Block cipher modes of operation
Encyclopedia
In cryptography
, modes of operation is the procedure of enabling the repeated and secure use of a block cipher
under a single key.
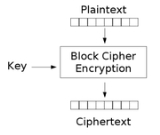
A block cipher by itself allows encryption
only of a single data block of the cipher's block length. When targeting a variable-length message, the data must first be partitioned into separate cipher blocks. Typically, the last block must also be extended to match the cipher's block length using a suitable padding scheme
. A mode of operation describes the process of encrypting each of these blocks, and generally uses randomization
based on an additional input value, often called an initialization vector
, to allow doing so safely.
Modes of operation have primarily been defined for encryption and authentication
.
Historically, encryption modes have been studied extensively in regard to their error propagation properties under various scenarios of data modification. Later development regarded integrity protection as an entirely separate cryptographic goal from encryption. Some modern modes of operation combine encryption and authentication in an efficient way, and are known as authenticated encryption
modes.
While modes of operation are commonly associated with symmetric encryption
, they may also be applied to public-key encryption
primitives such as RSA in principle (though in practice public-key encryption of longer messages is generally realized using hybrid encryption).
mode and available in many popular cryptographic libraries.
ECB, CBC, OFB, CFB, CTR, and XTS modes only provide confidentiality; to ensure an encrypted message is not accidentally modified or maliciously tampered requires a separate message authentication code
such as CBC-MAC
. The cryptographic community recognized the need for dedicated integrity assurances and NIST responded with HMAC, CMAC, and GMAC. HMAC
was approved in 2002 as FIPS 198, The Keyed-Hash Message Authentication Code (HMAC), CMAC
was released in 2005 under SP800-38B, Recommendation for Block Cipher Modes of Operation: The CMAC Mode for Authentication, and GMAC was formalized in 2007 under SP800-38D, Recommendation for Block Cipher Modes of Operation: Galois/Counter Mode (GCM) and GMAC.
After observing that compositing a confidentiality mode with an authenticity mode could be difficult and error prone, the cryptographic community began to supply modes which combined confidentiality and data integrity into a single cryptographic primitive. The modes are referred to as authenticated encryption
, AE or authenc. Examples of authenc modes are CCM
(SP800-38C), GCM (SP800-38D), CWC
, EAX
, IAPM
, and OCB
.
Modes of operation are nowadays defined by a number of national and internationally recognized standards bodies. The most influential source is the US NIST. Other notable standards organizations include the ISO, the IEC
, the IEEE, the national ANSI
, and the IETF.
(IV) is a block of bits that is used by several modes to randomize the encryption and hence to produce distinct ciphertexts even if the same plaintext is encrypted multiple times, without the need for a slower re-keying process.
An initialization vector
has different security requirements than a key, so the IV
usually does not need to be secret. However, in most cases, it is important that an initialization vector
is never reused under the same key. For CBC and CFB, reusing an IV leaks some information about the first block of plaintext, and about any common prefix shared by the two messages. For OFB and CTR, reusing an IV completely destroys security. In CBC mode, the IV
must, in addition, be unpredictable at encryption time; in particular, the (previously) common practice of re-using the last ciphertext block of a message as the IV
for the next message is insecure (for example, this method was used by SSL 2.0). If an attacker knows the IV
(or the previous block of ciphertext) before he specifies the next plaintext, he can check his guess about plaintext of some block that was encrypted with the same key before (this is known as the TLS CBC IV attack).
works on units of a fixed size
(known as a block size), but messages come in a variety of lengths. So some modes (namely ECB and CBC) require that the final block be padded before encryption. Several padding
schemes exist. The simplest is to add null bytes to the plaintext
to bring its length up to a multiple of the block size, but care must be taken that the original length of the plaintext can be recovered; this is so, for example, if the plaintext is a C
style string which contains no null bytes except at the end. Slightly more complex is the original DES
method, which is to add a single one bit
, followed by enough zero bit
s to fill out the block; if the message ends on a block boundary, a whole padding block will be added. Most sophisticated are CBC-specific schemes such as ciphertext stealing
or residual block termination
, which do not cause any extra ciphertext, at the expense of some additional complexity. Schneier
and Ferguson
suggest two possibilities, both simple: append a byte with value 128 (hex 80), followed by as many zero bytes as needed to fill the last block, or pad the last block with n bytes all with value n.
CFB, OFB and CTR modes do not require any special measures to handle messages whose lengths are not multiples of the block size, since the modes work by XORing the plaintext with the output of the block cipher. The last partial block of plaintext is XORed with the first few bytes of the last keystream
block, producing a final ciphertext block that is the same size as the final partial plaintext block. This characteristic of stream ciphers makes them suitable for applications that require the encrypted ciphertext data to be the same size as the original plaintext data,
and for applications that transmit data in streaming form where it is inconvenient to add padding bytes.
The disadvantage of this method is that identical plaintext
blocks are encrypted into identical ciphertext
blocks; thus, it does not hide data patterns well. In some senses, it doesn't provide serious message confidentiality, and it is not recommended for use in cryptographic protocols at all. A striking example of the degree to which ECB can leave plaintext data patterns in the ciphertext is shown below; a pixel-map version of the image on the left was encrypted with ECB mode to create the center image, versus a non-ECB mode for the right image.
The image on the right is how the image might appear encrypted with CBC, CTR or any of the other more secure modes—indistinguishable from random noise. Note that the random appearance of the image on the right does not ensure that the image has been securely encrypted; many kinds of insecure encryption have been developed which would produce output just as 'random-looking'.
ECB mode can also make protocols without integrity protection even more susceptible to replay attack
s, since each block gets decrypted in exactly the same way. For example, the Phantasy Star Online: Blue Burst
online video game uses Blowfish
in ECB mode. Before the key exchange system was cracked leading to even easier methods, cheaters repeated encrypted "monster killed" message packets, each an encrypted Blowfish block, to illegitimately gain experience point
s quickly.
must be used in the first block.
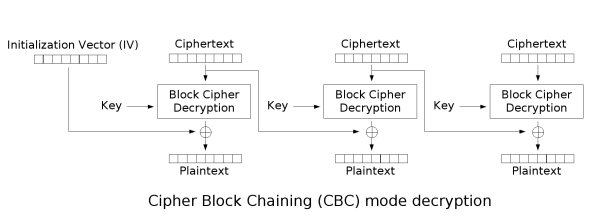
If the first block has index 1, the mathematical formula for CBC encryption is

while the mathematical formula for CBC decryption is

CBC has been the most commonly used mode of operation. Its main drawbacks are that encryption is sequential (i.e., it cannot be parallelized), and that the message must be padded to a multiple of the cipher block size. One way to handle this last issue is through the method known as ciphertext stealing
. Note that a one-bit change in a plaintext or IV affects all following ciphertext blocks.
Decrypting with the incorrect IV causes the first block of plaintext to be corrupt but subsequent plaintext blocks will be correct. This is because a plaintext block can be recovered from two adjacent blocks of ciphertext. As a consequence, decryption can be parallelized. Note that a one-bit change to the ciphertext causes complete corruption of the corresponding block of plaintext, and inverts the corresponding bit in the following block of plaintext, but the rest of the blocks remain intact.
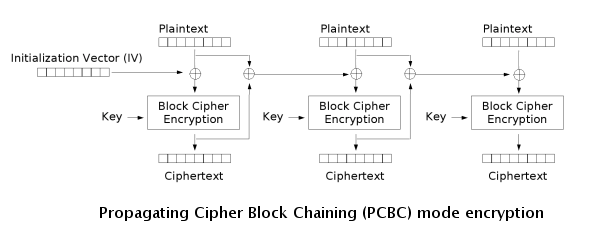
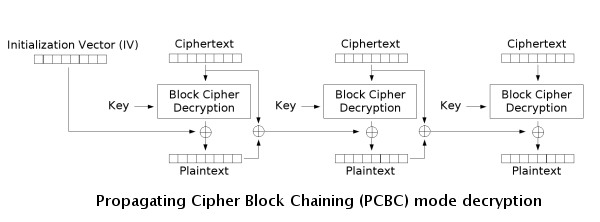
Encryption and decryption algorithms are as follows:


PCBC is used in Kerberos v4 and WASTE
, most notably, but otherwise is not common. On a message encrypted in PCBC mode, if two adjacent ciphertext blocks are exchanged, this does not affect the decryption of subsequent blocks. For this reason, PCBC is not used in Kerberos v5.
. Operation is very similar; in particular, CFB decryption is almost identical to CBC encryption performed in reverse:



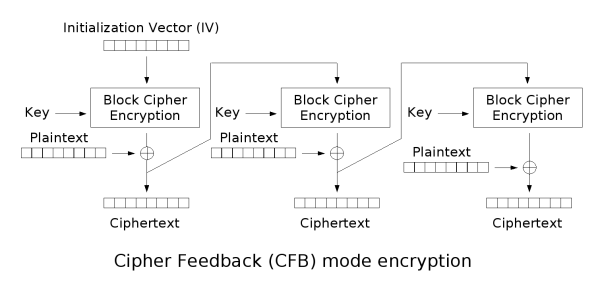
This simplest way of using CFB described above is not any more self-synchronizing than other cipher modes like CBC. If a whole blocksize of ciphertext is lost both CBC and CFB will synchronize, but losing only a single byte or bit will permanently throw off decryption. To be able to synchronize after the loss of only a single byte or bit, a single byte or bit must be encrypted at a time. CFB can be used this way when combined with a shift register
as the input for the block cipher.
To use CFB to make a self-synchronizing stream cipher that will synchronize for any multiple of x bits lost, start by initializing a shift register the size of the block size with the initialization vector. This is encrypted with the block cipher, and the highest x bits of the result are XOR'ed with x bits of the plaintext to produce x bits of ciphertext. These x bits of output are shifted into the shift register, and the process repeats with the next x bits of plaintext. Decryption is similar, start with the initialization vector, encrypt, and XOR the high bits of the result with x bits of the ciphertext to produce x bits of plaintext. Then shift the x bits of the ciphertext into the shift register. This way of proceeding is known as CFB-8 or CFB-1 (according to the size of the shifting).
In notation, where Si is the ith state of the shift register, a << x is a shifted up x bits, head(a, x) is the x highest bits of a and n is number of bits of IV:




If x bits are lost from the ciphertext, the cipher will output incorrect plaintext until the shift register once again equals a state it held while encrypting, at which point the cipher has resynchronized. This will result in at most one blocksize of output being garbled.
Like CBC mode, changes in the plaintext propagate forever in the ciphertext, and encryption cannot be parallelized. Also like CBC, decryption can be parallelized. When decrypting, a one-bit change in the ciphertext affects two plaintext blocks: a one-bit change in the corresponding plaintext block, and complete corruption of the following plaintext block. Later plaintext blocks are decrypted normally.
CFB shares two advantages over CBC mode with the stream cipher modes OFB and CTR: the block cipher is only ever used in the encrypting direction, and the message does not need to be padded to a multiple of the cipher block size (though ciphertext stealing
can also be used to make padding unnecessary).
. It generates keystream
blocks, which are then XORed with the plaintext blocks to get the ciphertext. Just as with other stream ciphers, flipping a bit in the ciphertext produces a flipped bit in the plaintext at the same location. This property allows many error correcting codes to function normally even when applied before encryption.
Because of the symmetry of the XOR operation, encryption and decryption are exactly the same:




Each output feedback block cipher operation depends on all previous ones, and so cannot be performed in parallel. However, because the plaintext or ciphertext is only used for the final XOR, the block cipher operations may be performed in advance, allowing the final step to be performed in parallel once the plaintext or ciphertext is available.
It is possible to obtain an OFB mode keystream by using CBC mode with a constant string of zeroes as input. This can be useful, because it allows the usage of fast hardware implementations of CBC mode for OFB mode encryption.
Using OFB mode with a partial block as feedback like CFB mode reduces the average cycle length by a factor of or more. A mathematical model proposed by Davies and Parkin and substantiated by experimental results showed that only with full feedback an average cycle length near to the obtainable maximum can be achieved. For this reason, support for truncated feedback was removed from the specification of OFB.
or more. A mathematical model proposed by Davies and Parkin and substantiated by experimental results showed that only with full feedback an average cycle length near to the obtainable maximum can be achieved. For this reason, support for truncated feedback was removed from the specification of OFB.
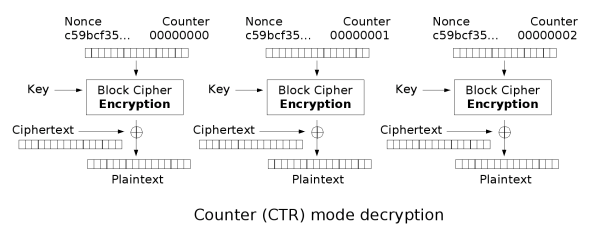
Like OFB, counter mode turns a block cipher
into a stream cipher
. It generates the next keystream
block by encrypting successive values of a "counter". The counter can be any function which produces a sequence which is guaranteed not to repeat for a long time, although an actual counter is the simplest and most popular. The usage of a simple deterministic input function used to be controversial; critics argued that "deliberately exposing a cryptosystem to a known systematic input represents an unnecessary risk." By now, CTR mode is widely accepted, and problems resulting from the input function are recognized as a weakness of the underlying block cipher instead of the CTR mode. Nevertheless, there are specialized attacks like a Hardware Fault Attack that is based on the usage of a simple counter function as input.
CTR mode has similar characteristics to OFB, but also allows a random access property during decryption. CTR mode is well suited to operation on a multi-processor machine where blocks can be encrypted in parallel. Furthermore, it does not suffer from the short-cycle problem that can affect OFB.
Note that the nonce
in this graph is the same thing as the initialization vector
(IV) in the other graphs. The IV/nonce and the counter can be concatenated, added, or XORed together to produce the actual unique counter block for encryption.
, it was common to discuss the "error propagation" properties as a selection criterion for a mode of operation. It might be observed, for example, that a one-block error in the transmitted ciphertext would result in a one-block error in the reconstructed plaintext for ECB mode encryption, while in CBC mode such an error would affect two blocks.
Some felt that such resilience was desirable in the face of random errors (e.g., line noise), while others argued that error correcting increased the scope for attackers to maliciously tamper with a message.
However, when proper integrity protection is used, such an error will result (with high probability) in the entire message being rejected. If resistance to random error is desirable, error-correcting codes should be applied to the ciphertext before transmission.
, OCB
, EAX
, CWC
, CCM
, and GCM. Authenticated encryption
modes are classified as single pass modes or double pass modes. Unfortunately for the cryptographic user community, many of the single pass authenticated encryption
algorithms (such as OCB mode
) are patent encumbered.
In addition, some modes also allow for the authentication of unencrypted associated data, and these are called AEAD
(Authenticated-Encryption with Associated-Data) schemes. For example, EAX mode is a double pass AEAD scheme while OCB mode is single pass.
NIST maintains a list of proposed modes for block ciphers at Modes Development.
Disk encryption often uses special purpose modes specifically designed for the application. Tweakable narrow-block encryption modes (LRW, XEX, and XTS) and wide-block encryption modes (CMC and EME) are designed to securely encrypt sectors of a disk. (See disk encryption theory)
Block ciphers can also be used in other cryptographic protocol
s. They are generally used in modes of operation similar to the block modes described here. As with all protocols, to be cryptographically secure, care must be taken to build them correctly.
There are several schemes which use a block cipher to build a cryptographic hash function
. See one-way compression function for descriptions of several such methods.
Cryptographically secure pseudorandom number generator
s (CSPRNGs) can also be built using block ciphers.
Message authentication code
s (MACs) are often built from block ciphers. CBC-MAC
, OMAC
and PMAC
are examples.
Authenticated encryption
also uses block ciphers as components. It means to both encrypt and MAC at the same time. That is to both provide confidentiality
and authentication
. IAPM
, CCM
, CWC
, EAX
, GCM
and OCB
are such authenticated encryption modes.
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
, modes of operation is the procedure of enabling the repeated and secure use of a block cipher
Block cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
under a single key.
A block cipher by itself allows encryption
Encryption
In cryptography, encryption is the process of transforming information using an algorithm to make it unreadable to anyone except those possessing special knowledge, usually referred to as a key. The result of the process is encrypted information...
only of a single data block of the cipher's block length. When targeting a variable-length message, the data must first be partitioned into separate cipher blocks. Typically, the last block must also be extended to match the cipher's block length using a suitable padding scheme
Padding (cryptography)
-Classical cryptography:Official messages often start and end in predictable ways: My dear ambassador, Weather report, Sincerely yours, etc. The primary use of padding with classical ciphers is to prevent the cryptanalyst from using that predictability to find cribs that aid in breaking the...
. A mode of operation describes the process of encrypting each of these blocks, and generally uses randomization
Randomization
Randomization is the process of making something random; this means:* Generating a random permutation of a sequence .* Selecting a random sample of a population ....
based on an additional input value, often called an initialization vector
Initialization vector
In cryptography, an initialization vector is a fixed-size input to a cryptographic primitive that is typically required to be random or pseudorandom...
, to allow doing so safely.
Modes of operation have primarily been defined for encryption and authentication
Authentication
Authentication is the act of confirming the truth of an attribute of a datum or entity...
.
Historically, encryption modes have been studied extensively in regard to their error propagation properties under various scenarios of data modification. Later development regarded integrity protection as an entirely separate cryptographic goal from encryption. Some modern modes of operation combine encryption and authentication in an efficient way, and are known as authenticated encryption
Authenticated encryption
Authenticated Encryption is a block cipher mode of operation which simultaneously provides confidentiality, integrity and authenticity assurances on the data. It became readily apparent that securely compositing a confidentiality mode with an authentication mode could be error prone and difficult...
modes.
While modes of operation are commonly associated with symmetric encryption
Symmetric-key algorithm
Symmetric-key algorithms are a class of algorithms for cryptography that use trivially related, often identical, cryptographic keys for both encryption of plaintext and decryption of ciphertext. The encryption key is trivially related to the decryption key, in that they may be identical or there is...
, they may also be applied to public-key encryption
Public-key cryptography
Public-key cryptography refers to a cryptographic system requiring two separate keys, one to lock or encrypt the plaintext, and one to unlock or decrypt the cyphertext. Neither key will do both functions. One of these keys is published or public and the other is kept private...
primitives such as RSA in principle (though in practice public-key encryption of longer messages is generally realized using hybrid encryption).
History and standardization
The earliest modes of operation, ECB, CBC, OFB, and CFB (see below for all), date back to 1981 and were specified in FIPS 81, DES Modes of Operation. In 2001, NIST revised its list of approved modes of operation by including AES as a block cipher and adding CTR mode in SP800-38A, Recommendation for Block Cipher Modes of Operation. Finally, in January, 2010, NIST added XTS-AES in SP800-38E, Recommendation for Block Cipher Modes of Operation: The XTS-AES Mode for Confidentiality on Storage Devices. Other confidentiality modes exist which have not been approved by NIST. For example, CTS is ciphertext stealingCiphertext stealing
In cryptography, ciphertext stealing is a general method of using a block cipher mode of operation that allows for processing of messages that are not evenly divisible into blocks without resulting in any expansion of the ciphertext, at the cost of slightly increased complexity.-General...
mode and available in many popular cryptographic libraries.
ECB, CBC, OFB, CFB, CTR, and XTS modes only provide confidentiality; to ensure an encrypted message is not accidentally modified or maliciously tampered requires a separate message authentication code
Message authentication code
In cryptography, a message authentication code is a short piece of information used to authenticate a message.A MAC algorithm, sometimes called a keyed hash function, accepts as input a secret key and an arbitrary-length message to be authenticated, and outputs a MAC...
such as CBC-MAC
CBC-MAC
In cryptography, a cipher block chaining message authentication code , is a technique for constructing a message authentication code from a block cipher. The message is encrypted with some block cipher algorithm in CBC mode to create a chain of blocks such that each block depends on the proper...
. The cryptographic community recognized the need for dedicated integrity assurances and NIST responded with HMAC, CMAC, and GMAC. HMAC
HMAC
In cryptography, HMAC is a specific construction for calculating a message authentication code involving a cryptographic hash function in combination with a secret key. As with any MAC, it may be used to simultaneously verify both the data integrity and the authenticity of a message...
was approved in 2002 as FIPS 198, The Keyed-Hash Message Authentication Code (HMAC), CMAC
CMAC
In cryptography, CMAC is a block cipher-based message authentication code algorithm. It may be used to provide assurance of the authenticity and, hence, the integrity of binary data...
was released in 2005 under SP800-38B, Recommendation for Block Cipher Modes of Operation: The CMAC Mode for Authentication, and GMAC was formalized in 2007 under SP800-38D, Recommendation for Block Cipher Modes of Operation: Galois/Counter Mode (GCM) and GMAC.
After observing that compositing a confidentiality mode with an authenticity mode could be difficult and error prone, the cryptographic community began to supply modes which combined confidentiality and data integrity into a single cryptographic primitive. The modes are referred to as authenticated encryption
Authenticated encryption
Authenticated Encryption is a block cipher mode of operation which simultaneously provides confidentiality, integrity and authenticity assurances on the data. It became readily apparent that securely compositing a confidentiality mode with an authentication mode could be error prone and difficult...
, AE or authenc. Examples of authenc modes are CCM
CCM mode
CCM mode is a mode of operation for cryptographic block ciphers. It is an authenticated encryption algorithm designed to provide both authentication and confidentiality. CCM mode is only defined for block ciphers with a block length of 128 bits...
(SP800-38C), GCM (SP800-38D), CWC
CWC mode
In cryptography, CWC Mode is an AEAD block cipher mode of operation that provides both encryption and built-in message integrity, similar to CCM and OCB modes. Designed by Tadayoshi Kohno, John Viega and Doug Whiting, NIST is CWC mode for standardization...
, EAX
EAX mode
EAX mode is a mode of operation for cryptographic block ciphers. It is an Authenticated Encryption with Associated Data algorithm designed to simultaneously provide both authentication and privacy of the message with a two-pass scheme, one pass for achieving privacy and one for authenticity for...
, IAPM
IAPM mode
Integrity Aware Parallelizable Mode is a mode of operation for cryptographic block ciphers. As its name implies, it allows for a parallel mode of operation for very high throughput.-Encryption and authentication:...
, and OCB
OCB mode
OCB mode is a mode of operation for cryptographic block ciphers.-Encryption and authentication:It was designed to provide both authentication and privacy. It is essentially a scheme for integrating a Message Authentication Code into the operation of a block cipher...
.
Modes of operation are nowadays defined by a number of national and internationally recognized standards bodies. The most influential source is the US NIST. Other notable standards organizations include the ISO, the IEC
International Electrotechnical Commission
The International Electrotechnical Commission is a non-profit, non-governmental international standards organization that prepares and publishes International Standards for all electrical, electronic and related technologies – collectively known as "electrotechnology"...
, the IEEE, the national ANSI
Ansi
Ansi is a village in Kaarma Parish, Saare County, on the island of Saaremaa, Estonia....
, and the IETF.
Initialization vector (IV)
An initialization vectorInitialization vector
In cryptography, an initialization vector is a fixed-size input to a cryptographic primitive that is typically required to be random or pseudorandom...
(IV) is a block of bits that is used by several modes to randomize the encryption and hence to produce distinct ciphertexts even if the same plaintext is encrypted multiple times, without the need for a slower re-keying process.
An initialization vector
Initialization vector
In cryptography, an initialization vector is a fixed-size input to a cryptographic primitive that is typically required to be random or pseudorandom...
has different security requirements than a key, so the IV
Initialization vector
In cryptography, an initialization vector is a fixed-size input to a cryptographic primitive that is typically required to be random or pseudorandom...
usually does not need to be secret. However, in most cases, it is important that an initialization vector
Initialization vector
In cryptography, an initialization vector is a fixed-size input to a cryptographic primitive that is typically required to be random or pseudorandom...
is never reused under the same key. For CBC and CFB, reusing an IV leaks some information about the first block of plaintext, and about any common prefix shared by the two messages. For OFB and CTR, reusing an IV completely destroys security. In CBC mode, the IV
Initialization vector
In cryptography, an initialization vector is a fixed-size input to a cryptographic primitive that is typically required to be random or pseudorandom...
must, in addition, be unpredictable at encryption time; in particular, the (previously) common practice of re-using the last ciphertext block of a message as the IV
Initialization vector
In cryptography, an initialization vector is a fixed-size input to a cryptographic primitive that is typically required to be random or pseudorandom...
for the next message is insecure (for example, this method was used by SSL 2.0). If an attacker knows the IV
Initialization vector
In cryptography, an initialization vector is a fixed-size input to a cryptographic primitive that is typically required to be random or pseudorandom...
(or the previous block of ciphertext) before he specifies the next plaintext, he can check his guess about plaintext of some block that was encrypted with the same key before (this is known as the TLS CBC IV attack).
Padding
A block cipherBlock cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
works on units of a fixed size
Block size (cryptography)
In modern cryptography, symmetric key ciphers are generally divided into stream ciphers and block ciphers. Block ciphers operate on a fixed length string of bits. The length of this bit string is the block size...
(known as a block size), but messages come in a variety of lengths. So some modes (namely ECB and CBC) require that the final block be padded before encryption. Several padding
Padding (cryptography)
-Classical cryptography:Official messages often start and end in predictable ways: My dear ambassador, Weather report, Sincerely yours, etc. The primary use of padding with classical ciphers is to prevent the cryptanalyst from using that predictability to find cribs that aid in breaking the...
schemes exist. The simplest is to add null bytes to the plaintext
Plaintext
In cryptography, plaintext is information a sender wishes to transmit to a receiver. Cleartext is often used as a synonym. Before the computer era, plaintext most commonly meant message text in the language of the communicating parties....
to bring its length up to a multiple of the block size, but care must be taken that the original length of the plaintext can be recovered; this is so, for example, if the plaintext is a C
C (programming language)
C is a general-purpose computer programming language developed between 1969 and 1973 by Dennis Ritchie at the Bell Telephone Laboratories for use with the Unix operating system....
style string which contains no null bytes except at the end. Slightly more complex is the original DES
Data Encryption Standard
The Data Encryption Standard is a block cipher that uses shared secret encryption. It was selected by the National Bureau of Standards as an official Federal Information Processing Standard for the United States in 1976 and which has subsequently enjoyed widespread use internationally. It is...
method, which is to add a single one bit
Bit
A bit is the basic unit of information in computing and telecommunications; it is the amount of information stored by a digital device or other physical system that exists in one of two possible distinct states...
, followed by enough zero bit
Bit
A bit is the basic unit of information in computing and telecommunications; it is the amount of information stored by a digital device or other physical system that exists in one of two possible distinct states...
s to fill out the block; if the message ends on a block boundary, a whole padding block will be added. Most sophisticated are CBC-specific schemes such as ciphertext stealing
Ciphertext stealing
In cryptography, ciphertext stealing is a general method of using a block cipher mode of operation that allows for processing of messages that are not evenly divisible into blocks without resulting in any expansion of the ciphertext, at the cost of slightly increased complexity.-General...
or residual block termination
Residual block termination
In cryptography, residual block termination is a variation of cipher block chaining mode that does not require any padding. It does this by effectively changing to cipher feedback mode for one block...
, which do not cause any extra ciphertext, at the expense of some additional complexity. Schneier
Bruce Schneier
Bruce Schneier is an American cryptographer, computer security specialist, and writer. He is the author of several books on general security topics, computer security and cryptography, and is the founder and chief technology officer of BT Managed Security Solutions, formerly Counterpane Internet...
and Ferguson
Niels Ferguson
Niels T. Ferguson is a Dutch cryptographer and consultant who currently works for Microsoft. He has worked with others, including Bruce Schneier, designing cryptographic algorithms, testing algorithms and protocols, and writing papers and books...
suggest two possibilities, both simple: append a byte with value 128 (hex 80), followed by as many zero bytes as needed to fill the last block, or pad the last block with n bytes all with value n.
CFB, OFB and CTR modes do not require any special measures to handle messages whose lengths are not multiples of the block size, since the modes work by XORing the plaintext with the output of the block cipher. The last partial block of plaintext is XORed with the first few bytes of the last keystream
Keystream
In cryptography, a keystream is a stream of random or pseudorandom characters that are combined with a plaintext message to produce an encrypted message ....
block, producing a final ciphertext block that is the same size as the final partial plaintext block. This characteristic of stream ciphers makes them suitable for applications that require the encrypted ciphertext data to be the same size as the original plaintext data,
and for applications that transmit data in streaming form where it is inconvenient to add padding bytes.
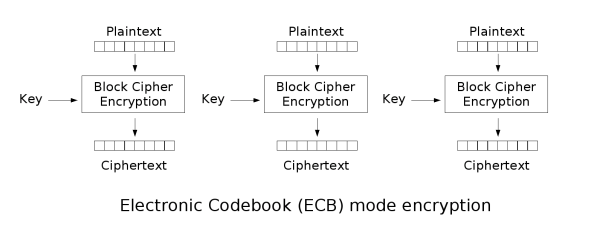
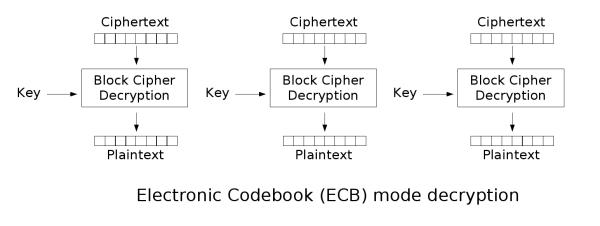
Electronic codebook (ECB)
The simplest of the encryption modes is the electronic codebook (ECB) mode. The message is divided into blocks and each block is encrypted separately.

The disadvantage of this method is that identical plaintext
Plaintext
In cryptography, plaintext is information a sender wishes to transmit to a receiver. Cleartext is often used as a synonym. Before the computer era, plaintext most commonly meant message text in the language of the communicating parties....
blocks are encrypted into identical ciphertext
Ciphertext
In cryptography, ciphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext that is unreadable by a human or computer without the proper cipher...
blocks; thus, it does not hide data patterns well. In some senses, it doesn't provide serious message confidentiality, and it is not recommended for use in cryptographic protocols at all. A striking example of the degree to which ECB can leave plaintext data patterns in the ciphertext is shown below; a pixel-map version of the image on the left was encrypted with ECB mode to create the center image, versus a non-ECB mode for the right image.
 |
 |
 |
| Original | Encrypted using ECB mode | Modes other than ECB result in pseudo-randomness |
The image on the right is how the image might appear encrypted with CBC, CTR or any of the other more secure modes—indistinguishable from random noise. Note that the random appearance of the image on the right does not ensure that the image has been securely encrypted; many kinds of insecure encryption have been developed which would produce output just as 'random-looking'.
ECB mode can also make protocols without integrity protection even more susceptible to replay attack
Replay attack
A replay attack is a form of network attack in which a valid data transmission is maliciously or fraudulently repeated or delayed. This is carried out either by the originator or by an adversary who intercepts the data and retransmits it, possibly as part of a masquerade attack by IP packet...
s, since each block gets decrypted in exactly the same way. For example, the Phantasy Star Online: Blue Burst
Phantasy Star Online
Phantasy Star Online is an online multiplayer action RPG title, originally released for the Dreamcast in 2000, bundled with a demo of Sonic Adventure 2. Another edition, entitled Phantasy Star Online ver.2, was released for Dreamcast the following year...
online video game uses Blowfish
Blowfish (cipher)
Blowfish is a keyed, symmetric block cipher, designed in 1993 by Bruce Schneier and included in a large number of cipher suites and encryption products. Blowfish provides a good encryption rate in software and no effective cryptanalysis of it has been found to date...
in ECB mode. Before the key exchange system was cracked leading to even easier methods, cheaters repeated encrypted "monster killed" message packets, each an encrypted Blowfish block, to illegitimately gain experience point
Experience point
An experience point is a unit of measurement used in many role-playing games and role-playing video games to quantify a player character's progression through the game...
s quickly.
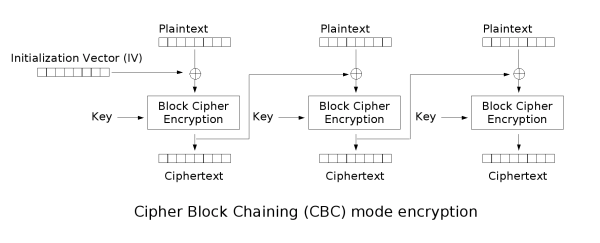
Cipher-block chaining (CBC)
Cipher-block chaining (CBC) mode of operation was invented by IBM in 1976. In CBC mode, each block of plaintext is XORed with the previous ciphertext block before being encrypted. This way, each ciphertext block is dependent on all plaintext blocks processed up to that point. Also, to make each message unique, an initialization vectorInitialization vector
In cryptography, an initialization vector is a fixed-size input to a cryptographic primitive that is typically required to be random or pseudorandom...
must be used in the first block.


If the first block has index 1, the mathematical formula for CBC encryption is

while the mathematical formula for CBC decryption is

CBC has been the most commonly used mode of operation. Its main drawbacks are that encryption is sequential (i.e., it cannot be parallelized), and that the message must be padded to a multiple of the cipher block size. One way to handle this last issue is through the method known as ciphertext stealing
Ciphertext stealing
In cryptography, ciphertext stealing is a general method of using a block cipher mode of operation that allows for processing of messages that are not evenly divisible into blocks without resulting in any expansion of the ciphertext, at the cost of slightly increased complexity.-General...
. Note that a one-bit change in a plaintext or IV affects all following ciphertext blocks.
Decrypting with the incorrect IV causes the first block of plaintext to be corrupt but subsequent plaintext blocks will be correct. This is because a plaintext block can be recovered from two adjacent blocks of ciphertext. As a consequence, decryption can be parallelized. Note that a one-bit change to the ciphertext causes complete corruption of the corresponding block of plaintext, and inverts the corresponding bit in the following block of plaintext, but the rest of the blocks remain intact.
Propagating cipher-block chaining (PCBC)
The propagating cipher-block chaining or plaintext cipher-block chaining mode was designed to cause small changes in the ciphertext to propagate indefinitely when decrypting, as well as when encrypting.

Encryption and decryption algorithms are as follows:


PCBC is used in Kerberos v4 and WASTE
WASTE
WASTE is a peer-to-peer and friend-to-friend protocol and software application developed by Justin Frankel at Nullsoft in 2003 that features instant messaging, chat rooms and file browsing/sharing capabilities. The name WASTE is a reference to Thomas Pynchon's novel The Crying of Lot 49. In the...
, most notably, but otherwise is not common. On a message encrypted in PCBC mode, if two adjacent ciphertext blocks are exchanged, this does not affect the decryption of subsequent blocks. For this reason, PCBC is not used in Kerberos v5.
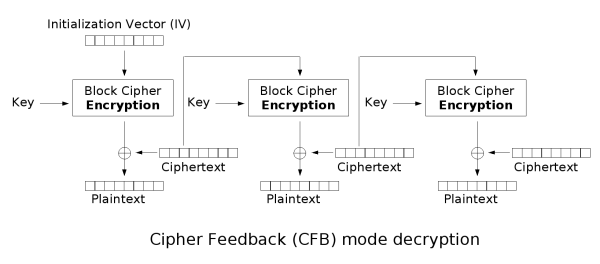
Cipher feedback (CFB)
The cipher feedback (CFB) mode, a close relative of CBC, makes a block cipher into a self-synchronizing stream cipherStream cipher
In cryptography, a stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream . In a stream cipher the plaintext digits are encrypted one at a time, and the transformation of successive digits varies during the encryption...
. Operation is very similar; in particular, CFB decryption is almost identical to CBC encryption performed in reverse:





This simplest way of using CFB described above is not any more self-synchronizing than other cipher modes like CBC. If a whole blocksize of ciphertext is lost both CBC and CFB will synchronize, but losing only a single byte or bit will permanently throw off decryption. To be able to synchronize after the loss of only a single byte or bit, a single byte or bit must be encrypted at a time. CFB can be used this way when combined with a shift register
Shift register
In digital circuits, a shift register is a cascade of flip flops, sharing the same clock, which has the output of any one but the last flip-flop connected to the "data" input of the next one in the chain, resulting in a circuit that shifts by one position the one-dimensional "bit array" stored in...
as the input for the block cipher.
To use CFB to make a self-synchronizing stream cipher that will synchronize for any multiple of x bits lost, start by initializing a shift register the size of the block size with the initialization vector. This is encrypted with the block cipher, and the highest x bits of the result are XOR'ed with x bits of the plaintext to produce x bits of ciphertext. These x bits of output are shifted into the shift register, and the process repeats with the next x bits of plaintext. Decryption is similar, start with the initialization vector, encrypt, and XOR the high bits of the result with x bits of the ciphertext to produce x bits of plaintext. Then shift the x bits of the ciphertext into the shift register. This way of proceeding is known as CFB-8 or CFB-1 (according to the size of the shifting).
In notation, where Si is the ith state of the shift register, a << x is a shifted up x bits, head(a, x) is the x highest bits of a and n is number of bits of IV:




If x bits are lost from the ciphertext, the cipher will output incorrect plaintext until the shift register once again equals a state it held while encrypting, at which point the cipher has resynchronized. This will result in at most one blocksize of output being garbled.
Like CBC mode, changes in the plaintext propagate forever in the ciphertext, and encryption cannot be parallelized. Also like CBC, decryption can be parallelized. When decrypting, a one-bit change in the ciphertext affects two plaintext blocks: a one-bit change in the corresponding plaintext block, and complete corruption of the following plaintext block. Later plaintext blocks are decrypted normally.
CFB shares two advantages over CBC mode with the stream cipher modes OFB and CTR: the block cipher is only ever used in the encrypting direction, and the message does not need to be padded to a multiple of the cipher block size (though ciphertext stealing
Ciphertext stealing
In cryptography, ciphertext stealing is a general method of using a block cipher mode of operation that allows for processing of messages that are not evenly divisible into blocks without resulting in any expansion of the ciphertext, at the cost of slightly increased complexity.-General...
can also be used to make padding unnecessary).
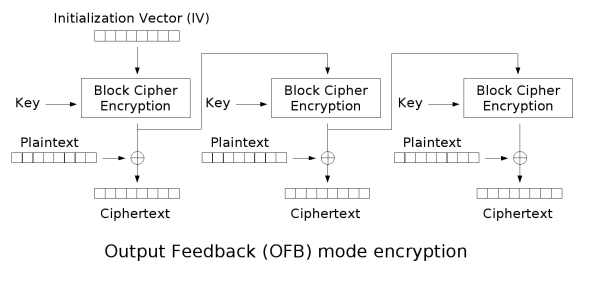
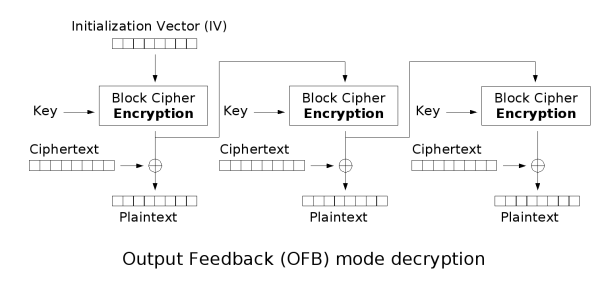
Output feedback (OFB)
The output feedback (OFB) mode makes a block cipher into a synchronous stream cipherStream cipher
In cryptography, a stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream . In a stream cipher the plaintext digits are encrypted one at a time, and the transformation of successive digits varies during the encryption...
. It generates keystream
Keystream
In cryptography, a keystream is a stream of random or pseudorandom characters that are combined with a plaintext message to produce an encrypted message ....
blocks, which are then XORed with the plaintext blocks to get the ciphertext. Just as with other stream ciphers, flipping a bit in the ciphertext produces a flipped bit in the plaintext at the same location. This property allows many error correcting codes to function normally even when applied before encryption.
Because of the symmetry of the XOR operation, encryption and decryption are exactly the same:






Each output feedback block cipher operation depends on all previous ones, and so cannot be performed in parallel. However, because the plaintext or ciphertext is only used for the final XOR, the block cipher operations may be performed in advance, allowing the final step to be performed in parallel once the plaintext or ciphertext is available.
It is possible to obtain an OFB mode keystream by using CBC mode with a constant string of zeroes as input. This can be useful, because it allows the usage of fast hardware implementations of CBC mode for OFB mode encryption.
Using OFB mode with a partial block as feedback like CFB mode reduces the average cycle length by a factor of
 or more. A mathematical model proposed by Davies and Parkin and substantiated by experimental results showed that only with full feedback an average cycle length near to the obtainable maximum can be achieved. For this reason, support for truncated feedback was removed from the specification of OFB.
or more. A mathematical model proposed by Davies and Parkin and substantiated by experimental results showed that only with full feedback an average cycle length near to the obtainable maximum can be achieved. For this reason, support for truncated feedback was removed from the specification of OFB.Counter (CTR)
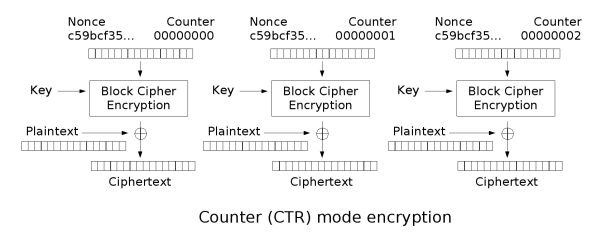
- Note: CTR mode (CM) is also known as integer counter mode (ICM) and segmented integer counter (SIC) mode
Like OFB, counter mode turns a block cipher
Block cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
into a stream cipher
Stream cipher
In cryptography, a stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream . In a stream cipher the plaintext digits are encrypted one at a time, and the transformation of successive digits varies during the encryption...
. It generates the next keystream
Keystream
In cryptography, a keystream is a stream of random or pseudorandom characters that are combined with a plaintext message to produce an encrypted message ....
block by encrypting successive values of a "counter". The counter can be any function which produces a sequence which is guaranteed not to repeat for a long time, although an actual counter is the simplest and most popular. The usage of a simple deterministic input function used to be controversial; critics argued that "deliberately exposing a cryptosystem to a known systematic input represents an unnecessary risk." By now, CTR mode is widely accepted, and problems resulting from the input function are recognized as a weakness of the underlying block cipher instead of the CTR mode. Nevertheless, there are specialized attacks like a Hardware Fault Attack that is based on the usage of a simple counter function as input.
CTR mode has similar characteristics to OFB, but also allows a random access property during decryption. CTR mode is well suited to operation on a multi-processor machine where blocks can be encrypted in parallel. Furthermore, it does not suffer from the short-cycle problem that can affect OFB.
Note that the nonce
Cryptographic nonce
In security engineering, nonce is an arbitrary number used only once to sign a cryptographic communication. It is similar in spirit to a nonce word, hence the name. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused...
in this graph is the same thing as the initialization vector
Initialization vector
In cryptography, an initialization vector is a fixed-size input to a cryptographic primitive that is typically required to be random or pseudorandom...
(IV) in the other graphs. The IV/nonce and the counter can be concatenated, added, or XORed together to produce the actual unique counter block for encryption.


Error propagation
Before the widespread use of message authentication codes and authenticated encryptionAuthenticated encryption
Authenticated Encryption is a block cipher mode of operation which simultaneously provides confidentiality, integrity and authenticity assurances on the data. It became readily apparent that securely compositing a confidentiality mode with an authentication mode could be error prone and difficult...
, it was common to discuss the "error propagation" properties as a selection criterion for a mode of operation. It might be observed, for example, that a one-block error in the transmitted ciphertext would result in a one-block error in the reconstructed plaintext for ECB mode encryption, while in CBC mode such an error would affect two blocks.
Some felt that such resilience was desirable in the face of random errors (e.g., line noise), while others argued that error correcting increased the scope for attackers to maliciously tamper with a message.
However, when proper integrity protection is used, such an error will result (with high probability) in the entire message being rejected. If resistance to random error is desirable, error-correcting codes should be applied to the ciphertext before transmission.
Authenticated encryption
A number of modes of operation have been designed to combine confidentiality and authentication in a single cryptographic primitive. Examples of such modes are XCBC, IACBC, IAPMIAPM mode
Integrity Aware Parallelizable Mode is a mode of operation for cryptographic block ciphers. As its name implies, it allows for a parallel mode of operation for very high throughput.-Encryption and authentication:...
, OCB
OCB mode
OCB mode is a mode of operation for cryptographic block ciphers.-Encryption and authentication:It was designed to provide both authentication and privacy. It is essentially a scheme for integrating a Message Authentication Code into the operation of a block cipher...
, EAX
EAX mode
EAX mode is a mode of operation for cryptographic block ciphers. It is an Authenticated Encryption with Associated Data algorithm designed to simultaneously provide both authentication and privacy of the message with a two-pass scheme, one pass for achieving privacy and one for authenticity for...
, CWC
CWC mode
In cryptography, CWC Mode is an AEAD block cipher mode of operation that provides both encryption and built-in message integrity, similar to CCM and OCB modes. Designed by Tadayoshi Kohno, John Viega and Doug Whiting, NIST is CWC mode for standardization...
, CCM
CCM mode
CCM mode is a mode of operation for cryptographic block ciphers. It is an authenticated encryption algorithm designed to provide both authentication and confidentiality. CCM mode is only defined for block ciphers with a block length of 128 bits...
, and GCM. Authenticated encryption
Authenticated encryption
Authenticated Encryption is a block cipher mode of operation which simultaneously provides confidentiality, integrity and authenticity assurances on the data. It became readily apparent that securely compositing a confidentiality mode with an authentication mode could be error prone and difficult...
modes are classified as single pass modes or double pass modes. Unfortunately for the cryptographic user community, many of the single pass authenticated encryption
Authenticated encryption
Authenticated Encryption is a block cipher mode of operation which simultaneously provides confidentiality, integrity and authenticity assurances on the data. It became readily apparent that securely compositing a confidentiality mode with an authentication mode could be error prone and difficult...
algorithms (such as OCB mode
OCB mode
OCB mode is a mode of operation for cryptographic block ciphers.-Encryption and authentication:It was designed to provide both authentication and privacy. It is essentially a scheme for integrating a Message Authentication Code into the operation of a block cipher...
) are patent encumbered.
In addition, some modes also allow for the authentication of unencrypted associated data, and these are called AEAD
AEAD block cipher modes of operation
Authenticated Encryption with Associated Data is a class of block cipher modes which encrypt the message and authenticate the message simultaneously. Interest in these modes was sparked by the publication of Charanjit Jutla's IACBC and IAPM modes in 2000. As of 2005 this is an active area of...
(Authenticated-Encryption with Associated-Data) schemes. For example, EAX mode is a double pass AEAD scheme while OCB mode is single pass.
Other modes and other cryptographic primitives
Many more modes of operation for block ciphers have been suggested. Some have been accepted, fully described (even standardized), and are in use. Others have been found insecure, and should never be used. Still others don't categorize as confidentiality, authenticity, or authenticated encryption - for example Key Feedback Mode (KFM) and AES-hash.NIST maintains a list of proposed modes for block ciphers at Modes Development.
Disk encryption often uses special purpose modes specifically designed for the application. Tweakable narrow-block encryption modes (LRW, XEX, and XTS) and wide-block encryption modes (CMC and EME) are designed to securely encrypt sectors of a disk. (See disk encryption theory)
Block ciphers can also be used in other cryptographic protocol
Cryptographic protocol
A security protocol is an abstract or concrete protocol that performs a security-related function and applies cryptographic methods.A protocol describes how the algorithms should be used...
s. They are generally used in modes of operation similar to the block modes described here. As with all protocols, to be cryptographically secure, care must be taken to build them correctly.
There are several schemes which use a block cipher to build a cryptographic hash function
Cryptographic hash function
A cryptographic hash function is a deterministic procedure that takes an arbitrary block of data and returns a fixed-size bit string, the hash value, such that an accidental or intentional change to the data will change the hash value...
. See one-way compression function for descriptions of several such methods.
Cryptographically secure pseudorandom number generator
Cryptographically secure pseudorandom number generator
A cryptographically secure pseudo-random number generator is a pseudo-random number generator with properties that make it suitable for use in cryptography.Many aspects of cryptography require random numbers, for example:...
s (CSPRNGs) can also be built using block ciphers.
Message authentication code
Message authentication code
In cryptography, a message authentication code is a short piece of information used to authenticate a message.A MAC algorithm, sometimes called a keyed hash function, accepts as input a secret key and an arbitrary-length message to be authenticated, and outputs a MAC...
s (MACs) are often built from block ciphers. CBC-MAC
CBC-MAC
In cryptography, a cipher block chaining message authentication code , is a technique for constructing a message authentication code from a block cipher. The message is encrypted with some block cipher algorithm in CBC mode to create a chain of blocks such that each block depends on the proper...
, OMAC
One-key MAC
OMAC is a message authentication code constructed from a block cipher much like the PMAC algorithm.Officially there are two OMAC algorithms which are both essentially the same except for a small tweak....
and PMAC
PMAC (cryptography)
PMAC, which stands for Parallelizable MAC, is a message authentication code algorithm. It was created by Phillip Rogaway ....
are examples.
Authenticated encryption
Authenticated encryption
Authenticated Encryption is a block cipher mode of operation which simultaneously provides confidentiality, integrity and authenticity assurances on the data. It became readily apparent that securely compositing a confidentiality mode with an authentication mode could be error prone and difficult...
also uses block ciphers as components. It means to both encrypt and MAC at the same time. That is to both provide confidentiality
Confidentiality
Confidentiality is an ethical principle associated with several professions . In ethics, and in law and alternative forms of legal resolution such as mediation, some types of communication between a person and one of these professionals are "privileged" and may not be discussed or divulged to...
and authentication
Authentication
Authentication is the act of confirming the truth of an attribute of a datum or entity...
. IAPM
IAPM mode
Integrity Aware Parallelizable Mode is a mode of operation for cryptographic block ciphers. As its name implies, it allows for a parallel mode of operation for very high throughput.-Encryption and authentication:...
, CCM
CCM mode
CCM mode is a mode of operation for cryptographic block ciphers. It is an authenticated encryption algorithm designed to provide both authentication and confidentiality. CCM mode is only defined for block ciphers with a block length of 128 bits...
, CWC
CWC mode
In cryptography, CWC Mode is an AEAD block cipher mode of operation that provides both encryption and built-in message integrity, similar to CCM and OCB modes. Designed by Tadayoshi Kohno, John Viega and Doug Whiting, NIST is CWC mode for standardization...
, EAX
EAX mode
EAX mode is a mode of operation for cryptographic block ciphers. It is an Authenticated Encryption with Associated Data algorithm designed to simultaneously provide both authentication and privacy of the message with a two-pass scheme, one pass for achieving privacy and one for authenticity for...
, GCM
Galois/Counter Mode
Galois/Counter Mode is a mode of operation for symmetric key cryptographic block ciphers that has been widely adopted because of its efficiency and performance...
and OCB
OCB mode
OCB mode is a mode of operation for cryptographic block ciphers.-Encryption and authentication:It was designed to provide both authentication and privacy. It is essentially a scheme for integrating a Message Authentication Code into the operation of a block cipher...
are such authenticated encryption modes.
See also
- Disk encryptionDisk encryptionDisk encryption is a special case of data at rest protection when the storage media is a sector-addressable device . This article presents cryptographic aspects of the problem...
- Message authentication codeMessage authentication codeIn cryptography, a message authentication code is a short piece of information used to authenticate a message.A MAC algorithm, sometimes called a keyed hash function, accepts as input a secret key and an arbitrary-length message to be authenticated, and outputs a MAC...
- Authenticated encryptionAuthenticated encryptionAuthenticated Encryption is a block cipher mode of operation which simultaneously provides confidentiality, integrity and authenticity assurances on the data. It became readily apparent that securely compositing a confidentiality mode with an authentication mode could be error prone and difficult...
- One-way compression function

