
Wired Equivalent Privacy
Encyclopedia
Wired Equivalent Privacy (WEP) is a weak security algorithm
for IEEE 802.11
wireless networks
. Introduced as part of the original 802.11 standard ratified in September 1999, its intention was to provide data confidentiality
comparable to that of a traditional wired network
. WEP, recognizable by the key of 10 or 26 hexadecimal
digits, is widely in use and is often the first security choice presented to users by router configuration tools.
Although its name implies that it is as secure as a wired connection, WEP has been demonstrated to have numerous flaws and has been deprecated in favor of newer standards such as WPA2. In 2003 the Wi-Fi Alliance
announced that WEP had been superseded by Wi-Fi Protected Access
(WPA). In 2004, with the ratification of the full 802.11i standard (i.e. WPA2), the IEEE declared that both WEP-40 and WEP-104 "have been deprecated as they fail to meet their security goals".
standard ratified in September 1999. WEP uses the stream cipher
RC4
for confidentiality
, and the CRC-32 checksum for integrity
. It was deprecated in 2004 and is documented in the current standard.
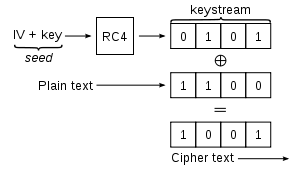 Standard 64-bit WEP uses a 40 bit key (also known as WEP-40), which is concatenated with a 24-bit initialization vector
Standard 64-bit WEP uses a 40 bit key (also known as WEP-40), which is concatenated with a 24-bit initialization vector
(IV) to form the RC4 key. At the time that the original WEP standard was drafted, the U.S. Government's export restrictions on cryptographic technology
limited the key size. Once the restrictions were lifted, manufacturers of access points implemented an extended 128-bit WEP protocol using a 104-bit key size (WEP-104).
A 64-bit WEP key is usually entered as a string of 10 hexadecimal
(base 16) characters (0-9 and A-F). Each character represents four bits, 10 digits of four bits each gives 40 bits; adding the 24-bit IV produces the complete 64-bit WEP key. Most devices also allow the user to enter the key as five ASCII characters, each of which is turned into eight bits using the character's byte value in ASCII; however, this restricts each byte to be a printable ASCII character, which is only a small fraction of possible byte values, greatly reducing the space of possible keys.
A 128-bit WEP key is usually entered as a string of 26 hexadecimal characters. 26 digits of four bits each gives 104 bits; adding the 24-bit IV produces the complete 128-bit WEP key. Most devices also allow the user to enter it as 13 ASCII characters.
A 256-bit WEP system is available from some vendors. As with the other WEP-variants 24 bits of that is for the IV, leaving 232 bits for actual protection. These 232 bits are typically entered as 58 hexadecimal characters. ((58 × 4 bits =) 232 bits) + 24 IV bits = 256-bit WEP key.
Key size is one of the security limitations in WEP. Cracking
a longer key requires interception of more packets, but there are active attacks that stimulate the necessary traffic. There are other weaknesses in WEP, including the possibility of IV collisions and altered packets, that are not helped by using a longer key.
For the sake of clarity, we discuss WEP authentication in the Infrastructure mode (that is, between a WLAN client and an Access Point). The discussion applies to the ad-Hoc mode
as well.
In Open System authentication, the WLAN client need not provide its credentials to the Access Point during authentication. Any client can authenticate with the Access Point and then attempt to associate. In effect, no authentication occurs. Subsequently WEP keys can be used for encrypting data frames. At this point, the client must have the correct keys.
In Shared Key authentication, the WEP key is used for authentication in a four step challenge-response handshake:
After the authentication and association, the pre-shared WEP key is also used for encrypting the data frames using RC4
.
At first glance, it might seem as though Shared Key authentication is more secure than Open System authentication, since the latter offers no real authentication. However, it is quite the reverse. It is possible to derive the keystream used for the handshake by capturing the challenge frames in Shared Key authentication. Hence, it is advisable to use Open System authentication for WEP authentication, rather than Shared Key authentication. (Note that both authentication mechanisms are weak.)
, the same traffic key must never be used twice. The purpose of an IV, which is transmitted as plain text, is to prevent any repetition, but a 24-bit IV is not long enough to ensure this on a busy network. The way the IV was used also opened WEP to a related key attack. For a 24-bit IV, there is a 50% probability the same IV will repeat after 5000 packets.
In August 2001, Scott Fluhrer, Itsik Mantin, and Adi Shamir
published a cryptanalysis of WEP that exploits the way the RC4 cipher and IV is used in WEP, resulting in a passive attack that can recover the RC4 key
after eavesdropping on the network. Depending on the amount of network traffic, and thus the number of packets available for inspection, a successful key recovery could take as little as one minute. If an insufficient number of packets are being sent, there are ways for an attacker to send packets on the network and thereby stimulate reply packets which can then be inspected to find the key. The attack was soon implemented, and automated tools have since been released. It is possible to perform the attack with a personal computer, off-the-shelf hardware and freely available software such as aircrack-ng
to crack any WEP key in minutes.
Cam-Winget et al. (2003) surveyed a variety of shortcomings in WEP. They write "Experiments in the field indicate that, with proper equipment, it is practical to eavesdrop on WEP-protected networks from distances of a mile or more from the target." They also reported two generic weaknesses:
In 2005, a group from the U.S. Federal Bureau of Investigation
gave a demonstration where they cracked a WEP-protected network in 3 minutes using publicly available tools. Andreas Klein presented another analysis of the RC4 stream cipher. Klein showed that there are more correlations between the RC4 keystream and the key than the ones found by Fluhrer, Mantin and Shamir which can additionally be used to break WEP in WEP-like usage modes.
In 2006, Bittau, Handley
, and Lackey showed that the 802.11 protocol itself can be used against WEP to enable earlier attacks that were previously thought impractical. After eavesdropping a single packet, an attacker can rapidly bootstrap to be able to transmit arbitrary data. The eavesdropped packet can then be decrypted one byte at a time (by transmitting about 128 packets per byte to decrypt) to discover the local network IP addresses. Finally, if the 802.11 network is connected to the Internet, the attacker can use 802.11 fragmentation to replay eavesdropped packets while crafting a new IP header onto them. The access point can then be used to decrypt these packets and relay them on to a buddy on the Internet, allowing real-time decryption of WEP traffic within a minute of eavesdropping the first packet.
In 2007, Erik Tews, Andrei Pychkine, and Ralf-Philipp Weinmann were able to extend Klein's 2005 attack and optimize it for usage against WEP. With the new attack it is possible to recover a 104-bit WEP key with probability 50% using only 40,000 captured packets. For 60,000 available data packets, the success probability is about 80% and for 85,000 data packets about 95%. Using active techniques like deauth and ARP
re-injection, 40,000 packets can be captured in less than one minute under good conditions. The actual computation takes about 3 seconds and 3 MB of main memory on a Pentium-M 1.7 GHz and can additionally be optimized for devices with slower CPUs. The same attack can be used for 40-bit keys with an even higher success probability.
In 2008, Payment Card Industry
(PCI) Security Standards Council’s latest update of the Data Security Standard
(DSS), prohibits use of the WEP as part of any credit-card processing after 30 June 2010, and prohibits any new system from being installed that uses WEP after 31 March 2009. The use of WEP contributed to the T.J. Maxx parent company network invasion.
, Secure Shell
) can provide secure data transmission over an insecure network. However, replacements for WEP have been developed with the goal of restoring security to the wireless network itself.
was an intermediate solution for hardware that could not support WPA2, but it has been cracked. Either is much more secure than WEP. To add support for WPA or WPA2, some old Wi-Fi access point
s might need to be replaced or have their firmware
upgraded. WPA was designed as an interim software-implementable solution for WEP that could forestall immediate deployment of new hardware. However, TKIP (the basis of WPA) has reached the end of its designed lifetime, has been broken, and has been deprecated in the next full release of the 802.11 standard.
key attacks.
After it became clear that the overall WEP algorithm was deficient (and not just the IV and key sizes) and would require even more fixes, both the WEP2 name and original algorithm were dropped. The two extended key lengths remained in what eventually became WPA's TKIP.
(formerly a subsidiary of Lucent Technologies
) that enhances WEP security by avoiding "weak IVs". It is only completely effective when WEPplus is used at both ends of the wireless connection. As this cannot easily be enforced, it remains a serious limitation. It also does not necessarily prevent replay attack
s.
. Dynamic WEP changes WEP keys dynamically. It is a vendor-specific feature provided by several vendors such as 3Com
.
The dynamic change idea made it into 802.11i as part of TKIP, but not for the actual WEP algorithm.
Algorithm
In mathematics and computer science, an algorithm is an effective method expressed as a finite list of well-defined instructions for calculating a function. Algorithms are used for calculation, data processing, and automated reasoning...
for IEEE 802.11
IEEE 802.11
IEEE 802.11 is a set of standards for implementing wireless local area network computer communication in the 2.4, 3.6 and 5 GHz frequency bands. They are created and maintained by the IEEE LAN/MAN Standards Committee . The base version of the standard IEEE 802.11-2007 has had subsequent...
wireless networks
Computer network
A computer network, often simply referred to as a network, is a collection of hardware components and computers interconnected by communication channels that allow sharing of resources and information....
. Introduced as part of the original 802.11 standard ratified in September 1999, its intention was to provide data confidentiality
Confidentiality
Confidentiality is an ethical principle associated with several professions . In ethics, and in law and alternative forms of legal resolution such as mediation, some types of communication between a person and one of these professionals are "privileged" and may not be discussed or divulged to...
comparable to that of a traditional wired network
Local area network
A local area network is a computer network that interconnects computers in a limited area such as a home, school, computer laboratory, or office building...
. WEP, recognizable by the key of 10 or 26 hexadecimal
Hexadecimal
In mathematics and computer science, hexadecimal is a positional numeral system with a radix, or base, of 16. It uses sixteen distinct symbols, most often the symbols 0–9 to represent values zero to nine, and A, B, C, D, E, F to represent values ten to fifteen...
digits, is widely in use and is often the first security choice presented to users by router configuration tools.
Although its name implies that it is as secure as a wired connection, WEP has been demonstrated to have numerous flaws and has been deprecated in favor of newer standards such as WPA2. In 2003 the Wi-Fi Alliance
Wi-Fi Alliance
The Wi-Fi Alliance is a trade association that promotes Wireless LAN technology and certifies products if they conform to certain standards of interoperability. Not every IEEE 802.11-compliant device is submitted for certification to the Wi-Fi Alliance, sometimes because of costs associated with...
announced that WEP had been superseded by Wi-Fi Protected Access
Wi-Fi Protected Access
Wi-Fi Protected Access and Wi-Fi Protected Access II are two security protocols and security certification programs developed by the Wi-Fi Alliance to secure wireless computer networks...
(WPA). In 2004, with the ratification of the full 802.11i standard (i.e. WPA2), the IEEE declared that both WEP-40 and WEP-104 "have been deprecated as they fail to meet their security goals".
Encryption details
WEP was included as the privacy component of the original IEEE 802.11IEEE 802.11
IEEE 802.11 is a set of standards for implementing wireless local area network computer communication in the 2.4, 3.6 and 5 GHz frequency bands. They are created and maintained by the IEEE LAN/MAN Standards Committee . The base version of the standard IEEE 802.11-2007 has had subsequent...
standard ratified in September 1999. WEP uses the stream cipher
Stream cipher
In cryptography, a stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream . In a stream cipher the plaintext digits are encrypted one at a time, and the transformation of successive digits varies during the encryption...
RC4
RC4
In cryptography, RC4 is the most widely used software stream cipher and is used in popular protocols such as Secure Sockets Layer and WEP...
for confidentiality
Confidentiality
Confidentiality is an ethical principle associated with several professions . In ethics, and in law and alternative forms of legal resolution such as mediation, some types of communication between a person and one of these professionals are "privileged" and may not be discussed or divulged to...
, and the CRC-32 checksum for integrity
Data integrity
Data Integrity in its broadest meaning refers to the trustworthiness of system resources over their entire life cycle. In more analytic terms, it is "the representational faithfulness of information to the true state of the object that the information represents, where representational faithfulness...
. It was deprecated in 2004 and is documented in the current standard.

Initialization vector
In cryptography, an initialization vector is a fixed-size input to a cryptographic primitive that is typically required to be random or pseudorandom...
(IV) to form the RC4 key. At the time that the original WEP standard was drafted, the U.S. Government's export restrictions on cryptographic technology
Export of cryptography
The export of cryptography in the United States is the transfer from the United States to another country of devices and technology related to cryptography....
limited the key size. Once the restrictions were lifted, manufacturers of access points implemented an extended 128-bit WEP protocol using a 104-bit key size (WEP-104).
A 64-bit WEP key is usually entered as a string of 10 hexadecimal
Hexadecimal
In mathematics and computer science, hexadecimal is a positional numeral system with a radix, or base, of 16. It uses sixteen distinct symbols, most often the symbols 0–9 to represent values zero to nine, and A, B, C, D, E, F to represent values ten to fifteen...
(base 16) characters (0-9 and A-F). Each character represents four bits, 10 digits of four bits each gives 40 bits; adding the 24-bit IV produces the complete 64-bit WEP key. Most devices also allow the user to enter the key as five ASCII characters, each of which is turned into eight bits using the character's byte value in ASCII; however, this restricts each byte to be a printable ASCII character, which is only a small fraction of possible byte values, greatly reducing the space of possible keys.
A 128-bit WEP key is usually entered as a string of 26 hexadecimal characters. 26 digits of four bits each gives 104 bits; adding the 24-bit IV produces the complete 128-bit WEP key. Most devices also allow the user to enter it as 13 ASCII characters.
A 256-bit WEP system is available from some vendors. As with the other WEP-variants 24 bits of that is for the IV, leaving 232 bits for actual protection. These 232 bits are typically entered as 58 hexadecimal characters. ((58 × 4 bits =) 232 bits) + 24 IV bits = 256-bit WEP key.
Key size is one of the security limitations in WEP. Cracking
Cryptanalysis
Cryptanalysis is the study of methods for obtaining the meaning of encrypted information, without access to the secret information that is normally required to do so. Typically, this involves knowing how the system works and finding a secret key...
a longer key requires interception of more packets, but there are active attacks that stimulate the necessary traffic. There are other weaknesses in WEP, including the possibility of IV collisions and altered packets, that are not helped by using a longer key.
Authentication
Two methods of authentication can be used with WEP: Open System authentication and Shared Key authentication.For the sake of clarity, we discuss WEP authentication in the Infrastructure mode (that is, between a WLAN client and an Access Point). The discussion applies to the ad-Hoc mode
Wireless ad-hoc network
A wireless ad-hoc network is a decentralized type of wireless network. The network is ad hoc because it does not rely on a preexisting infrastructure, such as routers in wired networks or access points in managed wireless networks...
as well.
In Open System authentication, the WLAN client need not provide its credentials to the Access Point during authentication. Any client can authenticate with the Access Point and then attempt to associate. In effect, no authentication occurs. Subsequently WEP keys can be used for encrypting data frames. At this point, the client must have the correct keys.
In Shared Key authentication, the WEP key is used for authentication in a four step challenge-response handshake:
- The client sends an authentication request to the Access Point.
- The Access Point replies with a clear-text challenge.
- The client encrypts the challenge-text using the configured WEP key, and sends it back in another authentication request.
- The Access Point decrypts the response. If this matches the challenge-text the Access Point sends back a positive reply.
After the authentication and association, the pre-shared WEP key is also used for encrypting the data frames using RC4
RC4
In cryptography, RC4 is the most widely used software stream cipher and is used in popular protocols such as Secure Sockets Layer and WEP...
.
At first glance, it might seem as though Shared Key authentication is more secure than Open System authentication, since the latter offers no real authentication. However, it is quite the reverse. It is possible to derive the keystream used for the handshake by capturing the challenge frames in Shared Key authentication. Hence, it is advisable to use Open System authentication for WEP authentication, rather than Shared Key authentication. (Note that both authentication mechanisms are weak.)
Flaws
Because RC4 is a stream cipherStream cipher
In cryptography, a stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream . In a stream cipher the plaintext digits are encrypted one at a time, and the transformation of successive digits varies during the encryption...
, the same traffic key must never be used twice. The purpose of an IV, which is transmitted as plain text, is to prevent any repetition, but a 24-bit IV is not long enough to ensure this on a busy network. The way the IV was used also opened WEP to a related key attack. For a 24-bit IV, there is a 50% probability the same IV will repeat after 5000 packets.
In August 2001, Scott Fluhrer, Itsik Mantin, and Adi Shamir
Adi Shamir
Adi Shamir is an Israeli cryptographer. He is a co-inventor of the RSA algorithm , a co-inventor of the Feige–Fiat–Shamir identification scheme , one of the inventors of differential cryptanalysis and has made numerous contributions to the fields of cryptography and computer...
published a cryptanalysis of WEP that exploits the way the RC4 cipher and IV is used in WEP, resulting in a passive attack that can recover the RC4 key
Key (cryptography)
In cryptography, a key is a piece of information that determines the functional output of a cryptographic algorithm or cipher. Without a key, the algorithm would produce no useful result. In encryption, a key specifies the particular transformation of plaintext into ciphertext, or vice versa...
after eavesdropping on the network. Depending on the amount of network traffic, and thus the number of packets available for inspection, a successful key recovery could take as little as one minute. If an insufficient number of packets are being sent, there are ways for an attacker to send packets on the network and thereby stimulate reply packets which can then be inspected to find the key. The attack was soon implemented, and automated tools have since been released. It is possible to perform the attack with a personal computer, off-the-shelf hardware and freely available software such as aircrack-ng
Aircrack-ng
Aircrack-ng is a network software suite consisting of a detector, packet sniffer, WEP and WPA/WPA2-PSK cracker and analysis tool for 802.11 wireless LANs. It works with any wireless network interface controller whose driver supports raw monitoring mode and can sniff 802.11a, 802.11b and 802.11g...
to crack any WEP key in minutes.
Cam-Winget et al. (2003) surveyed a variety of shortcomings in WEP. They write "Experiments in the field indicate that, with proper equipment, it is practical to eavesdrop on WEP-protected networks from distances of a mile or more from the target." They also reported two generic weaknesses:
- the use of WEP was optional, resulting in many installations never even activating it, and
- WEP did not include a key management protocol, relying instead on a single shared key among users.
In 2005, a group from the U.S. Federal Bureau of Investigation
Federal Bureau of Investigation
The Federal Bureau of Investigation is an agency of the United States Department of Justice that serves as both a federal criminal investigative body and an internal intelligence agency . The FBI has investigative jurisdiction over violations of more than 200 categories of federal crime...
gave a demonstration where they cracked a WEP-protected network in 3 minutes using publicly available tools. Andreas Klein presented another analysis of the RC4 stream cipher. Klein showed that there are more correlations between the RC4 keystream and the key than the ones found by Fluhrer, Mantin and Shamir which can additionally be used to break WEP in WEP-like usage modes.
In 2006, Bittau, Handley
Mark Handley (computer scientist)
Mark Handley is Professor of Networked Systems in the Department of Computer Science of University College London since 2003, where he leads the Networks Research Group...
, and Lackey showed that the 802.11 protocol itself can be used against WEP to enable earlier attacks that were previously thought impractical. After eavesdropping a single packet, an attacker can rapidly bootstrap to be able to transmit arbitrary data. The eavesdropped packet can then be decrypted one byte at a time (by transmitting about 128 packets per byte to decrypt) to discover the local network IP addresses. Finally, if the 802.11 network is connected to the Internet, the attacker can use 802.11 fragmentation to replay eavesdropped packets while crafting a new IP header onto them. The access point can then be used to decrypt these packets and relay them on to a buddy on the Internet, allowing real-time decryption of WEP traffic within a minute of eavesdropping the first packet.
In 2007, Erik Tews, Andrei Pychkine, and Ralf-Philipp Weinmann were able to extend Klein's 2005 attack and optimize it for usage against WEP. With the new attack it is possible to recover a 104-bit WEP key with probability 50% using only 40,000 captured packets. For 60,000 available data packets, the success probability is about 80% and for 85,000 data packets about 95%. Using active techniques like deauth and ARP
Address Resolution Protocol
Address Resolution Protocol is a telecommunications protocol used for resolution of network layer addresses into link layer addresses, a critical function in multiple-access networks. ARP was defined by RFC 826 in 1982. It is Internet Standard STD 37...
re-injection, 40,000 packets can be captured in less than one minute under good conditions. The actual computation takes about 3 seconds and 3 MB of main memory on a Pentium-M 1.7 GHz and can additionally be optimized for devices with slower CPUs. The same attack can be used for 40-bit keys with an even higher success probability.
In 2008, Payment Card Industry
Payment card industry
The payment card industry denotes the debit, credit, prepaid, e-purse, ATM, and POS cards and associated businesses.The term is sometimes more specifically used to refer to the Payment Card Industry Security Standards Council, a council originally formed by American Express, Discover Financial...
(PCI) Security Standards Council’s latest update of the Data Security Standard
PCI DSS
The Payment Card Industry Data Security Standard is an information security standard for organizations that handle cardholder information for the major debit, credit, prepaid, e-purse, ATM, and POS cards....
(DSS), prohibits use of the WEP as part of any credit-card processing after 30 June 2010, and prohibits any new system from being installed that uses WEP after 31 March 2009. The use of WEP contributed to the T.J. Maxx parent company network invasion.
Remedies
Use of encrypted tunneling protocols (e.g. IPSecIPsec
Internet Protocol Security is a protocol suite for securing Internet Protocol communications by authenticating and encrypting each IP packet of a communication session...
, Secure Shell
Secure Shell
Secure Shell is a network protocol for secure data communication, remote shell services or command execution and other secure network services between two networked computers that it connects via a secure channel over an insecure network: a server and a client...
) can provide secure data transmission over an insecure network. However, replacements for WEP have been developed with the goal of restoring security to the wireless network itself.
802.11i (WPA and WPA2)
The recommended solution to WEP security problems is to switch to WPA2. WPAWi-Fi Protected Access
Wi-Fi Protected Access and Wi-Fi Protected Access II are two security protocols and security certification programs developed by the Wi-Fi Alliance to secure wireless computer networks...
was an intermediate solution for hardware that could not support WPA2, but it has been cracked. Either is much more secure than WEP. To add support for WPA or WPA2, some old Wi-Fi access point
Wireless access point
In computer networking, a wireless access point is a device that allows wireless devices to connect to a wired network using Wi-Fi, Bluetooth or related standards...
s might need to be replaced or have their firmware
Firmware
In electronic systems and computing, firmware is a term often used to denote the fixed, usually rather small, programs and/or data structures that internally control various electronic devices...
upgraded. WPA was designed as an interim software-implementable solution for WEP that could forestall immediate deployment of new hardware. However, TKIP (the basis of WPA) has reached the end of its designed lifetime, has been broken, and has been deprecated in the next full release of the 802.11 standard.
WEP2
This stopgap enhancement to WEP was present in some of the early 802.11i drafts. It was implementable on some (not all) hardware not able to handle WPA or WPA2, and extended both the IV and the key values to 128 bits. It was hoped to eliminate the duplicate IV deficiency as well as stop brute forceBrute force attack
In cryptography, a brute-force attack, or exhaustive key search, is a strategy that can, in theory, be used against any encrypted data. Such an attack might be utilized when it is not possible to take advantage of other weaknesses in an encryption system that would make the task easier...
key attacks.
After it became clear that the overall WEP algorithm was deficient (and not just the IV and key sizes) and would require even more fixes, both the WEP2 name and original algorithm were dropped. The two extended key lengths remained in what eventually became WPA's TKIP.
WEPplus
WEPplus, also known as WEP+, is a proprietary enhancement to WEP by Agere SystemsAgere Systems
Agere Systems Inc. was an integrated circuit components company based in Allentown, Pennsylvania. Spun out of Lucent Technologies in 2002, Agere was merged into LSI Corporation in 2007....
(formerly a subsidiary of Lucent Technologies
Lucent Technologies
Alcatel-Lucent USA, Inc., originally Lucent Technologies, Inc. is a French-owned technology company composed of what was formerly AT&T Technologies, which included Western Electric and Bell Labs...
) that enhances WEP security by avoiding "weak IVs". It is only completely effective when WEPplus is used at both ends of the wireless connection. As this cannot easily be enforced, it remains a serious limitation. It also does not necessarily prevent replay attack
Replay attack
A replay attack is a form of network attack in which a valid data transmission is maliciously or fraudulently repeated or delayed. This is carried out either by the originator or by an adversary who intercepts the data and retransmits it, possibly as part of a masquerade attack by IP packet...
s.
Dynamic WEP
Dynamic WEP refers to the combination of 802.1x technology and the Extensible Authentication ProtocolExtensible Authentication Protocol
Extensible Authentication Protocol, or EAP, is an authentication framework frequently used in wireless networks and Point-to-Point connections. It is defined in RFC 3748, which made RFC 2284 obsolete, and was updated by RFC 5247....
. Dynamic WEP changes WEP keys dynamically. It is a vendor-specific feature provided by several vendors such as 3Com
3Com
3Com was a pioneering digital electronics manufacturer best known for its computer network infrastructure products. The company was co-founded in 1979 by Robert Metcalfe, Howard Charney, Bruce Borden, and Greg Shaw...
.
The dynamic change idea made it into 802.11i as part of TKIP, but not for the actual WEP algorithm.

