Idle scan
Encyclopedia
The idle scan is a TCP
port scan
method that consists of sending spoofed
packets to a computer to find out what services are available. This is accomplished by impersonating another computer called a "zombie" (that is not transmitting or receiving information) and observing the behavior of the zombie system.
This action can be done through common software
network utilities
such as nmap
and hping
. The attack involves sending forged packets to a specific machine target in an effort to find distinct characteristics of another zombie machine.
The attack is sophisticated because there is no interaction between the attacker computer and the target: the attacker interacts only with the "zombie" computer.
This exploit
is dual-hatted as a port scanner and a mapper of trusted IP relationships between machines. The target system interacts with the "zombie" computer and difference in behaviour can be observed using different "zombies" with evidence of different privileges granted by the target to different computers.
Discovered by Salvatore Sanfilippo (also known by his handle "Antirez") in 1998, the idle scan has been used by many black hat
"hackers" to covertly identify open ports on a target computer in preparation for attacking it.
Although it was originally named dumb scan, the term idle scan was coined in 1999, after the publication of a proof of concept 16-bit identification field (IPID) scanner named idlescan, by Filipe Almeida (aka LiquidK). This type of scan can also be referenced as zombie scan; all the nomenclatures are due to the nature of one of the computers involved in the attack.
is based on the Internet Protocol Suite
, commonly also called TCP/IP.
IP is the primary protocol in the Internet Layer
of the Internet Protocol Suite and has the task of delivering datagrams from the source host
to the destination host solely based on their addresses
. For this purpose, IP defines addressing methods and structures for datagram encapsulation
. It is a connectionless protocol and relies on the transmission of packets. Every IP packet from a given source has an ID that uniquely identifying IP datagram.
TCP
provides reliable, ordered delivery of a stream of bytes from a program on one computer to another program on another computer. TCP is the protocol that major Internet applications rely on, such as the World Wide Web, e-mail, and file transfer. Each application server is called a service.
In this system, hosts and host services are referenced using two components: an address and a port number. There are 65536 distinct and usable port numbers per host. Most services use a limited range of numbers.
Some port scanners scan only the most common port numbers, or ports most commonly associated with vulnerable services, on a given host. See: List of TCP and UDP port numbers.
The result of a scan on a port is usually generalized into one of three categories:
Open ports present two vulnerabilities of which administrator
s must be wary:
Filtered ports do not tend to present vulnerabilities.
The host in a local network can be protected by a firewall
that filters, according with rules that its administrator set up, packets. This is done to deny services to hosts not known and prevent intrusion
in the inside network.
The IP protocol is network layer transmission protocol
An attacker would first scan for a host with a sequential and predictable sequence number (IPID). The latest versions of Linux
, Solaris and OpenBSD
, Windows Vista
are not suitable as zombie, since the IPID has been implemented with patches that randomized the IP ID. Computers chosen to be used in this stage are known as "zombies".
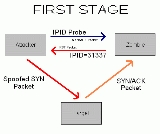
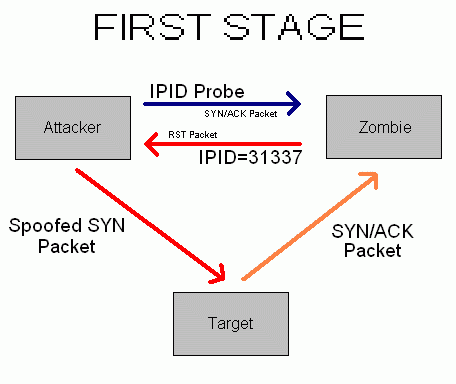
Once a suitable zombie is found the next step would be to try to establish a TCP connection with a given service (port) of the target system, impersonating the zombie. It is done by sending a SYN packet to the target computer, spoofing the IP address from the zombie, i.e. with the source address equal to zombie IP address.
If the port of the target computer is open it will accept the connection for the service, responding with a SYN/ACK packet back to the zombie.
The zombie computer will then send a RST packet to the target computer (to reset the connection) because it did not actually send the SYN packet in the first place.
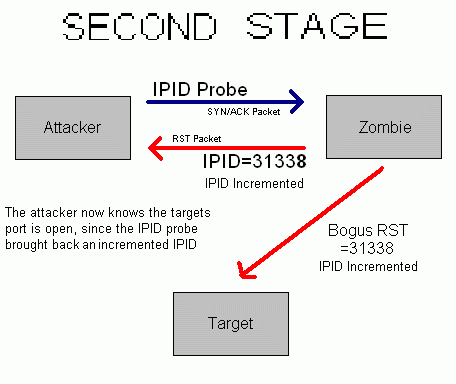
Since the zombie had to send the RST packet it will increment its IPID. This is how an attacker would find out if the targets port is open. The attacker will send another packet to the zombie. If the IPID is incremented only by a step then the attacker would know that the particular port is closed.
The method assumes that zombie has no other interactions: if there is any message sent for other reasons between the first interaction of the attacker with the zombie and the second interaction other than RST message, there will be a false positive.
between the attacker and the zombie, and between the zombie and the target, the faster the scan will proceed.
When an idle scan is attempted, tools (for example nmap) tests the proposed zombie and reports any problems with it. If one doesn't work, try another. Enough Internet hosts are vulnerable that zombie candidates aren't hard to find.
A common approach is to simply execute a ping sweep
of some network. Choosing a network near your source address, or near the target, produces better results. You can try an idle scan using each available host from the ping sweep results until you find one that works. As usual, it is best to ask permission before using someone's machines for unexpected purposes such as idle scanning.
Funny—simple network devices often make great zombies because they are commonly both underused (idle) and built with simple network stacks which are vulnerable to IP ID traffic detection.
While identifying a suitable zombie takes some initial work, you can keep re-using the good ones. Alternatively, there have been some research on utilizing unintended public web services as zombie hosts to perform similar idle scans. Leveraging the way some of these services perform outbound connections upon user submissions can serve as some kind of poor's man idle scanning.
First, establish that the idle host is actually idle, send packets using hping2
and observe the id numbers increase incrementally by one. If the id numbers
increase haphazardly, the host is not actually idle or has an OS that has no predictable IP ID.
[root@localhost hping2-rc3]# ./hping2 -S 172.16.0.105
HPING 172.16.0.105 (eth0 172.16.0.105): S set, 40 headers + 0 data bytes
len=46 ip=172.16.0.105 ttl=128 id=1371 sport=0 flags=RA seq=0 win=0 rtt=0.3 ms
len=46 ip=172.16.0.105 ttl=128 id=1372 sport=0 flags=RA seq=1 win=0 rtt=0.2 ms
len=46 ip=172.16.0.105 ttl=128 id=1373 sport=0 flags=RA seq=2 win=0 rtt=0.3 ms
len=46 ip=172.16.0.105 ttl=128 id=1374 sport=0 flags=RA seq=3 win=0 rtt=0.2 ms
len=46 ip=172.16.0.105 ttl=128 id=1375 sport=0 flags=RA seq=4 win=0 rtt=0.2 ms
len=46 ip=172.16.0.105 ttl=128 id=1376 sport=0 flags=RA seq=5 win=0 rtt=0.2 ms
len=46 ip=172.16.0.105 ttl=128 id=1377 sport=0 flags=RA seq=6 win=0 rtt=0.2 ms
len=46 ip=172.16.0.105 ttl=128 id=1378 sport=0 flags=RA seq=7 win=0 rtt=0.2 ms
len=46 ip=172.16.0.105 ttl=128 id=1379 sport=0 flags=RA seq=8 win=0 rtt=0.4 ms
Send a spoofed SYN packet to the target host on a port you expect to be open. In this case, port 22 (ssh) is being tested.
# hping2—spoof 172.16.0.105 -S 172.16.0.100 -p 22 -c 1
HPING 172.16.0.100 (eth0 172.16.0.100): S set, 40 headers + 0 data bytes
--- 172.16.0.100 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
Since we spoofed the packet, we did not receive a reply and hping reports 100% packet loss. The target host replied directly to the idle host with a syn/ack packet. Now, check the idle host to see if the id number has increased.
# hping2 -S 172.16.0.105 -p 445 -c 1
HPING 172.16.0.105 (eth0 172.16.0.105): S set, 40 headers + 0 data bytes
len=46 ip=172.16.0.105 ttl=128 DF id=1381 sport=445 flags=SA seq=0 win=64320 rtt=0.3 ms
--- 172.16.0.105 hping statistic ---
1 packets tramitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 0.3/0.3/0.3 ms
Notice that the proxy hosts id increased from id=1379 to id=1381. 1380 was consumed when the idle host replied to the target host's syn/ack packet with an rst packet.
Run through the same processes again testing a port that is likely closed. Here we are testing port 23 (telnet).
# hping2 -S 172.16.0.105 -p 445 -c 1; hping2—spoof 172.16.0.105 -S 172.16.0.100 -p 23 -c 1; hping2 -S 172.16.0.105 -p 445 -c 1
HPING 172.16.0.105 (eth0 172.16.0.105): S set, 40 headers + 0 data bytes
len=46 ip=172.16.0.105 ttl=128 DF id=1382 sport=445 flags=SA seq=0 win=64320 rtt=2.1 ms
--- 172.16.0.105 hping statistic ---
1 packets tramitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 2.1/2.1/2.1 ms
HPING 172.16.0.100 (eth0 172.16.0.100): S set, 40 headers + 0 data bytes
--- 172.16.0.100 hping statistic ---
1 packets tramitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
HPING 172.16.0.105 (eth0 172.16.0.105): S set, 40 headers + 0 data bytes
len=46 ip=172.16.0.105 ttl=128 DF id=1383 sport=445 flags=SA seq=0 win=64320 rtt=0.3 ms
--- 172.16.0.105 hping statistic ---
1 packets tramitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 0.3/0.3/0.3 ms
Notice that this time, the id did not increase because the port was closed. When we sent the spoofed packet to the target host, it replied to the idle host with an rst packet which did not increase the id counter.
:
Performing a port scan and OS identification (-O option in nmap) on the zombie candidate network rather than just a ping scan helps in selecting a good zombie. As long as verbose mode (-v) is enabled, OS detection will usually determine the IP ID sequence generation method and print a line such as “IP ID Sequence Generation: Incremental”. If the type is given as Incremental or Broken little-endian incremental, the machine is a good zombie candidate. That is still no guarantee that it will work, as Solaris and some other systems create a new IP ID sequence for each host they communicate with. The host could also be too busy. OS detection and the open port list can also help in identifying systems that are likely to be idle.
Another approach to identifying zombie candidates is the run the ipidseq NSE script against a host. This script probes a host to classify its IP ID generation method, then prints the IP ID classification much like the OS detection does. Like most NSE scripts, ipidseq.nse can be run against many hosts in parallel, making it another good choice when scanning entire networks looking for suitable hosts.
This tells nmap to do a ping sweep and show all hosts that are up in the given IP range. Once you have found a zombie, next you would send the spoofed packets:
The images juxtaposition show both of these stages in a successful scenario.
or Intrusion-detection system
log. Another useful possibility is the chance of by-passing a firewall because you are scanning the target from the zombie's computer, which might have extra rights than the attacker's.
Transmission Control Protocol
The Transmission Control Protocol is one of the core protocols of the Internet Protocol Suite. TCP is one of the two original components of the suite, complementing the Internet Protocol , and therefore the entire suite is commonly referred to as TCP/IP...
port scan
Port scanner
A port scanner is a software application designed to probe a server or host for open ports. This is often used by administrators to verify security policies of their networks and by attackers to identify running services on a host with the view to compromise it.A port scan or portscan is "An attack...
method that consists of sending spoofed
IP address spoofing
In computer networking, the term IP address spoofing or IP spoofing refers to the creation of Internet Protocol packets with a forged source IP address, called spoofing, with the purpose of concealing the identity of the sender or impersonating another computing system.-Background:The basic...
packets to a computer to find out what services are available. This is accomplished by impersonating another computer called a "zombie" (that is not transmitting or receiving information) and observing the behavior of the zombie system.
This action can be done through common software
Computer software
Computer software, or just software, is a collection of computer programs and related data that provide the instructions for telling a computer what to do and how to do it....
network utilities
Utility software
Utility software is system software designed to help analyze, configure, optimize or maintain a computer. A single piece of utility software is usually called a utility or tool....
such as nmap
Nmap
Nmap is a security scanner originally written by Gordon Lyon used to discover hosts and services on a computer network, thus creating a "map" ofthe network...
and hping
Hping
hping is a free packet generator and analyzer for the TCP/IP protocol distributed by Salvatore Sanfilippo .Hping is one of the de facto tools for security auditing and testing of firewalls and networks, and was used to exploit the idle scan scanning technique , and now implemented in the Nmap...
. The attack involves sending forged packets to a specific machine target in an effort to find distinct characteristics of another zombie machine.
The attack is sophisticated because there is no interaction between the attacker computer and the target: the attacker interacts only with the "zombie" computer.
This exploit
Exploit (computer security)
An exploit is a piece of software, a chunk of data, or sequence of commands that takes advantage of a bug, glitch or vulnerability in order to cause unintended or unanticipated behavior to occur on computer software, hardware, or something electronic...
is dual-hatted as a port scanner and a mapper of trusted IP relationships between machines. The target system interacts with the "zombie" computer and difference in behaviour can be observed using different "zombies" with evidence of different privileges granted by the target to different computers.
Discovered by Salvatore Sanfilippo (also known by his handle "Antirez") in 1998, the idle scan has been used by many black hat
Black hat
A black hat is the villain or bad guy, especially in a western movie in which such a character would stereotypically wear a black hat in contrast to the hero's white hat, especially in black and white movies....
"hackers" to covertly identify open ports on a target computer in preparation for attacking it.
Although it was originally named dumb scan, the term idle scan was coined in 1999, after the publication of a proof of concept 16-bit identification field (IPID) scanner named idlescan, by Filipe Almeida (aka LiquidK). This type of scan can also be referenced as zombie scan; all the nomenclatures are due to the nature of one of the computers involved in the attack.
TCP/IP basic knowledge
The design and operation of the InternetInternet
The Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
is based on the Internet Protocol Suite
Internet protocol suite
The Internet protocol suite is the set of communications protocols used for the Internet and other similar networks. It is commonly known as TCP/IP from its most important protocols: Transmission Control Protocol and Internet Protocol , which were the first networking protocols defined in this...
, commonly also called TCP/IP.
IP is the primary protocol in the Internet Layer
Internet layer
The internet layer or IP layer is a group of internetworking methods in the Internet protocol suite, commonly also called TCP/IP, which is the foundation of the Internet...
of the Internet Protocol Suite and has the task of delivering datagrams from the source host
Host (network)
A network host is a computer connected to a computer network. A network host may offer information resources, services, and applications to users or other nodes on the network. A network host is a network node that is assigned a network layer host address....
to the destination host solely based on their addresses
IP address
An Internet Protocol address is a numerical label assigned to each device participating in a computer network that uses the Internet Protocol for communication. An IP address serves two principal functions: host or network interface identification and location addressing...
. For this purpose, IP defines addressing methods and structures for datagram encapsulation
Encapsulation (networking)
In computer networking, encapsulation is a method of designing modular communication protocols in which logically separate functions in the network are abstracted from their underlying structures by inclusion or information hiding within higher level objects....
. It is a connectionless protocol and relies on the transmission of packets. Every IP packet from a given source has an ID that uniquely identifying IP datagram.
TCP
Transmission Control Protocol
The Transmission Control Protocol is one of the core protocols of the Internet Protocol Suite. TCP is one of the two original components of the suite, complementing the Internet Protocol , and therefore the entire suite is commonly referred to as TCP/IP...
provides reliable, ordered delivery of a stream of bytes from a program on one computer to another program on another computer. TCP is the protocol that major Internet applications rely on, such as the World Wide Web, e-mail, and file transfer. Each application server is called a service.
In this system, hosts and host services are referenced using two components: an address and a port number. There are 65536 distinct and usable port numbers per host. Most services use a limited range of numbers.
Some port scanners scan only the most common port numbers, or ports most commonly associated with vulnerable services, on a given host. See: List of TCP and UDP port numbers.
The result of a scan on a port is usually generalized into one of three categories:
- Open or Accepted: The host sent a reply indicating that a service is listening on the port.
- Closed or Denied or Not Listening: The host sent a reply indicating that connections will be denied to the port.
- Filtered, Dropped or Blocked: There was no reply from the host.
Open ports present two vulnerabilities of which administrator
System administrator
A system administrator, IT systems administrator, systems administrator, or sysadmin is a person employed to maintain and operate a computer system and/or network...
s must be wary:
- Security and stability concerns associated with the program responsible for delivering the service - Open ports.
- Security and stability concerns associated with the operating systemOperating systemAn operating system is a set of programs that manage computer hardware resources and provide common services for application software. The operating system is the most important type of system software in a computer system...
that is running on the host - Open or Closed ports.
Filtered ports do not tend to present vulnerabilities.
The host in a local network can be protected by a firewall
Firewall (computing)
A firewall is a device or set of devices designed to permit or deny network transmissions based upon a set of rules and is frequently used to protect networks from unauthorized access while permitting legitimate communications to pass....
that filters, according with rules that its administrator set up, packets. This is done to deny services to hosts not known and prevent intrusion
Intrusion
An intrusion is liquid rock that forms under Earth's surface. Magma from under the surface is slowly pushed up from deep within the earth into any cracks or spaces it can find, sometimes pushing existing country rock out of the way, a process that can take millions of years. As the rock slowly...
in the inside network.
The IP protocol is network layer transmission protocol
Basic mechanics
Idle scans take advantage of predictable Identification field value from IP header: every IP packet from a given source has an ID that uniquely identifying fragments of an original IP datagram; the protocol implementation assigns values to this mandatory field generally by a fixed value (1) increment. Because transmitted packets are numbered in a sequence you can say how many packets are transmitted between two packets that you receive.An attacker would first scan for a host with a sequential and predictable sequence number (IPID). The latest versions of Linux
Linux
Linux is a Unix-like computer operating system assembled under the model of free and open source software development and distribution. The defining component of any Linux system is the Linux kernel, an operating system kernel first released October 5, 1991 by Linus Torvalds...
, Solaris and OpenBSD
OpenBSD
OpenBSD is a Unix-like computer operating system descended from Berkeley Software Distribution , a Unix derivative developed at the University of California, Berkeley. It was forked from NetBSD by project leader Theo de Raadt in late 1995...
, Windows Vista
Windows Vista
Windows Vista is an operating system released in several variations developed by Microsoft for use on personal computers, including home and business desktops, laptops, tablet PCs, and media center PCs...
are not suitable as zombie, since the IPID has been implemented with patches that randomized the IP ID. Computers chosen to be used in this stage are known as "zombies".
Once a suitable zombie is found the next step would be to try to establish a TCP connection with a given service (port) of the target system, impersonating the zombie. It is done by sending a SYN packet to the target computer, spoofing the IP address from the zombie, i.e. with the source address equal to zombie IP address.
If the port of the target computer is open it will accept the connection for the service, responding with a SYN/ACK packet back to the zombie.
The zombie computer will then send a RST packet to the target computer (to reset the connection) because it did not actually send the SYN packet in the first place.
Since the zombie had to send the RST packet it will increment its IPID. This is how an attacker would find out if the targets port is open. The attacker will send another packet to the zombie. If the IPID is incremented only by a step then the attacker would know that the particular port is closed.
The method assumes that zombie has no other interactions: if there is any message sent for other reasons between the first interaction of the attacker with the zombie and the second interaction other than RST message, there will be a false positive.
 |
 |
Finding a zombie host
The first step in executing an idle scan is to find an appropriate zombie. It needs to assign IP ID packets incrementally on a global (rather than per-host it communicates with) basis. It should be idle (hence the scan name), as extraneous traffic will bump up its IP ID sequence, confusing the scan logic. The lower the latencyLatency (engineering)
Latency is a measure of time delay experienced in a system, the precise definition of which depends on the system and the time being measured. Latencies may have different meaning in different contexts.-Packet-switched networks:...
between the attacker and the zombie, and between the zombie and the target, the faster the scan will proceed.
When an idle scan is attempted, tools (for example nmap) tests the proposed zombie and reports any problems with it. If one doesn't work, try another. Enough Internet hosts are vulnerable that zombie candidates aren't hard to find.
A common approach is to simply execute a ping sweep
Ping sweep
In computing, a ping sweep is a method that can establish a range of IP addresses which map to live hosts.The classic tool used for ping sweeps is , which traditionally was accompanied by gping to generate the list of hosts for large subnets, although more recent version of fping include that...
of some network. Choosing a network near your source address, or near the target, produces better results. You can try an idle scan using each available host from the ping sweep results until you find one that works. As usual, it is best to ask permission before using someone's machines for unexpected purposes such as idle scanning.
Funny—simple network devices often make great zombies because they are commonly both underused (idle) and built with simple network stacks which are vulnerable to IP ID traffic detection.
While identifying a suitable zombie takes some initial work, you can keep re-using the good ones. Alternatively, there have been some research on utilizing unintended public web services as zombie hosts to perform similar idle scans. Leveraging the way some of these services perform outbound connections upon user submissions can serve as some kind of poor's man idle scanning.
Using hping
The hping method for idle scanning provides a lower level example for how idle scanning is performed. In this example the target host (172.16.0.100) will be scanned using an idle host (172.16.0.105). An open and a closed port will be tested to see how each scenario plays out.First, establish that the idle host is actually idle, send packets using hping2
and observe the id numbers increase incrementally by one. If the id numbers
increase haphazardly, the host is not actually idle or has an OS that has no predictable IP ID.
[root@localhost hping2-rc3]# ./hping2 -S 172.16.0.105
HPING 172.16.0.105 (eth0 172.16.0.105): S set, 40 headers + 0 data bytes
len=46 ip=172.16.0.105 ttl=128 id=1371 sport=0 flags=RA seq=0 win=0 rtt=0.3 ms
len=46 ip=172.16.0.105 ttl=128 id=1372 sport=0 flags=RA seq=1 win=0 rtt=0.2 ms
len=46 ip=172.16.0.105 ttl=128 id=1373 sport=0 flags=RA seq=2 win=0 rtt=0.3 ms
len=46 ip=172.16.0.105 ttl=128 id=1374 sport=0 flags=RA seq=3 win=0 rtt=0.2 ms
len=46 ip=172.16.0.105 ttl=128 id=1375 sport=0 flags=RA seq=4 win=0 rtt=0.2 ms
len=46 ip=172.16.0.105 ttl=128 id=1376 sport=0 flags=RA seq=5 win=0 rtt=0.2 ms
len=46 ip=172.16.0.105 ttl=128 id=1377 sport=0 flags=RA seq=6 win=0 rtt=0.2 ms
len=46 ip=172.16.0.105 ttl=128 id=1378 sport=0 flags=RA seq=7 win=0 rtt=0.2 ms
len=46 ip=172.16.0.105 ttl=128 id=1379 sport=0 flags=RA seq=8 win=0 rtt=0.4 ms
Send a spoofed SYN packet to the target host on a port you expect to be open. In this case, port 22 (ssh) is being tested.
# hping2—spoof 172.16.0.105 -S 172.16.0.100 -p 22 -c 1
HPING 172.16.0.100 (eth0 172.16.0.100): S set, 40 headers + 0 data bytes
--- 172.16.0.100 hping statistic ---
1 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
Since we spoofed the packet, we did not receive a reply and hping reports 100% packet loss. The target host replied directly to the idle host with a syn/ack packet. Now, check the idle host to see if the id number has increased.
# hping2 -S 172.16.0.105 -p 445 -c 1
HPING 172.16.0.105 (eth0 172.16.0.105): S set, 40 headers + 0 data bytes
len=46 ip=172.16.0.105 ttl=128 DF id=1381 sport=445 flags=SA seq=0 win=64320 rtt=0.3 ms
--- 172.16.0.105 hping statistic ---
1 packets tramitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 0.3/0.3/0.3 ms
Notice that the proxy hosts id increased from id=1379 to id=1381. 1380 was consumed when the idle host replied to the target host's syn/ack packet with an rst packet.
Run through the same processes again testing a port that is likely closed. Here we are testing port 23 (telnet).
# hping2 -S 172.16.0.105 -p 445 -c 1; hping2—spoof 172.16.0.105 -S 172.16.0.100 -p 23 -c 1; hping2 -S 172.16.0.105 -p 445 -c 1
HPING 172.16.0.105 (eth0 172.16.0.105): S set, 40 headers + 0 data bytes
len=46 ip=172.16.0.105 ttl=128 DF id=1382 sport=445 flags=SA seq=0 win=64320 rtt=2.1 ms
--- 172.16.0.105 hping statistic ---
1 packets tramitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 2.1/2.1/2.1 ms
HPING 172.16.0.100 (eth0 172.16.0.100): S set, 40 headers + 0 data bytes
--- 172.16.0.100 hping statistic ---
1 packets tramitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
HPING 172.16.0.105 (eth0 172.16.0.105): S set, 40 headers + 0 data bytes
len=46 ip=172.16.0.105 ttl=128 DF id=1383 sport=445 flags=SA seq=0 win=64320 rtt=0.3 ms
--- 172.16.0.105 hping statistic ---
1 packets tramitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 0.3/0.3/0.3 ms
Notice that this time, the id did not increase because the port was closed. When we sent the spoofed packet to the target host, it replied to the idle host with an rst packet which did not increase the id counter.
Using nmap
The first thing the user would do is to find a suitable zombie on the LANLän
Län and lääni refer to the administrative divisions used in Sweden and previously in Finland. The provinces of Finland were abolished on January 1, 2010....
:
Performing a port scan and OS identification (-O option in nmap) on the zombie candidate network rather than just a ping scan helps in selecting a good zombie. As long as verbose mode (-v) is enabled, OS detection will usually determine the IP ID sequence generation method and print a line such as “IP ID Sequence Generation: Incremental”. If the type is given as Incremental or Broken little-endian incremental, the machine is a good zombie candidate. That is still no guarantee that it will work, as Solaris and some other systems create a new IP ID sequence for each host they communicate with. The host could also be too busy. OS detection and the open port list can also help in identifying systems that are likely to be idle.
Another approach to identifying zombie candidates is the run the ipidseq NSE script against a host. This script probes a host to classify its IP ID generation method, then prints the IP ID classification much like the OS detection does. Like most NSE scripts, ipidseq.nse can be run against many hosts in parallel, making it another good choice when scanning entire networks looking for suitable hosts.
nmap -v -O -sS 192.168.1.0/24This tells nmap to do a ping sweep and show all hosts that are up in the given IP range. Once you have found a zombie, next you would send the spoofed packets:
nmap -P0 -p -sI The images juxtaposition show both of these stages in a successful scenario.
Effectiveness
Although many Operating Systems are now immune from being used in this attack, Some popular systems are still vulnerable; making the idle scan still very effective. Once a successful scan is completed there is no trace of the attackers IP address on the target's firewallFirewall (computing)
A firewall is a device or set of devices designed to permit or deny network transmissions based upon a set of rules and is frequently used to protect networks from unauthorized access while permitting legitimate communications to pass....
or Intrusion-detection system
Intrusion-detection system
An intrusion detection system is a device or software application that monitors network and/or system activities for malicious activities or policy violations and produces reports to a Management Station. Some systems may attempt to stop an intrusion attempt but this is neither required nor...
log. Another useful possibility is the chance of by-passing a firewall because you are scanning the target from the zombie's computer, which might have extra rights than the attacker's.
See also
- Computer securityComputer securityComputer security is a branch of computer technology known as information security as applied to computers and networks. The objective of computer security includes protection of information and property from theft, corruption, or natural disaster, while allowing the information and property to...
- Computer system
- Content Vectoring ProtocolContent Vectoring ProtocolContent Vectoring Protocol is a protocol for filtering data that is crossing a firewall into an external scanning device. An example of this is where all HTTP traffic is virus-scanned before being sent out to the user....
- Port scannerPort scannerA port scanner is a software application designed to probe a server or host for open ports. This is often used by administrators to verify security policies of their networks and by attackers to identify running services on a host with the view to compromise it.A port scan or portscan is "An attack...
- Cracking
- Service scanService scanOn computer networks, a service scan identifies the services running on a list of open ports. This is closely tied to port scanning and some tools support both...
- TCPTransmission Control ProtocolThe Transmission Control Protocol is one of the core protocols of the Internet Protocol Suite. TCP is one of the two original components of the suite, complementing the Internet Protocol , and therefore the entire suite is commonly referred to as TCP/IP...
- Vulnerability scannerVulnerability scannerA vulnerability scanner is a computer program designed to assess computers, computer systems, networks or applications for weaknesses. There are a number of types of vulnerability scanners available today, distinguished from one another by a focus on particular targets...
External links
- Insecure.org/nmap/idlescan - An in-depth article on idle scanning
- Insecure.org - Official site of Nmap
- Hping.org - Official site of Hping
- Nmap-Online.com - An online Nmap scanner
- Techtarget.com - An article on idle scanning
- Seclists.org - Original bugtraq post
- ANTH Blog - Idle scans using public services

