Singulation
Encyclopedia
Singulation is a method by which an RFID reader identifies a tag with a specific serial number
from a number of tags in its field. This is necessary because if multiple tags respond simultaneously to a query, they will jam
each other. In a typical commercial application, such as scanning a bag of groceries, potentially hundreds of tags might be within range of the reader.
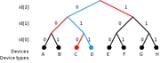
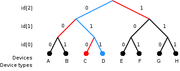 There are different methods of singulation, but the most common is "tree walking", which involves asking all tags with a serial number that starts with either a 1 or 0 to respond. If more than one responds, the reader might ask for all tags with a serial number that starts with 01 to respond, and then 010. It keeps doing this until it finds the tag it is looking for. Note that if the reader has some idea of what tags it wishes to interrogate, it can considerably optimise the search order. For example with some designs of tags, if a reader already suspects certain tags to be present then those tags can be instructed to remain silent, the tree walked without interference from them, and then finally they can be queried individually.
There are different methods of singulation, but the most common is "tree walking", which involves asking all tags with a serial number that starts with either a 1 or 0 to respond. If more than one responds, the reader might ask for all tags with a serial number that starts with 01 to respond, and then 010. It keeps doing this until it finds the tag it is looking for. Note that if the reader has some idea of what tags it wishes to interrogate, it can considerably optimise the search order. For example with some designs of tags, if a reader already suspects certain tags to be present then those tags can be instructed to remain silent, the tree walked without interference from them, and then finally they can be queried individually.
This simple protocol leaks considerable information, because anyone able to eavesdrop on the tag reader alone can determine all but the last bit
of a tag's serial number. Thus a tag can be (largely) identified so long as the reader's signal is receivable, which is usually possible at much greater distance than simply reading a tag directly. Because of privacy and security concerns related to this, the Auto-ID Labs
have developed two more advanced singulation protocols, called Class 0 UHF and Class 1 UHF, which are intended to be resistant to these sorts of attacks. These protocols, which are based on tree-walking but include other elements, have a performance of up to 1000 tags per second.
The tree walking protocol may be blocked or partially blocked by RSA Security
's blocker tags.
used by Ethernet
. These protocols are mainly used in HF tags. In ALOHA
, tags detect when a collision has occurred, and attempt to resend after waiting a random interval. The performance of such collide-and-resend protocols is approximately doubled if transmissions are synchronised to particular time-slots, and in this application time-slots for the tags are readily provided for by the reader. ALOHA does not leak information like the tree-walking protocol, and is much less vulnerable to blocker tags, which would need to be active devices with much higher power handling capabilities in order to work. However when the reader field is densely populated, ALOHA may make much less efficient use of available bandwidth than optimised versions of tree-walking. In the worst case, an ALOHA protocol network can reach a state of congestion collapse
. The Auto-ID consortium is attempting to standardise a version of an ALOHA protocol which it calls Class 0 HF. This has a performance of up to 200 tags per second.
is another variety offering better properties than the initial concept.
, elementary term explanation in RFID Tribe) as well as with concurrence of tags.
Serial number
A serial number is a unique number assigned for identification which varies from its successor or predecessor by a fixed discrete integer value...
from a number of tags in its field. This is necessary because if multiple tags respond simultaneously to a query, they will jam
Radio jamming
Radio jamming is the transmission of radio signals that disrupt communications by decreasing the signal to noise ratio. Unintentional jamming occurs when an operator transmits on a busy frequency without first checking whether it is in use, or without being able to hear stations using the frequency...
each other. In a typical commercial application, such as scanning a bag of groceries, potentially hundreds of tags might be within range of the reader.
Collision avoidance
Generally collision occurs when two entities require the identical resource; for example, two ships with crossing courses in a narrows. In wireless technology, collision occurs when two transmitters transmit at the same time with the same modulation scheme on the same frequency. In RFID technology, various strategies have been developed to overcome this dangerous situation.Tree walking

This simple protocol leaks considerable information, because anyone able to eavesdrop on the tag reader alone can determine all but the last bit
Bit
A bit is the basic unit of information in computing and telecommunications; it is the amount of information stored by a digital device or other physical system that exists in one of two possible distinct states...
of a tag's serial number. Thus a tag can be (largely) identified so long as the reader's signal is receivable, which is usually possible at much greater distance than simply reading a tag directly. Because of privacy and security concerns related to this, the Auto-ID Labs
Auto-ID Labs
The Auto-ID Labs network is a research group in the field of networked radio-frequency identification and emerging sensing technologies. The labs consist of seven research universities located on four different continents. These institutions were chosen by the former Auto-ID Center to design the...
have developed two more advanced singulation protocols, called Class 0 UHF and Class 1 UHF, which are intended to be resistant to these sorts of attacks. These protocols, which are based on tree-walking but include other elements, have a performance of up to 1000 tags per second.
The tree walking protocol may be blocked or partially blocked by RSA Security
RSA Security
RSA, the security division of EMC Corporation, is headquartered in Bedford, Massachusetts, United States, and maintains offices in Australia, Ireland, Israel, the United Kingdom, Singapore, India, China, Hong Kong and Japan....
's blocker tags.
ALOHA
The first offered singulation protocol is the ALOHA protocol, originally used decades ago in ALOHAnet and very similar to CSMA/CDCarrier sense multiple access with collision detection
Carrier sense multiple access with collision detection is a Media Access Control method in which:*a carrier sensing scheme is used....
used by Ethernet
Ethernet
Ethernet is a family of computer networking technologies for local area networks commercially introduced in 1980. Standardized in IEEE 802.3, Ethernet has largely replaced competing wired LAN technologies....
. These protocols are mainly used in HF tags. In ALOHA
Aloha
Aloha in the Hawaiian language means affection, peace, compassion and mercy. Since the middle of the 19th century, it also has come to be used as an English greeting to say goodbye and hello...
, tags detect when a collision has occurred, and attempt to resend after waiting a random interval. The performance of such collide-and-resend protocols is approximately doubled if transmissions are synchronised to particular time-slots, and in this application time-slots for the tags are readily provided for by the reader. ALOHA does not leak information like the tree-walking protocol, and is much less vulnerable to blocker tags, which would need to be active devices with much higher power handling capabilities in order to work. However when the reader field is densely populated, ALOHA may make much less efficient use of available bandwidth than optimised versions of tree-walking. In the worst case, an ALOHA protocol network can reach a state of congestion collapse
Network congestion
In data networking and queueing theory, network congestion occurs when a link or node is carrying so much data that its quality of service deteriorates. Typical effects include queueing delay, packet loss or the blocking of new connections...
. The Auto-ID consortium is attempting to standardise a version of an ALOHA protocol which it calls Class 0 HF. This has a performance of up to 200 tags per second.
Slotted Aloha
Slotted AlohaAloha
Aloha in the Hawaiian language means affection, peace, compassion and mercy. Since the middle of the 19th century, it also has come to be used as an English greeting to say goodbye and hello...
is another variety offering better properties than the initial concept.
Listen before talk
This concept is known from polite conversation. It applies as well to wireless communication, also named listen before send. With RFID it is applied for concurrence of readers (CSMACarrier Sense Multiple Access
Carrier Sense Multiple Access is a probabilistic Media Access Control protocol in which a node verifies the absence of other traffic before transmitting on a shared transmission medium, such as an electrical bus, or a band of the electromagnetic spectrum."Carrier Sense" describes the fact that a...
, elementary term explanation in RFID Tribe) as well as with concurrence of tags.

