Trivial File Transfer Protocol
Encyclopedia
Trivial File Transfer Protocol (TFTP) is a file
transfer protocol known for its simplicity. It is generally used for
automated transfer of configuration or boot files between machines in a local environment.
Compared to FTP
, TFTP is extremely limited, providing
no authentication, and is rarely used interactively by a user.
Due to its simple design, TFTP could be implemented using a very small amount of memory
.
It is therefore useful for booting
computers such as routers which may not have any data storage device
s.
It is an element of the Preboot Execution Environment
(PXE) network boot protocol,
where it is implemented in the firmware BIOS of the host's network card.
It is also used to transfer small amounts of data between hosts on a network
, such as IP phone
firmware or operating system images when a remote X Window System
terminal
or any other thin client
boots from a network host or server
. The initial stages of some network based installation systems (such as Solaris Jumpstart
, Red Hat Kickstart
, Symantec Ghost and Windows NT
's Remote Installation Services
) use TFTP to load a basic kernel that performs the actual installation.
TFTP was first defined in 1980 by IEN
133.
It is currently defined by RFC 1350.
There have been some extensions to the TFTP protocol documented in later
RFC's (see the section on Extensions, below).
TFTP is based in part on the earlier protocol EFTP
, which was part of the PUP
protocol suite.
TFTP support appeared first as part of 4.3 BSD.
Due to the lack of security, it is dangerous to use it over the Internet. Thus, TFTP is generally only used on private, local networks.
(UDP) using port number 69. TFTP is designed to be small and easy to implement, therefore, lacks most of the features of a regular FTP. TFTP only reads and writes files (or mail) from/to a remote server. It cannot list directories, and currently has no provisions for user authentication.
In TFTP, any transfer begins with a request to read or write a file, which also serves to request a connection. If the server grants the request, the connection is opened and the file is sent in fixed length blocks of 512 bytes. Each data packet contains one block of data, and must be acknowledged by an acknowledgment packet before the next packet can be sent. A data packet of less than 512 bytes signals termination of a transfer. If a packet gets lost in the network, the intended recipient will timeout and may retransmit his last packet (which may be data or an acknowledgment), thus causing the sender of the lost packet to retransmit that lost packet. The sender has to keep just one packet on hand for retransmission, since the lock step acknowledgment guarantees that all older packets have been received. Notice that both machines involved in a transfer are considered senders and receivers. One sends data and receives acknowledgments, the other sends acknowledgments and receives data.
TFTP typically uses UDP
as its transport protocol
, but it is not a requirement. Data transfer is initiated on port 69, but the data transfer ports are chosen independently by the sender and receiver during initialization of the connection. The ports are chosen at random according to the parameters of the
networking stack, typically from the range of Ephemeral ports.
TFTP defines three modes of transfer:
netascii, octet, and mail. Netascii is a modified form of ASCII
,
defined in RFC 764. It consists of an 8-bit extension of the 7-bit ASCII character
space from 0x20 to 0x7F (the printable characters and the space)
and eight of the control characters.
The allowed control characters include the null (0x00),
the line feed (LF, 0x0A), and the carriage return (CR, 0x0D).
Netascii also requires that the end of line marker on a host be translated
to the character pair CR LF for transmission, and that any CR must be followed
by either a LF or the null.
Octet allows for the transfer of arbitrary 8-bit bytes, with the
received file identical to the sent file. More correctly, if a host
receives an octet file and then returns it, the returned file must be identical
to the original.
The Mail transfer mode uses Netascii transfer, but the file is
sent to an email recipient by specifying that recipient's email address
as the file name. RFC 1350 declared this mode of transfer obsolete.
No security or authentication is provided by the protocol specification.
Unix implementations often restrict file transfers to a single configured
directory, and only to read from files with world readability, and only
write to already existing files that have world writeability.

tftp-hpa: An opensource TFTP host published under BSD license.
atftp: a GPL client/server implementation of the TFTP protocol for Linux
tftp-server: a GPL, multi-threaded TFTP server for Linux
TFTP Server: TFTP server for Mac OS X
Tftpd32: an opensource (EUPL
) IPv6
ready TFTP and DHCP
server/service
for Windows
haneWIN DHCP: a shareware
TFTP and DHCP
server/service
for Windows
Computer file
A computer file is a block of arbitrary information, or resource for storing information, which is available to a computer program and is usually based on some kind of durable storage. A file is durable in the sense that it remains available for programs to use after the current program has finished...
transfer protocol known for its simplicity. It is generally used for
automated transfer of configuration or boot files between machines in a local environment.
Compared to FTP
File Transfer Protocol
File Transfer Protocol is a standard network protocol used to transfer files from one host to another host over a TCP-based network, such as the Internet. FTP is built on a client-server architecture and utilizes separate control and data connections between the client and server...
, TFTP is extremely limited, providing
no authentication, and is rarely used interactively by a user.
Due to its simple design, TFTP could be implemented using a very small amount of memory
Computer memory
In computing, memory refers to the physical devices used to store programs or data on a temporary or permanent basis for use in a computer or other digital electronic device. The term primary memory is used for the information in physical systems which are fast In computing, memory refers to the...
.
It is therefore useful for booting
Network booting
Network booting is the process of booting a computer from a network rather than a local drive. This method of booting can be used by routers, diskless workstations and centrally managed computers such as public computers at libraries and schools...
computers such as routers which may not have any data storage device
Data storage device
thumb|200px|right|A reel-to-reel tape recorder .The magnetic tape is a data storage medium. The recorder is data storage equipment using a portable medium to store the data....
s.
It is an element of the Preboot Execution Environment
Preboot Execution Environment
The Preboot eXecution Environment is an environment to boot computers using a network interface independently of data storage devices or installed operating systems.PXE was introduced as part of the Wired for Management framework by Intel and is described in the specification The Preboot...
(PXE) network boot protocol,
where it is implemented in the firmware BIOS of the host's network card.
It is also used to transfer small amounts of data between hosts on a network
Computer network
A computer network, often simply referred to as a network, is a collection of hardware components and computers interconnected by communication channels that allow sharing of resources and information....
, such as IP phone
IP Phone
A VoIP phone uses voice over IP technologies allowing telephone calls to be made over an IP network such as the Internet instead of the ordinary PSTN system. Calls can traverse the Internet, or a private IP network such as that of a company...
firmware or operating system images when a remote X Window System
X Window System
The X window system is a computer software system and network protocol that provides a basis for graphical user interfaces and rich input device capability for networked computers...
terminal
Computer terminal
A computer terminal is an electronic or electromechanical hardware device that is used for entering data into, and displaying data from, a computer or a computing system...
or any other thin client
Thin client
A thin client is a computer or a computer program which depends heavily on some other computer to fulfill its traditional computational roles. This stands in contrast to the traditional fat client, a computer designed to take on these roles by itself...
boots from a network host or server
Server (computing)
In the context of client-server architecture, a server is a computer program running to serve the requests of other programs, the "clients". Thus, the "server" performs some computational task on behalf of "clients"...
. The initial stages of some network based installation systems (such as Solaris Jumpstart
Jumpstart (Solaris)
Jumpstart is a computer network installation tool set used by the Solaris operating system.- Usage :Jumpstart is used to manage operating system installation in many Information technology environments where Solaris operating system computers are widely used...
, Red Hat Kickstart
Kickstart (Linux)
The Red Hat Kickstart installation method is used primarily by the Red Hat Enterprise Linux operating system to automatically perform unattended operating system installation and configuration...
, Symantec Ghost and Windows NT
Windows NT
Windows NT is a family of operating systems produced by Microsoft, the first version of which was released in July 1993. It was a powerful high-level-language-based, processor-independent, multiprocessing, multiuser operating system with features comparable to Unix. It was intended to complement...
's Remote Installation Services
Remote Installation Services
RIS, Remote Installation Services is a Microsoft-supplied server that allows PXE BIOS-enabled computers to remotely execute boot environment variables.-Background:...
) use TFTP to load a basic kernel that performs the actual installation.
TFTP was first defined in 1980 by IEN
Internet Experiment Note
An Internet Experiment Note is a sequentially numbered document in a series of technical publications issued by the participants of the early development work groups that created the precursors of the modern Internet....
133.
It is currently defined by RFC 1350.
There have been some extensions to the TFTP protocol documented in later
RFC's (see the section on Extensions, below).
TFTP is based in part on the earlier protocol EFTP
EFTP
EFTP was a very simple file transfer protocol developed as part of the PUP protocol suite at Xerox PARC in the late 1970s...
, which was part of the PUP
PARC Universal Packet
The PARC Universal Packet was one of the two earliest internetwork protocol suites; it was created by researchers at Xerox PARC in the mid-1970s...
protocol suite.
TFTP support appeared first as part of 4.3 BSD.
Due to the lack of security, it is dangerous to use it over the Internet. Thus, TFTP is generally only used on private, local networks.
Overview
Trivial File Transfer Protocol (TFTP) is a simple protocol to transfer files. It has been implemented on top of the User Datagram ProtocolUser Datagram Protocol
The User Datagram Protocol is one of the core members of the Internet Protocol Suite, the set of network protocols used for the Internet. With UDP, computer applications can send messages, in this case referred to as datagrams, to other hosts on an Internet Protocol network without requiring...
(UDP) using port number 69. TFTP is designed to be small and easy to implement, therefore, lacks most of the features of a regular FTP. TFTP only reads and writes files (or mail) from/to a remote server. It cannot list directories, and currently has no provisions for user authentication.
In TFTP, any transfer begins with a request to read or write a file, which also serves to request a connection. If the server grants the request, the connection is opened and the file is sent in fixed length blocks of 512 bytes. Each data packet contains one block of data, and must be acknowledged by an acknowledgment packet before the next packet can be sent. A data packet of less than 512 bytes signals termination of a transfer. If a packet gets lost in the network, the intended recipient will timeout and may retransmit his last packet (which may be data or an acknowledgment), thus causing the sender of the lost packet to retransmit that lost packet. The sender has to keep just one packet on hand for retransmission, since the lock step acknowledgment guarantees that all older packets have been received. Notice that both machines involved in a transfer are considered senders and receivers. One sends data and receives acknowledgments, the other sends acknowledgments and receives data.
TFTP typically uses UDP
User Datagram Protocol
The User Datagram Protocol is one of the core members of the Internet Protocol Suite, the set of network protocols used for the Internet. With UDP, computer applications can send messages, in this case referred to as datagrams, to other hosts on an Internet Protocol network without requiring...
as its transport protocol
Transport layer
In computer networking, the transport layer or layer 4 provides end-to-end communication services for applications within a layered architecture of network components and protocols...
, but it is not a requirement. Data transfer is initiated on port 69, but the data transfer ports are chosen independently by the sender and receiver during initialization of the connection. The ports are chosen at random according to the parameters of the
networking stack, typically from the range of Ephemeral ports.
TFTP defines three modes of transfer:
netascii, octet, and mail. Netascii is a modified form of ASCII
ASCII
The American Standard Code for Information Interchange is a character-encoding scheme based on the ordering of the English alphabet. ASCII codes represent text in computers, communications equipment, and other devices that use text...
,
defined in RFC 764. It consists of an 8-bit extension of the 7-bit ASCII character
space from 0x20 to 0x7F (the printable characters and the space)
and eight of the control characters.
The allowed control characters include the null (0x00),
the line feed (LF, 0x0A), and the carriage return (CR, 0x0D).
Netascii also requires that the end of line marker on a host be translated
to the character pair CR LF for transmission, and that any CR must be followed
by either a LF or the null.
Octet allows for the transfer of arbitrary 8-bit bytes, with the
received file identical to the sent file. More correctly, if a host
receives an octet file and then returns it, the returned file must be identical
to the original.
The Mail transfer mode uses Netascii transfer, but the file is
sent to an email recipient by specifying that recipient's email address
as the file name. RFC 1350 declared this mode of transfer obsolete.
No security or authentication is provided by the protocol specification.
Unix implementations often restrict file transfers to a single configured
directory, and only to read from files with world readability, and only
write to already existing files that have world writeability.
Protocol walkthrough






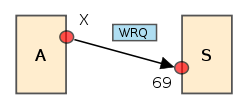
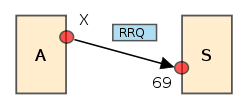
- The initiating host A sends an RRQ (read request) or WRQ (write request) packet to host S at the well-known port number 69, containing the filename and transfer mode.
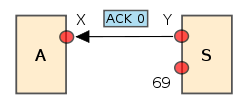
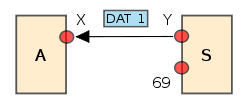
- S replies with an ACK (acknowledgement) packet to WRQ and directly with a DATA packet to RRQ. Packet is sent from a freshly allocated ephemeral portEphemeral portAn ephemeral port is a short-lived transport protocol port for Internet Protocol communications allocated automatically from a predefined range by the TCP/IP software...
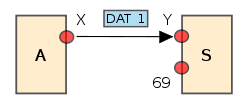
, and all future packets to host S should be to this port. - The source host sends numbered DATA packets to the destination host, all but the last containing a full-sized block of data (512 bytes). The destination host replies with numbered ACK packets for all DATA packets.
- The final DATA packet must contain less than a full-sized block of data to signal that it is the last. If the size of the transferred file is an exact multiple of the block-size, the source sends a final DATA packet containing 0 bytes of data.
- Receiver responds to each DATA with associated numbered ACK. Sender responds to the first received ACK of a block with DATA of the next block.
- If an ACK is not eventually received, a retransmit timer resends DATA packet.
Additional Details
- The original versions of TFTP, prior to RFC 1350, displayed a particularly bad protocol flaw which was named Sorcerer's Apprentice SyndromeSorcerer's Apprentice SyndromeSorcerer's Apprentice Syndrome is a particularly bad network protocol flaw, discovered in the original versions of TFTP. It was named after the "Sorcerer's Apprentice" segment of the animated film Fantasia, because the details of its operation closely resemble the disaster that befalls the...
(after the "Sorcerer's Apprentice" segment of FantasiaFantasia (film)Fantasia is a 1940 American animated film produced by Walt Disney and released by Walt Disney Productions. The third feature in the Walt Disney Animated Classics series, the film consists of eight animated segments set to pieces of classical music conducted by Leopold Stokowski, seven of which are...
) when it was discovered. - In the early days of work on the TCP/IP protocol suite, TFTP was often the first protocol implemented on a new host type, because it was so simple.
Extensions
- The original protocol has a file size limit of 32 MB. In 1998 this limit was extended to 4 GB by RFC 2347 which introduced option negotiation and RFC 2348 which introduced block-size negotiation. If the server and client support block number wraparound, file size is essentially unlimited.
- Since TFTP utilizes UDP, it has to supply its own transport and session support. Each file transferred via TFTP constitutes an independent exchange. Classically, this transfer is performed in lock-step, with only one packet (either a block of data, or an 'acknowledgement') ever in flight on the network at any time. Due to this lack of windowing, TFTP provides low throughputThroughputIn communication networks, such as Ethernet or packet radio, throughput or network throughput is the average rate of successful message delivery over a communication channel. This data may be delivered over a physical or logical link, or pass through a certain network node...
over high latencyLatency (engineering)Latency is a measure of time delay experienced in a system, the precise definition of which depends on the system and the time being measured. Latencies may have different meaning in different contexts.-Packet-switched networks:...
links. Note that Windows 2008 introduced pipelined TFTP as part of Windows Deployment Services (WDS) and uses an 8 packet window by default. This dramatically improves performance for things like PXEPreboot Execution EnvironmentThe Preboot eXecution Environment is an environment to boot computers using a network interface independently of data storage devices or installed operating systems.PXE was introduced as part of the Wired for Management framework by Intel and is described in the specification The Preboot...
booting.
Known TFTP hosts
GNU inetutils: the GNU project network suite includes a TFTP client/server implementationtftp-hpa: An opensource TFTP host published under BSD license.
atftp: a GPL client/server implementation of the TFTP protocol for Linux
Linux
Linux is a Unix-like computer operating system assembled under the model of free and open source software development and distribution. The defining component of any Linux system is the Linux kernel, an operating system kernel first released October 5, 1991 by Linus Torvalds...
tftp-server: a GPL, multi-threaded TFTP server for Linux
Linux
Linux is a Unix-like computer operating system assembled under the model of free and open source software development and distribution. The defining component of any Linux system is the Linux kernel, an operating system kernel first released October 5, 1991 by Linus Torvalds...
TFTP Server: TFTP server for Mac OS X
Mac OS X
Mac OS X is a series of Unix-based operating systems and graphical user interfaces developed, marketed, and sold by Apple Inc. Since 2002, has been included with all new Macintosh computer systems...
Tftpd32: an opensource (EUPL
European Union Public Licence
The European Union Public Licence is a software licence that has been created and approved by the European Commission. It is a free software licence.Its first version 1.0 was approved on 9 January 2007....
) IPv6
IPv6
Internet Protocol version 6 is a version of the Internet Protocol . It is designed to succeed the Internet Protocol version 4...
ready TFTP and DHCP
Dynamic Host Configuration Protocol
The Dynamic Host Configuration Protocol is a network configuration protocol for hosts on Internet Protocol networks. Computers that are connected to IP networks must be configured before they can communicate with other hosts. The most essential information needed is an IP address, and a default...
server/service
Windows Service
On Microsoft Windows operating systems, a Windows service is a long-running executable that performs specific functions and which is designed not to require user intervention. Windows services can be configured to start when the operating system is booted and run in the background as long as...
for Windows
Microsoft Windows
Microsoft Windows is a series of operating systems produced by Microsoft.Microsoft introduced an operating environment named Windows on November 20, 1985 as an add-on to MS-DOS in response to the growing interest in graphical user interfaces . Microsoft Windows came to dominate the world's personal...
haneWIN DHCP: a shareware
Shareware
The term shareware is a proprietary software that is provided to users without payment on a trial basis and is often limited by any combination of functionality, availability, or convenience. Shareware is often offered as a download from an Internet website or as a compact disc included with a...
TFTP and DHCP
Dynamic Host Configuration Protocol
The Dynamic Host Configuration Protocol is a network configuration protocol for hosts on Internet Protocol networks. Computers that are connected to IP networks must be configured before they can communicate with other hosts. The most essential information needed is an IP address, and a default...
server/service
Windows Service
On Microsoft Windows operating systems, a Windows service is a long-running executable that performs specific functions and which is designed not to require user intervention. Windows services can be configured to start when the operating system is booted and run in the background as long as...
for Windows
Microsoft Windows
Microsoft Windows is a series of operating systems produced by Microsoft.Microsoft introduced an operating environment named Windows on November 20, 1985 as an add-on to MS-DOS in response to the growing interest in graphical user interfaces . Microsoft Windows came to dominate the world's personal...
See also
- SSH file transfer protocolSSH file transfer protocolIn computing, the SSH File Transfer Protocol is a network protocol that provides file access, file transfer, and file management functionality over any reliable data stream...
- File Transfer ProtocolFile Transfer ProtocolFile Transfer Protocol is a standard network protocol used to transfer files from one host to another host over a TCP-based network, such as the Internet. FTP is built on a client-server architecture and utilizes separate control and data connections between the client and server...
- Simple File Transfer ProtocolSimple File Transfer ProtocolSimple File Transfer Protocol, as defined by RFC 913, was proposed as an file transfer protocol with a level of complexity intermediate between TFTP and FTP....
- List of TCP and UDP port numbers
Further reading
- RFC 906 – Bootstrap loading using TFTP, R. Finlayson, June 1984.
- RFC 1350 – TFTP Protocol (revision 2), K. R. Sollins, July 1992. (This superseded the preceding, RFC 783 and earlier FTP RFCs back to the original IENInternet Experiment NoteAn Internet Experiment Note is a sequentially numbered document in a series of technical publications issued by the participants of the early development work groups that created the precursors of the modern Internet....
133) - RFC 1785 – TFTP Option Negotiation Analysis, G. Malkin, A. Harkin, March 1995.
- RFC 2090 – TFTP Multicast Option, A. Emberson, February 1997. (Status: Experimental)
- RFC 2347 – TFTP Option Extension, G. Malkin, A. Harkin, May 1998. (This superseded the preceding, RFC 1782)
- RFC 2348 – TFTP Blocksize Option, G. Malkin, A. Harkin, May 1998. (This superseded the preceding, RFC 1783)
- RFC 2349 – TFTP Timeout Interval and Transfer Size Options, G. Malkin, A. Harkin, May 1998 (This superseded the preceding, RFC 1784).
- RFC 3617 – Uniform Resource Identifier (URI) Scheme and Applicability Statement for the Trivial File Transfer Protocol (TFTP), E. Lear, October 2003.

