
Public key infrastructure
Encyclopedia
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
, a PKI is an arrangement that binds public keys with respective user identities by means of a certificate authority
Certificate authority
In cryptography, a certificate authority, or certification authority, is an entity that issues digital certificates. The digital certificate certifies the ownership of a public key by the named subject of the certificate...
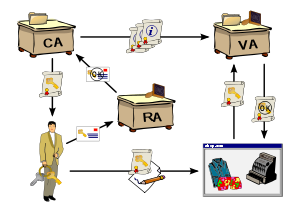
(CA). The user identity must be unique within each CA domain. The binding is established through the registration and issuance process, which, depending on the level of assurance the binding has, may be carried out by software at a CA, or under human supervision. The PKI role that assures this binding is called the Registration Authority (RA). The RA ensures that the public key is bound to the individual to which it is assigned in a way that ensures non-repudiation
Non-repudiation
Non-repudiation refers to a state of affairs where the purported maker of a statement will not be able to successfully challenge the validity of the statement or contract. The term is often seen in a legal setting wherein the authenticity of a signature is being challenged...
.
The term trusted third party
Trusted third party
In cryptography, a trusted third party is an entity which facilitates interactions between two parties who both trust the third party; The Third Party reviews all critical transaction communications between the parties, based on the ease of creating fraudulent digital content. In TTP models, the...
(TTP) may also be used for certificate authority
Certificate authority
In cryptography, a certificate authority, or certification authority, is an entity that issues digital certificates. The digital certificate certifies the ownership of a public key by the named subject of the certificate...
(CA). The term PKI is sometimes erroneously used to denote public key algorithms
Public-key cryptography
Public-key cryptography refers to a cryptographic system requiring two separate keys, one to lock or encrypt the plaintext, and one to unlock or decrypt the cyphertext. Neither key will do both functions. One of these keys is published or public and the other is kept private...
, which do not require the use of a CA.
Alternatives
Broadly speaking, there are three approaches to getting this trust: Certificate Authorities (CAs), Web of Trust (WoT), and Simple public key infrastructure (SPKI).Certificate Authorities
The primary role of the CA is to digitally sign and publish the public key bound to a given user. This is done using the CA's own private key, so that trust in the user key relies on one's trust in the validity of the CA's key. The mechanism that binds keys to users is called the Registration Authority (RA), which may or may not be separate from the CA. The key-user binding is established, depending on the level of assurance the binding has, by software or under human supervision.The term trusted third party
Trusted third party
In cryptography, a trusted third party is an entity which facilitates interactions between two parties who both trust the third party; The Third Party reviews all critical transaction communications between the parties, based on the ease of creating fraudulent digital content. In TTP models, the...
(TTP) may also be used for certificate authority
Certificate authority
In cryptography, a certificate authority, or certification authority, is an entity that issues digital certificates. The digital certificate certifies the ownership of a public key by the named subject of the certificate...
(CA). Moreover, PKI is itself often used as a synonym for a CA implementation.
Temporary Certificates & Single Sign-On
This approach involves a server that acts as an online certificate authority within a single sign-onSingle sign-on
Single sign-on is a property of access control of multiple related, but independent software systems. With this property a user logs in once and gains access to all systems without being prompted to log in again at each of them...
system. A single sign-on server will issue digital certificates into the client system, but never stores them. Users can execute programs, etc. with the temporary certificate. It is common to find this solution variety with x.509
X.509
In cryptography, X.509 is an ITU-T standard for a public key infrastructure and Privilege Management Infrastructure . X.509 specifies, amongst other things, standard formats for public key certificates, certificate revocation lists, attribute certificates, and a certification path validation...
-based certificates.
Web of Trust
An alternative approach to the problem of public authentication of public key information is the web of trust scheme, which uses self-signed certificatesPublic key certificate
In cryptography, a public key certificate is an electronic document which uses a digital signature to bind a public key with an identity — information such as the name of a person or an organization, their address, and so forth...
and third party attestations of those certificates. The singular term Web of Trust does not imply the existence of a single web of trust, or common point of trust, but rather one of any number of potentially disjoint "webs of trust". Examples of implementations of this approach are PGP
Pretty Good Privacy
Pretty Good Privacy is a data encryption and decryption computer program that provides cryptographic privacy and authentication for data communication. PGP is often used for signing, encrypting and decrypting texts, E-mails, files, directories and whole disk partitions to increase the security...
(Pretty Good Privacy) and GnuPG (an implementation of OpenPGP, the standardized specification of PGP). Because PGP and implementations allow the use of e-mail
E-mail
Electronic mail, commonly known as email or e-mail, is a method of exchanging digital messages from an author to one or more recipients. Modern email operates across the Internet or other computer networks. Some early email systems required that the author and the recipient both be online at the...
digital signatures for self-publication of public key information, it is relatively easy to implement one's own Web of Trust.
One of the benefits of the Web of Trust, such as in PGP
Pretty Good Privacy
Pretty Good Privacy is a data encryption and decryption computer program that provides cryptographic privacy and authentication for data communication. PGP is often used for signing, encrypting and decrypting texts, E-mails, files, directories and whole disk partitions to increase the security...
, is that it can interoperate with a PKI CA fully trusted by all parties in a domain (such as an internal CA in a company) that is willing to guarantee certificates, as a trusted introducer. Only if the "web of trust" is completely trusted, and because of the nature of a web of trust, trusting one certificate is granting trust to all the certificates in that web. A PKI is only as valuable as the standards and practices that control the issuance of certificates and including PGP or a personally instituted web of trust could significantly degrade the trustability of that enterprise's or domain's implementation of PKI.
The web of trust concept was first put forth by PGP creator Phil Zimmermann
Phil Zimmermann
Philip R. "Phil" Zimmermann Jr. is the creator of Pretty Good Privacy , the most widely used email encryption software in the world. He is also known for his work in VoIP encryption protocols, notably ZRTP and Zfone....
in 1992 in the manual for PGP version 2.0:
Simple public key infrastructure
Another alternative, which does not deal with public authentication of public key information, is the simple public key infrastructureSimple public key infrastructure
Simple public key infrastructure was born out of a joint effort to overcome the overcomplication and scalability problems of traditional X.509 public key infrastructure. It is specified in two Internet Engineering Task Force Request For Comments specifications—RFC 2692 and RFC 2693—from the IETF...
(SPKI) that grew out of three independent efforts to overcome the complexities of X.509
X.509
In cryptography, X.509 is an ITU-T standard for a public key infrastructure and Privilege Management Infrastructure . X.509 specifies, amongst other things, standard formats for public key certificates, certificate revocation lists, attribute certificates, and a certification path validation...
and PGP
Pretty Good Privacy
Pretty Good Privacy is a data encryption and decryption computer program that provides cryptographic privacy and authentication for data communication. PGP is often used for signing, encrypting and decrypting texts, E-mails, files, directories and whole disk partitions to increase the security...
's web of trust. SPKI does not associate users with persons, since the key is what is trusted, rather than the person. SPKI does not use any notion of trust, as the verifier is also the issuer. This is called an "authorization loop" in SPKI terminology, where authorization is integral to its design.
History
The concepts and use of Public Key Infrastructure were discovered by James H. EllisJames H. Ellis
James Henry Ellis was a British engineer and mathematician. In 1970, while working at the Government Communications Headquarters in Cheltenham he conceived of the possibility of "non-secret encryption", more commonly termed public-key cryptography.-Early life, education and career:Ellis was born...
and British GCHQ scientists in 1969. After the re-discovery and commercial use of PKI by Rivest, Shamir, Diffie and others, the British government considered releasing the records of GCHQ's successes in this field. However, the untimely publication of Spycatcher
Spycatcher
Spycatcher: The Candid Autobiography of a Senior Intelligence Officer , is a book written by Peter Wright, former MI5 officer and Assistant Director, and co-author Paul Greengrass. It was published first in Australia...
meant that the government once again issued a gag order and full details of GCHQ achievement were never revealed.
The public disclosure of both secure key exchange
Key exchange
Key exchange is any method in cryptography by which cryptographic keys are exchanged between users, allowing use of a cryptographic algorithm....
and asymmetric key algorithms in 1976 by Diffie
Whitfield Diffie
Bailey Whitfield 'Whit' Diffie is an American cryptographer and one of the pioneers of public-key cryptography.Diffie and Martin Hellman's paper New Directions in Cryptography was published in 1976...
, Hellman
Martin Hellman
Martin Edward Hellman is an American cryptologist, and is best known for his invention of public key cryptography in cooperation with Whitfield Diffie and Ralph Merkle...
, Rivest
Ron Rivest
Ronald Linn Rivest is a cryptographer. He is the Andrew and Erna Viterbi Professor of Computer Science at MIT's Department of Electrical Engineering and Computer Science and a member of MIT's Computer Science and Artificial Intelligence Laboratory...
, Shamir
Adi Shamir
Adi Shamir is an Israeli cryptographer. He is a co-inventor of the RSA algorithm , a co-inventor of the Feige–Fiat–Shamir identification scheme , one of the inventors of differential cryptanalysis and has made numerous contributions to the fields of cryptography and computer...
, and Adleman
Leonard Adleman
Leonard Max Adleman is an American theoretical computer scientist and professor of computer science and molecular biology at the University of Southern California. He is known for being a co-inventor of the RSA cryptosystem in 1977, and of DNA computing...
changed secure communications entirely. With the further development of high speed digital electronic communications (the Internet
Internet
The Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
and its predecessors), a need became evident for ways in which users could securely communicate with each other, and as a further consequence of that, for ways in which users could be sure with whom they were actually interacting.
Assorted cryptographic protocols
Cryptographic engineering
Cryptographic engineering is the discipline of using cryptography to solve human problems. Cryptography is typically applied when trying to ensure data confidentiality, to authenticate people or devices, or to verify data integrity in risky environments....
were invented and analyzed within which the new cryptographic primitive
Cryptographic primitive
Cryptographic primitives are well-established, low-level cryptographic algorithms that are frequently used to build computer security systems. These routines include, but are not limited to, one-way hash functions and encryption functions.- Rationale :...
s could be effectively used. With the invention of the World Wide Web
World Wide Web
The World Wide Web is a system of interlinked hypertext documents accessed via the Internet...
and its rapid spread, the need for authentication and secure communication became still more acute. Commercial reasons alone (e.g., e-commerce, on-line access to proprietary databases from Web browsers, etc.) were sufficient. Taher Elgamal
Taher Elgamal
Dr. Taher Elgamal is an Egyptian cryptographer. Elgamal is sometimes written as El Gamal or ElGamal, but Elgamal is now preferred...
and others at Netscape developed the SSL
Transport Layer Security
Transport Layer Security and its predecessor, Secure Sockets Layer , are cryptographic protocols that provide communication security over the Internet...
protocol ('https
Https
Hypertext Transfer Protocol Secure is a combination of the Hypertext Transfer Protocol with SSL/TLS protocol to provide encrypted communication and secure identification of a network web server...
' in Web URL
Uniform Resource Locator
In computing, a uniform resource locator or universal resource locator is a specific character string that constitutes a reference to an Internet resource....
s); it included key establishment, server authentication (prior to v3, one-way only), and so on. A PKI structure was thus created for Web users/sites wishing secure communications.
Vendors and entrepreneurs saw the possibility of a large market, started companies (or new projects at existing companies), and began to agitate for legal recognition and protection from liability. An American Bar Association
American Bar Association
The American Bar Association , founded August 21, 1878, is a voluntary bar association of lawyers and law students, which is not specific to any jurisdiction in the United States. The ABA's most important stated activities are the setting of academic standards for law schools, and the formulation...
technology project published an extensive analysis of some of the foreseeable legal aspects of PKI operations (see ABA digital signature guidelines
ABA digital signature guidelines
The ABA digital signature guidelines are a set of guidelines published on 1 August 1996 by the American Bar Association Section of Science and Technology Law. The authors are members of the Section's Information Security Committee...
), and shortly thereafter, several US states (Utah
Utah
Utah is a state in the Western United States. It was the 45th state to join the Union, on January 4, 1896. Approximately 80% of Utah's 2,763,885 people live along the Wasatch Front, centering on Salt Lake City. This leaves vast expanses of the state nearly uninhabited, making the population the...
being the first in 1995) and other jurisdictions throughout the world, began to enact laws and adopt regulations. Consumer groups and others raised questions of privacy
Privacy
Privacy is the ability of an individual or group to seclude themselves or information about themselves and thereby reveal themselves selectively...
, access, and liability considerations which were more taken into consideration in some jurisdictions than in others.
The enacted laws and regulations differed, there were technical and operational problems in converting PKI schemes into successful commercial operation, and progress has been far slower than pioneers had imagined it would be.
By the first few years of the 21st century the underlying cryptographic engineering was clearly not easy to deploy correctly. Operating procedures (manual or automatic) were not easy to correctly design (nor even if so designed, to execute perfectly, which the engineering required). The standards that existed were insufficient.
PKI vendors have found a market, but it is not quite the market envisioned in the mid-90s, and it has grown both more slowly and in somewhat different ways than were anticipated. PKIs have not solved some of the problems they were expected to, and several major vendors have gone out of business or been acquired by others. PKI has had the most success in government implementations; the largest PKI implementation to date is the Defense Information Systems Agency
Defense Information Systems Agency
The Defense Information Systems Agency is a United States Department of Defense agency that provides information technology and communications support to the President, Vice President, Secretary of Defense, the military Services, and the Combatant Commands.As part of the Base Realignment and...
(DISA) PKI infrastructure for the Common Access Card
Common Access Card
The Common Access Card is a United States Department of Defense smart card issued as standard identification for active-duty military personnel, reserve personnel, civilian employees, other non-DoD government employees, state employees of the National Guard, and eligible contractor personnel.The...
s program.
Security issues
- See PKI security issues with X.509
- See Breach of Comodo CA
- See Breach of Diginotar CA
Usage examples
PKIs of one type or another, and from any of several vendors, have many uses, including providing public keys and bindings to user identities which are used for:- EncryptionEncryptionIn cryptography, encryption is the process of transforming information using an algorithm to make it unreadable to anyone except those possessing special knowledge, usually referred to as a key. The result of the process is encrypted information...
and/or sender authenticationAuthenticationAuthentication is the act of confirming the truth of an attribute of a datum or entity...
of e-mailE-mailElectronic mail, commonly known as email or e-mail, is a method of exchanging digital messages from an author to one or more recipients. Modern email operates across the Internet or other computer networks. Some early email systems required that the author and the recipient both be online at the...
messages (e.g., using OpenPGP or S/MIMES/MIMES/MIME is a standard for public key encryption and signing of MIME data. S/MIME is on an IETF standards track and defined in a number of documents, most importantly RFCs. S/MIME was originally developed by RSA Data Security Inc...
). - Encryption and/or authentication of documents (e.g., the XML SignatureXML SignatureXML Signature defines an XML syntax for digital signatures and is defined in the W3C recommendation . Functionally, it has much in common with PKCS#7 but is more extensible and geared towards signing XML documents...
http://www.w3.org/TR/xmldsig-core/ or XML EncryptionXML EncryptionXML Encryption, also known as XML-Enc, is a specification, governed by a W3C recommendation, that defines how to encrypt the contents of an XML element....
http://www.w3.org/TR/xmlenc-core/ standards if documents are encoded as XMLXMLExtensible Markup Language is a set of rules for encoding documents in machine-readable form. It is defined in the XML 1.0 Specification produced by the W3C, and several other related specifications, all gratis open standards....
). - AuthenticationAuthenticationAuthentication is the act of confirming the truth of an attribute of a datum or entity...
of users to applications (e.g., smart cardSmart cardA smart card, chip card, or integrated circuit card , is any pocket-sized card with embedded integrated circuits. A smart card or microprocessor cards contain volatile memory and microprocessor components. The card is made of plastic, generally polyvinyl chloride, but sometimes acrylonitrile...
logon, client authentication with SSL). There's experimental usage for digitally signed HTTP authentication in the EnigformEnigformEnigform is a Mozilla Firefox extension authored by Arturo 'Buanzo' Busleiman which uses GnuPG to implement OpenPGP-signed HTTP requests. OpenPGP encryption began to be implemented in 2007. Some people believe it to be an alternative for the Secure Sockets Layer method for encrypting Hypertext...
and mod openpgp projects. - BootstrappingBootstrappingBootstrapping or booting refers to a group of metaphors that share a common meaning: a self-sustaining process that proceeds without external help....
secure communication protocols, such as Internet key exchange (IKE)Internet key exchangeInternet Key Exchange is the protocol used to set up a security association in the IPsec protocol suite. IKE builds upon the Oakley protocol and ISAKMP...
and SSL. In both of these, initial set-up of a secure channel (a "security associationSecurity associationA Security Association is the establishment of shared security attributes between two network entities to support secure communication. An SA may include attributes such as: cryptographic algorithm and mode; traffic encryption key; and parameters for the network data to be passed over the...
") uses asymmetric key (a.k.a. public key) methods, whereas actual communication uses faster symmetric key (a.k.a. secret key) methods. - Mobile signatures are electronic signatures that are created using a mobile device and rely on signature or certification services in a location independent telecommunication environment.
- Universal Metering InterfaceUniversal Metering InterfaceUMI is a set of 3 free open specifications for smart metering and smart home products. The UMI specifications define; a module interface based on SPI, an optical communications interface based on EN62056-21 and a security interface based on ECC-256 and AES-128...
(UMI) an open standard, originally created by Cambridge Consultants for use in Smart Metering devices/systems and home automation, uses a PKI infrastructure for security.
External links
- PKI tutorial by Peter GutmannPeter Gutmann (computer scientist)Peter Gutmann is a computer scientist in the Department of Computer Science at the University of Auckland, Auckland, New Zealand. He has a Ph.D. in computer science from the University of Auckland. His Ph.D. thesis and a book based on the thesis were about a cryptographic security architecture...
- PKI Tutorial using Fingerpuppets
- PKIX workgroup
- Easing the PAIN — a detailed explanation of PKI Privacy, Authentication, Integrity and Non-repudiation (PAIN)
- NIST PKI Program — in which the National Institute of Standards and Technology (NIST) is attempting to develop a public key infrastructure
- Ten Risks of PKI: What You're Not Being Told About Public Key Infrastructure by C. Ellison and B. Schneier
- Response to Ten Risks by A. Perez
- Seven and a Half Non-risks of PKI by B. Laurie
- The Inevitable Collapse of the Certificate Model by Hagai Bar-El

