Identity management
Encyclopedia
- IdM redirects here. It can also mean Middle-of-the-Road ItalyMiddle-of-the-Road ItalyMiddle-of-the-Road Italy was an Italian centrist political grouping founded in 2006 by Marco Follini, Senate member and former leader of the Union of Christian and Centre Democrats , and Riccardo Conti, member of the Chamber of Deputies...
.
Identity management (or ID management, or simply IdM) is a broad administrative area that deals with identifying individuals in a system (such as a country, a network, or an organization) and controlling access to the resources in that system by placing restrictions on the established identities of the individuals.
Identity management is multidisciplinary and covers many dimensions, such as:
- Technical – Employs identity management systemsIdentity management systemsAn identity management system refers to an information system, or to a set of technologies that can be used to support the management of identities.An identity management system:# Establishes the identity...
(identification, implementation, administration and termination of identities with access to information systems, buildings and data within an organization). - Legal – Deals with legislation for data protection.
- Police – Deals with identity theftIdentity theftIdentity theft is a form of stealing another person's identity in which someone pretends to be someone else by assuming that person's identity, typically in order to access resources or obtain credit and other benefits in that person's name...
. - Social and humanity – Deals with issues such as privacyPrivacyPrivacy is the ability of an individual or group to seclude themselves or information about themselves and thereby reveal themselves selectively...
. - Security – Manages elements such as access control.
- Organizations – Hierarchies and divisions of access.
History
Identity management (IdM) is a term related to how humans are identified and authorizedAuthorization
Authorization is the function of specifying access rights to resources, which is related to information security and computer security in general and to access control in particular. More formally, "to authorize" is to define access policy...
across computer network
Computer network
A computer network, often simply referred to as a network, is a collection of hardware components and computers interconnected by communication channels that allow sharing of resources and information....
s. It covers issues such as how users are given an identity, the protection of that identity, and the technologies supporting that protection (e.g., network protocols, digital certificates
Public key certificate
In cryptography, a public key certificate is an electronic document which uses a digital signature to bind a public key with an identity — information such as the name of a person or an organization, their address, and so forth...
, password
Password
A password is a secret word or string of characters that is used for authentication, to prove identity or gain access to a resource . The password should be kept secret from those not allowed access....
s, etc.).
Digital identity: Personal identifying information (PII) selectively exposed over a network. See OECD and NIST guidelines on protecting PII and the risk of identity theft
Identity theft
Identity theft is a form of stealing another person's identity in which someone pretends to be someone else by assuming that person's identity, typically in order to access resources or obtain credit and other benefits in that person's name...
.
While the term management requires little explanation, the term identity is a more abstract concept that will always be difficult to define in a way that satisfies everyone. It is a concept that is fluid and contextual depending on a number of factors including culture.
Thus the term management is appended to "identity" to indicate that there is technological and best practice
Best practice
A best practice is a method or technique that has consistently shown results superior to those achieved with other means, and that is used as a benchmark...
framework around a somewhat intractable philosophical concept. Digital identity
Digital identity
Digital identity is the aspect of digital technology that is concerned with the mediation of people's experience of their own identity and the identity of other people and things...
can be interpreted as the codification of identity names and attributes of a physical instance in a way that facilitates processing. In each organization there is normally a role or department that is responsible for managing the schema of digital identities of their staff and their own objects, these represented by object identities or object identifiers (OID).
The SAML protocol is a prominent means used to exchange identity information between two identity domains. Other examples are listed on the Website of this project.
Perspectives on IdM
In the real-world context of engineering online systems, identity management can involve three perspectives:- The pure identity paradigm: Creation, management and deletion of identities without regard to access or entitlements;
- The user access (log-on) paradigm: For example: a smart cardSmart cardA smart card, chip card, or integrated circuit card , is any pocket-sized card with embedded integrated circuits. A smart card or microprocessor cards contain volatile memory and microprocessor components. The card is made of plastic, generally polyvinyl chloride, but sometimes acrylonitrile...
and its associated data used by a customer to log on to a service or services (a traditional view); - The service paradigm: A system that delivers personalized, role-based, online, on-demand, multimedia (content), presence-based services to users and their devices.
Pure identity paradigm
A general model of identityIdentity (philosophy)
In philosophy, identity, from , is the relation each thing bears just to itself. According to Leibniz's law two things sharing every attribute are not only similar, but are the same thing. The concept of sameness has given rise to the general concept of identity, as in personal identity and...
can be constructed from a small set of axiomatic principles, for example that all identities in a given abstract namespace
Namespace
In general, a namespace is a container that provides context for the identifiers it holds, and allows the disambiguation of homonym identifiers residing in different namespaces....
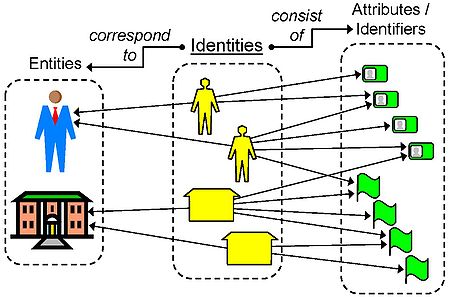
are unique and distinctive, or that such identities bear a specific relationship to corresponding entities in the real world. An axiomatic model of this kind can be considered to express "pure identity" in the sense that the model is not constrained by the context in which it is applied. In general, an entity can have multiple identities, and each identity can consist of multiple attributes or identifiers, some of which are shared and some of which are unique within a given name space. The diagram below illustrates the conceptual relationship between identities and the entities they represent, as well as between identities and the attributes they consist of.
Digital identity
Digital identity is the aspect of digital technology that is concerned with the mediation of people's experience of their own identity and the identity of other people and things...
, a given identity object consists of a finite set of properties
Property (philosophy)
In modern philosophy, logic, and mathematics a property is an attribute of an object; a red object is said to have the property of redness. The property may be considered a form of object in its own right, able to possess other properties. A property however differs from individual objects in that...
. These properties may be used to record information about the object, either for purposes external to the model itself or so as to assist the model operationally, for example in classification and retrieval. A "pure identity" model is strictly not concerned with the external semantics
Semantics
Semantics is the study of meaning. It focuses on the relation between signifiers, such as words, phrases, signs and symbols, and what they stand for, their denotata....
of these properties.
The most common departure from "pure identity" in practice occurs with properties intended to assure some aspect of identity, for example a digital signature
Digital signature
A digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender, and that it was not altered in transit...
or software token
Software token
A software token is a type of two-factor authentication security device that may be used to authorize the use of computer services. Software tokens are stored on a general-purpose electronic device such as a desktop computer, laptop, PDA, or mobile phone...
which the model may use internally to verify some aspect of the identity in satisfaction of an external purpose. To the extent that the model attempts to express these semantics internally, it is not a pure model.
Contrast this situation with properties which might be externally used for purposes of information security
Information security
Information security means protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction....
such as managing access or entitlement, but which are simply stored and retrieved, in other words not treated specially by the model. The absence of external semantics within the model qualifies it as a "pure identity" model.
Identity management, then, can be defined as a set of operations on a given identity model, or as a set of capabilities with reference to it. In practice, identity management is often used to express how identity information is to be provisioned
Provisioning
In telecommunication, provisioning is the process of preparing and equipping a network to allow it to provide services to its users. In NS/EP telecommunications services, "provisioning" equates to "initiation" and includes altering the state of an existing priority service or capability.In a...
and reconciled
Reconciliation (accounting)
In accounting, reconciliation refers to a process that compares two sets of records to make sure they are in agreement...
between multiple identity models.
User access paradigm
User access requires each user to assume a unique "digital identity" across applications and networked infrastructures, which enables access controls to be assigned and evaluate against this identity. Technically, the use of a unique identity across all systems ease the monitoring and verification of potential unauthorized access, and allows the organization to keep tabs of excessive privileges granted to any individual within the company. From the user lifecycle perspective, user access can be tracked from new hire, suspension to termination of employee.Service paradigm
In the service paradigm perspective, where organizations evolve their systems to the world of converged services, the scope of identity management becomes much larger, and its application more critical. The scope of identity management includes all the resources of the company deployed to deliver online services. These may include devices, network equipment, servers, portals, content, applications and/or products as well as a user's credentials, address books, preferences, entitlements and telephone numbers. See Service Delivery PlatformService Delivery Platform
In telecommunications, the term Service Delivery Platform usually refers to a set of components that provide a services delivery architecture for a type of service...
and Directory service
Directory service
A directory service is the software system that stores, organizes and provides access to information in a directory. In software engineering, a directory is a map between names and values. It allows the lookup of values given a name, similar to a dictionary...
.
, many organizations face a major clean-up in their systems if they are to bring identity coherence into their influence. Such coherence has become a prerequisite for delivering unified services to very large numbers of users on demand — cheaply, with security and single-customer viewing facilities.
Emerging fundamental points
- IdM provides significantly greater opportunities to online businesses beyond the process of authenticating and granting access to authorized users via cards, tokens and webWorld Wide WebThe World Wide Web is a system of interlinked hypertext documents accessed via the Internet...
access controlAccess controlAccess control refers to exerting control over who can interact with a resource. Often but not always, this involves an authority, who does the controlling. The resource can be a given building, group of buildings, or computer-based information system...
systems. - User-based IdM has started to evolve away from username/passwordPasswordA password is a secret word or string of characters that is used for authentication, to prove identity or gain access to a resource . The password should be kept secret from those not allowed access....
and web-access control systems toward those that embrace preferences, parental controls, entitlements, policy-based routingRoutingRouting is the process of selecting paths in a network along which to send network traffic. Routing is performed for many kinds of networks, including the telephone network , electronic data networks , and transportation networks...
, presence and loyalty schemeLoyalty programLoyalty programs are structured marketing efforts that reward, and therefore encourage, loyal buying behavior — behavior which is potentially beneficial to the firm....
s. - IdM provides the focus to deal with system-wide data quality and integrityData integrityData Integrity in its broadest meaning refers to the trustworthiness of system resources over their entire life cycle. In more analytic terms, it is "the representational faithfulness of information to the true state of the object that the information represents, where representational faithfulness...
issues often encountered by fragmented databases and workflowWorkflowA workflow consists of a sequence of connected steps. It is a depiction of a sequence of operations, declared as work of a person, a group of persons, an organization of staff, or one or more simple or complex mechanisms. Workflow may be seen as any abstraction of real work...
processes. - IdM embraces what the user actually gets in terms of products and services and how and when they acquire them. Therefore, IdM applies to the products and services of an organization, such as health, media, insurance, travel and government services. It is also applicable to means by which these products and services are provisioned and assigned to (or removed from) "entitled" users.
- IdM can deliver single-customer views that include the presence and location of the customer, single products and services as well as single IT infrastructure and network views to the respective parties. Accordingly, IdM relates intrinsically to information engineeringInformation engineeringInformation engineering or information engineering methodology in software engineering is an approach to designing and developing information systems.-Overview:...
, security and privacy. - IdM covers the machinery (system infrastructure components) that delivers such services because a system may assign the service of a user to: a particular network technology, content title, usage right, media server, mail server, soft switch, voice mailbox, product catalog set, security domain, billing system, CRMCustomer relationship managementCustomer relationship management is a widely implemented strategy for managing a company’s interactions with customers, clients and sales prospects. It involves using technology to organize, automate, and synchronize business processes—principally sales activities, but also those for marketing,...
, help deskHelp deskA help desk is an information and assistance resource that troubleshoots problems with computers or similar products. Corporations often provide help desk support to their customers via a toll-free number, website and e-mail. There are also in-house help desks geared toward providing the same kind...
etc. - It is equally important for users to correctly identify and authenticate service providers as it is for service providers to identify and authenticate users. This aspect has largely been ignored during the early development of identity management, but will have to be taken seriously in the future.
- Critical factors in IdM projects include consideration of the online services of an organization (what the users log on to) and how they are managed from an internal and customer self-care perspective.
Issues
The management of identity raises a certain number of issues, such as privacyPrivacy
Privacy is the ability of an individual or group to seclude themselves or information about themselves and thereby reveal themselves selectively...
issues that may lead to the implementation of a surveillance
Surveillance
Surveillance is the monitoring of the behavior, activities, or other changing information, usually of people. It is sometimes done in a surreptitious manner...
society , or risk related to the stealing of identity (identity theft
Identity theft
Identity theft is a form of stealing another person's identity in which someone pretends to be someone else by assuming that person's identity, typically in order to access resources or obtain credit and other benefits in that person's name...
).
The advent of the social web
Social Web
The social Web is a set of social relations that link people through the World Wide Web. The Social web encompasses how websites and software are designed and developed in order to support and foster social interaction. These online social interactions form the basis of much online activity...
, and in particular the important development of online social networking services, for which the management of their identities of their members represent a core element of these systems, also create a certain number of risks related to the disclosure of personal information , and in particular in losing an individual's privacy .
Addressing the identity issues
First, it should be noted that people, and in particular the young people (15-25), are well aware of the risks towards eID enabled services . More specifically young people:- are often very knowledgeable about these systems (web 2.0Web 2.0The term Web 2.0 is associated with web applications that facilitate participatory information sharing, interoperability, user-centered design, and collaboration on the World Wide Web...
) that they use frequently and for a long time - have a high level of perception of risk associated to these tools
Addressing these different issues may be done only by legislation or via the use of technical systems, but have to combine the different dimensions such as:
- legal. With the data protection legislation or human rightsHuman rightsHuman rights are "commonly understood as inalienable fundamental rights to which a person is inherently entitled simply because she or he is a human being." Human rights are thus conceived as universal and egalitarian . These rights may exist as natural rights or as legal rights, in both national...
legislation . - technical. Using for instance with the use of Privacy enhancing technologiesPrivacy enhancing technologiesPrivacy enhancing technologies is a general term for a set of computer tools, applications and mechanisms which - when integrated in online services or applications, or when used in conjunction with such services or applications - allow online users to protect the privacy of their personally...
. - security. Including socio-psychological aspects (social engineeringSocial engineering (security)Social engineering is commonly understood to mean the art of manipulating people into performing actions or divulging confidential information...
). - police (i.e. ForensicsForensicsForensic science is the application of a broad spectrum of sciences to answer questions of interest to a legal system. This may be in relation to a crime or a civil action...
).
Research
Research related to the management of identity covers a variety of disciplines (such as technology, social sciences, the humanities and the law ) and areas, and tries to investigate many different issues (technical, legal, societal, etc.).European research
Within the Seventh Research Framework Programme of the European Union from 2007 to 2013, several new projects related to Identity Management started. PICOS investigates and develops a state-of-the-art platform for providing trust, privacy and identity management in mobile communities. On the backdrop of an increased risk to privacy of the citizen in the Information Society, PrimeLife will develop concepts and technologies to help individuals to protect their autonomy and retain control over personal information, irrespective of their activities. SWIFT focuses on extending identity functions and federation to the network while addressing usability and privacy concerns, and leverages identity technology as a key to integrate service and transport infrastructures for the benefit of users and the providers.Other identity related projects from older European Union funded framework programs include:
Publications
Different academic journals can be used to publish articles related to identity management such as:Less specialized journals may also publish on the topic, and for instance have special issue on Identity such as:
- Online Information Review. See for instance the Special Issue on: Digital ID management (Volume 33, Issue 3, 2009).
Standardization
ISO (and more specifically ISO/IEC JTC1ISO/IEC JTC1
ISO/IEC JTC 1 is Joint Technical Committee 1 of the International Organization for Standardization and the International Electrotechnical Commission . It deals with all matters of information technology....
, SC27 IT Security techniques) is conducting some standardization work for identity management , such as the elaboration of a framework for identity management, including the definition of different identity related terms.
Implementation challenges
- Getting all stakeholders to have a common view of area which is likely to come together and discuss the issues
- Expectation to make the IdM a data synchronization engine for application data
- Envisaging an appropriate business processBusiness processA business process or business method is a collection of related, structured activities or tasks that produce a specific service or product for a particular customer or customers...
leading to post-production challenges - Lack of leadershipLeadershipLeadership has been described as the “process of social influence in which one person can enlist the aid and support of others in the accomplishment of a common task". Other in-depth definitions of leadership have also emerged.-Theories:...
and support from sponsors - Overlooking change managementChange managementChange management is a structured approach to shifting/transitioning individuals, teams, and organizations from a current state to a desired future state. It is an organizational process aimed at helping employees to accept and embrace changes in their current business environment....
— expecting everybody to go through the self-learning process - Lack of definition of the post-production phase in a project planProject planA project plan, according to the Project Management Body of Knowledge, isPRINCE2 defines:In some industries, particularly information technology, the term "project plan" can refer to a Gantt chart or other document that shows project activities along a timeline. While common, this use is inaccurate...
— for a smooth transition of the system to the end-user community, it becomes critical that an organization gears up for proper support through a transition phase or stabilization phase. This may take from three to six months. - Lack of focus on integration testingIntegration testingIntegration testing is the phase in software testing in which individual software modules are combined and tested as a group. It occurs after unit testing and before validation testing...
- Lack of consistent architecturalInformation ArchitectureInformation architecture is the art of expressing a model or concept of information used in activities that require explicit details of complex systems. Among these activities are library systems, Content Management Systems, web development, user interactions, database development, programming,...
vision - Expectations for "over-automation"
- Deploying too many IdM technologies in a short time period
See also
- Access Control ServiceAccess Control ServiceAccess Control Service, or Windows Azure AppFabric Access Control Service is a cloud-based service that provides an easy way of authenticating and authorizing users to gain access to web applications and services while allowing the features of authentication and authorization to be factored out of...
- Athens access and identity managementAthens access and identity managementAthens is an Access and Identity Management service based in the United Kingdom that is supplied by Eduserv to provide single sign-on to protected resources combined with full user management capability...
- AuthenticationAuthenticationAuthentication is the act of confirming the truth of an attribute of a datum or entity...
- Claims Based Identity
- Digital identityDigital identityDigital identity is the aspect of digital technology that is concerned with the mediation of people's experience of their own identity and the identity of other people and things...
- Directory serviceDirectory serviceA directory service is the software system that stores, organizes and provides access to information in a directory. In software engineering, a directory is a map between names and values. It allows the lookup of values given a name, similar to a dictionary...
- DongleDongleA software protection dongle is a small piece of hardware that plugs into an electrical connector on a computer and serves as an electronic "key" for a piece of software; the program will only run when the dongle is plugged in...
- Federated Identity ManagementFederated identity managementIn information technology, Federated Identity Management amounts to having a common set of policies, practices and protocols in place to manage the identity and trust into IT users and devices across organizations....
- Future of Identity in the Information Society (FIDIS)
- Hardware Security ModuleHardware Security ModuleA hardware security module is a type of secure cryptoprocessor targeted at managing digital keys, accelerating cryptoprocesses in terms of digital signings/second and for providing strong authentication to access critical keys for server applications...
- Identity as a service
- Identity assuranceIdentity assuranceIdentity assurance, in the context of Federated Identity Management, is the ability for a party to determine, with some level of certainty, that an electronic credential representing an entity - whether a human or a machine, with which it interacts to effect a transaction, can be trusted to...
- Identity driven networkingIdentity Driven NetworkingIdentity Driven Networking is the process of applying network controls to a network device access based on the identity of an individual or group of individuals responsible to or operating the device...
- Identity management systemsIdentity management systemsAn identity management system refers to an information system, or to a set of technologies that can be used to support the management of identities.An identity management system:# Establishes the identity...
- Information privacy
- Initiative For Open AuthenticationInitiative For Open AuthenticationInitiative for Open Authentication is an industry-wide collaboration to develop an open reference architecture using open standards to promote the adoption of strong authentication...
- Loyalty card
- Mobile identity managementMobile identity managementThe mobile phone in addition to a wallet and house keys has become one of the essentials to take with you when leaving the house. By storing all the technical necessary applications on a SIM card, the mobile phone has turned into a device for managing each person’s digital identity.Mobile Identity...
- Mobile SignatureMobile signatureA mobile signature is a digital signature generated either on a mobile phone or on a SIM card.-Origins of the term:mSignThe term first appeared in articles introducing mSign . It was founded in 1999 and comprised 35 member companies...
s - Multi-factor authenticationMulti-factor authenticationMulti-factor authentication, sometimes called strong authentication, is an extension of two-factor authentication. This is the Defense in depth approach of "Security In Layers" applied to authentication. While two-factor authentication only involves exactly two factors, multi-factor...
- Mutual authenticationMutual authenticationMutual authentication or two-way authentication refers to two parties authenticating each other suitably. In technology terms, it refers to a client or user authenticating themselves to a server and that server authenticating itself to the user in such a way that both parties are assured of the...
- Online identity managementOnline identity managementOnline identity management also known as online image management or online personal branding or personal reputation management is a set of methods for generating a distinguished Web presence of a person on the Internet...
- Real-time locating
- Real-time locating systemReal-time locating systemReal-time locating systems are a type of local positioning system that allow to track and identify the location of objects in real time. Using simple, inexpensive badges or tags attached to the objects, readers receive wireless signals from these tags to determine their locations...
- Software tokenSoftware tokenA software token is a type of two-factor authentication security device that may be used to authorize the use of computer services. Software tokens are stored on a general-purpose electronic device such as a desktop computer, laptop, PDA, or mobile phone...
- Two-factor authenticationTwo-factor authenticationTwo-factor authentication is an approach to authentication which requires the presentation of two different kinds of evidence that someone is who they say they are. It is a part of the broader family of multi-factor authentication, which is a defense in depth approach to security...
- User modelingUser modelingUser modeling is a subdivision of human–computer interaction and describes theprocess of building up and modifying a user model. The main goal of user modeling is customization and adaptation of systems to the user's specific needs. The system needs to "say the 'right' thing at the 'right' time in...
- U-ProveU-ProveU-Prove is a cryptographic technology for claims-based identity management developed by Stefan Brands and the company he founded, Credentica. It aims to offer greater security, scalability, and privacy than existing identity management frameworks, and allows for claims to be tied to the use of...
External links
- General Public Tutorial about Privacy and Identity Management
- Identity Management Overview (Computer Weekly)
- Secure Widespread Identities for Federated Telecommunications (SWIFT)
- Federation for Identity and Cross-Credentialing Systems (FiXs)
- Identity management and information sharing in ISO 18876 Industrial automation systems and integration
- Identity management terminology (free, no registration required)
- Sloppiness in access and authorization management can cost enterprises dearly
- Identity management with virtual credentials- a dimension to the access control industry

