
NuFW
Encyclopedia
NuFW is a GPL
extension to Netfilter (that is Linux firewall
). It adds authentication
to filtering rules. NuFW is also provided as a hardware firewall, in the EdenWall firewalling appliance.
NuFW can :
can easily be spoofed
. It thus uses
its own algorithm to perform authentication. It depends on two subsystems: Nufw which is connected to Netfilter and Nuauth
which is connected to clients and Nufw.
The algorithm is the following:
This algorithm realizes an A Posteriori authentication of the connection. As there is no time-based association, this ensures the identity of the user who sent the packet.
NuFW is the only real Authentication firewall, as it never associates a user with his machine.
Awards
External links
GNU General Public License
The GNU General Public License is the most widely used free software license, originally written by Richard Stallman for the GNU Project....
extension to Netfilter (that is Linux firewall
Firewall (computing)
A firewall is a device or set of devices designed to permit or deny network transmissions based upon a set of rules and is frequently used to protect networks from unauthorized access while permitting legitimate communications to pass....
). It adds authentication
Authentication
Authentication is the act of confirming the truth of an attribute of a datum or entity...
to filtering rules. NuFW is also provided as a hardware firewall, in the EdenWall firewalling appliance.
Introduction
NuFW is an extension of Netfilter which brings the notion of user to IP filtering.NuFW can :
- Authenticate any connection that goes through your gateway or only from/to a chosen subset or a specific protocol (iptables is used to select the connections to authenticate).
- Perform accounting, routingRoutingRouting is the process of selecting paths in a network along which to send network traffic. Routing is performed for many kinds of networks, including the telephone network , electronic data networks , and transportation networks...
and Quality of serviceQuality of serviceThe quality of service refers to several related aspects of telephony and computer networks that allow the transport of traffic with special requirements...
(QOS) based on users and not simply on IPs. - Filter packets with criteria such as application and OS used by distant users.
- Be the key of a secure and simple Single Sign On system.
Principles
NuFW refuses the idea of IP user as an IP addressIP address
An Internet Protocol address is a numerical label assigned to each device participating in a computer network that uses the Internet Protocol for communication. An IP address serves two principal functions: host or network interface identification and location addressing...
can easily be spoofed
Spoofing attack
In the context of network security, a spoofing attack is a situation in which one person or program successfully masquerades as another by falsifying data and thereby gaining an illegitimate advantage.- Spoofing and TCP/IP :...
. It thus uses
its own algorithm to perform authentication. It depends on two subsystems: Nufw which is connected to Netfilter and Nuauth
which is connected to clients and Nufw.
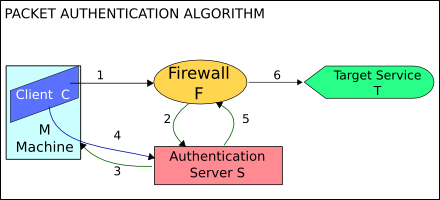
The algorithm is the following:

- A standard application sends a packet.
- The Nufw client sees that a connection is being initiated and sends a user request packet.
- The Nufw server queues the packet and sends an auth request packet to the Nuauth server.
- The Nuauth server sums the auth request and the user request packet and checks this against an authentication authority.
- The Nuauth server sends answer back to the Nufw server
- The Nufw server transmits the packet following the answer given to its request.
This algorithm realizes an A Posteriori authentication of the connection. As there is no time-based association, this ensures the identity of the user who sent the packet.
NuFW is the only real Authentication firewall, as it never associates a user with his machine.
Awards
- 2007 : Lutèce d'Or (Paris, France), Best Innovation
- 2005 : Les Trophées du LibreLes Trophées du LibreLes Trophées du Libre contest is a free software contest whose goal is to promote innovative software projects and give these projects recognition and media coverage - recently also to motivate students and academic institutions with special prizes. The competition is international and it is...
(Soissons, France), Security
External linksLes Trophées du Libre
Les Trophées du Libre contest is a free software contest whose goal is to promote innovative software projects and give these projects recognition and media coverage - recently also to motivate students and academic institutions with special prizes. The competition is international and it is...
(Soissons, France), Security
- NuFW website
- Netfilter website
- NuApplet - Qt client for NuFW

