
Hacking: The Art of Exploitation Second Edition
Encyclopedia
Author and background information
This book is written by Jon Erickson and was published in 2008. Jon Erickson is a computer security expert, with a background in computer science. He currently works as a vulnerabilityVulnerability (computing)
In computer security, a vulnerability is a weakness which allows an attacker to reduce a system's information assurance.Vulnerability is the intersection of three elements: a system susceptibility or flaw, attacker access to the flaw, and attacker capability to exploit the flaw...
researcher and computer security
Computer security
Computer security is a branch of computer technology known as information security as applied to computers and networks. The objective of computer security includes protection of information and property from theft, corruption, or natural disaster, while allowing the information and property to...
specialist in California. He also wrote Hacking: The Art of Exploitation
Hacking: The Art of Exploitation
Hacking: The Art of Exploitation is a book written by Jon "Smibbs" Erickson and published by No Starch Press in 2003. It is a computer security and network security book. All of the examples in the book were developed, compiled, and tested on Gentoo Linux.-Content:The content of Hacking moves...
, the first edition. The contents of this book are intended to be shared with everyone who wants to learn about computer hacking
Hacking
Hacking may refer to:* Computer hacking, including the following types of activity:** Hacker , activity within the computer programmer subculture** Hacker , to access computer networks, legally or otherwise...
. This book tries not only to give the reader an understanding about computer hacking but to make it easy for them to read. The book includes many pictures of code and examples on how to accomplish the techniques which are taught in the book. A bootable CD is included with the book which provides a linux
Linux
Linux is a Unix-like computer operating system assembled under the model of free and open source software development and distribution. The defining component of any Linux system is the Linux kernel, an operating system kernel first released October 5, 1991 by Linus Torvalds...
-based programming and debugging
Debugging
Debugging is a methodical process of finding and reducing the number of bugs, or defects, in a computer program or a piece of electronic hardware, thus making it behave as expected. Debugging tends to be harder when various subsystems are tightly coupled, as changes in one may cause bugs to emerge...
environment for the users. The bootable CD is very useful because the users can try out the techniques that are taught in the book while they are reading it. A lot of the information in this book requires some computer and programming knowledge to fully understand it.
Introduction
In the introduction of this book it makes a clear point that hacking should be about following the law and ways to prevent computer hacking. This book does not condone hacking when it is used for the wrong reasons. Furthermore the introduction describes how to think outside the box and gives a background of some basic ideas of computer hacking. However hacking can be used for good reasons also, like the preventative ones. Knowing how to hack into computers also gives you the ability to understand and prevent ways of having your own computer to be hacked into. The book is going to provide a solid base for understanding computer and network security issues. As the reader will get further into the book the information begins to get more complex. Being able to understand the concepts illustrated further into this book can only better a person’s understanding of the computer security world.0x200 Programming
Programming is a series of statements written in a specific language. Programs are used everyday for millions of different things. Computers use machine language in order to understand the commands that we want to give to them. Programs are written for these machine languages so that they are more easily understood by the machines and by the people writing the commands. To make this process easier, translators (assemblerAssembler
Assembler may refer to:* Assembler , for an assembly language, a computer program to translate between lower-level representations of computer programs...
and compiler
Compiler
A compiler is a computer program that transforms source code written in a programming language into another computer language...
) were created to translate less complex code into machine languages, making it easier for people and computers to understand what is happening. The languages that were created to be translated into machine code were ones like C
C (programming language)
C is a general-purpose computer programming language developed between 1969 and 1973 by Dennis Ritchie at the Bell Telephone Laboratories for use with the Unix operating system....
, C++
C++
C++ is a statically typed, free-form, multi-paradigm, compiled, general-purpose programming language. It is regarded as an intermediate-level language, as it comprises a combination of both high-level and low-level language features. It was developed by Bjarne Stroustrup starting in 1979 at Bell...
, and Fortran
Fortran
Fortran is a general-purpose, procedural, imperative programming language that is especially suited to numeric computation and scientific computing...
. Having the ability to translate programming languages into machine code saves a lot of time and resources. In the programming chapter of this book the different types of programs are described as well as shown by examples of actual coding in the book.
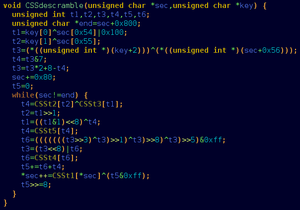
Changing the flow from a program's execution into a more complex flow is known as a control structure. A common type of control structure is the if-then-else statement. This type of control structure in certain cases makes it possible for a program to take a different route during the execution of the program. The if-then-else statement is a very commonly used part of programming and there are good examples of the actual code written in this book.
More Fundamental Programming Concepts
Variables, arithmetic operators, comparison operators and functions are some of the fundamental programming concepts. These types of concepts make the program able to compute things such as using numbers, decimals, and signs like > or =. All of these signs are very common and mean exactly what they appear to like the greater than sign (>). The use of these fundamental programming concepts greatly approves one’s ability to write and understand programming code. The examples in the book in relation to fundamental concepts do a very good job of showing the reader what they should look like.
Getting Your Hands Dirty
This part of the book is about using the live CD to practice some programming concepts. Now that some background in computer programming has been explained it is time to try some programming. Knowing a programming language like C will help when it comes to trying out computer programming
Computer programming
Computer programming is the process of designing, writing, testing, debugging, and maintaining the source code of computer programs. This source code is written in one or more programming languages. The purpose of programming is to create a program that performs specific operations or exhibits a...
. The live CD provides an environment so that the reader can not only follow along in the book but actually do some programming themselves. The examples illustrated in the book are also on the live CD.
Back to Basics
Applying some new ideas like strings and pointers to the computer programming makes things even easier. Most of the programming is done by using English words and phrases so that they are very basic commands. Once again the reader will be able to experience this with the live CD.
Memory Segmentation
A program's memory is divided into five segments: text, data, bss, heap, and stack. These segments tell the program where certain things are located and when the program is going to be executed. When the program is executed it compiles and finds the segments in which it needs to for the completion of the program. Depending on what type of program or what type of code is written the location of the order to execute the program will be in the five segments.
Building on Basics
Now that the basic components of C have been explained things become easier to understand. This part of the book talks about everything from file access to setting file permissions that are used by functions in C. Knowing these functions once again is applied by having a background in C and some of them will be taught to you in the book. At the end of this chapter is a computer program
Computer program
A computer program is a sequence of instructions written to perform a specified task with a computer. A computer requires programs to function, typically executing the program's instructions in a central processor. The program has an executable form that the computer can use directly to execute...
that is set up like a game of chance. The coding and implementation of code is in the book along with other examples of programming code.
0x300 Exploitation
ExploitationExploitation
This article discusses the term exploitation in the meaning of using something in an unjust or cruel manner.- As unjust benefit :In political economy, economics, and sociology, exploitation involves a persistent social relationship in which certain persons are being mistreated or unfairly used for...
is taking the computer's code or set of rules and changing them so the computer does what you want it do. Finding ways or holes in the system to change is an important part of exploitation. Knowing where to look and what to look for is also a key concept when finding exploits. There are many cases of exploitation in real world scenarios and is one reason why this chapter is a very important one. Exploitation is one of the most fundamental concepts when talking about computer hacking. Most of the time a hacker
Hacker (computer security)
In computer security and everyday language, a hacker is someone who breaks into computers and computer networks. Hackers may be motivated by a multitude of reasons, including profit, protest, or because of the challenge...
is going to exploit information or code that another person has created so there is most likely going to be some errors in it. An example of a program not being coded correctly is something a hacker will find and exploit.
Generalized Exploit Techniques
Most program exploits have to do with memory corruption and Buffer
Buffer
Buffer may refer to:*Buffer state, a country lying between two potentially hostile greater powers, thought to prevent conflict between them* Buffer zone, any area that keeps two or more other areas distant from one another, may be demilitarized...
Overflows. Each technique used in the book is one that requires the computer to allow you to change the actual code of the program or insert your own code. If a hacker can insert their own code into the program then it will run however the code tells it to which means a hacker can tell the computer what to do.
Buffer Overflows
Buffer Overflows have been around since the first computers were invented. Internet
Internet
The Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
worms even use buffer overflows to exploit vulnerabilities in programs like Internet Explorer
Internet Explorer
Windows Internet Explorer is a series of graphical web browsers developed by Microsoft and included as part of the Microsoft Windows line of operating systems, starting in 1995. It was first released as part of the add-on package Plus! for Windows 95 that year...
. A buffer overflow is when a programmer does not allow even bytes of data to be processed in the code and has more bytes than he is supposed to. When the program goes to execute the code it will overflow and information can sometimes be overwritten or lost.
Experimenting With Bash
Knowing how Perl
Perl
Perl is a high-level, general-purpose, interpreted, dynamic programming language. Perl was originally developed by Larry Wall in 1987 as a general-purpose Unix scripting language to make report processing easier. Since then, it has undergone many changes and revisions and become widely popular...
, the interpreted programming language, works is essential in this chapter. Perl
Perl
Perl is a high-level, general-purpose, interpreted, dynamic programming language. Perl was originally developed by Larry Wall in 1987 as a general-purpose Unix scripting language to make report processing easier. Since then, it has undergone many changes and revisions and become widely popular...
is used to create buffer overflows and use shellcode to implement its own executions. There are a lot of programming code examples in this chapter that are needed to understand how Perl
Perl
Perl is a high-level, general-purpose, interpreted, dynamic programming language. Perl was originally developed by Larry Wall in 1987 as a general-purpose Unix scripting language to make report processing easier. Since then, it has undergone many changes and revisions and become widely popular...
and Bash shellcode work. A debugger
Debugger
A debugger or debugging tool is a computer program that is used to test and debug other programs . The code to be examined might alternatively be running on an instruction set simulator , a technique that allows great power in its ability to halt when specific conditions are encountered but which...
is also used in this chapter to find out where shellcode
Shellcode
In computer security, a shellcode is a small piece of code used as the payload in the exploitation of a software vulnerability. It is called "shellcode" because it typically starts a command shell from which the attacker can control the compromised machine. Shellcode is commonly written in...
is used in programs. Buffer overflows can happen in other memory segments also like the heap and bss. The exploitation of the heap and bss can also be used when buffer overflows occur. Once again the coding which is located in the book will give the user a better idea of how these exploitation techniques work.
Format Strings
A Format string is another way to find exploits in programming mistakes. However vulnerabilities in this area are not as common as they used to be but they are easy to notice. Essentially using the wrong functions in programming code creates these format string mistakes. Looking at the programming code in the book or using the live cd make these mistakes very noticeable to the user.
0x400 Networking
Communication can give programs more power especially when connected to the internet. People and programs use the internet everyday and there is a lot of information and programs on the internet. Even applications like emailEmail
Electronic mail, commonly known as email or e-mail, is a method of exchanging digital messages from an author to one or more recipients. Modern email operates across the Internet or other computer networks. Some early email systems required that the author and the recipient both be online at the...
and instant messaging
Instant messaging
Instant Messaging is a form of real-time direct text-based chatting communication in push mode between two or more people using personal computers or other devices, along with shared clients. The user's text is conveyed over a network, such as the Internet...
could not exist without networking. Protocols
Communications protocol
A communications protocol is a system of digital message formats and rules for exchanging those messages in or between computing systems and in telecommunications...
are used throughout networking for communication between devices and one example of a protocol is ipv4
IPv4
Internet Protocol version 4 is the fourth revision in the development of the Internet Protocol and the first version of the protocol to be widely deployed. Together with IPv6, it is at the core of standards-based internetworking methods of the Internet...
.
OSI Model
In communication among computers through networking the OSI Model
OSI model
The Open Systems Interconnection model is a product of the Open Systems Interconnection effort at the International Organization for Standardization. It is a prescription of characterizing and standardizing the functions of a communications system in terms of abstraction layers. Similar...
is used. The OSI Model is a model that provides the standards that computers use to communicate. There are seven layers in the OSI Model and they are Physical layer, Data-Link layer, Network layer, Transport layer, Session layer, Presentation layer, and Application layer. Each packet that a computer sends out to another computer must go through each layer of the OSI Model.
Sockets
The standard way to communicate on a network with the use of computer operating systems is a socket
Internet socket
In computer networking, an Internet socket or network socket is an endpoint of a bidirectional inter-process communication flow across an Internet Protocol-based computer network, such as the Internet....
. A socket is used by a programmer to create a way to send and receive data using the layers of the OSI. There are two types of sockets a Stream Socket and a Datagram Socket. Stream Sockets use Transmission Control Protocol
Transmission Control Protocol
The Transmission Control Protocol is one of the core protocols of the Internet Protocol Suite. TCP is one of the two original components of the suite, complementing the Internet Protocol , and therefore the entire suite is commonly referred to as TCP/IP...
(TCP). A Datagram Socket uses User Datagram Protocol (UDP).
Peeling Back the Layers
Peeling back of the layers describes how the OSI layers actually work. The OSI Model is described in great detail with some images in the book that make it easy to understand.
Network Sniffing
Switched and unswitched networks exist in networking. A switched network uses devices called switches that analyze and tell the packets travelling on the network where their endpoint is. An unswitched network is a free flow of packets without them being stopped and analyzed. Sniffing refers to using a program that allows you to see packets on the network and where they are going.
Denial of Service
A denial of service attack is an attempt to make a computer resource unavailable to its intended users. This means that the denial of service attack sends a large quantity of communication requests to an intended resource in order to overflow the resource so that it becomes unusable for a certain period of time. These types of attacks are usually directed at a routers or firewalls in order to shut them down to gain access to other computers on the network. A router is very susceptible to these types of attacks but a firewall can usually handle the attack and is unaffected. A distributed denial of service attack is when communication requests come from multiple computers making the amount of requests greatly more than a regular denial of service attack. Some other types of DOS attacks include Ping of Death
Ping of death
A ping of death is a type of attack on a computer that involves sending a malformed or otherwise malicious ping to a computer. A ping is normally 32 bytes in size ; historically, many computer systems could not handle a ping packet larger than the maximum IPv4 packet size, which is 65,535 bytes...
, Teardrop, Ping Flooding, and Amplification attacks.
TCP/IP Hijacking
TCP/IP Hijacking is another way that uses spoofed packets to take over a connection between the victim and a host machine. This technique is mainly used to collect passwords when a host machine uses a password to be connected to. When this type of attack takes place the victim and the attacker must be on the same network. Another form of TCP/IP hijacking is RST hijacking. When injecting an authentic looking reset packet instead of a real reset packet it is called RST hijacking.
Port Scanning
Port scanning is simply a way to figure out which ports are accepting and listening to connections. The hacker would just use a program that lets him know which ports are open by scanning all the ports on a network and trying to open them. There are many other type of scans also like SYN, Idle, FIN, X-Mas, and Null scans.
Reach Out and Hack Someone
This part is about finding vulnerabilities in the typecasting of the network. Using a debugger to go through lines of code which are used for network protocols is the most efficient way to accomplish this. Once the vulnerabilities are found it is up to the hacker how they want to exploit them.
0x500 Shellcode
Shellcode is used in the exploitation of code. It is like the hacker's own code that he wants to run when he gains control over a program. Usually a hacker will find an exploit in a programs code and be able to insert some of his own code (shellcode) where he found the exploit.Assembly vs. C
Assembly
Assembly (programming)
An assembly is a runtime unit consisting of types and other resources. All types in an assembly have the same version number.Often, one assembly has only one namespace and is used by one program. But it can span over several namespaces. Also, one namespace can spread over several assemblies...
differs from C because assembly is a low-level programming language
Low-level programming language
In computer science, a low-level programming language is a programming language that provides little or no abstraction from a computer's instruction set architecture. Generally this refers to either machine code or assembly language...
and when processed can communicate directly with the processor. When using C which is a high-level programming language the code must be compiled and sent to the kernel by making a system call and then making a call to the processor. In other words it is almost like taking the system calling to the kernel out of the picture when using assembly.
The Path to shellcode
This part of shellcode is about how to inject a program with shellcode so it can be taken over. There are many examples of code in the book and ways to accomplish this task.
Self-spawning shellcode
Spawning shellcode is code that will be enabled when an exploit is found. It is shellcode that will be able to be run when a vulnerability is found in the program. The best way to accomplish this is shown in the book and by making sure the code is very small.
Port-binding shellcode
This type of shellcode attaches itself to a network port. Once bound to a port it will listen for a TCP connection. After it finds the TCP connection there is a lot more programming involved and is shown vividly in the book.
Connect-back shellcode
This type of shellcode is mainly used when getting around firewalls. Most firewalls are going to block port-binding shellcode form working because they are set up to only allow known services through the active ports. Connect-back shellcode initiates the connection back to the hacker's IP address so it will be coming out from the firewall instead of going into it. Once again the code it the book depicts with the use of shellcode on ways to accomplish this.
0x600 Countermeasures
This part of the book is about having defenses and intrusion prevention systems to stop the hacking exploits which we now know about. Not only can hacking be harmful, hacking can be considered helpful because it also produces way to stop the exploits and new ways to better the computer industry.Countermeasures That Detect
An administrator
Network administrator
A network administrator, network analyst or network engineer is a person responsible for the maintenance of computer hardware and software that comprises a computer network...
of the network has to be aware of when an exploit may be occurring. Using certain tools like reading logs or packet sniffing on the network are a few ways to catch exploits when they occur. Anticipating what how the hacker is going to try to penetrate the system or network is the administrator’s most valuable tool. If an administrator knows where to look and catches a hacker in the middle of the attack he can quickly shut down the program and restore files from back up. Once a hacker is detected it is a lot easier to deploy countermeasures. If a hacker is not caught he can sometimes go months without being noticed and steal large amounts of data. This is why stealth is a hackers best friend.
System Daemons
A System Daemon is a server program on a Unix
Unix
Unix is a multitasking, multi-user computer operating system originally developed in 1969 by a group of AT&T employees at Bell Labs, including Ken Thompson, Dennis Ritchie, Brian Kernighan, Douglas McIlroy, and Joe Ossanna...
system which receives and accepts incoming connections. A daemon is a program which runs in the background and detaches from controlling the terminal in a certain way. At this point in the book there is some code shown on how to run a daemon program. Signals are also used in a Unix based environment to make operating system calls. When a signal is type in the terminal it will immediately send an interrupt message to complete the task of whatever the signal was which was typed. The uses of signals are displayed in some coding examples in the book.
Tools of the Trade
A hacker has a certain set of tools that he needs to help him when exploiting. An exploit script is a tool in which uses already written exploit code to find holes in the system or program. Using exploit scripts is easy for even a non-hacker to use because the code is already written in it. A couple exams of some exploit tools are shown in the book and how to use them.
Log Files
As stated earlier log files are away to check events that have been happening on a computer or network. Checking these log files is one way to make sure everything is running correctly. If an error is discovered in a log file it is very easy to tell what the problem is. For a hacker having the ability to change what the log file says can help him not to be noticed. There is code and directions on how to change some log files in the book.
Overlooking the Obvious
Another sign of a program being hacked is that it will no longer work correctly. Most of the time programs do not work correctly because the hacker has modified them do accomplish another task. A skilled hacker however can modify the program so it still works correctly and does what he wants it do. If a program is exploited there are ways to tell how it happened. Finding out how a program was exploited can be a very tedious process since it usually starts with taking parts of the program and looking at them individually. Putting a exploited program back together again to see how it was exploited is shown in the book.
Advanced Camouflage
When a hacker is exploiting a program his IP address can be written to a log file. Camouflaging the log files so that his IP address can not be detected is shown in the book. When an IP address
IP address
An Internet Protocol address is a numerical label assigned to each device participating in a computer network that uses the Internet Protocol for communication. An IP address serves two principal functions: host or network interface identification and location addressing...
is hidden, it is called spoofing the IP address. There are a few ways shown in the book on how to not show up in the log files of a computer while hacking.
The Whole Infrastructure
The use of intrusion detection systems and intrusion prevention systems greatly helps avoid the risk of being exploited. Even firewalls and routers have log files that can show evidence of hacking. Making sure that outbound TCP connections cannot be processed is one way to limit being found. A few ways are shown in the book on how to use TCP connections so that it is easier to go undetected.
Payload Smuggling
When using shellcode to exploit programs, it can be caught by intrusion detection systems. Usually the intrusion detection system will catch the programs that are already written and have noticeable shell code in them. Most exploit programs will be caught because real hackers are not using them. There are ways to hide shellcode so it can be harder to detect which. A couple ways and examples on how to hide shellcode are found in the book.
Buffer Restrictions
Sometimes there are restrictions put on buffers so that vulnerabilities cannot be exploited. There are a few ways that the book depicts on how to get around buffer restrictions.
Hardening Countermeasures
The exploits that are found in this book have been around for a long time. It took hackers a while before they figured out how to take advantage of the vulnerabilities described in this book. Memory corruption, a change of control, and the use of shellcode are the three easiest steps to exploitation.
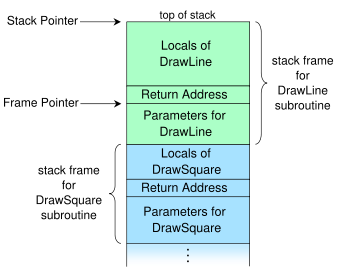
Most applications do not use the stack for any type of executing. One defense is to make the stack non-executable so that buffer overflows cannot be used in the exploitation of the program. This defense is very effective for stopping the use of shellcode in an application. However there is a way to get around the use of a non-executable stack which is shown and described in the book.
Randomized Stack Space
A randomized stack is a type of countermeasure used so that the hacker is unable to tell where the shellcode he implemented is. It randomizes the memory layout within the stack. Once again, there is also a way to get around this countermeasure with some examples in the book.
0x700 Cryptology
Cryptology is the use of communicating secretly through the use of ciphers, and cryptanalysis is the process of cracking or deciphering such secret communications. The uses of encryption methods are common in today's world so that credit card and other valuable information cannot be stolen.Information Theory
This part of the book refers to Claude Shannon and his expertise in cryptology. A few concepts of cryptology are unconditional security, one-time pad
One-time pad
In cryptography, the one-time pad is a type of encryption, which has been proven to be impossible to crack if used correctly. Each bit or character from the plaintext is encrypted by a modular addition with a bit or character from a secret random key of the same length as the plaintext, resulting...
s, quantum key distribution, and computational security. These concepts were influenced by the ideas of Claude Shannon.
Algorithmic Run Time
When using algorithms in computer code, the time calculated to evaluate the code is called algorithmic run time. These times will vary depending on how big or small the algorithms are. One way to express an algorithms efficiency is by Asymptotic Notation. Since some algorithms can have infinite sizes asymptotic notation must be used to calculate efficiency. There is also another mathematical notation called big-oh notation which also calculates algorithms efficiency.
Symmetric Encryption
Using the same key to encrypt and to decrypt messages is symmetric encryption. Asymmetric encryption in usually faster however when using different keys it can become difficult. The book gives some examples of symmetric encryption and how to use them in this chapter.
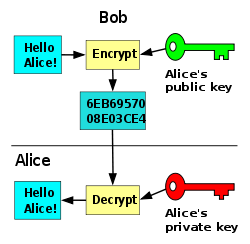
This type of encryption uses to different keys, one for encrypting and the other for decrypting. The two keys that are used are called public (encryption) and private keys (decryption). The book once again gives some examples of asymmetric encryption and how to use them.
Hybrid Ciphers
A cipher is an encryption algorithm. Combining the use of a symmetric cipher and asymmetric cipher is called a hybrid cipher. Asymmetric key pairs provide better protection than a symmetric key but they're slower at encrypting/decrypting. For this reason an asymmetric key pair is used to establish a symmetric key so the communicating parties have the benefit of authentication without the speed penalities. Ways to attack ciphers and to get around some encryption methods are shown and described in the book.
Password Cracking
Passwords stored on a computer are usually encrypted. Of course this chapter is going to shown examples and methods on how to get past some encryption methods. A couple methods are Brute-force attacks and hash look-ups. There are many more password methods shown in the book.
Wireless 802.11b Encryption
Wireless Internet is very insecure when it comes to some encryption methods. Examples of why wireless is insecure arise in this chapter as well as ways to get around the encryption.
WEP Attacks
Wired equivalent privacy (WEP) is not very secure and was not supposed to be very secure. There are many ways to attack it and its cryptographic protocols are not very good. The book gives many examples of ways to get around WEP and also ways to prevent WEP attacks.
See also
- Hacking: The Art of ExploitationHacking: The Art of ExploitationHacking: The Art of Exploitation is a book written by Jon "Smibbs" Erickson and published by No Starch Press in 2003. It is a computer security and network security book. All of the examples in the book were developed, compiled, and tested on Gentoo Linux.-Content:The content of Hacking moves...
- Attack (computer)Attack (computer)In computer and computer networks an attack is any attempt to destroy, expose, alter, disable, steal or gain unauthorized access to or make unauthorized use of an asset.- IETF :Internet Engineering Task Force defines attack in RFC 2828 as:...
- Computer securityComputer securityComputer security is a branch of computer technology known as information security as applied to computers and networks. The objective of computer security includes protection of information and property from theft, corruption, or natural disaster, while allowing the information and property to...
- Information securityInformation securityInformation security means protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction....
- IT riskIT riskInformation technology risk, or IT risk, IT-related risk, is a risk related to information technology. This relatively new term due to an increasing awareness that information security is simply one facet of a multitude of risks that are relevant to IT and the real world processes it...
- Threat (computer)Threat (computer)In Computer security a threat is a possible danger that might exploit a vulnerability to breach security and thus cause possible harm.A threat can be either "intentional" or "accidental" In Computer security a threat is a possible danger that might exploit a vulnerability to breach security and...
- Vulnerability (computing)Vulnerability (computing)In computer security, a vulnerability is a weakness which allows an attacker to reduce a system's information assurance.Vulnerability is the intersection of three elements: a system susceptibility or flaw, attacker access to the flaw, and attacker capability to exploit the flaw...

