Shatter attack
Encyclopedia
In computing, a shatter attack is a programming technique employed by crackers on Microsoft Windows
operating system
s that can be used to bypass security restrictions between processes in a session. A shatter attack takes advantage of a design flaw in Windows's message-passing system whereby arbitrary code could be injected
into any other running application or service in the same session, that makes use of a message loop
. This could result in a privilege escalation
exploit.
s of higher-privileged application - and some messages can have the address of a callback function in the application's address space as its parameter. If an attacker manages to put his own string into the memory of the higher-privileged application (say by pasting shellcode
to an edit box or using VirtualAllocEx and WriteProcessMemory) at a known location, they could then send WM_TIMER messages with callback function parameters set to point to the attacker's string.
A few weeks after the publication of this paper, Microsoft responded, noting that: "The paper is correct that this situation exists, and it does correctly describe its effect. ... Where the paper errs is in claiming that this is a flaw in Windows. In reality, the flaw lies in the specific, highly privileged service. By design, all services within the interactive desktop are peers, and can levy requests upon each other. As a result, all services in the interactive desktop effectively have privileges commensurate with the most highly privileged service there."
, Windows 2000
, and Windows XP
that closed off some avenues of exploitation. This was only a partial solution, however, as the fix was limited to services included with Windows that could be exploited using this technique; the underlying design flaw still existed and could still be used to target other applications or third-party services. With Windows Vista
, Microsoft aimed to solve the problem in two ways: First, local users no longer log in to Session 0, thus separating the message loop of a logged-in user's session from high-privilege system services, which are loaded into Session 0. Second, a new feature called User Interface Privilege Isolation
(UIPI) was introduced, whereby processes can be further protected against shatter attacks by assigning an Integrity Level to each process. Attempts to send messages to a process with a higher Integrity Level will fail, even if both processes are owned by the same user. However, not all interactions between processes at different Integrity Levels are prevented by UIPI. Internet Explorer 7
, for example, uses the UIPI feature to limit the extent to which its rendering components interact with the rest of the system.
The way sessions are instantiated was redesigned in Windows Vista
and Windows Server 2008 to provide additional protection against shatter attacks. Local user logins were moved from Session 0 to Session 1, thus separating the user's processes from system services that could be vulnerable.
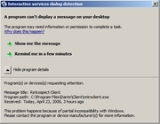
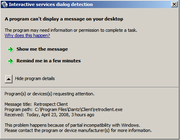 This creates backward compatibility
This creates backward compatibility
issues, however, as some software was designed with the assumption that the service is running in the same session as the logged-in user. To support this view, Windows Vista and Windows Server 2008 include a Windows service
called "Interactive Services Detection" that enables access to dialogs created by interactive services when they appear. The interactive user is shown a dialog box and is offered the ability to switch to Session 0 to access the dialog box.
Also, services configured with the "interact with the desktop" privilege can still create popup dialogues, system notification icons, or other user interface elements for the interactive user. This circumvents the protections afforded by having the interactive user logged in to a separate session, so this practice is discouraged. Instead, a two-process design is recommended where a process is loaded into the user's session that interacts with the service process through inter-process communication. Additionally, when a privileged operation is required to be undertaken, an authenticated call is made that loads additional service code. Once that privileged code is finished doing what needs to be done, it is unloaded from memory so that it does not remain to be a possible target for later exploitation.
Microsoft Windows
Microsoft Windows is a series of operating systems produced by Microsoft.Microsoft introduced an operating environment named Windows on November 20, 1985 as an add-on to MS-DOS in response to the growing interest in graphical user interfaces . Microsoft Windows came to dominate the world's personal...
operating system
Operating system
An operating system is a set of programs that manage computer hardware resources and provide common services for application software. The operating system is the most important type of system software in a computer system...
s that can be used to bypass security restrictions between processes in a session. A shatter attack takes advantage of a design flaw in Windows's message-passing system whereby arbitrary code could be injected
Code injection
Code injection is the exploitation of a computer bug that is caused by processing invalid data. Code injection can be used by an attacker to introduce code into a computer program to change the course of execution. The results of a code injection attack can be disastrous...
into any other running application or service in the same session, that makes use of a message loop
Message loop in Microsoft Windows
Microsoft Windows programs are event-based. They act upon messages that the operating system posts to the main thread of the application. These messages are received from the message queue by the application by repeatedly calling the GetMessage function in a section of code called the "event...
. This could result in a privilege escalation
Privilege escalation
Privilege escalation is the act of exploiting a bug, design flaw or configuration oversight in an operating system or software application to gain elevated access to resources that are normally protected from an application or user...
exploit.
Overview
Shatter attacks became a topic of intense conversation in the security community in August 2002 after the publication of Chris Paget's paper titled, "Exploiting design flaws in the Win32 API for privilege escalation". The paper, which coined the term "shatter attack", explained the process by which an application could execute arbitrary code in another application. This could occur because Windows allows unprivileged applications to send messages to message loopMessage loop in Microsoft Windows
Microsoft Windows programs are event-based. They act upon messages that the operating system posts to the main thread of the application. These messages are received from the message queue by the application by repeatedly calling the GetMessage function in a section of code called the "event...
s of higher-privileged application - and some messages can have the address of a callback function in the application's address space as its parameter. If an attacker manages to put his own string into the memory of the higher-privileged application (say by pasting shellcode
Shellcode
In computer security, a shellcode is a small piece of code used as the payload in the exploitation of a software vulnerability. It is called "shellcode" because it typically starts a command shell from which the attacker can control the compromised machine. Shellcode is commonly written in...
to an edit box or using VirtualAllocEx and WriteProcessMemory) at a known location, they could then send WM_TIMER messages with callback function parameters set to point to the attacker's string.
A few weeks after the publication of this paper, Microsoft responded, noting that: "The paper is correct that this situation exists, and it does correctly describe its effect. ... Where the paper errs is in claiming that this is a flaw in Windows. In reality, the flaw lies in the specific, highly privileged service. By design, all services within the interactive desktop are peers, and can levy requests upon each other. As a result, all services in the interactive desktop effectively have privileges commensurate with the most highly privileged service there."
Solutions
In December 2002, Microsoft issued a patch for Windows NT 4.0Windows NT 4.0
Windows NT 4.0 is a preemptive, graphical and business-oriented operating system designed to work with either uniprocessor or symmetric multi-processor computers. It was the next release of Microsoft's Windows NT line of operating systems and was released to manufacturing on 31 July 1996...
, Windows 2000
Windows 2000
Windows 2000 is a line of operating systems produced by Microsoft for use on personal computers, business desktops, laptops, and servers. Windows 2000 was released to manufacturing on 15 December 1999 and launched to retail on 17 February 2000. It is the successor to Windows NT 4.0, and is the...
, and Windows XP
Windows XP
Windows XP is an operating system produced by Microsoft for use on personal computers, including home and business desktops, laptops and media centers. First released to computer manufacturers on August 24, 2001, it is the second most popular version of Windows, based on installed user base...
that closed off some avenues of exploitation. This was only a partial solution, however, as the fix was limited to services included with Windows that could be exploited using this technique; the underlying design flaw still existed and could still be used to target other applications or third-party services. With Windows Vista
Windows Vista
Windows Vista is an operating system released in several variations developed by Microsoft for use on personal computers, including home and business desktops, laptops, tablet PCs, and media center PCs...
, Microsoft aimed to solve the problem in two ways: First, local users no longer log in to Session 0, thus separating the message loop of a logged-in user's session from high-privilege system services, which are loaded into Session 0. Second, a new feature called User Interface Privilege Isolation
User Interface Privilege Isolation
User Interface Privilege Isolation is a technology introduced in Windows NT 6.0 to combat shatter attack exploits. By making use of Mandatory Integrity Control, it prevents processes with a lower "integrity level" from sending messages to higher IL processes...
(UIPI) was introduced, whereby processes can be further protected against shatter attacks by assigning an Integrity Level to each process. Attempts to send messages to a process with a higher Integrity Level will fail, even if both processes are owned by the same user. However, not all interactions between processes at different Integrity Levels are prevented by UIPI. Internet Explorer 7
Internet Explorer 7
Windows Internet Explorer 7 is a web browser released by Microsoft in October 2006. Internet Explorer 7 is part of a long line of versions of Internet Explorer and was the first major update to the browser in more than 5 years...
, for example, uses the UIPI feature to limit the extent to which its rendering components interact with the rest of the system.
The way sessions are instantiated was redesigned in Windows Vista
Windows Vista
Windows Vista is an operating system released in several variations developed by Microsoft for use on personal computers, including home and business desktops, laptops, tablet PCs, and media center PCs...
and Windows Server 2008 to provide additional protection against shatter attacks. Local user logins were moved from Session 0 to Session 1, thus separating the user's processes from system services that could be vulnerable.

Backward compatibility
In the context of telecommunications and computing, a device or technology is said to be backward or downward compatible if it can work with input generated by an older device...
issues, however, as some software was designed with the assumption that the service is running in the same session as the logged-in user. To support this view, Windows Vista and Windows Server 2008 include a Windows service
Windows Service
On Microsoft Windows operating systems, a Windows service is a long-running executable that performs specific functions and which is designed not to require user intervention. Windows services can be configured to start when the operating system is booted and run in the background as long as...
called "Interactive Services Detection" that enables access to dialogs created by interactive services when they appear. The interactive user is shown a dialog box and is offered the ability to switch to Session 0 to access the dialog box.
Also, services configured with the "interact with the desktop" privilege can still create popup dialogues, system notification icons, or other user interface elements for the interactive user. This circumvents the protections afforded by having the interactive user logged in to a separate session, so this practice is discouraged. Instead, a two-process design is recommended where a process is loaded into the user's session that interacts with the service process through inter-process communication. Additionally, when a privileged operation is required to be undertaken, an authenticated call is made that loads additional service code. Once that privileged code is finished doing what needs to be done, it is unloaded from memory so that it does not remain to be a possible target for later exploitation.

