Transient-key cryptography
Encyclopedia
Transient-key cryptography is a form of public-key cryptography
wherein keypairs are generated and assigned to brief intervals of time instead of to individuals or organizations. In a transient-key system, private keys are used briefly and then destroyed, which is why it is sometimes nicknamed “disposable crypto.” Data encrypted with a private key associated with a specific time interval can be irrefutably linked to that interval, making transient-key cryptography
particularly useful for digital trusted timestamping
.
s that assert that a given piece of data has not changed since it was signed. But the similarities end there.
In a traditional public key system, the public/private keypair is typically assigned to an individual, server, or organization. Data signed by a private key asserts that the signature came from the indicated source. Keypairs persist for years at a time, so the private component must be carefully guarded against disclosure; in a public-key system, anyone with access to a private key can counterfeit that person’s digital signature.
In transient-key systems, however, the keypair is assigned to a brief interval of time, not to a particular person or entity. Data signed by a specific private key becomes associated with a specific time and date. A keypair is active only for a few minutes, after which the private key is permanently destroyed. Therefore, unlike public-key systems, transient-key systems do not depend upon the long-term security of the private keys.
Instead, data is digitally signed with a time value derived from Universal Coordinated Time (UTC) accurate to within a millisecond, in accordance with the ANSI ASC X9.95 standard for Trusted Timestamping
.
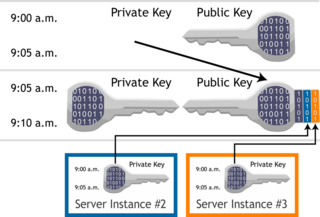
Whenever a time interval in a transient-key system expires, a new public/private keypair is generated, and the private key from the previous interval is used to digitally certify the new public key. The old private key is then destroyed.
For the new interval, time values are obtained from a trusted third-party source, and specific moments in time can be interpolated in between received times by using a time-biasing method based on the internal system timer. If a trusted time source cannot be obtained or is not running within specified tolerances
, transient private keys are not issued. In that case, the time interval chain is terminated, and a fresh one is begun. The old and new chains are connected through network archives, which enable all servers to continue to verify the data integrity
through time of protected data, regardless of how often the chain must be restarted.
The start times of the chain and of each interval can be coupled together to form an unbroken sequence of public keys, which can be used for the following:
As an extra security measure, all requests for signatures made during an interval are stored in a log that is concatenated and is itself appended to the public key at the start of the next interval. This mechanism makes it impossible to insert new “signed events” into the interval chain after the fact.
of traditional public key systems can be compromised if a single private key is exposed.
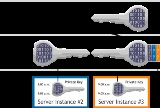
An individual transient key interval chain can be cross-certified with other transient key chains and server instances. Through cross-certification, Server A signs Server B's interval chain, the signed data of which is the interval definition. In effect, the private keys from Server B are used to sign the public keys of Server A. In the diagram, a server instance is cross-certified with two other server instances (blue and orange).
 Cross-certification requires that the timestamp for the interval agree with the timestamp of the cross-certifying server within acceptable tolerances, which are user-defined and typically a few hundred milliseconds in duration.
Cross-certification requires that the timestamp for the interval agree with the timestamp of the cross-certifying server within acceptable tolerances, which are user-defined and typically a few hundred milliseconds in duration.
is a logical database
that can be stored and replicated on any system to enable verification of data that has been timestamped and signed by transient keys. A map of the set of accessible archives is stored within every digital signature created in the system. Whenever cross-certifications are completed at the beginning of an interval, the archive map is updated and published to all servers in the network.
the data at a later time, a receiver accesses the persistent
public key for the appropriate time interval. The public key applied to the digital signature can be passed through published cryptographic routines to unpack the hash
of the original data, which is then compared against a fresh hash of the stored data to verify data integrity. If the signature successfully decrypts using a particular interval’s published public key, the receiver can be assured that the signature originated during that time period. If the decrypted and fresh hashes match, the receiver can be assured that the data has not been tampered with since the transient private key created the timestamp and signed the data.
Transient-key cryptography was invented by Dr. Michael D. Doyle of Eolas Technologies Inc. and later acquired by and productized by ProofSpace, Inc. It is protected under US Patent #6,381,696 and has been included in the ANSI ASC X9.95 standard for Trusted Timestamping
.
Public-key cryptography
Public-key cryptography refers to a cryptographic system requiring two separate keys, one to lock or encrypt the plaintext, and one to unlock or decrypt the cyphertext. Neither key will do both functions. One of these keys is published or public and the other is kept private...
wherein keypairs are generated and assigned to brief intervals of time instead of to individuals or organizations. In a transient-key system, private keys are used briefly and then destroyed, which is why it is sometimes nicknamed “disposable crypto.” Data encrypted with a private key associated with a specific time interval can be irrefutably linked to that interval, making transient-key cryptography
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
particularly useful for digital trusted timestamping
Trusted timestamping
Trusted timestamping is the process of securelykeeping track of the creation and modification time of a document. Securityhere means that no one — not even the owner of the document — should be able to change it once it has been recorded provided that the timestamper's integrity is never...
.
Public-key vs. transient-key cryptography
Both public-key and transient-key systems can be used to generate digital signatureDigital signature
A digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender, and that it was not altered in transit...
s that assert that a given piece of data has not changed since it was signed. But the similarities end there.
In a traditional public key system, the public/private keypair is typically assigned to an individual, server, or organization. Data signed by a private key asserts that the signature came from the indicated source. Keypairs persist for years at a time, so the private component must be carefully guarded against disclosure; in a public-key system, anyone with access to a private key can counterfeit that person’s digital signature.
In transient-key systems, however, the keypair is assigned to a brief interval of time, not to a particular person or entity. Data signed by a specific private key becomes associated with a specific time and date. A keypair is active only for a few minutes, after which the private key is permanently destroyed. Therefore, unlike public-key systems, transient-key systems do not depend upon the long-term security of the private keys.
Establishing data integrity with transient-key timestamps
In a transient-key system, the source of time must be a consistent standard understood by all senders and receivers. Since a local system clock may be changed by a user, it is never used as a source of time.Instead, data is digitally signed with a time value derived from Universal Coordinated Time (UTC) accurate to within a millisecond, in accordance with the ANSI ASC X9.95 standard for Trusted Timestamping
ANSI ASC X9.95 Standard
The ANSI X9.95 standard for trusted timestamps expands on the widely used by adding data-level security requirements that can ensure data integrity against a reliable time source that is provable to any third party...
.
Whenever a time interval in a transient-key system expires, a new public/private keypair is generated, and the private key from the previous interval is used to digitally certify the new public key. The old private key is then destroyed.
For the new interval, time values are obtained from a trusted third-party source, and specific moments in time can be interpolated in between received times by using a time-biasing method based on the internal system timer. If a trusted time source cannot be obtained or is not running within specified tolerances
Tolerance (engineering)
Engineering tolerance is the permissible limit or limits of variation in# a physical dimension,# a measured value or physical property of a material, manufactured object, system, or service,# other measured values ....
, transient private keys are not issued. In that case, the time interval chain is terminated, and a fresh one is begun. The old and new chains are connected through network archives, which enable all servers to continue to verify the data integrity
Data integrity
Data Integrity in its broadest meaning refers to the trustworthiness of system resources over their entire life cycle. In more analytic terms, it is "the representational faithfulness of information to the true state of the object that the information represents, where representational faithfulness...
through time of protected data, regardless of how often the chain must be restarted.
The start times of the chain and of each interval can be coupled together to form an unbroken sequence of public keys, which can be used for the following:
- To irrefutably identify the time at which a set of data was signed.
- To identify the exact state of the data at the time it was signed.
As an extra security measure, all requests for signatures made during an interval are stored in a log that is concatenated and is itself appended to the public key at the start of the next interval. This mechanism makes it impossible to insert new “signed events” into the interval chain after the fact.
Cross-verification
Through independently operating servers, cross-certification can provide third-party proof of the validity of a time interval chain and irrefutable evidence of consensus on the current time. A web of interconnected cross-certifying servers in a distributed environment creates a widely witnessed chain of trust that is as strong as its strongest link. By contrast, entire hierarchiesHierarchy
A hierarchy is an arrangement of items in which the items are represented as being "above," "below," or "at the same level as" one another...
of traditional public key systems can be compromised if a single private key is exposed.
An individual transient key interval chain can be cross-certified with other transient key chains and server instances. Through cross-certification, Server A signs Server B's interval chain, the signed data of which is the interval definition. In effect, the private keys from Server B are used to sign the public keys of Server A. In the diagram, a server instance is cross-certified with two other server instances (blue and orange).

Network archives
Along with intervals, cross-certifications are stored in a network archive. Within a transient-key network, the archiveArchive
An archive is a collection of historical records, or the physical place they are located. Archives contain primary source documents that have accumulated over the course of an individual or organization's lifetime, and are kept to show the function of an organization...
is a logical database
Database
A database is an organized collection of data for one or more purposes, usually in digital form. The data are typically organized to model relevant aspects of reality , in a way that supports processes requiring this information...
that can be stored and replicated on any system to enable verification of data that has been timestamped and signed by transient keys. A map of the set of accessible archives is stored within every digital signature created in the system. Whenever cross-certifications are completed at the beginning of an interval, the archive map is updated and published to all servers in the network.
Verification
During an interval, the transient private key is used to sign data concatenated with trusted timestamps and authenticity certificates. To verifyFile verification
File verification is the process of using an algorithm for verifying the integrity or authenticity of a computer file. This can be done by comparing two files bit-by-bit, but requires two copies of the same file, and may miss systematic corruptions which might occur to both files...
the data at a later time, a receiver accesses the persistent
Persistence (computer science)
Persistence in computer science refers to the characteristic of state that outlives the process that created it. Without this capability, state would only exist in RAM, and would be lost when this RAM loses power, such as a computer shutdown....
public key for the appropriate time interval. The public key applied to the digital signature can be passed through published cryptographic routines to unpack the hash
Cryptographic hash function
A cryptographic hash function is a deterministic procedure that takes an arbitrary block of data and returns a fixed-size bit string, the hash value, such that an accidental or intentional change to the data will change the hash value...
of the original data, which is then compared against a fresh hash of the stored data to verify data integrity. If the signature successfully decrypts using a particular interval’s published public key, the receiver can be assured that the signature originated during that time period. If the decrypted and fresh hashes match, the receiver can be assured that the data has not been tampered with since the transient private key created the timestamp and signed the data.
Transient-key cryptography was invented by Dr. Michael D. Doyle of Eolas Technologies Inc. and later acquired by and productized by ProofSpace, Inc. It is protected under US Patent #6,381,696 and has been included in the ANSI ASC X9.95 standard for Trusted Timestamping
ANSI ASC X9.95 Standard
The ANSI X9.95 standard for trusted timestamps expands on the widely used by adding data-level security requirements that can ensure data integrity against a reliable time source that is provable to any third party...
.
- ProofSpace, Inc has published a more detailed technical overview document of transient key cryptography.

