
IEEE 802.11i-2004
Encyclopedia
IEEE 802.11i-2004 or 802.11i, implemented as WPA2, is an amendment to the original IEEE 802.11
. The draft standard was ratified on 24 June 2004. This standard specifies security mechanisms for wireless network
s. It replaced the short Authentication and privacy clause of the original standard with a detailed Security clause. In the process it deprecated
the broken WEP
. The amendment was later incorporated into the published IEEE 802.11-2007 standard.
(WEP), which was shown to have severe security weaknesses. Wi-Fi Protected Access
(WPA) had previously been introduced by the Wi-Fi Alliance
as an intermediate solution to WEP insecurities. WPA implemented a subset of a draft of 802.11i. The Wi-Fi Alliance refers to their approved, interoperable implementation of the full 802.11i as WPA2, also called RSN (Robust Security Network). 802.11i makes use of the Advanced Encryption Standard
(AES) block cipher
, whereas WEP and WPA use the RC4 stream cipher
.
to establish and change the appropriate cryptographic keys. The RSN is a security network that only allows the creation of robust security network associations (RSNAs), which are a type of association used by a pair of stations (STAs) if the procedure to establish authentication or association between them includes the 4-Way Handshake. It also provides two RSNA data confidentiality and integrity protocols, TKIP and CCMP
, with implementation of CCMP being mandatory.
(AP) still needs to authenticate itself to the client station (STA), and key
s to encrypt the traffic need to be derived. The earlier EAP
exchange has provided the shared secret key PMK (Pairwise Master Key). This key is, however, designed to last the entire session and should be exposed as little as possible. Therefore the four-way handshake is used to establish another key called the PTK (Pairwise Transient Key). The PTK is generated by concatenating the following attributes: PMK, AP nonce
(ANonce), STA nonce (SNonce), AP MAC address
, and STA MAC address. The product is then put through a cryptographic hash function
.
The handshake also yields the GTK (Group Temporal Key), used to decrypt multicast and broadcast traffic. The actual messages exchanged during the handshake are depicted in the figure and explained below:
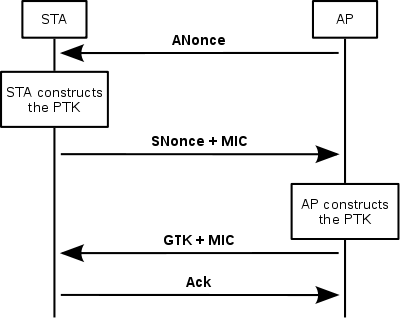
All the above messages are sent as EAPOL-Key frames.
As soon as the PTK is obtained it is divided into five separate keys:
PTK (Pairwise Transient Key – 64 bytes)
The Michael MIC Authenticator Tx/Rx Keys provided in the handshake are only used if the network is using TKIP to encrypt the data.
To handle the updating, 802.11i defines a Group Key Handshake that consists of a two-way handshake:
GTK ( Groupwise Transient Key – 32 bytes)
The Michael MIC Authenticator Tx/Rx Keys provided in the handshake are only used if the network is using TKIP to encrypt the data.
IEEE 802.11
IEEE 802.11 is a set of standards for implementing wireless local area network computer communication in the 2.4, 3.6 and 5 GHz frequency bands. They are created and maintained by the IEEE LAN/MAN Standards Committee . The base version of the standard IEEE 802.11-2007 has had subsequent...
. The draft standard was ratified on 24 June 2004. This standard specifies security mechanisms for wireless network
Wireless LAN
A wireless local area network links two or more devices using some wireless distribution method , and usually providing a connection through an access point to the wider internet. This gives users the mobility to move around within a local coverage area and still be connected to the network...
s. It replaced the short Authentication and privacy clause of the original standard with a detailed Security clause. In the process it deprecated
Deprecation
In the process of authoring computer software, its standards or documentation, deprecation is a status applied to software features to indicate that they should be avoided, typically because they have been superseded...
the broken WEP
Wired Equivalent Privacy
Wired Equivalent Privacy is a weak security algorithm for IEEE 802.11 wireless networks. Introduced as part of the original 802.11 standard ratified in September 1999, its intention was to provide data confidentiality comparable to that of a traditional wired network...
. The amendment was later incorporated into the published IEEE 802.11-2007 standard.
Replacement of WEP
802.11i supersedes the previous security specification, Wired Equivalent PrivacyWired Equivalent Privacy
Wired Equivalent Privacy is a weak security algorithm for IEEE 802.11 wireless networks. Introduced as part of the original 802.11 standard ratified in September 1999, its intention was to provide data confidentiality comparable to that of a traditional wired network...
(WEP), which was shown to have severe security weaknesses. Wi-Fi Protected Access
Wi-Fi Protected Access
Wi-Fi Protected Access and Wi-Fi Protected Access II are two security protocols and security certification programs developed by the Wi-Fi Alliance to secure wireless computer networks...
(WPA) had previously been introduced by the Wi-Fi Alliance
Wi-Fi Alliance
The Wi-Fi Alliance is a trade association that promotes Wireless LAN technology and certifies products if they conform to certain standards of interoperability. Not every IEEE 802.11-compliant device is submitted for certification to the Wi-Fi Alliance, sometimes because of costs associated with...
as an intermediate solution to WEP insecurities. WPA implemented a subset of a draft of 802.11i. The Wi-Fi Alliance refers to their approved, interoperable implementation of the full 802.11i as WPA2, also called RSN (Robust Security Network). 802.11i makes use of the Advanced Encryption Standard
Advanced Encryption Standard
Advanced Encryption Standard is a specification for the encryption of electronic data. It has been adopted by the U.S. government and is now used worldwide. It supersedes DES...
(AES) block cipher
Block cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
, whereas WEP and WPA use the RC4 stream cipher
Stream cipher
In cryptography, a stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream . In a stream cipher the plaintext digits are encrypted one at a time, and the transformation of successive digits varies during the encryption...
.
Protocol operation
IEEE 802.11i enhances IEEE 802.11-1999 by providing a Robust Security Network (RSN) with two new protocols, the 4-Way Handshake and the Group Key Handshake. These utilize the authentication services and port access control described in IEEE 802.1XIEEE 802.1X
IEEE 802.1X is an IEEE Standard for port-based Network Access Control . It is part of the IEEE 802.1 group of networking protocols. It provides an authentication mechanism to devices wishing to attach to a LAN or WLAN....
to establish and change the appropriate cryptographic keys. The RSN is a security network that only allows the creation of robust security network associations (RSNAs), which are a type of association used by a pair of stations (STAs) if the procedure to establish authentication or association between them includes the 4-Way Handshake. It also provides two RSNA data confidentiality and integrity protocols, TKIP and CCMP
CCMP
Counter Mode with Cipher Block Chaining Message Authentication Code Protocol or CCMP is an encryption protocol designed for Wireless LAN products that implement the standards of the IEEE 802.11i amendment to the original IEEE 802.11 standard...
, with implementation of CCMP being mandatory.
The Four-Way Handshake
The authentication process leaves two considerations: the access pointWireless access point
In computer networking, a wireless access point is a device that allows wireless devices to connect to a wired network using Wi-Fi, Bluetooth or related standards...
(AP) still needs to authenticate itself to the client station (STA), and key
Key (cryptography)
In cryptography, a key is a piece of information that determines the functional output of a cryptographic algorithm or cipher. Without a key, the algorithm would produce no useful result. In encryption, a key specifies the particular transformation of plaintext into ciphertext, or vice versa...
s to encrypt the traffic need to be derived. The earlier EAP
Extensible Authentication Protocol
Extensible Authentication Protocol, or EAP, is an authentication framework frequently used in wireless networks and Point-to-Point connections. It is defined in RFC 3748, which made RFC 2284 obsolete, and was updated by RFC 5247....
exchange has provided the shared secret key PMK (Pairwise Master Key). This key is, however, designed to last the entire session and should be exposed as little as possible. Therefore the four-way handshake is used to establish another key called the PTK (Pairwise Transient Key). The PTK is generated by concatenating the following attributes: PMK, AP nonce
Cryptographic nonce
In security engineering, nonce is an arbitrary number used only once to sign a cryptographic communication. It is similar in spirit to a nonce word, hence the name. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused...
(ANonce), STA nonce (SNonce), AP MAC address
MAC address
A Media Access Control address is a unique identifier assigned to network interfaces for communications on the physical network segment. MAC addresses are used for numerous network technologies and most IEEE 802 network technologies, including Ethernet...
, and STA MAC address. The product is then put through a cryptographic hash function
Cryptographic hash function
A cryptographic hash function is a deterministic procedure that takes an arbitrary block of data and returns a fixed-size bit string, the hash value, such that an accidental or intentional change to the data will change the hash value...
.
The handshake also yields the GTK (Group Temporal Key), used to decrypt multicast and broadcast traffic. The actual messages exchanged during the handshake are depicted in the figure and explained below:

- The APWireless access pointIn computer networking, a wireless access point is a device that allows wireless devices to connect to a wired network using Wi-Fi, Bluetooth or related standards...
sends a nonce-value to the STA (ANonce). The client now has all the attributes to construct the PTK. - The STA sends its own nonce-value (SNonce) to the AP together with a MIC, including authentication, which is really a Message Authentication and Integrity Code: (MAIC).
- The AP sends the GTK and a sequence number together with another MIC. This sequence number will be used in the next multicast or broadcast frame, so that the receiving STA can perform basic replay detection.
- The STA sends a confirmation to the AP.
All the above messages are sent as EAPOL-Key frames.
As soon as the PTK is obtained it is divided into five separate keys:
PTK (Pairwise Transient Key – 64 bytes)
- 16 bytes of EAPOL-Key Confirmation Key (KCK)– Used to compute MIC on WPA EAPOL Key message
- 16 bytes of EAPOL-Key Encryption Key (KEK) - AP uses this key to encrypt additional data sent (in the 'Key Data' field) to the client (for example, the RSN IE or the GTK)
- 16 bytes of Temporal Key (TK) – Used to encrypt/decrypt Unicast data packets
- 8 bytes of Michael MIC Authenticator Tx Key – Used to compute MIC on unicast data packets transmitted by the AP
- 8 bytes of Michael MIC Authenticator Rx Key – Used to compute MIC on unicast data packets transmitted by the station
The Michael MIC Authenticator Tx/Rx Keys provided in the handshake are only used if the network is using TKIP to encrypt the data.
The Group Key Handshake
The GTK used in the network may need to be updated due to the expiry of a preset timer. When a device leaves the network, the GTK also needs to be updated. This is to prevent the device from receiving any more multicast or broadcast messages from the AP.To handle the updating, 802.11i defines a Group Key Handshake that consists of a two-way handshake:
- The AP sends the new GTK to each STA in the network. The GTK is encrypted using the KEK assigned to that STA, and protects the data from tampering, by use of a MIC.
- The STA acknowledges the new GTK and replies to the AP.
GTK ( Groupwise Transient Key – 32 bytes)
- 16 bytes of Group Temporal Encryption Key – Used to encrypt Multicast data packets
- 8 bytes of Michael MIC Authenticator Tx Key – Used to compute MIC on Multicast packet transmitted by AP
- 8 bytes of Michael MIC Authenticator Rx Key – This is currently not used as stations do not send multicast traffic
The Michael MIC Authenticator Tx/Rx Keys provided in the handshake are only used if the network is using TKIP to encrypt the data.
See also
- WLAN Authentication and Privacy Infrastructure (WAPI), China's centralized wireless security method
- Wi-Fi Protected SetupWi-Fi Protected SetupWi-Fi Protected Setup is a computing standard for easy and secure establishment of a wireless home network....

