
SIGABA
Encyclopedia
In the history of cryptography
, the ECM Mark II was a cipher machine used by the United States
for message encryption
from World War II
until the 1950s. The machine was also known as the SIGABA or Converter M-134 by the Army, or CSP-888/889 by the Navy, and a modified Navy version was termed the CSP-2900.
Like many machines of the era it used an electromechanical system of rotors
in order to encipher messages, but with a number of security improvements over previous designs. No successful cryptanalysis
of the machine during its service lifetime is publicly known.
) could be exploited by attackers. In the case of the famous Enigma machine
, these attacks were supposed to be upset by periodically moving the rotors to random locations, once for each new message. This, however, proved not to be random enough, and the Enigma was being broken with relative ease late in the war.
William Friedman, director of the US Army
's Signals Intelligence Service
, devised a system to correct for this attack by truly randomizing the motion of the rotors. His modification consisted of a paper tape reader from a teletype machine attached to a small device with metal "feelers" positioned to pass electricity through the holes. When a letter was pressed on the keyboard the signal would be sent through the rotors as it was in the Engima, producing an encrypted version. In addition, the current would also flow through the paper tape attachment, and any holes in the tape at its current location would cause the corresponding rotor to turn, and then advance the paper tape one position. In comparison, the Enigma rotated its rotors one position with each key press, a much less random movement. The resulting design went into limited production as the M-134, and its message settings included the position of the tape and the settings of a plugboard that indicated which line of holes on the tape controlled which rotors. However, there were problems using fragile paper tapes under field conditions.
 Friedman's associate, Frank Rowlett
Friedman's associate, Frank Rowlett
, then came up with a different way to advance the rotors, using another set of rotors. In Rowlett's design, each rotor must be constructed such that between one and four output signals were generated, advancing one or more of the rotors (rotors normally have one output for every input). There was little money for encryption development in the US before the war, so Friedman and Rowlett built a series of "add on" devices called the SIGGOO (or M-229) that were used with the existing M-134s in place of the paper tape reader. These were external boxes containing a three rotor setup in which five of the inputs were live, as if someone had pressed five keys at the same time on an Enigma, and the outputs were "gathered up" into five groups as well — that is all the letters from A to E would be wired together for instance. That way the five signals on the input side would be randomized through the rotors, and come out the far side with power in one of five lines. Now the movement of the rotors could be controlled with a day code, and the paper tape was eliminated. They referred to the combination of machines as the M-134-C.
In 1935 they showed their work to a US Navy cryptographer in OP-20-G
, Joseph Wenger
. He found little interest for it in the Navy until early 1937, when he showed it to Commander Laurance Safford
, Friedman's counterpart in the Navy's Office of Naval Intelligence. He immediately saw the potential of the machine, and he and Cmdr. Seiler then added a number of features to make the machine easier to build, resulting in the Electric Code Machine Mark II (or ECM Mark II), which the Navy then produced as the CSP-889 (or 888).
Oddly the Army was unaware of either the changes or the mass production of the system, but were "let in" on the secret in early 1940. In 1941 the Army and Navy joined in a joint cryptographic system, based on the machine. The Army then started using it as the SIGABA.
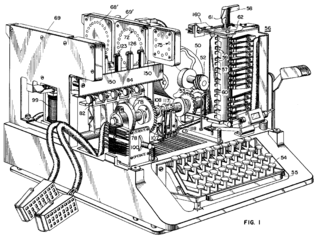
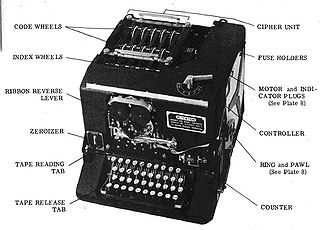 SIGABA was similar to the Enigma in basic theory, in that it used a series of rotors to encipher every character of the plaintext into a different character of ciphertext. Unlike Enigma's three rotors however, the SIGABA included fifteen, and did not use a reflecting rotor.
SIGABA was similar to the Enigma in basic theory, in that it used a series of rotors to encipher every character of the plaintext into a different character of ciphertext. Unlike Enigma's three rotors however, the SIGABA included fifteen, and did not use a reflecting rotor.
The SIGABA had three banks of five rotors each; the action of two of the banks controlled the stepping of the third.
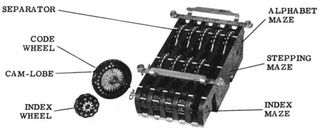 The SIGABA advanced one or more of its main rotors in a complex, pseudorandom fashion. This meant that attacks which could break other rotor machines with more simple stepping (for example, Enigma) were made much more complex. Even with the plaintext in hand, there are so many potential inputs to the encryption that it is difficult to work out the settings.
The SIGABA advanced one or more of its main rotors in a complex, pseudorandom fashion. This meant that attacks which could break other rotor machines with more simple stepping (for example, Enigma) were made much more complex. Even with the plaintext in hand, there are so many potential inputs to the encryption that it is difficult to work out the settings.
On the downside, the SIGABA was also large, heavy, expensive, difficult to operate, mechanically complex and fragile. It was nowhere near as practical a device as the Enigma, which was smaller and lighter than the radios it was used with. It found widespread use in the radio rooms of the US Navy's ships, but as a result of these practical problems the SIGABA simply couldn't be used in the field, and, in most theatres other systems were used instead, especially for tactical communications. The most famous may be the Navajo code talkers who provided tactical field communications in parts of the Pacific Theater beginning at Guadalcanal
. In other theatres, less secure, but smaller lighter and tougher machines were used, such as the M-209
. SIGABA, impressive as it was, was overkill for tactical communications.
. The common machine was known as the Combined Cipher Machine
(CCM), and was used from November 1943.
History of cryptography
The history of cryptography begins thousands of years ago. Until recent decades, it has been the story of what might be called classic cryptography — that is, of methods of encryption that use pen and paper, or perhaps simple mechanical aids...
, the ECM Mark II was a cipher machine used by the United States
United States
The United States of America is a federal constitutional republic comprising fifty states and a federal district...
for message encryption
Encryption
In cryptography, encryption is the process of transforming information using an algorithm to make it unreadable to anyone except those possessing special knowledge, usually referred to as a key. The result of the process is encrypted information...
from World War II
World War II
World War II, or the Second World War , was a global conflict lasting from 1939 to 1945, involving most of the world's nations—including all of the great powers—eventually forming two opposing military alliances: the Allies and the Axis...
until the 1950s. The machine was also known as the SIGABA or Converter M-134 by the Army, or CSP-888/889 by the Navy, and a modified Navy version was termed the CSP-2900.
Like many machines of the era it used an electromechanical system of rotors
Rotor machine
In cryptography, a rotor machine is an electro-mechanical device used for encrypting and decrypting secret messages. Rotor machines were the cryptographic state-of-the-art for a prominent period of history; they were in widespread use in the 1920s–1970s...
in order to encipher messages, but with a number of security improvements over previous designs. No successful cryptanalysis
Cryptanalysis
Cryptanalysis is the study of methods for obtaining the meaning of encrypted information, without access to the secret information that is normally required to do so. Typically, this involves knowing how the system works and finding a secret key...
of the machine during its service lifetime is publicly known.
History
It was clear to US cryptographers well before World War II that the single-stepping mechanical motion of rotor machines (e.g. the Hebern machineHebern rotor machine
The Hebern Rotor Machine was an electro-mechanical encryption machine built by combining the mechanical parts of a standard typewriter with the electrical parts of an electric typewriter, connecting the two through a scrambler...
) could be exploited by attackers. In the case of the famous Enigma machine
Enigma machine
An Enigma machine is any of a family of related electro-mechanical rotor cipher machines used for the encryption and decryption of secret messages. Enigma was invented by German engineer Arthur Scherbius at the end of World War I...
, these attacks were supposed to be upset by periodically moving the rotors to random locations, once for each new message. This, however, proved not to be random enough, and the Enigma was being broken with relative ease late in the war.
William Friedman, director of the US Army
United States Army
The United States Army is the main branch of the United States Armed Forces responsible for land-based military operations. It is the largest and oldest established branch of the U.S. military, and is one of seven U.S. uniformed services...
's Signals Intelligence Service
Signals Intelligence Service
The Signals Intelligence Service was the United States Army codebreaking division, headquartered at Arlington Hall. It was a part of the Signal Corps so secret that outside the office of the Chief Signal officer, it did not officially exist. William Friedman began the division with three "junior...
, devised a system to correct for this attack by truly randomizing the motion of the rotors. His modification consisted of a paper tape reader from a teletype machine attached to a small device with metal "feelers" positioned to pass electricity through the holes. When a letter was pressed on the keyboard the signal would be sent through the rotors as it was in the Engima, producing an encrypted version. In addition, the current would also flow through the paper tape attachment, and any holes in the tape at its current location would cause the corresponding rotor to turn, and then advance the paper tape one position. In comparison, the Enigma rotated its rotors one position with each key press, a much less random movement. The resulting design went into limited production as the M-134, and its message settings included the position of the tape and the settings of a plugboard that indicated which line of holes on the tape controlled which rotors. However, there were problems using fragile paper tapes under field conditions.

Frank Rowlett
Frank Byron Rowlett was an American cryptologist.Rowlett was born in Rose Hill, Virginia and attended Emory & Henry College in Emory, Virginia, where he was a member of the Beta Lambda Zeta fraternity. In 1929 he received a bachelor's degree in mathematics and chemistry...
, then came up with a different way to advance the rotors, using another set of rotors. In Rowlett's design, each rotor must be constructed such that between one and four output signals were generated, advancing one or more of the rotors (rotors normally have one output for every input). There was little money for encryption development in the US before the war, so Friedman and Rowlett built a series of "add on" devices called the SIGGOO (or M-229) that were used with the existing M-134s in place of the paper tape reader. These were external boxes containing a three rotor setup in which five of the inputs were live, as if someone had pressed five keys at the same time on an Enigma, and the outputs were "gathered up" into five groups as well — that is all the letters from A to E would be wired together for instance. That way the five signals on the input side would be randomized through the rotors, and come out the far side with power in one of five lines. Now the movement of the rotors could be controlled with a day code, and the paper tape was eliminated. They referred to the combination of machines as the M-134-C.
In 1935 they showed their work to a US Navy cryptographer in OP-20-G
OP-20-G
OP-20-G or "Office of Chief Of Naval Operations , 20th Division of the Office of Naval Communications, G Section / Communications Security", was the US Navy's signals intelligence and cryptanalysis group during World War II. Its mission was to intercept, decrypt, and analyze naval communications...
, Joseph Wenger
Joseph Wenger
Joseph Wenger was a Rear-Admiral of the United States Navy who served as the first Deputy Director of the Armed Forces Security Agency , and later as the first Vice Director of the National Security Agency, from December 1952 to November 1953, after the separate divisions of the AFSA merged into...
. He found little interest for it in the Navy until early 1937, when he showed it to Commander Laurance Safford
Laurance Safford
Captain Laurance F. Safford was a U.S. Navy cryptologist. He established the Naval cryptologic organization after World War I, and headed the effort more or less constantly until shortly after the Japanese attack on Pearl Harbor. His identification with the Naval effort was so close that he was...
, Friedman's counterpart in the Navy's Office of Naval Intelligence. He immediately saw the potential of the machine, and he and Cmdr. Seiler then added a number of features to make the machine easier to build, resulting in the Electric Code Machine Mark II (or ECM Mark II), which the Navy then produced as the CSP-889 (or 888).
Oddly the Army was unaware of either the changes or the mass production of the system, but were "let in" on the secret in early 1940. In 1941 the Army and Navy joined in a joint cryptographic system, based on the machine. The Army then started using it as the SIGABA.
Description

The SIGABA had three banks of five rotors each; the action of two of the banks controlled the stepping of the third.
- The main bank of five rotors was termed the cipher rotors, and each had 26 contacts. This acted similarly to other rotor machines, such as the Enigma; when a plaintext letter was input, a signal would enter one side of the bank and exit the other, denoting the ciphertext letter.
- The second bank of five rotors was termed the control rotors. These were also 26 contact-rotors. The control rotors received four signals at each step. After passing through the control rotors, the outputs were divided into ten groups of various sizes, ranging from 1–6 wires. Each group corresponded to an input wire for the next bank of rotors.
- The third bank of rotors was called the index rotors. These rotors were smaller with only ten contacts, and did not step during the encryption. After travelling though the index rotors, one to four of five output lines would have power. These then turned the cypher rotors.

On the downside, the SIGABA was also large, heavy, expensive, difficult to operate, mechanically complex and fragile. It was nowhere near as practical a device as the Enigma, which was smaller and lighter than the radios it was used with. It found widespread use in the radio rooms of the US Navy's ships, but as a result of these practical problems the SIGABA simply couldn't be used in the field, and, in most theatres other systems were used instead, especially for tactical communications. The most famous may be the Navajo code talkers who provided tactical field communications in parts of the Pacific Theater beginning at Guadalcanal
Guadalcanal
Guadalcanal is a tropical island in the South-Western Pacific. The largest island in the Solomons, it was discovered by the Spanish expedition of Alvaro de Mendaña in 1568...
. In other theatres, less secure, but smaller lighter and tougher machines were used, such as the M-209
M-209
In cryptography, the M-209, designated CSP-1500 by the Navy is a portable, mechanical cipher machine used by the US military primarily in World War II, though it remained in active use through the Korean War...
. SIGABA, impressive as it was, was overkill for tactical communications.
Combined cipher machine
SIGABA was also adapted for interoperation with a modified British machine, TypexTypex
In the history of cryptography, Typex machines were British cipher machines used from 1937. It was an adaptation of the commercial German Enigma with a number of enhancements that greatly increased its security....
. The common machine was known as the Combined Cipher Machine
Combined Cipher Machine
The Combined Cipher Machine was a common cipher machine system for securing Allied communications during World War II and for a few years after amongst NATO...
(CCM), and was used from November 1943.
See also
- MercuryMercury (cipher machine)Mercury was a British cipher machine used by the Air Ministry from 1950 until at least the early 1960s. Mercury was an online rotor machine descended from Typex, but modified to achieve a longer cycle length using a so-called double-drum basket system....
— British machine which also used rotors to control other rotors - SIGCUMSIGCUMSIGCUM, also known as Converter M-228, was a rotor cipher machine used to encrypt teleprinter traffic by the United States Army. Hastily designed by William Friedman and Frank Rowlett, the system was put into service in January 1943 before any rigorous analysis of its security had taken place...
— teleprinter encryption system which used SIGABA-style rotors
External links
- Electronic Cipher Machine (ECM) Mark II by Rich Pekelney
- SIGABA simulator for Windows
- Code Book Tool for the Sigaba Simulator (Windows 2000-XP)
- The ECM Mark II, also known as SIGABA, M-134-C, and CSP-889 — by John Savard
- Cryptanalysis of SIGABA], Michael Lee, University of California Santa Barbara Masters Thesis, 2003

