
Security protocol notation
Encyclopedia
In cryptography
, security (engineering) protocol notation is a way of expressing a protocol
of correspondence between entities of a dynamic system, such as a computer network
. In the context of a formal model, it allows reasoning about the properties of such a system.
The standard notation consists of a set of individuals (traditionally named Alice, Bob
, Charlie, and so on) who wish to communicate. They may have access to a server S, shared keys K, timestamps T, and can generate nonces
N for authentication purposes.
A simple example might be the following:
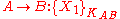
This states that Alice intends a message for Bob consisting of a plaintext
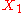 encrypted under shared key KAB.
encrypted under shared key KAB.
Another example might be the following:
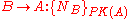
This states that Bob intends a message for Alice consisting of a nonce
encrypted using public key of Alice.
A key with two subscripts is a symmetric key shared by the two corresponding individuals. A key with one subscript is the public key of the corresponding individual. A private key is represented as the inverse of the public key.
The notation specifies only the operation and not its semantics — for instance, private key encryption and signature are represented identically.
We can express more complicated protocols in such a fashion. See Kerberos as an example. Some sources refer to this notation as Kerberos Notation. Some authors consider the notation used by Steiner, Neuman, & Schiller as a notable reference.
Several models exist to reason about security protocols in this way, one of which is BAN logic.
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
, security (engineering) protocol notation is a way of expressing a protocol
Cryptographic protocol
A security protocol is an abstract or concrete protocol that performs a security-related function and applies cryptographic methods.A protocol describes how the algorithms should be used...
of correspondence between entities of a dynamic system, such as a computer network
Computer network
A computer network, often simply referred to as a network, is a collection of hardware components and computers interconnected by communication channels that allow sharing of resources and information....
. In the context of a formal model, it allows reasoning about the properties of such a system.
The standard notation consists of a set of individuals (traditionally named Alice, Bob
Alice and Bob
The names Alice and Bob are commonly used placeholder names for archetypal characters in fields such as cryptography and physics. The names are used for convenience; for example, "Alice sends a message to Bob encrypted with his public key" is easier to follow than "Party A sends a message to Party...
, Charlie, and so on) who wish to communicate. They may have access to a server S, shared keys K, timestamps T, and can generate nonces
Cryptographic nonce
In security engineering, nonce is an arbitrary number used only once to sign a cryptographic communication. It is similar in spirit to a nonce word, hence the name. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused...
N for authentication purposes.
A simple example might be the following:
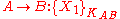
This states that Alice intends a message for Bob consisting of a plaintext
Plaintext
In cryptography, plaintext is information a sender wishes to transmit to a receiver. Cleartext is often used as a synonym. Before the computer era, plaintext most commonly meant message text in the language of the communicating parties....
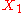 encrypted under shared key KAB.
encrypted under shared key KAB.Another example might be the following:
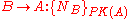
This states that Bob intends a message for Alice consisting of a nonce
Cryptographic nonce
In security engineering, nonce is an arbitrary number used only once to sign a cryptographic communication. It is similar in spirit to a nonce word, hence the name. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused...
encrypted using public key of Alice.
A key with two subscripts is a symmetric key shared by the two corresponding individuals. A key with one subscript is the public key of the corresponding individual. A private key is represented as the inverse of the public key.
The notation specifies only the operation and not its semantics — for instance, private key encryption and signature are represented identically.
We can express more complicated protocols in such a fashion. See Kerberos as an example. Some sources refer to this notation as Kerberos Notation. Some authors consider the notation used by Steiner, Neuman, & Schiller as a notable reference.
Several models exist to reason about security protocols in this way, one of which is BAN logic.

