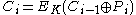Disk encryption
Encyclopedia
Disk encryption is a special case of data at rest protection when the storage media is a sector-addressable device (e.g., a hard disk). This article presents cryptographic aspects of the problem. For discussion of different software packages and hardware devices devoted to this problem see disk encryption software
and disk encryption hardware
.
The first property requires defining an adversary
with respect to whom the data is being kept confidential. The strongest adversaries studied in the field of disk encryption have these abilities:
A method provides good confidentiality if the only information such an adversary can determine over time is whether the data in a sector has or has not changed since the last time they looked.
The second property requires dividing the disk into several sectors, usually 512 bytes (4096 bits) long, which are encrypted and decrypted independently of each other. In turn, if the data is to stay confidential, the encryption method must be tweakable – no two sectors should be processed in exactly the same way. Otherwise, the adversary could decrypt any sector of the disk by copying it to an unused sector of the disk and requesting its decryption.
The third property is generally noncontroversial. However, it indirectly prohibits the use of stream ciphers, since stream ciphers require, for their security, that the same initial state not be used twice (which would be the case if a sector is updated with different data); thus this would require an encryption method to store separate initial states for every sector on disk – seemingly a clear waste of space. The alternative – a block cipher
– is limited to a certain block size (usually 128 or 256 bits). Because of this, disk encryption chiefly studies chaining modes
, which expand the encryption block length to cover a whole disk sector
. The considerations already listed make several well-known chaining modes unsuitable: ECB mode, which cannot be tweaked, and modes that turn block ciphers into stream ciphers, such as the CTR mode.
These three properties do not provide any assurance of disk integrity – that is, they don't tell you whether an adversary has been modifying your ciphertext. In part, this is because an absolute assurance of disk integrity is impossible: no matter what, an adversary could always revert the entire disk to a prior state, circumventing any such checks. If some non-absolute level of disk integrity is desired, it can be achieved within the encrypted disk on a file-by-file basis using message authentication codes.
Since there isn't a "previous block's ciphertext" for the first block, an initialization vector
(IV) must be used as . This, in turn, makes CBC tweakable in some ways.
. This, in turn, makes CBC tweakable in some ways.
CBC suffers from some problems. For example, if the IVs are predictable an adversary can manage to store a file specially created to zero out the IV, it is possible to leave a "watermark" on the disk, proving that the specially created file is, indeed, stored on disk. The exact method of constructing the watermark depends on the exact function providing the IVs; but the general recipe is to create two encrypted sectors which have identical first blocks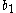 and
and 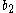 ; these two are then related to each other by
; these two are then related to each other by 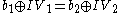 . Thus, when these two blocks are encrypted, they both encrypt to the same thing, leaving a watermark on the disk. The exact pattern of "same-different-same-different" on disk can then be altered to make the watermark unique to a given file.
. Thus, when these two blocks are encrypted, they both encrypt to the same thing, leaving a watermark on the disk. The exact pattern of "same-different-same-different" on disk can then be altered to make the watermark unique to a given file.
To protect against the watermarking attack, a cipher or a hash function is used to generate the IVs from the key and the current sector number, so that an adversary cannot predict them. In particular, the ESSIV approach discussed below uses a block cipher in CTR mode to generate the IVs.
Whereas a purpose of a usual block cipher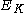 is to mimic a random permutation for any secret key
is to mimic a random permutation for any secret key 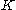 , the purpose of tweakable encryption
, the purpose of tweakable encryption  is to mimic a random permutation for any secret key
is to mimic a random permutation for any secret key  and any known tweak
and any known tweak 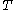 . The tweakable narrow-block encryption (LRW) is an instantiation of the mode of operations introduced by Liskov, Rivest, and Wagner (see Theorem 2). This mode uses two keys:
. The tweakable narrow-block encryption (LRW) is an instantiation of the mode of operations introduced by Liskov, Rivest, and Wagner (see Theorem 2). This mode uses two keys: 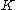 is the key for the block cipher and
is the key for the block cipher and 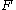 is an additional key of the same size as block. For example, for AES with a 256-bit key,
is an additional key of the same size as block. For example, for AES with a 256-bit key,  is a 256-bit number and
is a 256-bit number and 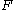 is a 128-bit number. Encrypting block
is a 128-bit number. Encrypting block 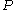 with logical index (tweak)
with logical index (tweak) 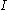 uses the following formula:
uses the following formula: 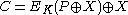 , where
, where 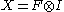 . Here multiplication
. Here multiplication  and addition
and addition  are performed
are performed
in the finite field (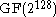 for AES). With some precomputation, only a single multiplication per sector is required (note that addition in a binary finite field is a simple bitwise addition, also known as xor):
for AES). With some precomputation, only a single multiplication per sector is required (note that addition in a binary finite field is a simple bitwise addition, also known as xor): 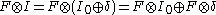 , where
, where 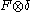 are precomputed for all possible values of
are precomputed for all possible values of 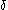 . This mode of operation needs only a single encryption per block and protects against all the above attacks except a minor leak: if the user changes a single plaintext block in a sector then only a single ciphertext block changes. (Note that this is not the same leak the ECB mode has: with LRW mode equal plaintexts in different positions are encrypted to different ciphertexts.)
. This mode of operation needs only a single encryption per block and protects against all the above attacks except a minor leak: if the user changes a single plaintext block in a sector then only a single ciphertext block changes. (Note that this is not the same leak the ECB mode has: with LRW mode equal plaintexts in different positions are encrypted to different ciphertexts.)
Some security concerns exist with LRW, and this mode of operation has now been replaced by XTS.
LRW is employed by Bestcrypt
and supported as an option for dm-crypt
and FreeOTFE
disk encryption systems.
), was designed by Rogaway to allow efficient processing of consecutive blocks (with respect to the cipher used) within one data unit (e.g. a disk sector). The tweak is represented as a combination of the sector address and index of the block inside the sector (the original XEX mode proposed by Rogaway allows to have several indexes). To encrypt block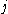 in sector
in sector 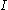 , the following formula is used
, the following formula is used 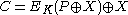 , where
, where 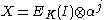 and
and  is the primitive element of
is the primitive element of  defined by polynomial
defined by polynomial  , i.e. the number "2".
, i.e. the number "2".
The basic blocks of the LRW mode (AES cipher and Galois field multiplication) are the same as the ones used in the Galois/Counter Mode
(GCM) thus permitting a compact implementation of the universal LRW/XEX/GCM hardware.
(CTS). Ciphertext stealing provides support for sectors with size not divisible by block size, for example, 520-byte sectors and 16-byte blocks. XTS-AES was standardized on 2007-12-19 as IEEE P1619
.
On January 27, 2010, NIST released Special Publication (SP) 800-38E in final form. SP 800-38E is a recommendation for the XTS-AES mode of operation, as standardized by IEEE Std 1619-2007, for cryptographic modules. The publication approves the XTS-AES mode of the AES algorithm by reference to the IEEE Std 1619-2007, subject to one additional requirement, which limits the maximum size of each encrypted data unit (typically a sector
or disk block
) to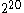 AES blocks. According to SP 800-38E, "In the absence of authentication or access control, XTS-AES provides more protection than the other approved confidentiality-only modes against unauthorized manipulation of the encrypted data."
AES blocks. According to SP 800-38E, "In the absence of authentication or access control, XTS-AES provides more protection than the other approved confidentiality-only modes against unauthorized manipulation of the encrypted data."
As of September 2010, XTS is supported by BestCrypt
, dm-crypt
, FreeOTFE
, TrueCrypt
, DiskCryptor
, FreeBSD
and OpenBSD
softraid disk encryption software (also native in Mac OS X Lion
's FileVault
), in hardware-based media encryption devices by the SPYRUS Hydra PC Digital Attaché and the Kingston DataTraveler 5000.
CMC, introduced by Halevi and Rogaway, stands for CBC-mask-CBC: the whole sector encrypted in CBC mode (with ), the ciphertext is masked by xoring with
), the ciphertext is masked by xoring with 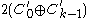 , and re-encrypted in CBC mode starting from the last block. When the underlying block cipher is a strong pseudorandom permutation
, and re-encrypted in CBC mode starting from the last block. When the underlying block cipher is a strong pseudorandom permutation
(PRP) then on the sector level the scheme is a tweakable PRP. One problem is that in order to decrypt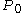 one must sequentially pass over all the data twice.
one must sequentially pass over all the data twice.
In order to solve this problem, Halevi and Rogaway introduced a parallelizable variant called EME (ECB-mask-ECB). It works in the following way:
Note that unlike LRW and CMC there is only a single key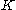 .
.
CMC and EME were considered for standardization by SISWG. CMC was rejected for technical considerations. EME is patented, and so is not favored to be a primary supported mode.
s for block encryption
to use in disk encryption. The usual methods for generating IVs are predictable sequences of numbers based on, for example, time stamp or sector number, and permits certain attacks such as a watermarking attack
. ESSIV prevents such attacks by generating IVs from a combination of the sector number with the hash of the key. It is the combination with the key in form of a hash
that makes the IV unpredictable.
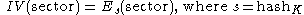
ESSIV was designed by Clemens Fruhwirth and has been integrated into the Linux kernel
since version 2.6.10, though a similar scheme has been used to generate IVs for OpenBSD's swap encryption since 2000.
ESSIV is supported as an option by the dm-crypt
and FreeOTFE
disk encryption systems.
Disk encryption software
To protect confidentiality of the data stored on a computer disk a computer security technique called disk encryption is used. This article discusses software that is used to implement the technique...
and disk encryption hardware
Disk encryption hardware
To protect confidentiality of the data stored on a computer disk a computer security technique called disk encryption is used. This article discusses hardware which is used to implement the technique...
.
Problem definition
Disk encryption methods aim to provide three distinct properties:- The data on the disk should remain confidential
- Data retrieval and storage should both be fast operations, no matter where on the disk the data is stored.
- The encryption method should not waste disk space (i.e., the amount of storage used for encrypted data should not be significantly larger than the size of plaintextPlaintextIn cryptography, plaintext is information a sender wishes to transmit to a receiver. Cleartext is often used as a synonym. Before the computer era, plaintext most commonly meant message text in the language of the communicating parties....
)
The first property requires defining an adversary
Adversary (cryptography)
In cryptography, an adversary is a malicious entity whose aim is to prevent the users of the cryptosystem from achieving their goal...
with respect to whom the data is being kept confidential. The strongest adversaries studied in the field of disk encryption have these abilities:
- they can read the raw contents of the disk at any time;
- they can request the disk to encrypt and store arbitrary files of their choosing;
- and they can modify unused sectors on the disk and then request their decryption.
A method provides good confidentiality if the only information such an adversary can determine over time is whether the data in a sector has or has not changed since the last time they looked.
The second property requires dividing the disk into several sectors, usually 512 bytes (4096 bits) long, which are encrypted and decrypted independently of each other. In turn, if the data is to stay confidential, the encryption method must be tweakable – no two sectors should be processed in exactly the same way. Otherwise, the adversary could decrypt any sector of the disk by copying it to an unused sector of the disk and requesting its decryption.
The third property is generally noncontroversial. However, it indirectly prohibits the use of stream ciphers, since stream ciphers require, for their security, that the same initial state not be used twice (which would be the case if a sector is updated with different data); thus this would require an encryption method to store separate initial states for every sector on disk – seemingly a clear waste of space. The alternative – a block cipher
Block cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
– is limited to a certain block size (usually 128 or 256 bits). Because of this, disk encryption chiefly studies chaining modes
Block cipher modes of operation
In cryptography, modes of operation is the procedure of enabling the repeated and secure use of a block cipher under a single key.A block cipher by itself allows encryption only of a single data block of the cipher's block length. When targeting a variable-length message, the data must first be...
, which expand the encryption block length to cover a whole disk sector
Disk sector
In computer disk storage, a sector is a subdivision of a track on a magnetic disk or optical disc. Each sector stores a fixed amount of user data. Traditional formatting of these storage media provides space for 512 bytes or 2048 bytes of user-accessible data per sector...
. The considerations already listed make several well-known chaining modes unsuitable: ECB mode, which cannot be tweaked, and modes that turn block ciphers into stream ciphers, such as the CTR mode.
These three properties do not provide any assurance of disk integrity – that is, they don't tell you whether an adversary has been modifying your ciphertext. In part, this is because an absolute assurance of disk integrity is impossible: no matter what, an adversary could always revert the entire disk to a prior state, circumventing any such checks. If some non-absolute level of disk integrity is desired, it can be achieved within the encrypted disk on a file-by-file basis using message authentication codes.
Block cipher-based modes
All block cipher-based methods make use of so-called modes, which allow encrypting larger amounts of data than the ciphers' block-size (typically 128 bits). Modes are therefore rules on how to repeatedly apply the ciphers' single-block operations.CBC
Cipher block chaining (CBC) is a common chaining mode in which the previous block's ciphertext is xored with the current block's plaintext before encryption:Since there isn't a "previous block's ciphertext" for the first block, an initialization vector
Initialization vector
In cryptography, an initialization vector is a fixed-size input to a cryptographic primitive that is typically required to be random or pseudorandom...
(IV) must be used as
 . This, in turn, makes CBC tweakable in some ways.
. This, in turn, makes CBC tweakable in some ways.CBC suffers from some problems. For example, if the IVs are predictable an adversary can manage to store a file specially created to zero out the IV, it is possible to leave a "watermark" on the disk, proving that the specially created file is, indeed, stored on disk. The exact method of constructing the watermark depends on the exact function providing the IVs; but the general recipe is to create two encrypted sectors which have identical first blocks
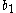 and
and 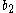 ; these two are then related to each other by
; these two are then related to each other by 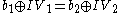 . Thus, when these two blocks are encrypted, they both encrypt to the same thing, leaving a watermark on the disk. The exact pattern of "same-different-same-different" on disk can then be altered to make the watermark unique to a given file.
. Thus, when these two blocks are encrypted, they both encrypt to the same thing, leaving a watermark on the disk. The exact pattern of "same-different-same-different" on disk can then be altered to make the watermark unique to a given file.To protect against the watermarking attack, a cipher or a hash function is used to generate the IVs from the key and the current sector number, so that an adversary cannot predict them. In particular, the ESSIV approach discussed below uses a block cipher in CTR mode to generate the IVs.
LRW
In order to prevent such elaborate attacks, different modes of operation were introduced: tweakable narrow-block encryption (LRW and XEX) and wide-block encryption (CMC and EME).Whereas a purpose of a usual block cipher
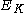 is to mimic a random permutation for any secret key
is to mimic a random permutation for any secret key 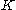 , the purpose of tweakable encryption
, the purpose of tweakable encryption  is to mimic a random permutation for any secret key
is to mimic a random permutation for any secret key  and any known tweak
and any known tweak 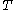 . The tweakable narrow-block encryption (LRW) is an instantiation of the mode of operations introduced by Liskov, Rivest, and Wagner (see Theorem 2). This mode uses two keys:
. The tweakable narrow-block encryption (LRW) is an instantiation of the mode of operations introduced by Liskov, Rivest, and Wagner (see Theorem 2). This mode uses two keys: 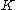 is the key for the block cipher and
is the key for the block cipher and 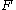 is an additional key of the same size as block. For example, for AES with a 256-bit key,
is an additional key of the same size as block. For example, for AES with a 256-bit key,  is a 256-bit number and
is a 256-bit number and 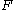 is a 128-bit number. Encrypting block
is a 128-bit number. Encrypting block 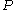 with logical index (tweak)
with logical index (tweak) 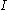 uses the following formula:
uses the following formula: 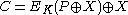 , where
, where 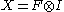 . Here multiplication
. Here multiplication  and addition
and addition  are performed
are performedFinite field arithmetic
Arithmetic in a finite field is different from standard integer arithmetic. There are a limited number of elements in the finite field; all operations performed in the finite field result in an element within that field....
in the finite field (
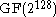 for AES). With some precomputation, only a single multiplication per sector is required (note that addition in a binary finite field is a simple bitwise addition, also known as xor):
for AES). With some precomputation, only a single multiplication per sector is required (note that addition in a binary finite field is a simple bitwise addition, also known as xor): 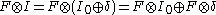 , where
, where 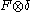 are precomputed for all possible values of
are precomputed for all possible values of 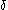 . This mode of operation needs only a single encryption per block and protects against all the above attacks except a minor leak: if the user changes a single plaintext block in a sector then only a single ciphertext block changes. (Note that this is not the same leak the ECB mode has: with LRW mode equal plaintexts in different positions are encrypted to different ciphertexts.)
. This mode of operation needs only a single encryption per block and protects against all the above attacks except a minor leak: if the user changes a single plaintext block in a sector then only a single ciphertext block changes. (Note that this is not the same leak the ECB mode has: with LRW mode equal plaintexts in different positions are encrypted to different ciphertexts.)Some security concerns exist with LRW, and this mode of operation has now been replaced by XTS.
LRW is employed by Bestcrypt
BestCrypt
BestCrypt is a commercial disk encryption program for Windows and Linux, developed by Jetico.-Features:* BestCrypt can create and mount an encrypted virtual drive using AES, Blowfish, Twofish, CAST, and various other encryption methods...
and supported as an option for dm-crypt
Dm-crypt
dm-crypt is a transparent disk encryption subsystem in Linux kernel versions 2.6 and later and in DragonFly BSD. It is part of the device mapper infrastructure, and uses cryptographic routines from the kernel's Crypto API...
and FreeOTFE
FreeOTFE
FreeOTFE is an open source on-the-fly disk encryption computer program for PCs running Microsoft Windows, and personal digital assistants running Windows Mobile . It creates virtual drives, or disks, to which anything written is automatically encrypted before being stored on a computer's hard or...
disk encryption systems.
XEX
Another tweakable encryption mode XEX (Xor-Encrypt-XorKey whitening
In cryptography, key whitening is a technique intended to increase the security of an iterated block cipher. It consists of steps that combine the data with portions of the key before the first round and after the last round of encryption.The first block cipher to use a form of key whitening is...
), was designed by Rogaway to allow efficient processing of consecutive blocks (with respect to the cipher used) within one data unit (e.g. a disk sector). The tweak is represented as a combination of the sector address and index of the block inside the sector (the original XEX mode proposed by Rogaway allows to have several indexes). To encrypt block
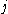 in sector
in sector 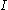 , the following formula is used
, the following formula is used 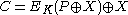 , where
, where 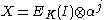 and
and  is the primitive element of
is the primitive element of  defined by polynomial
defined by polynomial  , i.e. the number "2".
, i.e. the number "2".The basic blocks of the LRW mode (AES cipher and Galois field multiplication) are the same as the ones used in the Galois/Counter Mode
Galois/Counter Mode
Galois/Counter Mode is a mode of operation for symmetric key cryptographic block ciphers that has been widely adopted because of its efficiency and performance...
(GCM) thus permitting a compact implementation of the universal LRW/XEX/GCM hardware.
XTS
XTS is XEX-based Tweaked Codebook mode (TCB) with ciphertext stealingCiphertext stealing
In cryptography, ciphertext stealing is a general method of using a block cipher mode of operation that allows for processing of messages that are not evenly divisible into blocks without resulting in any expansion of the ciphertext, at the cost of slightly increased complexity.-General...
(CTS). Ciphertext stealing provides support for sectors with size not divisible by block size, for example, 520-byte sectors and 16-byte blocks. XTS-AES was standardized on 2007-12-19 as IEEE P1619
IEEE P1619
IEEE P1619 is an Institute of Electrical and Electronics Engineers standardization project for encryption of stored data, but more generically refers to the work of the IEEE P1619 Security in Storage Working Group , which includes a family of standards for protection of stored data and for the...
.
On January 27, 2010, NIST released Special Publication (SP) 800-38E in final form. SP 800-38E is a recommendation for the XTS-AES mode of operation, as standardized by IEEE Std 1619-2007, for cryptographic modules. The publication approves the XTS-AES mode of the AES algorithm by reference to the IEEE Std 1619-2007, subject to one additional requirement, which limits the maximum size of each encrypted data unit (typically a sector
Disk sector
In computer disk storage, a sector is a subdivision of a track on a magnetic disk or optical disc. Each sector stores a fixed amount of user data. Traditional formatting of these storage media provides space for 512 bytes or 2048 bytes of user-accessible data per sector...
or disk block
Block (data storage)
In computing , a block is a sequence of bytes or bits, having a nominal length . Data thus structured are said to be blocked. The process of putting data into blocks is called blocking. Blocking is used to facilitate the handling of the data-stream by the computer program receiving the data...
) to
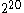 AES blocks. According to SP 800-38E, "In the absence of authentication or access control, XTS-AES provides more protection than the other approved confidentiality-only modes against unauthorized manipulation of the encrypted data."
AES blocks. According to SP 800-38E, "In the absence of authentication or access control, XTS-AES provides more protection than the other approved confidentiality-only modes against unauthorized manipulation of the encrypted data."As of September 2010, XTS is supported by BestCrypt
BestCrypt
BestCrypt is a commercial disk encryption program for Windows and Linux, developed by Jetico.-Features:* BestCrypt can create and mount an encrypted virtual drive using AES, Blowfish, Twofish, CAST, and various other encryption methods...
, dm-crypt
Dm-crypt
dm-crypt is a transparent disk encryption subsystem in Linux kernel versions 2.6 and later and in DragonFly BSD. It is part of the device mapper infrastructure, and uses cryptographic routines from the kernel's Crypto API...
, FreeOTFE
FreeOTFE
FreeOTFE is an open source on-the-fly disk encryption computer program for PCs running Microsoft Windows, and personal digital assistants running Windows Mobile . It creates virtual drives, or disks, to which anything written is automatically encrypted before being stored on a computer's hard or...
, TrueCrypt
TrueCrypt
TrueCrypt is a software application used for on-the-fly encryption . It is free and open source. It can create a virtual encrypted disk within a file or encrypt a partition or the entire storage device .- Operating systems :TrueCrypt supports Microsoft Windows, Mac OS X, and...
, DiskCryptor
DiskCryptor
DiskCryptor is the first open source full disk encryption system for MS Windows that allows the encryption of an entire PC's harddrive or individual partitions – including the ability to encrypt the partition and disk on which the OS is installed....
, FreeBSD
FreeBSD
FreeBSD is a free Unix-like operating system descended from AT&T UNIX via BSD UNIX. Although for legal reasons FreeBSD cannot be called “UNIX”, as the direct descendant of BSD UNIX , FreeBSD’s internals and system APIs are UNIX-compliant...
and OpenBSD
OpenBSD
OpenBSD is a Unix-like computer operating system descended from Berkeley Software Distribution , a Unix derivative developed at the University of California, Berkeley. It was forked from NetBSD by project leader Theo de Raadt in late 1995...
softraid disk encryption software (also native in Mac OS X Lion
Mac OS X Lion
Mac OS X Lion is the eighth and current major release of Mac OS X, Apple's desktop and server operating system for Macintosh computers....
's FileVault
FileVault
FileVault is a system which encrypts files on a Macintosh computer. It can be found in the Mac OS X v10.4 "Tiger" operating system and later....
), in hardware-based media encryption devices by the SPYRUS Hydra PC Digital Attaché and the Kingston DataTraveler 5000.
Issues with XTS
XTS makes use of two different keys, usually generated by splitting the supplied block cipher's key in half, which is the major difference to XEX, without adding any additional security, but complicating the process. According to this source, the reason for this seems to be rooted in a misinterpretation of the original XEX-paper. Because of the splitting, users wanting AES 256 and AES 128 encryption will need to choose key sizes of 512 bits and 256 bits respectively.CMC and EME
CMC and EME protect even against the minor leak mentioned above for LRW. Unfortunately, the price is a twofold degradation of performance: each block must be encrypted twice; many consider this to be too high a cost, since the same leak on a sector level is unavoidable anyway.CMC, introduced by Halevi and Rogaway, stands for CBC-mask-CBC: the whole sector encrypted in CBC mode (with
 ), the ciphertext is masked by xoring with
), the ciphertext is masked by xoring with 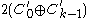 , and re-encrypted in CBC mode starting from the last block. When the underlying block cipher is a strong pseudorandom permutation
, and re-encrypted in CBC mode starting from the last block. When the underlying block cipher is a strong pseudorandom permutationPseudorandom permutation
In cryptography, the term pseudorandom permutation, abbreviated PRP, refers to a function that cannot be distinguished from a random permutation with practical effort.A pseudorandom permutation family is a collection of pseudorandom permutations,...
(PRP) then on the sector level the scheme is a tweakable PRP. One problem is that in order to decrypt
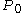 one must sequentially pass over all the data twice.
one must sequentially pass over all the data twice.In order to solve this problem, Halevi and Rogaway introduced a parallelizable variant called EME (ECB-mask-ECB). It works in the following way:
- the plaintexts are xored with
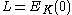 , shifted by different amount to the left, and are encrypted:
, shifted by different amount to the left, and are encrypted: 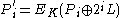 ;
; - the mask is calculated:
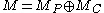 , where
, where 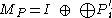 and
and 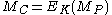 ;
; - intermediate ciphertexts are masked:
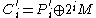 for
for 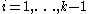 and
and 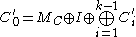 ;
; - the final ciphertexts are calculated:
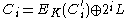 for
for  .
.
Note that unlike LRW and CMC there is only a single key
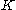 .
.CMC and EME were considered for standardization by SISWG. CMC was rejected for technical considerations. EME is patented, and so is not favored to be a primary supported mode.
ESSIV
Encrypted Salt-Sector Initialization Vector (ESSIV) is a method for generating initialization vectorInitialization vector
In cryptography, an initialization vector is a fixed-size input to a cryptographic primitive that is typically required to be random or pseudorandom...
s for block encryption
Block cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
to use in disk encryption. The usual methods for generating IVs are predictable sequences of numbers based on, for example, time stamp or sector number, and permits certain attacks such as a watermarking attack
Watermarking attack
In cryptography, a watermarking attack is an attack on disk encryption methods where the presence of a specially crafted piece of data can be detected by an attacker without knowing the encryption key.-Problem description:...
. ESSIV prevents such attacks by generating IVs from a combination of the sector number with the hash of the key. It is the combination with the key in form of a hash
Cryptographic hash function
A cryptographic hash function is a deterministic procedure that takes an arbitrary block of data and returns a fixed-size bit string, the hash value, such that an accidental or intentional change to the data will change the hash value...
that makes the IV unpredictable.
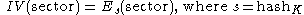
ESSIV was designed by Clemens Fruhwirth and has been integrated into the Linux kernel
Linux kernel
The Linux kernel is an operating system kernel used by the Linux family of Unix-like operating systems. It is one of the most prominent examples of free and open source software....
since version 2.6.10, though a similar scheme has been used to generate IVs for OpenBSD's swap encryption since 2000.
ESSIV is supported as an option by the dm-crypt
Dm-crypt
dm-crypt is a transparent disk encryption subsystem in Linux kernel versions 2.6 and later and in DragonFly BSD. It is part of the device mapper infrastructure, and uses cryptographic routines from the kernel's Crypto API...
and FreeOTFE
FreeOTFE
FreeOTFE is an open source on-the-fly disk encryption computer program for PCs running Microsoft Windows, and personal digital assistants running Windows Mobile . It creates virtual drives, or disks, to which anything written is automatically encrypted before being stored on a computer's hard or...
disk encryption systems.
See also
- Data remanenceData remanenceData remanence is the residual representation of data that remains even after attempts have been made to remove or erase the data. This residue may result from data being left intact by a nominal file deletion operation, by reformatting of storage media that does not remove data previously written...
- Cold boot attackCold boot attackIn cryptography, a cold boot attack is a type of side channel attack in which an attacker with physical access to a computer is able to retrieve encryption keys from a running operating system after using a cold reboot to restart the machine from a completely "off" state...
- Disk encryption softwareDisk encryption softwareTo protect confidentiality of the data stored on a computer disk a computer security technique called disk encryption is used. This article discusses software that is used to implement the technique...
- Disk encryption hardwareDisk encryption hardwareTo protect confidentiality of the data stored on a computer disk a computer security technique called disk encryption is used. This article discusses hardware which is used to implement the technique...
- Full disk encryptionFull disk encryptionDisk encryption uses disk encryption software or hardware to encrypt every bit of data that goes on a disk or disk volume. Disk encryption prevents unauthorized access to data storage. The term "full disk encryption" is often used to signify that everything on a disk is encrypted, including the...
- IEEE P1619IEEE P1619IEEE P1619 is an Institute of Electrical and Electronics Engineers standardization project for encryption of stored data, but more generically refers to the work of the IEEE P1619 Security in Storage Working Group , which includes a family of standards for protection of stored data and for the...
, standardization project for encryption of the storage data
Endnotes
- Latest SISWG and IEEE P1619 drafts and meeting information are on the P1619 home page http://siswg.net/.
- M. Liskov, R. Rivest, and D. Wagner. Tweakable block ciphers http://theory.lcs.mit.edu/~rivest/LiskovRivestWagner-TweakableBlockCiphers.pdf, CRYPTO '02 (LNCS, volume 2442), 2002.
- P. Rogaway, Block cipher mode of operation for constructing a wide-blocksize block cipher from a conventional block cipher, US Patent Application 20040131182 A1, http://appft1.uspto.gov/netacgi/nph-Parser?Sect1=PTO2&Sect2=HITOFF&p=1&u=%2Fnetahtml%2FPTO%2Fsearch-bool.html&r=1&f=G&l=50&co1=AND&d=PG01&s1=rogaway.IN.&OS=IN/rogaway
Papers
- S. Halevi and P. Rogaway, A Tweakable Enciphering Mode, CRYPTO '03 (LNCS, volume 2729), 2003.
- S. Halevi and P. Rogaway, A Parallelizable Enciphering Mode http://www.cs.ucdavis.edu/~rogaway/papers/eme.ps, 2003.
- Standard Architecture for Encrypted Shared Storage Media, IEEE Project 1619 (P1619), https://siswg.net/index.php?option=com_content&task=view&id=38&Itemid=73.
- SISWG, Draft Proposal for Key Backup Format http://www.siswg.org/docs/KeyBackup-10-04-2004.pdf, 2004.
- SISWG, Draft Proposal for Tweakable Wide-block Encryption http://www.siswg.org/docs/EME-AES-03-22-2004.pdf, 2004.
- James Hughes, Encrypted Storage — Challenges and Methods http://www.dtc.umn.edu/resources/hughes1.pdf
External links
- Security in Storage Working Group SISWG.