
Alice and Bob
Encyclopedia
The names Alice and Bob are commonly used placeholder name
s for archetypal characters in fields such as cryptography
and physics
. The names are used for convenience; for example, "Alice sends a message to Bob encrypted with his public key" is easier to follow than "Party A sends a message to Party B encrypted by Party B's public key." Following the alphabet, the specific names have evolved into common parlance within these fields—helping technical topics to be explained in a more understandable fashion.
In cryptography
and computer security
, there are a number of widely used names for the participants in discussions and presentations about various protocols. The names are conventional, somewhat self-suggestive, sometimes humorous, and effectively act as metasyntactic variable
s.
In typical implementations of these protocols, it is understood that the actions attributed to characters such as Alice or Bob need not always be carried out by human parties directly, but also by a trusted automated agent (such as a computer program) on their behalf. Despite the advantage of Alice and Bob's distinct genders in reducing ambiguity, there has been little tendency to introduce inanimate parties so they could be referred by neuter pronouns.
 This list is drawn mostly from the book Applied Cryptography by Bruce Schneier
This list is drawn mostly from the book Applied Cryptography by Bruce Schneier
. Alice and Bob are archetypes in cryptography; Eve is also common. Names further down the alphabet are less common.
Although an interactive proof system
is not quite a cryptographic protocol, it is sufficiently related to mention the cast of characters its literature features:
A similar pair of characters is Paul and Carole. The characters were introduced in the solution of the Twenty Questions
problem, where "Paul", who asked questions, stood for Paul Erdős
and "Carole", who answered them, was an anagram
of "oracle". They were further used in certain combinatorial games
in the roles of Pusher and Chooser respectively, and have since been used in various roles.
Placeholder name
Placeholder names are words that can refer to objects or people whose names are either temporarily forgotten, irrelevant, or unknown in the context in which they are being discussed...
s for archetypal characters in fields such as cryptography
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
and physics
Physics
Physics is a natural science that involves the study of matter and its motion through spacetime, along with related concepts such as energy and force. More broadly, it is the general analysis of nature, conducted in order to understand how the universe behaves.Physics is one of the oldest academic...
. The names are used for convenience; for example, "Alice sends a message to Bob encrypted with his public key" is easier to follow than "Party A sends a message to Party B encrypted by Party B's public key." Following the alphabet, the specific names have evolved into common parlance within these fields—helping technical topics to be explained in a more understandable fashion.
In cryptography
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
and computer security
Computer security
Computer security is a branch of computer technology known as information security as applied to computers and networks. The objective of computer security includes protection of information and property from theft, corruption, or natural disaster, while allowing the information and property to...
, there are a number of widely used names for the participants in discussions and presentations about various protocols. The names are conventional, somewhat self-suggestive, sometimes humorous, and effectively act as metasyntactic variable
Metasyntactic variable
In computer science, programmers use metasyntactic variables to describe a placeholder name or an alias term commonly used to denote the subject matter under discussion or an arbitrary member of a class of things under discussion...
s.
In typical implementations of these protocols, it is understood that the actions attributed to characters such as Alice or Bob need not always be carried out by human parties directly, but also by a trusted automated agent (such as a computer program) on their behalf. Despite the advantage of Alice and Bob's distinct genders in reducing ambiguity, there has been little tendency to introduce inanimate parties so they could be referred by neuter pronouns.
List of characters

Bruce Schneier
Bruce Schneier is an American cryptographer, computer security specialist, and writer. He is the author of several books on general security topics, computer security and cryptography, and is the founder and chief technology officer of BT Managed Security Solutions, formerly Counterpane Internet...
. Alice and Bob are archetypes in cryptography; Eve is also common. Names further down the alphabet are less common.
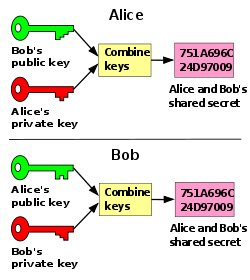
- Alice and Bob. Generally, Alice wants to send a message to Bob. These names were used by Ron RivestRon RivestRonald Linn Rivest is a cryptographer. He is the Andrew and Erna Viterbi Professor of Computer Science at MIT's Department of Electrical Engineering and Computer Science and a member of MIT's Computer Science and Artificial Intelligence Laboratory...
in the 1978 Communications of the ACMAssociation for Computing MachineryThe Association for Computing Machinery is a learned society for computing. It was founded in 1947 as the world's first scientific and educational computing society. Its membership is more than 92,000 as of 2009...
article presenting the RSA cryptosystem, and in A Method for Obtaining Digital Signatures and Public-Key Cryptosystems published April 4, 1977, revised September 1, 1977 as technical Memo LCS/TM82. Rivest denies that these names have any relation to the 1969 movie Bob & Carol & Ted & AliceBob & Carol & Ted & AliceBob & Carol & Ted & Alice is a 1969 comedy-drama film directed by Paul Mazursky. It stars Natalie Wood, Robert Culp, Elliott Gould and Dyan Cannon....
as occasionally suggested by others. - Carol, Carlos or Charlie, as a third participant in communications.
- Chuck, as a third participant usually of malicious intent.
- Dave, a fourth participant, and so on alphabetically.Eve, an eavesdropper, is usually a passive attacker. While she can listen in on messages between Alice and Bob, she cannot modify them. In quantum cryptographyQuantum cryptographyQuantum key distribution uses quantum mechanics to guarantee secure communication. It enables two parties to produce a shared random secret key known only to them, which can then be used to encrypt and decrypt messages...
, Eve may also represent the environment.Mallory, a malicious attacker (less commonly called Trudy, an intruder.); unlike Eve, Mallory can modify messages, substitute her own messages, replay old messages, and so on. The difficulty of securing a system against Mallory is much greater than against Eve. - Peggy, a prover, and Victor, a verifier, often must interact in some way to show that the intended transaction has actually taken place. They are often found in zero-knowledge proofZero-knowledge proofIn cryptography, a zero-knowledge proof or zero-knowledge protocol is an interactive method for one party to prove to another that a statement is true, without revealing anything other than the veracity of the statement....
s. - Trent, a trusted arbitrator, is some kind of neutral third partyTrusted third partyIn cryptography, a trusted third party is an entity which facilitates interactions between two parties who both trust the third party; The Third Party reviews all critical transaction communications between the parties, based on the ease of creating fraudulent digital content. In TTP models, the...
, whose exact role varies with the protocol under discussion. - Walter, a warden, may be needed to guard Alice and Bob in some respect, depending on the protocol being discussed.
Although an interactive proof system
Interactive proof system
In computational complexity theory, an interactive proof system is an abstract machine that models computation as the exchange of messages between two parties. The parties, the verifier and the prover, interact by exchanging messages in order to ascertain whether a given string belongs to a...
is not quite a cryptographic protocol, it is sufficiently related to mention the cast of characters its literature features:
- Arthur and Merlin: In interactive proof systems, the prover has unbounded computational ability and is hence associated with Merlin, the powerful wizard. He claims the truth of a statement, and ArthurKing ArthurKing Arthur is a legendary British leader of the late 5th and early 6th centuries, who, according to Medieval histories and romances, led the defence of Britain against Saxon invaders in the early 6th century. The details of Arthur's story are mainly composed of folklore and literary invention, and...
, the wise king, questions him to verify the claim. These two characters also give the name for two complexity classComplexity classIn computational complexity theory, a complexity class is a set of problems of related resource-based complexity. A typical complexity class has a definition of the form:...
es, namely MA and AM.
A similar pair of characters is Paul and Carole. The characters were introduced in the solution of the Twenty Questions
Twenty Questions
Twenty Questions is a spoken parlor game which encourages deductive reasoning and creativity. It originated in the United States and escalated in popularity during the late 1940s when it became the format for a successful weekly radio quiz program....
problem, where "Paul", who asked questions, stood for Paul Erdős
Paul Erdos
Paul Erdős was a Hungarian mathematician. Erdős published more papers than any other mathematician in history, working with hundreds of collaborators. He worked on problems in combinatorics, graph theory, number theory, classical analysis, approximation theory, set theory, and probability theory...
and "Carole", who answered them, was an anagram
Anagram
An anagram is a type of word play, the result of rearranging the letters of a word or phrase to produce a new word or phrase, using all the original letters exactly once; e.g., orchestra = carthorse, A decimal point = I'm a dot in place, Tom Marvolo Riddle = I am Lord Voldemort. Someone who...
of "oracle". They were further used in certain combinatorial games
Combinatorial game theory
Combinatorial game theory is a branch of applied mathematics and theoretical computer science that studies sequential games with perfect information, that is, two-player games which have a position in which the players take turns changing in defined ways or moves to achieve a defined winning...
in the roles of Pusher and Chooser respectively, and have since been used in various roles.
See also
- Dave and Sue
- John DoeJohn DoeThe name "John Doe" is used as a placeholder name in a legal action, case or discussion for a male party, whose true identity is unknown or must be withheld for legal reasons. The name is also used to refer to a male corpse or hospital patient whose identity is unknown...
- George SpelvinGeorge SpelvinGeorge Spelvin, Georgette Spelvin, and Georgina Spelvin are the traditional pseudonyms used in programs in American theater. The reasons for the use of an alternate name vary. Actors who do not want to be credited, or whose names would otherwise appear twice because they are playing more than one...
- Metasyntactic variableMetasyntactic variableIn computer science, programmers use metasyntactic variables to describe a placeholder name or an alias term commonly used to denote the subject matter under discussion or an arbitrary member of a class of things under discussion...
- Ruritania, a fictional country sometimes used like personal names Alice and Bob as a generic country
- Tommy AtkinsTommy AtkinsTommy Atkins is a term for a common soldier in the British Army that was already well established in the 19th century, but is particularly associated with World War I. It can be used as a term of reference, or as a form of address. German soldiers would call out to "Tommy" across no man's land if...
External links
- A Method for Obtaining Digital Signatures and Public-Key Cryptosystems
- Geek Song: "Alice and Bob"
- Alice and Bob jokes (mainly Quantum Computing-related)
- Alice and Bob: IT's inseparable couple
- A short history of Bobs (story and slideshow) in the computing industry, from Alice & Bob to Microsoft Bob and Father of Ethernet Bob Metcalfe
- Alice and Bob Recopilatory

