an email-address based PKI was developed by Adi Shamir
in 1984, which allowed users to verify digital signature
s using only public information such as the user's identifier.
ID-based encryption was proposed by Adi Shamir
in 1984. He was however only able to give an instantiation of identity-based signatures
. Identity-based encryption remained an open problem for many years. One example of the research leading up to identity-based encryption is provided in Maurer.
The Boneh
/Franklin's pairing-based encryption scheme
and Cocks's encryption scheme
based on quadratic residues both solved the IBE problem in 2001.
As a result, parties may encrypt messages (or verify signatures) with no prior distribution of keys between individual participants. This is extremely useful in cases where pre-distribution of authenticated keys is inconvenient or infeasible due to technical restraints. However, to decrypt or sign messages, the authorized user must obtain the appropriate private key from the PKG. A caveat of this approach is that the PKG must be highly trusted, as it is capable of generating any user's private key and may therefore decrypt (or sign) messages without authorization. Because any user's private key can be generated through the use of the third party's secret, this system has inherent key escrow
. A number of variant systems have been proposed which remove the escrow including certificate-based encryption
, secure key issuing cryptography
and certificateless cryptography
.
The steps involved are depicted in this diagram: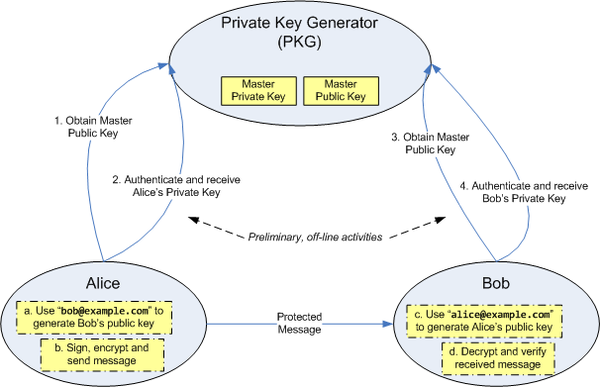
and Matthew K. Franklin defined a set of four algorithms that form a complete IBE system:

or Tate pairings. The first of these schemes was developed by Dan Boneh
and Matthew K. Franklin (2001), and performs probabilistic encryption
of arbitrary ciphertexts using an Elgamal
-like approach. Though the Boneh-Franklin scheme is provably secure
, the security proof rests on relatively new assumptions about the hardness of problems in certain elliptic curve groups.
Another approach to identity-based encryption was proposed by Clifford Cocks
in 2001. The Cocks IBE scheme
is based on well-studied assumptions (the quadratic residuosity assumption
) but encrypts messages one bit at a time with a high degree of ciphertext expansion
. Thus it is highly inefficient and impractical for sending all but the shortest messages, such as a session key for use with a symmetric cipher.
Moreover, as public keys are derived from identifiers, IBE eliminates the need for a public key distribution infrastructure. The authenticity
of the public keys is guaranteed implicitly as long as the transport of the private keys to the corresponding user is kept secure (Authenticity, Integrity
, Confidentiality
).
Apart from these aspects, IBE offers interesting features emanating from the possibility to encode additional information into the identifier. For instance, a sender might specify an expiration date for a message. He appends this timestamp to the actual recipient's identity (possibly using some binary format like X.509). When the receiver contacts the PKG to retrieve the private key for this public key, the PKG can evaluate the identifier and decline the extraction if the expiration date has passed. Generally, embedding data in the ID corresponds to opening an additional channel between sender and PKG with authenticity guaranteed through the dependency of the private key on the identifier.
ID-based cryptography
ID-based encryption is an important primitive of ID-based cryptography. As such it is a type of public-key encryption in which the public key of a user is some unique information about the identity of the user...
. As such it is a type of public-key encryption in which the public key of a user is some unique information about the identity of the user (e.g. a user's email address). This can use the text-value of the name or domain name as a key or the physical IP address it translates to.
The first implementation of an email-address based PKI was developed by Adi Shamir
Adi Shamir
Adi Shamir is an Israeli cryptographer. He is a co-inventor of the RSA algorithm , a co-inventor of the Feige–Fiat–Shamir identification scheme , one of the inventors of differential cryptanalysis and has made numerous contributions to the fields of cryptography and computer...
in 1984, which allowed users to verify digital signature
Digital signature
A digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender, and that it was not altered in transit...
s using only public information such as the user's identifier.
ID-based encryption was proposed by Adi Shamir
Adi Shamir
Adi Shamir is an Israeli cryptographer. He is a co-inventor of the RSA algorithm , a co-inventor of the Feige–Fiat–Shamir identification scheme , one of the inventors of differential cryptanalysis and has made numerous contributions to the fields of cryptography and computer...
in 1984. He was however only able to give an instantiation of identity-based signatures
ID-based cryptography
ID-based encryption is an important primitive of ID-based cryptography. As such it is a type of public-key encryption in which the public key of a user is some unique information about the identity of the user...
. Identity-based encryption remained an open problem for many years. One example of the research leading up to identity-based encryption is provided in Maurer.
The Boneh
Dan Boneh
Dan Boneh is a Professor of Computer Science and Electrical Engineering atStanford University. He is a well-known researcher in the areas of applied cryptographyand computer security.-Education:...
/Franklin's pairing-based encryption scheme
Boneh/Franklin scheme
The Boneh/Franklin scheme is an Identity based encryption system proposed by Dan Boneh and Matthew K. Franklin in 2001 . This article refers to the protocol version called BasicIdent...
and Cocks's encryption scheme
Cocks IBE scheme
Cocks IBE scheme is an Identity based encryption system proposed by Clifford Cocks in 2001 . The security of the scheme is based on the hardness of the quadratic residuosity problem.-Setup:The PKG chooses:...
based on quadratic residues both solved the IBE problem in 2001.
Usage
Identity-based systems allow any party to generate a public key from a known identity value such as an ASCII string. A trusted third party, called the Private Key Generator (PKG), generates the corresponding private keys. To operate, the PKG first publishes a master public key, and retains the corresponding master private key (referred to as master key). Given the master public key, any party can compute a public key corresponding to the identity ID by combining the master public key with the identity value. To obtain a corresponding private key, the party authorized to use the identity ID contacts the PKG, which uses the master private key to generate the private key for identity ID.As a result, parties may encrypt messages (or verify signatures) with no prior distribution of keys between individual participants. This is extremely useful in cases where pre-distribution of authenticated keys is inconvenient or infeasible due to technical restraints. However, to decrypt or sign messages, the authorized user must obtain the appropriate private key from the PKG. A caveat of this approach is that the PKG must be highly trusted, as it is capable of generating any user's private key and may therefore decrypt (or sign) messages without authorization. Because any user's private key can be generated through the use of the third party's secret, this system has inherent key escrow
Key escrow
Key escrow is an arrangement in which the keys needed to decrypt encrypted data are held in escrow so that, under certain circumstances, an authorized third party may gain access to those keys...
. A number of variant systems have been proposed which remove the escrow including certificate-based encryption
Certificate-based encryption
Certificate-based encryption is a system in which a certificate authority uses ID-based cryptography to produce a certificate. This system gives the users both implicit and explicit certification, the certificate can be used as a conventional certificate , but also implicitly for the purpose of...
, secure key issuing cryptography
Secure key issuing cryptography
Secure key issuing is variant of ID-based cryptography that reduces the level of trust that needs to be placed in a trusted third party by spreading the trust across multiple third parties. In addition to the normally transmitted information the user supplies what is known as "blinding"...
and certificateless cryptography
Certificateless cryptography
Certificateless cryptography is a variant of ID-based cryptography intended to prevent the key escrow problem. Ordinarily, keys are generated by a certificate authority or a key generation center who is given complete power and is implicitly trusted...
.
The steps involved are depicted in this diagram:

Protocol framework
Dan BonehDan Boneh
Dan Boneh is a Professor of Computer Science and Electrical Engineering atStanford University. He is a well-known researcher in the areas of applied cryptographyand computer security.-Education:...
and Matthew K. Franklin defined a set of four algorithms that form a complete IBE system:
- Setup: This algorithm is run by the PKG one time for creating the whole IBE environment. The master key is kept secret and used to derive users' private keys, while the system parameters are made public. It accepts a security parameterSecurity parameterIn cryptography, the security parameter is a variable that measures the input size of the problem. Both the resource requirements of the cryptographic algorithm or protocol as well as the adversary's probability of breaking security are expressed in terms of the security parameter.The security...
 (i.e. binary length of key material) and outputs:
(i.e. binary length of key material) and outputs:
- A set
 of system parameters, including the message space and ciphertext space
of system parameters, including the message space and ciphertext space  and
and  ,
, - a master key
 .
.
- Extract: This algorithm is run by the PKG when a user requests his private key. Note that the verification of the authenticityAuthenticationAuthentication is the act of confirming the truth of an attribute of a datum or entity...
of the requestor and the secure transport of are problems with which IBE protocols do not try to deal. It takes as input
are problems with which IBE protocols do not try to deal. It takes as input  ,
,  and an identifier
and an identifier  and returns the private key
and returns the private key  for user
for user  .
.
- Encrypt: Takes
 , a message
, a message  and
and  and outputs the encryption
and outputs the encryption  .
.
- Decrypt: Accepts
 ,
,  and
and  and returns
and returns  .
.
Correctness constraint
In order for the whole system to work, one has to postulate that:
Encryption schemes
The most efficient identity-based encryption schemes are currently based on bilinear pairings on elliptic curves, such as the WeilWeil pairing
In mathematics, the Weil pairing is a construction of roots of unity by means of functions on an elliptic curve E, in such a way as to constitute a pairing on the torsion subgroup of E...
or Tate pairings. The first of these schemes was developed by Dan Boneh
Dan Boneh
Dan Boneh is a Professor of Computer Science and Electrical Engineering atStanford University. He is a well-known researcher in the areas of applied cryptographyand computer security.-Education:...
and Matthew K. Franklin (2001), and performs probabilistic encryption
Probabilistic encryption
Probabilistic encryption is the use of randomness in an encryption algorithm, so that when encrypting the same message several times it will, in general, yield different ciphertexts...
of arbitrary ciphertexts using an Elgamal
ElGamal encryption
In cryptography, the ElGamal encryption system is an asymmetric key encryption algorithm for public-key cryptography which is based on the Diffie–Hellman key exchange. It was described by Taher Elgamal in 1984. ElGamal encryption is used in the free GNU Privacy Guard software, recent versions of...
-like approach. Though the Boneh-Franklin scheme is provably secure
Provable security
In cryptography, a system has provable security if its security requirements can be stated formally in an adversarial model, as opposed to heuristically, with clear assumptions that the adversary has access to the system as well as enough computational resources...
, the security proof rests on relatively new assumptions about the hardness of problems in certain elliptic curve groups.
Another approach to identity-based encryption was proposed by Clifford Cocks
Clifford Cocks
Clifford Christopher Cocks, CB, is a British mathematician and cryptographer at GCHQ.He invented the widely-used encryption algorithm now commonly known as RSA, about three years before it was independently developed by Rivest, Shamir, and Adleman at MIT...
in 2001. The Cocks IBE scheme
Cocks IBE scheme
Cocks IBE scheme is an Identity based encryption system proposed by Clifford Cocks in 2001 . The security of the scheme is based on the hardness of the quadratic residuosity problem.-Setup:The PKG chooses:...
is based on well-studied assumptions (the quadratic residuosity assumption
Quadratic residuosity problem
The quadratic residuosity problem in computational number theory is the question of distinguishing by calculating the quadratic residues modulo N, where N is a composite number...
) but encrypts messages one bit at a time with a high degree of ciphertext expansion
Ciphertext expansion
In cryptography, the term ciphertext expansion refers to the length increase of a message when it is encrypted. Many modern cryptosystems cause some degree of expansion during the encryption process, for instance when the resulting ciphertext must include a message-unique Initialization Vector...
. Thus it is highly inefficient and impractical for sending all but the shortest messages, such as a session key for use with a symmetric cipher.
Advantages
One of the major advantages of any identity-based encryption scheme is that if there are only a finite number of users, after all users have been issued with keys the third party's secret can be destroyed. This can take place because this system assumes that, once issued, keys are always valid (as this basic system lacks a method of key revocation). The majority of derivatives of this system which have key revocation lose this advantage.Moreover, as public keys are derived from identifiers, IBE eliminates the need for a public key distribution infrastructure. The authenticity
Authentication
Authentication is the act of confirming the truth of an attribute of a datum or entity...
of the public keys is guaranteed implicitly as long as the transport of the private keys to the corresponding user is kept secure (Authenticity, Integrity
Data integrity
Data Integrity in its broadest meaning refers to the trustworthiness of system resources over their entire life cycle. In more analytic terms, it is "the representational faithfulness of information to the true state of the object that the information represents, where representational faithfulness...
, Confidentiality
Confidentiality
Confidentiality is an ethical principle associated with several professions . In ethics, and in law and alternative forms of legal resolution such as mediation, some types of communication between a person and one of these professionals are "privileged" and may not be discussed or divulged to...
).
Apart from these aspects, IBE offers interesting features emanating from the possibility to encode additional information into the identifier. For instance, a sender might specify an expiration date for a message. He appends this timestamp to the actual recipient's identity (possibly using some binary format like X.509). When the receiver contacts the PKG to retrieve the private key for this public key, the PKG can evaluate the identifier and decline the extraction if the expiration date has passed. Generally, embedding data in the ID corresponds to opening an additional channel between sender and PKG with authenticity guaranteed through the dependency of the private key on the identifier.
Drawbacks
- If a Private Key Generator (PKG) is compromised, all messages protected over the entire lifetime of the public-private key pair used by that server are also compromised. This makes the PKG a high value target to adversaries. To limit the exposure due to a compromised server, the master private-public key pair could be updated with a new independent key pair. However, this introduces a key-management problem where all users must have the most recent public key for the server.
- Because the Private Key Generator (PKG) generates private keys for users, it may decrypt and/or sign any message without authorisation. This implies that IBE systems cannot be used for non-repudiationNon-repudiationNon-repudiation refers to a state of affairs where the purported maker of a statement will not be able to successfully challenge the validity of the statement or contract. The term is often seen in a legal setting wherein the authenticity of a signature is being challenged...
. This may not be an issue for organizations that host their own PKG and are willing to trust their system administrators and do not require non-repudiation. - The issue of implicit key escrow does not exist with the current PKIPublic key infrastructurePublic Key Infrastructure is a set of hardware, software, people, policies, and procedures needed to create, manage, distribute, use, store, and revoke digital certificates. In cryptography, a PKI is an arrangement that binds public keys with respective user identities by means of a certificate...
system wherein private keys are usually generated on the user's computer. Depending on the context key escrow can be seen as a positive feature (e.g., within Enterprises). A number of variant systems have been proposed which remove the escrow including certificate-based encryptionCertificate-based encryptionCertificate-based encryption is a system in which a certificate authority uses ID-based cryptography to produce a certificate. This system gives the users both implicit and explicit certification, the certificate can be used as a conventional certificate , but also implicitly for the purpose of...
, secret sharingSecret sharingSecret sharing refers to method for distributing a secret amongst a group of participants, each of whom is allocated a share of the secret. The secret can be reconstructed only when a sufficient number of shares are combined together; individual shares are of no use on their own.More formally, in a...
, secure key issuing cryptographySecure key issuing cryptographySecure key issuing is variant of ID-based cryptography that reduces the level of trust that needs to be placed in a trusted third party by spreading the trust across multiple third parties. In addition to the normally transmitted information the user supplies what is known as "blinding"...
and certificateless cryptographyCertificateless cryptographyCertificateless cryptography is a variant of ID-based cryptography intended to prevent the key escrow problem. Ordinarily, keys are generated by a certificate authority or a key generation center who is given complete power and is implicitly trusted...
. - A secure channel between a user and the Private Key Generator (PKG) is required for transmitting the private key on joining the system. Here, a SSL-like connection is a common solution for a large-scale system. It is important to observe that users that hold accounts with the PKG must be able to authenticate themselves. In principle, this may be achieved through username,password or through public key pairs managed on smart cards.
- IBE solutions may rely on cryptographic techniques that are insecure against code breaking quantum computerQuantum computerA quantum computer is a device for computation that makes direct use of quantum mechanical phenomena, such as superposition and entanglement, to perform operations on data. Quantum computers are different from traditional computers based on transistors...
attacks (see Shor's algorithmShor's algorithmShor's algorithm, named after mathematician Peter Shor, is a quantum algorithm for integer factorization formulated in 1994...
)
External links
- Seminar 'Cryptography and Security in Banking'/'Alternative Cryptology', Ruhr University Bochum
- RFC 5091 - the IETF RFC defining two common IBE algorithms
- HP Role-Based Encryption
- The Pairing-Based Crypto Lounge
- The Voltage Security Network - IBE encryption web service
- VSN Fully Managed Email Encryption Service - UK based IBE encryption web service
- Analyst report on the cost of IBE versus PKI

