
OpenBSD
Encyclopedia
OpenBSD is a Unix-like
computer operating system
descended from Berkeley Software Distribution
(BSD), a Unix
derivative developed at the University of California, Berkeley
. It was forked
from NetBSD
by project leader Theo de Raadt
in late 1995. The project is widely known for the developers' insistence on open-source code and quality documentation, uncompromising position on software licensing
, and focus on security
and code correctness. The project is coordinated from de Raadt's home in Calgary
, Alberta, Canada. Its logo and mascot is a pufferfish
named Puffy.
OpenBSD includes a number of security features absent or optional in other operating systems, and has a tradition in which developers audit
the source code for software bug
s and security problems. The project maintains strict policies on licensing and prefers the open-source BSD licence and its variants—in the past this has led to a comprehensive license audit and moves to remove or replace code under licences found less acceptable.
As with most other BSD-based operating systems, the OpenBSD kernel and userland programs, such as the shell
and common tools like cat
and ps
, are developed together in one source code repository. Third-party software is available as binary packages or may be built from source using the ports tree
.
The OpenBSD project maintains ports for 17 different hardware
platforms
, including the DEC Alpha
, Intel i386
, Hewlett-Packard
PA-RISC
, AMD AMD64 and Motorola 68000
processors, Apple
's PowerPC
machines, Sun
SPARC
and SPARC64
-based computers, the VAX
and the Sharp Zaurus
.
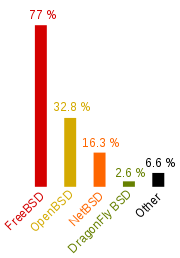 In December 1994, NetBSD co-founder Theo de Raadt
In December 1994, NetBSD co-founder Theo de Raadt
was asked to resign from his position as a senior developer and member of the NetBSD core team. The reason for this is not wholly clear, although there are claims that it was due to personality clashes within the NetBSD project and on its mailing lists
. De Raadt has been criticized for having a sometimes abrasive personality: in his book, Free For All, Peter Wayner claims that de Raadt "began to rub some people the wrong way" before the split from NetBSD; Linus Torvalds
has described him as "difficult"; and an interviewer admits to being "apprehensive" before meeting him. Many have different feelings: the same interviewer describes de Raadt's "transformation" on founding OpenBSD and his "desire to take care of his team," some find his straightforwardness refreshing, and few deny he is a talented coder
and security "guru".
In October 1995, de Raadt founded OpenBSD, a new project forked from NetBSD 1.0. The initial release, OpenBSD 1.2, was made in July 1996, followed in October of the same year by OpenBSD 2.0. Since then, the project has followed a schedule of a release every six months, each of which is maintained and supported for one year. The latest release, OpenBSD 5.0, appeared on November 1, 2011.
On 25 July 2007, OpenBSD developer Bob Beck announced the formation of the OpenBSD Foundation
, a Canadian not-for-profit corporation formed to "act as a single point of contact for persons and organizations requiring a legal entity to deal with when they wish to support OpenBSD."
Just how widely OpenBSD is used is hard to ascertain: its developers neither publish nor collect usage statistics, and there are few other sources of information. In September 2005, the nascent BSD Certification Group performed a usage survey which revealed that 32.8% of BSD users (1420 of 4330 respondents) were using OpenBSD, placing it second of the four major BSD variants, behind FreeBSD
with 77% and ahead of NetBSD with 16.3%. The DistroWatch
website
, well-known in the Linux
community and often used as a reference for popularity, publishes page hits
for each of the Linux distribution
s and other operating systems it covers. As of June 2011, using a data span of the last six months it placed FreeBSD in 15th place with 484 hits per day; PC-BSD in 24th place with 346 hits per day; GhostBSD in 53rd place with 171 hits, OpenBSD in 58th place with 164 hits per day; DragonFly in 62nd place with 142 hits per day; and NetBSD in 100th place with 94 hits per day.
server. This was the first of its kind in the software development world: at the time, the tradition was for only a small team of developers to have access to a project's source repository. Craner and de Raadt concluded that this practice "runs counter to the open source philosophy" and is inconvenient to contributors. de Raadt's decision allowed "users to take a more active role", and signaled the project's belief in open and public access to source code.
A revealing incident regarding open documentation occurred in March 2005, when de Raadt posted a message to the openbsd-misc mailing list. He announced that after four months of discussion, Adaptec
had not disclosed the documentation required to improve the OpenBSD drivers
for its AAC RAID controllers
. As in similar circumstances in the past, he encouraged the OpenBSD community to become involved and express their opinion to Adaptec. Shortly after this, FreeBSD committer
, former Adaptec employee and author of the FreeBSD AAC RAID support Scott Long, castigated de Raadt on the OSNews
website for not contacting him directly regarding the issues with Adaptec. This caused the discussion to spill over onto the freebsd-questions mailing list, where the OpenBSD project leader countered by claiming that he had received no previous offer of help from Scott Long nor been referred to him by Adaptec. The debate was amplified by disagreements between members of the two camps regarding the use of binary blob
drivers and non-disclosure agreement
s (NDAs): OpenBSD developers do not permit the inclusion of closed source binary drivers in the source tree and are reluctant to sign NDAs. However, the FreeBSD project has a different policy and much of the Adaptec RAID management code Scott Long proposed as assistance for OpenBSD was closed source or written under an NDA. As no documentation was forthcoming before the deadline for the release of OpenBSD 3.7, support for Adaptec AAC RAID controllers was removed from the standard OpenBSD kernel.
The OpenBSD policy on openness extends to hardware documentation: in the slides for a December 2006 presentation, de Raadt explained that without it "developers often make mistakes writing drivers", and pointed out that "the [oh my god, I got it to work] rush is harder to achieve, and some developers just give up". He went on to say that vendor binary drivers are unacceptable to OpenBSD, that they have "no trust of vendor binaries running in our kernel" and that there is "no way to fix [them] ... when they break".
s", which permitted a "relatively un-encumbered Unix source distribution". To this end, the Internet Systems Consortium (ISC) licence, a simplified version of the BSD licence with wording removed that is unnecessary under the Berne convention
, is preferred for new code, but the MIT
or BSD licences are accepted. The widely used GNU General Public License
is considered overly restrictive in comparison with these.
In June 2001, triggered by concerns over Darren Reed's modification of IPFilter's licence wording, a systematic licence audit of the OpenBSD ports and source trees was undertaken. Code in more than a hundred files throughout the system was found to be unlicensed, ambiguously licensed or in use against the terms of the licence. To ensure that all licences were properly adhered to, an attempt was made to contact all the relevant copyright holders: some pieces of code were removed, many were replaced, and others, including the multicast
routing
tools, mrinfo and map-mbone, which were licensed by Xerox
for research only, were relicensed so that OpenBSD could continue to use them; also removed during this audit was all software produced by Daniel J. Bernstein
. At the time, Bernstein requested that all modified versions of his code be approved by him prior to redistribution, a requirement to which OpenBSD developers were unwilling to devote time or effort. The removal led to a clash with Bernstein who felt the removal of his software to be uncalled for. He cited the Netscape
web browser
as much less freely licensed and accused the OpenBSD developers of hypocrisy for permitting Netscape to remain while removing his software. The OpenBSD project's stance was that Netscape, although not open source, had licence conditions that could be more easily met. They asserted that Bernstein's demand for control of derivatives would lead to a great deal of additional work and that removal was the most appropriate way to comply with his requirements.
The OpenBSD team has developed software from scratch, or adopted suitable existing software, because of licence concerns. Of particular note is the development, after licence restrictions were imposed on IPFilter
, of the pf
packet filter, which first appeared in OpenBSD 3.0 and is now available in DragonFly BSD
, NetBSD and FreeBSD. OpenBSD developers have also replaced GPL licensed tools (such as diff
, grep
and pkg-config
) with BSD licensed equivalents and founded new projects including the OpenBGPD
routing daemon and OpenNTPD
time service daemon. Also developed from scratch was the globally used software package OpenSSH.
), which was intended to find and attempt to exploit
possible software security flaws. This coincided well with de Raadt's own interest in security, so for a time the two cooperated, a relationship that was of particular use leading up to the release of OpenBSD 2.3 and helped to form security as the focal point of the project.
Until June 2002, the OpenBSD website featured the slogan:
In June 2002, Mark Dowd of Internet Security Systems
disclosed a bug in the OpenSSH
code implementing challenge-response
authentication
. This vulnerability in the OpenBSD default installation allowed an attacker remote access to the root
account, which was extremely serious not only to OpenBSD, but also to the large number of other operating systems that were using OpenSSH by that time. This problem necessitated the adjustment of the slogan on the OpenBSD website to:
The quote remained unchanged as time passed, until on March 13, 2007 when Alfredo Ortega of Core Security Technologies disclosed a network-related remote vulnerability. The quote was subsequently altered to:
This statement has been criticized because the default install contains few running services, and most users will install additional software. The project states that the default install is intentionally minimal to ensure novice users "do not need to become security experts overnight", which fits with open-source and code auditing practices argued to be important elements of a security system.
OpenBSD includes features designed to improve security. These include API
additions, such as the strlcat and strlcpy functions
; toolchain alterations, including a static bounds checker
; memory protection techniques to guard against invalid accesses, such as ProPolice and the W^X
(W xor X) page
protection feature; and cryptography
and randomization
features.
To reduce the risk of a vulnerability or misconfiguration allowing privilege escalation
, some programs have been written or adapted to make use of privilege separation
, privilege revocation
and chroot
ing. Privilege separation is a technique, pioneered on OpenBSD and inspired by the principle of least privilege
, where a program is split into two or more parts, one of which performs privileged operations and the other—almost always the bulk of the code—runs without privilege. Privilege revocation is similar and involves a program performing any necessary operations with the privileges it starts with then dropping them. Chrooting involves restricting an application to one section of the file system
, prohibiting it from accessing areas that contain private or system files. Developers have applied these features to OpenBSD versions of common applications, including tcpdump
and the Apache web server
.
OpenBSD developers were instrumental in the birth of—and the project continues to develop—OpenSSH
, a secure replacement for Telnet
. OpenSSH is based on the original SSH
suite and developed further by the OpenBSD team. It first appeared in OpenBSD 2.6 and is now the most popular SSH implementation, available on many operating systems.
The project has a policy of continually auditing code for problems, work that developer Marc Espie has described as "never finished ... more a question of process than of a specific bug being hunted". He went on to list several typical steps once a bug is found, including examining the entire source tree for the same and similar issues, "try[ing] to find out whether the documentation ought to be amended", and investigating whether "it's possible to augment the compiler
to warn against this specific problem".
Linux kernel
creator Linus Torvalds
has expressed the view that development efforts should be focused on fixing general problems rather than targeting security issues, as non-security bugs are more numerous ("all the boring normal bugs are _way_ more important, just because there's a lot more of them"). On July 15, 2008, he criticised the OpenBSD policy: "[T]hey make such a big deal about concentrating on security that they pretty much admit that nothing else matters to them". OpenBSD developer Marc Espie replied to Torvalds' statement: "It's a totally misinformed opinion ... [Fixing normal bugs] is exactly what people in the OpenBSD project do, all the time". Developer Artur Grabowski also expressed surprise: "That's the funniest part about this ... [Torvalds] was saying the same things we say".
On 11 December 2010, Gregory Perry sent an email to Theo de Raadt alleging that the FBI had paid some OpenBSD ex-developers 10 years previously to insert backdoors into the OpenBSD Cryptographic Framework. Theo de Raadt made the email public on 14 December by forwarding it to the openbsd-tech mailing list and suggested an audit of the IPsec
codebase. De Raadt's response was skeptical of the report and he invited all developers to independently review the relevant code. In the weeks that followed, bugs were fixed but no evidence of backdoors were found.
s and VPN
gateways.
Proprietary
systems from several manufacturers are based on OpenBSD, including devices from Armorlogic (Profense web application firewall), Calyptix Security, GeNUA mbH, RTMX Inc, and .vantronix GmbH. Code from many of the OpenBSD system tools has been used in recent versions of Microsoft
's Services for UNIX
, an extension to the Windows
operating system which provides some Unix-like functionality, originally based on 4.4BSD-Lite
. Core Force, a security product for Windows, is based on OpenBSD's pf firewall.
OpenBSD ships with the X window system
and is suitable for use on the desktop. Packages for popular desktop tools are available, including desktop environments GNOME
, KDE
, and Xfce
; web browsers Konqueror
, Mozilla Firefox
and Chromium
; and multimedia
programs MPlayer
, VLC media player
and xine
.
OpenBSD's performance and usability is occasionally criticised. Felix von Leitner
's performance and scalability
tests indicated that OpenBSD lagged behind other operating systems. In response, OpenBSD users and developers criticised von Leitner's objectivity and methodology, and asserted that although performance is given consideration, security and correct design are prioritised, with project member Nick Holland commenting: "It all boils down to what you consider important." OpenBSD is also a relatively small project, particularly when compared with FreeBSD and Linux, and developer time is sometimes seen as better spent on security enhancements than performance optimization. Critics of usability say that OpenBSD has a lack of user-friendly configuration tools, a bare default installation, and a "spartan" and "intimidating" installer. These see much the same rebuttals as performance: a preference for simplicity, reliability and security. As one reviewer puts it, "running an ultra-secure operating system can be a bit of work."
, and binary releases and development snapshots can be downloaded either by FTP
or HTTP
. Prepackaged CD-ROM
sets can be ordered online for a small fee, complete with an assortment of stickers and a copy of the release's theme song. These, with its artwork and other bonuses, are one of the project's few sources of income, funding hardware, bandwidth
and other expenses.
In common with other operating systems, OpenBSD provides a package management system
for easy installation and management of programs which are not part of the base operating system. Packages are binary files which are extracted, managed and removed using the package tools. On OpenBSD, the source of packages is the ports system, a collection of Makefiles and other infrastructure required to create packages. In OpenBSD, the ports and base operating system are developed and released together for each version: this means that the ports or packages released with, for example, 4.6 are not suitable for use with 4.5 and vice versa.
OpenBSD at first used the BSD daemon
mascot created by Phil Foglio
, updated by John Lasseter
and copyright Marshall Kirk McKusick
. Subsequent releases saw variations, eventually settling on Puffy, described as a pufferfish
. Since then Puffy has appeared on OpenBSD promotional material and featured in release songs and artwork. The promotional material of early OpenBSD releases did not have a cohesive theme or design but later the CD-ROMs, release songs, posters and tee-shirts for each release have been produced with a single style and theme, sometimes contributed to by Ty Semaka of the Plaid Tongued Devils
. These have become a part of OpenBSD advocacy
, with each release expanding a moral or political point important to the project, often through parody
. Past themes have included: in OpenBSD 3.8, the Hackers of the Lost RAID, a parody of Indiana Jones
linked to the new RAID tools featured as part of the release; The Wizard of OS, making its debut in OpenBSD 3.7, based on the work of Pink Floyd
and a parody of The Wizard of Oz
related to the project's recent wireless
work; and OpenBSD 3.3's Puff the Barbarian, including an 80s rock-style song and parody of Conan the Barbarian
, alluding to open documentation.
Unix-like
A Unix-like operating system is one that behaves in a manner similar to a Unix system, while not necessarily conforming to or being certified to any version of the Single UNIX Specification....
computer operating system
Operating system
An operating system is a set of programs that manage computer hardware resources and provide common services for application software. The operating system is the most important type of system software in a computer system...
descended from Berkeley Software Distribution
Berkeley Software Distribution
Berkeley Software Distribution is a Unix operating system derivative developed and distributed by the Computer Systems Research Group of the University of California, Berkeley, from 1977 to 1995...
(BSD), a Unix
Unix
Unix is a multitasking, multi-user computer operating system originally developed in 1969 by a group of AT&T employees at Bell Labs, including Ken Thompson, Dennis Ritchie, Brian Kernighan, Douglas McIlroy, and Joe Ossanna...
derivative developed at the University of California, Berkeley
University of California, Berkeley
The University of California, Berkeley , is a teaching and research university established in 1868 and located in Berkeley, California, USA...
. It was forked
Fork (software development)
In software engineering, a project fork happens when developers take a legal copy of source code from one software package and start independent development on it, creating a distinct piece of software...
from NetBSD
NetBSD
NetBSD is a freely available open source version of the Berkeley Software Distribution Unix operating system. It was the second open source BSD descendant to be formally released, after 386BSD, and continues to be actively developed. The NetBSD project is primarily focused on high quality design,...
by project leader Theo de Raadt
Theo de Raadt
Theo de Raadt , born May 19, 1968 in Pretoria, South Africa, is a software engineer who lives in Calgary, Alberta, Canada. He is the founder and leader of the OpenBSD and OpenSSH projects, and was a founding member of the NetBSD project.- Childhood :...
in late 1995. The project is widely known for the developers' insistence on open-source code and quality documentation, uncompromising position on software licensing
Software licensing
A software license is a legal instrument governing the usage or redistribution of software. All software is copyright protected, except material in the public domain. Contractual confidentiality is another way of protecting software...
, and focus on security
Computer insecurity
Computer insecurity refers to the concept that a computer system is always vulnerable to attack, and that this fact creates a constant battle between those looking to improve security, and those looking to circumvent security.-Security and systems design:...
and code correctness. The project is coordinated from de Raadt's home in Calgary
Calgary
Calgary is a city in the Province of Alberta, Canada. It is located in the south of the province, in an area of foothills and prairie, approximately east of the front ranges of the Canadian Rockies...
, Alberta, Canada. Its logo and mascot is a pufferfish
Pufferfish
Tetraodontidae is a family of primarily marine and estuarine fish of the Tetraodontiformes order. The family includes many familiar species which are variously called pufferfish, balloonfish, blowfish, bubblefish, globefish, swellfish, toadfish, toadies, honey toads, sugar toads, and sea squab...
named Puffy.
OpenBSD includes a number of security features absent or optional in other operating systems, and has a tradition in which developers audit
Code audit
A software code audit is a comprehensive analysis of source code in a programming project with the intent of discovering bugs, security breaches or violations of programming conventions. It is an integral part of the defensive programming paradigm, which attempts to reduce errors before the...
the source code for software bug
Software bug
A software bug is the common term used to describe an error, flaw, mistake, failure, or fault in a computer program or system that produces an incorrect or unexpected result, or causes it to behave in unintended ways. Most bugs arise from mistakes and errors made by people in either a program's...
s and security problems. The project maintains strict policies on licensing and prefers the open-source BSD licence and its variants—in the past this has led to a comprehensive license audit and moves to remove or replace code under licences found less acceptable.
As with most other BSD-based operating systems, the OpenBSD kernel and userland programs, such as the shell
Unix shell
A Unix shell is a command-line interpreter or shell that provides a traditional user interface for the Unix operating system and for Unix-like systems...
and common tools like cat
Cat (Unix)
The cat command is a standard Unix program used to concatenate and display files. The name is from catenate, a synonym of concatenate.- Specification :...
and ps
Ps (Unix)
In most Unix-like operating systems, the ps program displays the currently-running processes. A related Unix utility named top provides a real-time view of the running processes....
, are developed together in one source code repository. Third-party software is available as binary packages or may be built from source using the ports tree
Ports collection
Ports collections are the sets of makefiles and patches provided by the BSD-based operating systems, FreeBSD, NetBSD, and OpenBSD, as a simple method of installing software or creating binary packages...
.
The OpenBSD project maintains ports for 17 different hardware
Computer hardware
Personal computer hardware are component devices which are typically installed into or peripheral to a computer case to create a personal computer upon which system software is installed including a firmware interface such as a BIOS and an operating system which supports application software that...
platforms
Platform (computing)
A computing platform includes some sort of hardware architecture and a software framework , where the combination allows software, particularly application software, to run...
, including the DEC Alpha
DEC Alpha
Alpha, originally known as Alpha AXP, is a 64-bit reduced instruction set computer instruction set architecture developed by Digital Equipment Corporation , designed to replace the 32-bit VAX complex instruction set computer ISA and its implementations. Alpha was implemented in microprocessors...
, Intel i386
Intel 80386
The Intel 80386, also known as the i386, or just 386, was a 32-bit microprocessor introduced by Intel in 1985. The first versions had 275,000 transistors and were used as the central processing unit of many workstations and high-end personal computers of the time...
, Hewlett-Packard
Hewlett-Packard
Hewlett-Packard Company or HP is an American multinational information technology corporation headquartered in Palo Alto, California, USA that provides products, technologies, softwares, solutions and services to consumers, small- and medium-sized businesses and large enterprises, including...
PA-RISC
PA-RISC
PA-RISC is an instruction set architecture developed by Hewlett-Packard. As the name implies, it is a reduced instruction set computer architecture, where the PA stands for Precision Architecture...
, AMD AMD64 and Motorola 68000
Motorola 68000
The Motorola 68000 is a 16/32-bit CISC microprocessor core designed and marketed by Freescale Semiconductor...
processors, Apple
Apple Computer
Apple Inc. is an American multinational corporation that designs and markets consumer electronics, computer software, and personal computers. The company's best-known hardware products include the Macintosh line of computers, the iPod, the iPhone and the iPad...
's PowerPC
PowerPC
PowerPC is a RISC architecture created by the 1991 Apple–IBM–Motorola alliance, known as AIM...
machines, Sun
Sun Microsystems
Sun Microsystems, Inc. was a company that sold :computers, computer components, :computer software, and :information technology services. Sun was founded on February 24, 1982...
SPARC
SPARC
SPARC is a RISC instruction set architecture developed by Sun Microsystems and introduced in mid-1987....
and SPARC64
SPARC64
SPARC64 is a microprocessor developed by HAL Computer Systems and fabricated by Fujitsu. It implements the SPARC V9 instruction set architecture , the first microprocessor to do so. SPARC64 was HAL's first microprocessor and was the first in the SPARC64 brand. It operates at 101 and 118 MHz...
-based computers, the VAX
VAX
VAX was an instruction set architecture developed by Digital Equipment Corporation in the mid-1970s. A 32-bit complex instruction set computer ISA, it was designed to extend or replace DEC's various Programmed Data Processor ISAs...
and the Sharp Zaurus
Sharp Zaurus
The Sharp Zaurus is the name of a series of Personal Digital Assistant made by Sharp Corporation. The Zaurus was the most popular PDA during the 1990s in Japan and was based on a proprietary operating system. The first Sharp PDA to use the Linux operating system was the SL-5000D, running the...
.
History and popularity
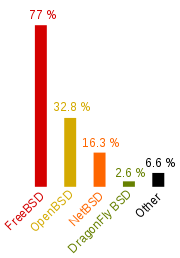
Theo de Raadt
Theo de Raadt , born May 19, 1968 in Pretoria, South Africa, is a software engineer who lives in Calgary, Alberta, Canada. He is the founder and leader of the OpenBSD and OpenSSH projects, and was a founding member of the NetBSD project.- Childhood :...
was asked to resign from his position as a senior developer and member of the NetBSD core team. The reason for this is not wholly clear, although there are claims that it was due to personality clashes within the NetBSD project and on its mailing lists
Electronic mailing list
An electronic mailing list is a special usage of email that allows for widespread distribution of information to many Internet users. It is similar to a traditional mailing list — a list of names and addresses — as might be kept by an organization for sending publications to...
. De Raadt has been criticized for having a sometimes abrasive personality: in his book, Free For All, Peter Wayner claims that de Raadt "began to rub some people the wrong way" before the split from NetBSD; Linus Torvalds
Linus Torvalds
Linus Benedict Torvalds is a Finnish software engineer and hacker, best known for having initiated the development of the open source Linux kernel. He later became the chief architect of the Linux kernel, and now acts as the project's coordinator...
has described him as "difficult"; and an interviewer admits to being "apprehensive" before meeting him. Many have different feelings: the same interviewer describes de Raadt's "transformation" on founding OpenBSD and his "desire to take care of his team," some find his straightforwardness refreshing, and few deny he is a talented coder
Programmer
A programmer, computer programmer or coder is someone who writes computer software. The term computer programmer can refer to a specialist in one area of computer programming or to a generalist who writes code for many kinds of software. One who practices or professes a formal approach to...
and security "guru".
In October 1995, de Raadt founded OpenBSD, a new project forked from NetBSD 1.0. The initial release, OpenBSD 1.2, was made in July 1996, followed in October of the same year by OpenBSD 2.0. Since then, the project has followed a schedule of a release every six months, each of which is maintained and supported for one year. The latest release, OpenBSD 5.0, appeared on November 1, 2011.
On 25 July 2007, OpenBSD developer Bob Beck announced the formation of the OpenBSD Foundation
OpenBSD Foundation
The OpenBSD Foundation is a Canadian federal non-profit organization founded by the OpenBSD project "as a single point of contact for persons and organizations requiring a legal entity to deal with when they wish to support OpenBSD." It also serves as a legal safeguard over other projects which are...
, a Canadian not-for-profit corporation formed to "act as a single point of contact for persons and organizations requiring a legal entity to deal with when they wish to support OpenBSD."
Just how widely OpenBSD is used is hard to ascertain: its developers neither publish nor collect usage statistics, and there are few other sources of information. In September 2005, the nascent BSD Certification Group performed a usage survey which revealed that 32.8% of BSD users (1420 of 4330 respondents) were using OpenBSD, placing it second of the four major BSD variants, behind FreeBSD
FreeBSD
FreeBSD is a free Unix-like operating system descended from AT&T UNIX via BSD UNIX. Although for legal reasons FreeBSD cannot be called “UNIX”, as the direct descendant of BSD UNIX , FreeBSD’s internals and system APIs are UNIX-compliant...
with 77% and ahead of NetBSD with 16.3%. The DistroWatch
DistroWatch
DistroWatch is a website which provides news, popularity rankings, and other general information about various Linux distributions as well as other free software/open source Unix-like operating systems such as OpenSolaris, MINIX and BSD. It now contains information on several hundred distributions...
website
Website
A website, also written as Web site, web site, or simply site, is a collection of related web pages containing images, videos or other digital assets. A website is hosted on at least one web server, accessible via a network such as the Internet or a private local area network through an Internet...
, well-known in the Linux
Linux
Linux is a Unix-like computer operating system assembled under the model of free and open source software development and distribution. The defining component of any Linux system is the Linux kernel, an operating system kernel first released October 5, 1991 by Linus Torvalds...
community and often used as a reference for popularity, publishes page hits
Hit (internet)
A hit is a request to a web server for a file . When a web page is uploaded from a server the number of "hits" or "page hits" is equal to the number of files requested. Therefore, one page load does not always equal one hit because often pages are made up of other images and other files which stack...
for each of the Linux distribution
Linux distribution
A Linux distribution is a member of the family of Unix-like operating systems built on top of the Linux kernel. Such distributions are operating systems including a large collection of software applications such as word processors, spreadsheets, media players, and database applications...
s and other operating systems it covers. As of June 2011, using a data span of the last six months it placed FreeBSD in 15th place with 484 hits per day; PC-BSD in 24th place with 346 hits per day; GhostBSD in 53rd place with 171 hits, OpenBSD in 58th place with 164 hits per day; DragonFly in 62nd place with 142 hits per day; and NetBSD in 100th place with 94 hits per day.
Open source and open documentation
When OpenBSD was created, Theo de Raadt decided that the source should be easily available for anyone to read at any time, so, with the assistance of Chuck Cranor, he set up a public, anonymous CVSConcurrent Versions System
The Concurrent Versions System , also known as the Concurrent Versioning System, is a client-server free software revision control system in the field of software development. Version control system software keeps track of all work and all changes in a set of files, and allows several developers ...
server. This was the first of its kind in the software development world: at the time, the tradition was for only a small team of developers to have access to a project's source repository. Craner and de Raadt concluded that this practice "runs counter to the open source philosophy" and is inconvenient to contributors. de Raadt's decision allowed "users to take a more active role", and signaled the project's belief in open and public access to source code.
A revealing incident regarding open documentation occurred in March 2005, when de Raadt posted a message to the openbsd-misc mailing list. He announced that after four months of discussion, Adaptec
Adaptec
Adaptec is a computer hardware brand owned by PMC-Sierra that is used on some of its host adapters for connecting storage devices to computers. The production line of Adaptec is in Indonesia. Products are made to interface with SCSI, Serial ATA, and Serial attached SCSI. Some of its host adapters...
had not disclosed the documentation required to improve the OpenBSD drivers
Device driver
In computing, a device driver or software driver is a computer program allowing higher-level computer programs to interact with a hardware device....
for its AAC RAID controllers
Disk array controller
A disk array controller is a device which manages the physical disk drives and presents them to the computer as logical units. It almost always implements hardware RAID, thus it is sometimes referred to as RAID controller. It also often provides additional disk cache.A disk array controller name is...
. As in similar circumstances in the past, he encouraged the OpenBSD community to become involved and express their opinion to Adaptec. Shortly after this, FreeBSD committer
Committer
A committer is an individual who is able to modify the source code of a particular piece of open-source software.-Common Roles:Project committers are usually the lead developers of a project and usually are the ones responsible for the majority of changes and as such as seen as trusted members of...
, former Adaptec employee and author of the FreeBSD AAC RAID support Scott Long, castigated de Raadt on the OSNews
OSNews
OSNews is a computing news web site with a focus on operating systems and their related technologies that launched in 1997. The content is managed by a group of editors and the owner. The managing editor of OSNews is Thom Holwerda . David Adams is a publisher for OSNews, and also contributes...
website for not contacting him directly regarding the issues with Adaptec. This caused the discussion to spill over onto the freebsd-questions mailing list, where the OpenBSD project leader countered by claiming that he had received no previous offer of help from Scott Long nor been referred to him by Adaptec. The debate was amplified by disagreements between members of the two camps regarding the use of binary blob
Binary blob
In the free software community, binary blob is a pejorative term for an object file loaded into the kernel of a open source operating system without publicly available source code...
drivers and non-disclosure agreement
Non-disclosure agreement
A non-disclosure agreement , also known as a confidentiality agreement , confidential disclosure agreement , proprietary information agreement , or secrecy agreement, is a legal contract between at least two parties that outlines confidential material, knowledge, or information that the parties...
s (NDAs): OpenBSD developers do not permit the inclusion of closed source binary drivers in the source tree and are reluctant to sign NDAs. However, the FreeBSD project has a different policy and much of the Adaptec RAID management code Scott Long proposed as assistance for OpenBSD was closed source or written under an NDA. As no documentation was forthcoming before the deadline for the release of OpenBSD 3.7, support for Adaptec AAC RAID controllers was removed from the standard OpenBSD kernel.
The OpenBSD policy on openness extends to hardware documentation: in the slides for a December 2006 presentation, de Raadt explained that without it "developers often make mistakes writing drivers", and pointed out that "the [oh my god, I got it to work] rush is harder to achieve, and some developers just give up". He went on to say that vendor binary drivers are unacceptable to OpenBSD, that they have "no trust of vendor binaries running in our kernel" and that there is "no way to fix [them] ... when they break".
Licensing
A goal of the OpenBSD project is to "maintain the spirit of the original Berkeley Unix copyrightCopyright
Copyright is a legal concept, enacted by most governments, giving the creator of an original work exclusive rights to it, usually for a limited time...
s", which permitted a "relatively un-encumbered Unix source distribution". To this end, the Internet Systems Consortium (ISC) licence, a simplified version of the BSD licence with wording removed that is unnecessary under the Berne convention
Berne Convention for the Protection of Literary and Artistic Works
The Berne Convention for the Protection of Literary and Artistic Works, usually known as the Berne Convention, is an international agreement governing copyright, which was first accepted in Berne, Switzerland in 1886.- Content :...
, is preferred for new code, but the MIT
MIT License
The MIT License is a free software license originating at the Massachusetts Institute of Technology . It is a permissive license, meaning that it permits reuse within proprietary software provided all copies of the licensed software include a copy of the MIT License terms...
or BSD licences are accepted. The widely used GNU General Public License
GNU General Public License
The GNU General Public License is the most widely used free software license, originally written by Richard Stallman for the GNU Project....
is considered overly restrictive in comparison with these.
In June 2001, triggered by concerns over Darren Reed's modification of IPFilter's licence wording, a systematic licence audit of the OpenBSD ports and source trees was undertaken. Code in more than a hundred files throughout the system was found to be unlicensed, ambiguously licensed or in use against the terms of the licence. To ensure that all licences were properly adhered to, an attempt was made to contact all the relevant copyright holders: some pieces of code were removed, many were replaced, and others, including the multicast
Multicast
In computer networking, multicast is the delivery of a message or information to a group of destination computers simultaneously in a single transmission from the source creating copies automatically in other network elements, such as routers, only when the topology of the network requires...
routing
Routing
Routing is the process of selecting paths in a network along which to send network traffic. Routing is performed for many kinds of networks, including the telephone network , electronic data networks , and transportation networks...
tools, mrinfo and map-mbone, which were licensed by Xerox
Xerox
Xerox Corporation is an American multinational document management corporation that produced and sells a range of color and black-and-white printers, multifunction systems, photo copiers, digital production printing presses, and related consulting services and supplies...
for research only, were relicensed so that OpenBSD could continue to use them; also removed during this audit was all software produced by Daniel J. Bernstein
Daniel J. Bernstein
Daniel Julius Bernstein is a mathematician, cryptologist, programmer, and professor of mathematics at the University of Illinois at Chicago...
. At the time, Bernstein requested that all modified versions of his code be approved by him prior to redistribution, a requirement to which OpenBSD developers were unwilling to devote time or effort. The removal led to a clash with Bernstein who felt the removal of his software to be uncalled for. He cited the Netscape
Netscape
Netscape Communications is a US computer services company, best known for Netscape Navigator, its web browser. When it was an independent company, its headquarters were in Mountain View, California...
web browser
Web browser
A web browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web. An information resource is identified by a Uniform Resource Identifier and may be a web page, image, video, or other piece of content...
as much less freely licensed and accused the OpenBSD developers of hypocrisy for permitting Netscape to remain while removing his software. The OpenBSD project's stance was that Netscape, although not open source, had licence conditions that could be more easily met. They asserted that Bernstein's demand for control of derivatives would lead to a great deal of additional work and that removal was the most appropriate way to comply with his requirements.
The OpenBSD team has developed software from scratch, or adopted suitable existing software, because of licence concerns. Of particular note is the development, after licence restrictions were imposed on IPFilter
IPFilter
IPFilter is an open source software package that provides firewall services and network address translation for many UNIX-like operating systems. The author and software maintainer is Darren Reed. IPFilter supports both IPv4 and IPv6 protocols, and is a stateful firewall.IPFilter is delivered...
, of the pf
PF (firewall)
PF is a BSD licensed stateful packet filter, a central piece of software for firewalling. It is comparable to iptables, ipfw and ipfilter...
packet filter, which first appeared in OpenBSD 3.0 and is now available in DragonFly BSD
DragonFly BSD
DragonFly BSD is a free Unix-like operating system created as a fork of FreeBSD 4.8. Matthew Dillon, an Amiga developer in the late 1980s and early 1990s and a FreeBSD developer between 1994 and 2003, began work on DragonFly BSD in June 2003 and announced it on the FreeBSD mailing lists on July...
, NetBSD and FreeBSD. OpenBSD developers have also replaced GPL licensed tools (such as diff
Diff
In computing, diff is a file comparison utility that outputs the differences between two files. It is typically used to show the changes between one version of a file and a former version of the same file. Diff displays the changes made per line for text files. Modern implementations also...
, grep
Grep
grep is a command-line text-search utility originally written for Unix. The name comes from the ed command g/re/p...
and pkg-config
Pkg-config
pkg-config is computer software that provides a unified interface for querying installed libraries for the purpose of compiling software from its source code. pkg-config was originally designed for Linux but is now also available for the various BSDs, Microsoft Windows, Mac OS X, and Solaris.It...
) with BSD licensed equivalents and founded new projects including the OpenBGPD
OpenBGPD
OpenBGPD allows general purpose computers to be used as routers. It is a Unix system daemon that provides a free, open-source implementation of the Border Gateway Protocol version 4. This allows a machine to exchange routes with other systems that speak BGP....
routing daemon and OpenNTPD
OpenNTPD
OpenNTPD is a Unix system daemon implementing the Network Time Protocol to synchronize the local clock of a computer system with remote NTP servers. It is also able to act as an NTP server to NTP-compatible clients....
time service daemon. Also developed from scratch was the globally used software package OpenSSH.
Security and code auditing
Shortly after OpenBSD's creation, Theo de Raadt was contacted by a local security software company named Secure Networks, Inc. or SNI. They were developing a "network security auditing tool" called Ballista (later renamed to Cybercop Scanner after SNI was purchased by Network AssociatesMcAfee
McAfee, Inc. is a computer security company headquartered in Santa Clara, California, USA. It markets software and services to home users, businesses and the public sector. On August 19, 2010, electronics company Intel agreed to purchase McAfee for $7.68 billion...
), which was intended to find and attempt to exploit
Exploit (computer security)
An exploit is a piece of software, a chunk of data, or sequence of commands that takes advantage of a bug, glitch or vulnerability in order to cause unintended or unanticipated behavior to occur on computer software, hardware, or something electronic...
possible software security flaws. This coincided well with de Raadt's own interest in security, so for a time the two cooperated, a relationship that was of particular use leading up to the release of OpenBSD 2.3 and helped to form security as the focal point of the project.
Until June 2002, the OpenBSD website featured the slogan:
In June 2002, Mark Dowd of Internet Security Systems
Internet Security Systems
IBM Internet Security Systems is a security software provider which was founded in 1994 as Internet Security Systems, and is often known simply as ISS or ISSX...
disclosed a bug in the OpenSSH
OpenSSH
OpenSSH is a set of computer programs providing encrypted communication sessions over a computer network using the SSH protocol...
code implementing challenge-response
Challenge-response authentication
In computer security, challenge-response authentication is a family of protocols in which one party presents a question and another party must provide a valid answer to be authenticated....
authentication
Authentication
Authentication is the act of confirming the truth of an attribute of a datum or entity...
. This vulnerability in the OpenBSD default installation allowed an attacker remote access to the root
Superuser
On many computer operating systems, the superuser is a special user account used for system administration. Depending on the operating system, the actual name of this account might be: root, administrator or supervisor....
account, which was extremely serious not only to OpenBSD, but also to the large number of other operating systems that were using OpenSSH by that time. This problem necessitated the adjustment of the slogan on the OpenBSD website to:
The quote remained unchanged as time passed, until on March 13, 2007 when Alfredo Ortega of Core Security Technologies disclosed a network-related remote vulnerability. The quote was subsequently altered to:
This statement has been criticized because the default install contains few running services, and most users will install additional software. The project states that the default install is intentionally minimal to ensure novice users "do not need to become security experts overnight", which fits with open-source and code auditing practices argued to be important elements of a security system.
OpenBSD includes features designed to improve security. These include API
Application programming interface
An application programming interface is a source code based specification intended to be used as an interface by software components to communicate with each other...
additions, such as the strlcat and strlcpy functions
Subroutine
In computer science, a subroutine is a portion of code within a larger program that performs a specific task and is relatively independent of the remaining code....
; toolchain alterations, including a static bounds checker
Static code analysis
Static program analysis is the analysis of computer software that is performed without actually executing programs built from that software In most cases the analysis is performed on some version of the source code and in the other cases some form of the object code...
; memory protection techniques to guard against invalid accesses, such as ProPolice and the W^X
W^X
W^X is the name of a security feature present in the OpenBSD operating system. It is a memory protection policy whereby every page in a process' address space is either writable or executable, but not both simultaneously...
(W xor X) page
Paging
In computer operating systems, paging is one of the memory-management schemes by which a computer can store and retrieve data from secondary storage for use in main memory. In the paging memory-management scheme, the operating system retrieves data from secondary storage in same-size blocks called...
protection feature; and cryptography
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
and randomization
Randomization
Randomization is the process of making something random; this means:* Generating a random permutation of a sequence .* Selecting a random sample of a population ....
features.
To reduce the risk of a vulnerability or misconfiguration allowing privilege escalation
Privilege escalation
Privilege escalation is the act of exploiting a bug, design flaw or configuration oversight in an operating system or software application to gain elevated access to resources that are normally protected from an application or user...
, some programs have been written or adapted to make use of privilege separation
Privilege separation
In computer programming and computer security, privilege separation is a technique in which a program is divided into parts which are limited to the specific privileges they require in order to perform a specific task...
, privilege revocation
Privilege revocation
Privilege revocation is the act of an entity giving up some, or all of, the privileges they possess, or some authority taking those rights away.- Information theory :...
and chroot
Chroot
A chroot on Unix operating systems is an operation that changes the apparent root directory for the current running process and its children. A program that is run in such a modified environment cannot name files outside the designated directory tree. The term "chroot" may refer to the chroot...
ing. Privilege separation is a technique, pioneered on OpenBSD and inspired by the principle of least privilege
Principle of least privilege
In information security, computer science, and other fields, the principle of least privilege, also known as the principle of minimal privilege or just least privilege, requires that in a particular abstraction layer of a computing environment, every module must be able to access only the...
, where a program is split into two or more parts, one of which performs privileged operations and the other—almost always the bulk of the code—runs without privilege. Privilege revocation is similar and involves a program performing any necessary operations with the privileges it starts with then dropping them. Chrooting involves restricting an application to one section of the file system
File system
A file system is a means to organize data expected to be retained after a program terminates by providing procedures to store, retrieve and update data, as well as manage the available space on the device which contain it. A file system organizes data in an efficient manner and is tuned to the...
, prohibiting it from accessing areas that contain private or system files. Developers have applied these features to OpenBSD versions of common applications, including tcpdump
Tcpdump
tcpdump is a common packet analyzer that runs under the command line. It allows the user to intercept and display TCP/IP and other packets being transmitted or received over a network to which the computer is attached...
and the Apache web server
Web server
Web server can refer to either the hardware or the software that helps to deliver content that can be accessed through the Internet....
.
OpenBSD developers were instrumental in the birth of—and the project continues to develop—OpenSSH
OpenSSH
OpenSSH is a set of computer programs providing encrypted communication sessions over a computer network using the SSH protocol...
, a secure replacement for Telnet
TELNET
Telnet is a network protocol used on the Internet or local area networks to provide a bidirectional interactive text-oriented communications facility using a virtual terminal connection...
. OpenSSH is based on the original SSH
Secure Shell
Secure Shell is a network protocol for secure data communication, remote shell services or command execution and other secure network services between two networked computers that it connects via a secure channel over an insecure network: a server and a client...
suite and developed further by the OpenBSD team. It first appeared in OpenBSD 2.6 and is now the most popular SSH implementation, available on many operating systems.
The project has a policy of continually auditing code for problems, work that developer Marc Espie has described as "never finished ... more a question of process than of a specific bug being hunted". He went on to list several typical steps once a bug is found, including examining the entire source tree for the same and similar issues, "try[ing] to find out whether the documentation ought to be amended", and investigating whether "it's possible to augment the compiler
Compiler
A compiler is a computer program that transforms source code written in a programming language into another computer language...
to warn against this specific problem".
Linux kernel
Linux kernel
The Linux kernel is an operating system kernel used by the Linux family of Unix-like operating systems. It is one of the most prominent examples of free and open source software....
creator Linus Torvalds
Linus Torvalds
Linus Benedict Torvalds is a Finnish software engineer and hacker, best known for having initiated the development of the open source Linux kernel. He later became the chief architect of the Linux kernel, and now acts as the project's coordinator...
has expressed the view that development efforts should be focused on fixing general problems rather than targeting security issues, as non-security bugs are more numerous ("all the boring normal bugs are _way_ more important, just because there's a lot more of them"). On July 15, 2008, he criticised the OpenBSD policy: "[T]hey make such a big deal about concentrating on security that they pretty much admit that nothing else matters to them". OpenBSD developer Marc Espie replied to Torvalds' statement: "It's a totally misinformed opinion ... [Fixing normal bugs] is exactly what people in the OpenBSD project do, all the time". Developer Artur Grabowski also expressed surprise: "That's the funniest part about this ... [Torvalds] was saying the same things we say".
On 11 December 2010, Gregory Perry sent an email to Theo de Raadt alleging that the FBI had paid some OpenBSD ex-developers 10 years previously to insert backdoors into the OpenBSD Cryptographic Framework. Theo de Raadt made the email public on 14 December by forwarding it to the openbsd-tech mailing list and suggested an audit of the IPsec
IPsec
Internet Protocol Security is a protocol suite for securing Internet Protocol communications by authenticating and encrypting each IP packet of a communication session...
codebase. De Raadt's response was skeptical of the report and he invited all developers to independently review the relevant code. In the weeks that followed, bugs were fixed but no evidence of backdoors were found.
Uses
OpenBSD's security enhancements, built-in cryptography and the pf packet filter suit it for use in the security industry, for example on firewalls, intrusion-detection systemIntrusion-detection system
An intrusion detection system is a device or software application that monitors network and/or system activities for malicious activities or policy violations and produces reports to a Management Station. Some systems may attempt to stop an intrusion attempt but this is neither required nor...
s and VPN
Virtual private network
A virtual private network is a network that uses primarily public telecommunication infrastructure, such as the Internet, to provide remote offices or traveling users access to a central organizational network....
gateways.
Proprietary
Proprietary software
Proprietary software is computer software licensed under exclusive legal right of the copyright holder. The licensee is given the right to use the software under certain conditions, while restricted from other uses, such as modification, further distribution, or reverse engineering.Complementary...
systems from several manufacturers are based on OpenBSD, including devices from Armorlogic (Profense web application firewall), Calyptix Security, GeNUA mbH, RTMX Inc, and .vantronix GmbH. Code from many of the OpenBSD system tools has been used in recent versions of Microsoft
Microsoft
Microsoft Corporation is an American public multinational corporation headquartered in Redmond, Washington, USA that develops, manufactures, licenses, and supports a wide range of products and services predominantly related to computing through its various product divisions...
's Services for UNIX
Microsoft Windows Services for UNIX
Windows Services for UNIX or Subsystem for UNIX-based Applications is a software package produced by Microsoft which provides a Unix subsystem and other parts of a full Unix environment on Windows NT and some of its immediate successor operating-systems...
, an extension to the Windows
Microsoft Windows
Microsoft Windows is a series of operating systems produced by Microsoft.Microsoft introduced an operating environment named Windows on November 20, 1985 as an add-on to MS-DOS in response to the growing interest in graphical user interfaces . Microsoft Windows came to dominate the world's personal...
operating system which provides some Unix-like functionality, originally based on 4.4BSD-Lite
Berkeley Software Distribution
Berkeley Software Distribution is a Unix operating system derivative developed and distributed by the Computer Systems Research Group of the University of California, Berkeley, from 1977 to 1995...
. Core Force, a security product for Windows, is based on OpenBSD's pf firewall.
OpenBSD ships with the X window system
X Window System
The X window system is a computer software system and network protocol that provides a basis for graphical user interfaces and rich input device capability for networked computers...
and is suitable for use on the desktop. Packages for popular desktop tools are available, including desktop environments GNOME
GNOME
GNOME is a desktop environment and graphical user interface that runs on top of a computer operating system. It is composed entirely of free and open source software...
, KDE
KDE
KDE is an international free software community producing an integrated set of cross-platform applications designed to run on Linux, FreeBSD, Microsoft Windows, Solaris and Mac OS X systems...
, and Xfce
Xfce
Xfce is a free software desktop environment for Unix and other Unix-like platforms, such as Linux, Solaris, and BSD – though recent compatibility issues have arisen with regard to BSD Unix platforms...
; web browsers Konqueror
Konqueror
Not to be confused with the Conqueror web browser.Konqueror is a web browser and file manager that provides file-viewer functionality for file systems such as local files, files on a remote ftp server and files in a disk image. It is a core part of the KDE desktop environment...
, Mozilla Firefox
Mozilla Firefox
Mozilla Firefox is a free and open source web browser descended from the Mozilla Application Suite and managed by Mozilla Corporation. , Firefox is the second most widely used browser, with approximately 25% of worldwide usage share of web browsers...
and Chromium
Chromium (web browser)
Chromium is the open source web browser project from which Google Chrome draws its source code. The project's hourly Chromium snapshots appear essentially similar to the latest builds of Google Chrome aside from the omission of certain Google additions, most noticeable among them: Google's...
; and multimedia
Multimedia
Multimedia is media and content that uses a combination of different content forms. The term can be used as a noun or as an adjective describing a medium as having multiple content forms. The term is used in contrast to media which use only rudimentary computer display such as text-only, or...
programs MPlayer
MPlayer
MPlayer is a free and open source media player. The program is available for all major operating systems, including Linux and other Unix-like systems, Microsoft Windows and Mac OS X. Versions for OS/2, Syllable, AmigaOS and MorphOS are also available. The Windows version works, with some minor...
, VLC media player
VLC media player
VLC media player is a free and open source media player and multimedia framework written by the VideoLAN project.VLC is a portable multimedia player, encoder, and streamer supporting many audio and video codecs and file formats as well as DVDs, VCDs, and various streaming protocols. It is able to...
and xine
Xine
xine is a multimedia playback engine for Unix-like operating systems released under the GNU General Public License. xine is built around a shared library that supports different frontend player applications. Another important feature of xine is the ability to manually correct the synchronization...
.
OpenBSD's performance and usability is occasionally criticised. Felix von Leitner
Felix von Leitner
Felix von Leitner, nicknamed Fefe is a German IT security expert. He is the main author of the dietlibc, a C standard library. His personal blog posts have received huge media coverage in Germany.- Biography :...
's performance and scalability
Scalability
In electronics scalability is the ability of a system, network, or process, to handle growing amount of work in a graceful manner or its ability to be enlarged to accommodate that growth...
tests indicated that OpenBSD lagged behind other operating systems. In response, OpenBSD users and developers criticised von Leitner's objectivity and methodology, and asserted that although performance is given consideration, security and correct design are prioritised, with project member Nick Holland commenting: "It all boils down to what you consider important." OpenBSD is also a relatively small project, particularly when compared with FreeBSD and Linux, and developer time is sometimes seen as better spent on security enhancements than performance optimization. Critics of usability say that OpenBSD has a lack of user-friendly configuration tools, a bare default installation, and a "spartan" and "intimidating" installer. These see much the same rebuttals as performance: a preference for simplicity, reliability and security. As one reviewer puts it, "running an ultra-secure operating system can be a bit of work."
Distribution and marketing
OpenBSD is available freely in various ways: the source can be retrieved by anonymous CVS or CVSupCVSup
CVSup is a computer program written for Unix/Linux based systems that synchronizes files and directories from one location to another while minimizing data transfer using file-type specific delta encoding when appropriate...
, and binary releases and development snapshots can be downloaded either by FTP
File Transfer Protocol
File Transfer Protocol is a standard network protocol used to transfer files from one host to another host over a TCP-based network, such as the Internet. FTP is built on a client-server architecture and utilizes separate control and data connections between the client and server...
or HTTP
Hypertext Transfer Protocol
The Hypertext Transfer Protocol is a networking protocol for distributed, collaborative, hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web....
. Prepackaged CD-ROM
CD-ROM
A CD-ROM is a pre-pressed compact disc that contains data accessible to, but not writable by, a computer for data storage and music playback. The 1985 “Yellow Book” standard developed by Sony and Philips adapted the format to hold any form of binary data....
sets can be ordered online for a small fee, complete with an assortment of stickers and a copy of the release's theme song. These, with its artwork and other bonuses, are one of the project's few sources of income, funding hardware, bandwidth
Bandwidth (computing)
In computer networking and computer science, bandwidth, network bandwidth, data bandwidth, or digital bandwidth is a measure of available or consumed data communication resources expressed in bits/second or multiples of it .Note that in textbooks on wireless communications, modem data transmission,...
and other expenses.
In common with other operating systems, OpenBSD provides a package management system
Package management system
In software, a package management system, also called package manager, is a collection of software tools to automate the process of installing, upgrading, configuring, and removing software packages for a computer's operating system in a consistent manner...
for easy installation and management of programs which are not part of the base operating system. Packages are binary files which are extracted, managed and removed using the package tools. On OpenBSD, the source of packages is the ports system, a collection of Makefiles and other infrastructure required to create packages. In OpenBSD, the ports and base operating system are developed and released together for each version: this means that the ports or packages released with, for example, 4.6 are not suitable for use with 4.5 and vice versa.
OpenBSD at first used the BSD daemon
BSD Daemon
The BSD daemon, nicknamed Beastie, is the generic mascot of BSD operating systems.-Overview:The BSD daemon is named after a software daemon, a computer program found on Unix-like operating systems, which through a play on words takes the cartoon shape of a mythical demon. The BSD daemon's nickname...
mascot created by Phil Foglio
Phil Foglio
Philip "Phil" Foglio is an American cartoonist and comic book artist best known for his humorous science fiction and fantasy work.-Early life and career:...
, updated by John Lasseter
John Lasseter
John Alan Lasseter is an American animator, director and the chief creative officer at Pixar and Walt Disney Animation Studios. He is also currently the Principal Creative Advisor for Walt Disney Imagineering....
and copyright Marshall Kirk McKusick
Marshall Kirk McKusick
Marshall Kirk McKusick is a computer scientist, known for his extensive work on BSD, from the 1980s to FreeBSD in the present day. He was president of the USENIX Association from 1990 to 1992 and again from 2002 to 2004, and still serves on the board. He is also on the editorial board of...
. Subsequent releases saw variations, eventually settling on Puffy, described as a pufferfish
Pufferfish
Tetraodontidae is a family of primarily marine and estuarine fish of the Tetraodontiformes order. The family includes many familiar species which are variously called pufferfish, balloonfish, blowfish, bubblefish, globefish, swellfish, toadfish, toadies, honey toads, sugar toads, and sea squab...
. Since then Puffy has appeared on OpenBSD promotional material and featured in release songs and artwork. The promotional material of early OpenBSD releases did not have a cohesive theme or design but later the CD-ROMs, release songs, posters and tee-shirts for each release have been produced with a single style and theme, sometimes contributed to by Ty Semaka of the Plaid Tongued Devils
Plaid Tongued Devils
The Plaid Tongued Devils are a Canadian musical group. It started as an alternative country duet with singer Ty Semaka and guitarist Alan Kolodziejzyk in 1990 and has been a 5 piece since 1992. Since 1998, their music has combined Roma, Klezmer, Ska, Rock and Jazz music, dubbed romaklezkarock by...
. These have become a part of OpenBSD advocacy
Operating system advocacy
Operating system advocacy is the practice of attempting to increase the awareness and improve the perception of a computer operating system. The motivation behind this may be to increase the number of users of a system, to assert the superiority of one choice over another or out of brand loyalty,...
, with each release expanding a moral or political point important to the project, often through parody
Parody
A parody , in current usage, is an imitative work created to mock, comment on, or trivialise an original work, its subject, author, style, or some other target, by means of humorous, satiric or ironic imitation...
. Past themes have included: in OpenBSD 3.8, the Hackers of the Lost RAID, a parody of Indiana Jones
Indiana Jones
Colonel Henry Walton "Indiana" Jones, Jr., Ph.D. is a fictional character and the protagonist of the Indiana Jones franchise. George Lucas and Steven Spielberg created the character in homage to the action heroes of 1930s film serials...
linked to the new RAID tools featured as part of the release; The Wizard of OS, making its debut in OpenBSD 3.7, based on the work of Pink Floyd
Pink Floyd
Pink Floyd were an English rock band that achieved worldwide success with their progressive and psychedelic rock music. Their work is marked by the use of philosophical lyrics, sonic experimentation, innovative album art, and elaborate live shows. Pink Floyd are one of the most commercially...
and a parody of The Wizard of Oz
The Wizard of Oz (1939 film)
The Wizard of Oz is a 1939 American musical fantasy film produced by Metro-Goldwyn-Mayer. It was directed primarily by Victor Fleming. Noel Langley, Florence Ryerson and Edgar Allan Woolf received credit for the screenplay, but there were uncredited contributions by others. The lyrics for the songs...
related to the project's recent wireless
Wireless
Wireless telecommunications is the transfer of information between two or more points that are not physically connected. Distances can be short, such as a few meters for television remote control, or as far as thousands or even millions of kilometers for deep-space radio communications...
work; and OpenBSD 3.3's Puff the Barbarian, including an 80s rock-style song and parody of Conan the Barbarian
Conan the Barbarian
Conan the Barbarian is a fictional sword and sorcery hero that originated in pulp fiction magazines and has since been adapted to books, comics, several films , television programs, video games, roleplaying games and other media...
, alluding to open documentation.
See also
- BSD AuthenticationBSD AuthenticationBSD Authentication, otherwise known as BSD Auth, is an authentication framework and software API employed by some Unix-like operating systems, specifically OpenBSD and BSD/OS, and accompanying system and application software such as OpenSSH and Apache...
- BSD and GPL licensing
- Comparison of BSD operating systemsComparison of BSD operating systemsThere are a number of Unix-like operating systems based on or descended from the Berkeley Software Distribution series of Unix variants. The three most notable descendants in current use are FreeBSD, OpenBSD, and NetBSD, which are all derived from 386BSD and 4.4BSD-Lite, by various routes...
- Comparison of operating systemsComparison of operating systemsThese tables compare general and technical information for a number of widely used and currently available operating systems.Because of the large number and variety of available Linux distributions, they are all grouped under a single entry; see comparison of Linux distributions for a detailed...
- Comparison of operating system kernels
- Comparison of open source operating systemsComparison of open source operating systemsThese tables compare the various free software / open source operating systems. Where not all of the non-EOL versions support a feature, the first version which support it is listed.- General information :- Supported architectures :- General :...
- HackathonHackathonA hackathon, a hacker neologism, is an event when programmers meet to do collaborative computer programming. The spirit of a hackathon is to collaboratively build programs and applications. Hackathons are typically between several days and a week in length...
- KAME projectKAME projectThe KAME project was a joint effort of six organizations in Japan which aimed to provide a free IPv6 and IPsec protocol stack implementation for variants of the BSD Unix computer operating-system...
- pfSensePfSensepfSense is an open source firewall/router distribution based on FreeBSD. pfSense is meant to be installed on a personal computer and is noted for its reliability and offering features often only found in expensive commercial firewalls. It can be configured and upgraded through a web-based...
- POSSE projectPOSSE projectThe Portable Open Source Security Elements, or POSSE project, was a co-operative venture between the University of Pennsylvania Distributed Systems Laboratory, the OpenBSD project and others. It received funding through a grant from the United States Defense Advanced Research Projects Agency, or...
- Security-focused operating system
External links
- OpenBSD journal
- Unofficial OpenBSD ports tracker
- [irc://irc.freenode.net/openbsd #openbsd] on freenode

