
T-function
Encyclopedia

Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
, a T-function is a bijective
Bijection
A bijection is a function giving an exact pairing of the elements of two sets. A bijection from the set X to the set Y has an inverse function from Y to X. If X and Y are finite sets, then the existence of a bijection means they have the same number of elements...
mapping that updates every bit of the state
State (computer science)
In computer science and automata theory, a state is a unique configuration of information in a program or machine. It is a concept that occasionally extends into some forms of systems programming such as lexers and parsers....
in a way that can be described as
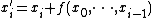 , or in simple words an update function in which each bit of the state is updated by a linear combination of the same bit and a function of a subset of its less significant bits. If every single less significant bit is included in the update of every bit in the state, such a T-function is called triangular. Thanks to their bijectivity (no collisions, therefore no entropy loss) regardless of the used Boolean functions and regardless of the selection of inputs (as long as they all come from one side of the output bit), T-functions are now widely used in cryptography to construct block cipher
, or in simple words an update function in which each bit of the state is updated by a linear combination of the same bit and a function of a subset of its less significant bits. If every single less significant bit is included in the update of every bit in the state, such a T-function is called triangular. Thanks to their bijectivity (no collisions, therefore no entropy loss) regardless of the used Boolean functions and regardless of the selection of inputs (as long as they all come from one side of the output bit), T-functions are now widely used in cryptography to construct block cipherBlock cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
s, stream cipher
Stream cipher
In cryptography, a stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream . In a stream cipher the plaintext digits are encrypted one at a time, and the transformation of successive digits varies during the encryption...
s, PRNGs and hash functions
Cryptographic hash function
A cryptographic hash function is a deterministic procedure that takes an arbitrary block of data and returns a fixed-size bit string, the hash value, such that an accidental or intentional change to the data will change the hash value...
. T-functions were first proposed in 2002 by A. Klimov and A. Shamir
Adi Shamir
Adi Shamir is an Israeli cryptographer. He is a co-inventor of the RSA algorithm , a co-inventor of the Feige–Fiat–Shamir identification scheme , one of the inventors of differential cryptanalysis and has made numerous contributions to the fields of cryptography and computer...
in their paper "A New Class of Invertible Mappings". Ciphers such as TSC-1, TSC-3
TSC-3
In cryptography, TSC-3 is a stream cypher algorithm developed by Jin Hong, Dong Hoon Lee, Yongjin Yeom, Daewan Han, and Seongtaek Chee. It has been submitted to the eSTREAM Project of the eCRYPT network....
, TSC-4, ABC, Mir-1
Mir-1
In cryptography, Mir-1 is a stream cypher algorithm developed by Alexander Maximov. It has been submitted to the eSTREAM project of the eCRYPT network. It has not been selected for focus or for consideration during Phase 2; it has been 'archived'....
and VEST
VEST
VEST ciphers are a set of families of general-purpose hardware-dedicated ciphers that support single pass authenticated encryption and can operate as collision-resistant hash functions designed by Sean O'Neil, Benjamin Gittins and Howard Landman...
are built with different types of T-functions.
Because arithmetic operations such as addition
Addition
Addition is a mathematical operation that represents combining collections of objects together into a larger collection. It is signified by the plus sign . For example, in the picture on the right, there are 3 + 2 apples—meaning three apples and two other apples—which is the same as five apples....
, subtraction
Subtraction
In arithmetic, subtraction is one of the four basic binary operations; it is the inverse of addition, meaning that if we start with any number and add any number and then subtract the same number we added, we return to the number we started with...
and multiplication
Multiplication
Multiplication is the mathematical operation of scaling one number by another. It is one of the four basic operations in elementary arithmetic ....
are also T-functions (triangular T-functions), software-efficient word-based T-functions can be constructed by combining bitwise logic with arithmetic operations. Another important property of T-functions based on arithmetic operations is predictability of their period, which is highly attractive to cryptographers. Although triangular T-functions are naturally vulnerable to guess-and-determine attacks, well chosen bitwise transpositions between rounds can neutralize that imbalance. In software-efficient cipher
Cipher
In cryptography, a cipher is an algorithm for performing encryption or decryption — a series of well-defined steps that can be followed as a procedure. An alternative, less common term is encipherment. In non-technical usage, a “cipher” is the same thing as a “code”; however, the concepts...
s, it can be done by interleaving
Interleaving
In computer science and telecommunication, interleaving is a way to arrange data in a non-contiguous way to increase performance.It is typically used:* In error-correction coding, particularly within data transmission, disk storage, and computer memory....
arithmetic operations with byte-swapping operations and to a small degree with bitwise rotation operations. However, triangular T-functions remain highly inefficient in hardware.
T-functions do not have any restrictions on the types and the widths of the update functions used for each bit. Subsequent transposition of the output bits and iteration
Iteration
Iteration means the act of repeating a process usually with the aim of approaching a desired goal or target or result. Each repetition of the process is also called an "iteration," and the results of one iteration are used as the starting point for the next iteration.-Mathematics:Iteration in...
of the T-function also do not affect bijectivity. This freedom allows the designer to choose the update functions or S-boxes that satisfy all other cryptographic criteria and even choose arbitrary or key-dependent update functions (see family keying).
Hardware-efficient lightweight T-functions with identical widths of all the update functions for each bit of the state can thus be easily constructed. The core accumulators of VEST ciphers are a good example of such reasonably light-weight T-functions that are balanced out after 2 rounds by the transposition layer making all the 2-round feedback functions of roughly the same width and losing the "T-function" bias of depending only on the less significant bits of the state.

