Ping
Encyclopedia
Ping is a computer network
administration utility used to test the reachability of a host
on an Internet Protocol
(IP) network and to measure the round-trip time for messages sent from the originating host to a destination computer. The name comes from active sonar terminology.
Ping operates by sending Internet Control Message Protocol
(ICMP) echo request packets to the target host and waiting for an ICMP response. In the process it measures the time from transmission to reception (round-trip time) and records any packet loss
. The results of the test are printed in the form of a statistical summary of the response packets received, including the minimum, maximum, and the mean
round-trip times, and sometimes the standard deviation
of the mean.
Ping may be run using various options (command line switches) depending on the implementation that enable special operational modes, such as to specify the packet size used as the probe, automatic repeated operation for sending a specified count of probes, time stamping options, or to perform a ping flood
. Flood pinging may be abused as a simple form of denial-of-service attack
, in which the attacker overwhelms the victim with ICMP echo request packets.
in December 1983 as a tool to troubleshoot problems in an IP network. He named it after the sound that sonar
makes, since its methodology is similar to sonar's echo location.
The usefulness of ping in assisting the diagnosis, of Internet connectivity issues was impaired starting in 2003, when a number of Internet service provider
s began filtering out ICMP Type 8 (ICMP Echo Request) messages at their network boundaries. This was partly due to the increasing use of ping for target reconnaissance, for example by Internet worms
such as Welchia that flood the Internet with ping requests in order to locate new computer
s to infect. Not only did the availability of ping responses leak information to an attacker, it added to the overall load on networks, causing problems for routers across the Internet.
However host discovery or ping scanning or ping sweep
is still a part of network scanning tools like nmap
, as it may give basic evidence about the existence of a remote machine.
Although RFC 1122 prescribes that any host must accept an echo-request and issue an echo-reply in return, this has been characterized as a security risk.
Generic composition of an ICMP packet
The utility summarizes its results after completing the ping probes. The shortest round trip time
was 80.393 ms, the average was 80.444 ms, and the maximum value was 80.521 ms. The measurement had a standard deviation
of 0.187 ms.
message whose data is expected to be received back in an echo reply ("ping"). The host must respond to all echo requests with an echo reply containing the exact data received in the request message.
Possible reply messages include
!H, !N, or !P (host, network or protocol unreachable)
!S (source route failed)
!F (fragmentation needed)
!U or !W (destination network/host unknown)
!I (source host is isolated)
!A (communication with destination network administratively prohibited)
!Z (communication with destination host administratively prohibited)
!Q (for this ToS the destination network is unreachable)
!T (for this ToS the destination host is unreachable)
!X (communication administratively prohibited)
!V (host precedence violation)
!C (precedence cutoff in effect)
! (ICMP unreachable code )
characters, as the output of the tcpdump
utility shows:
The payload includes a timestamp of when the message was sent, as well a sequence number. This allows ping to compute the round trip time in a stateless
manner without needing to record when packets were sent. In cases of no answer and no error message, most implementations of ping display nothing, or periodically print notifications about timing out.
(UDP) to a device located behind a network address translator (NAT) to keep the port binding on the NAT from timing out and removing the mapping. Other examples are short or empty instant message
s, emails, voice mails, or missed-call notification to indicate availability.
In various network multi-player games, a video game ping performs a similar function as the ping program for Internet traffic. The game server measures the time required for a game packet to reach a client and a response to be received. This round-trip time is usually reported as the player's ping. It is an effective measurement of the player's latency
, with lower ping times being desirable. This style of ping typically does not use ICMP packets.
Computer network
A computer network, often simply referred to as a network, is a collection of hardware components and computers interconnected by communication channels that allow sharing of resources and information....
administration utility used to test the reachability of a host
Host (network)
A network host is a computer connected to a computer network. A network host may offer information resources, services, and applications to users or other nodes on the network. A network host is a network node that is assigned a network layer host address....
on an Internet Protocol
Internet Protocol
The Internet Protocol is the principal communications protocol used for relaying datagrams across an internetwork using the Internet Protocol Suite...
(IP) network and to measure the round-trip time for messages sent from the originating host to a destination computer. The name comes from active sonar terminology.
Ping operates by sending Internet Control Message Protocol
Internet Control Message Protocol
The Internet Control Message Protocol is one of the core protocols of the Internet Protocol Suite. It is chiefly used by the operating systems of networked computers to send error messages indicating, for example, that a requested service is not available or that a host or router could not be...
(ICMP) echo request packets to the target host and waiting for an ICMP response. In the process it measures the time from transmission to reception (round-trip time) and records any packet loss
Packet loss
Packet loss occurs when one or more packets of data travelling across a computer network fail to reach their destination. Packet loss is distinguished as one of the three main error types encountered in digital communications; the other two being bit error and spurious packets caused due to noise.-...
. The results of the test are printed in the form of a statistical summary of the response packets received, including the minimum, maximum, and the mean
Average
In mathematics, an average, or central tendency of a data set is a measure of the "middle" value of the data set. Average is one form of central tendency. Not all central tendencies should be considered definitions of average....
round-trip times, and sometimes the standard deviation
Standard deviation
Standard deviation is a widely used measure of variability or diversity used in statistics and probability theory. It shows how much variation or "dispersion" there is from the average...
of the mean.
Ping may be run using various options (command line switches) depending on the implementation that enable special operational modes, such as to specify the packet size used as the probe, automatic repeated operation for sending a specified count of probes, time stamping options, or to perform a ping flood
Ping flood
A ping flood is a simple denial-of-service attack where the attacker/s overwhelms the victim with ICMP Echo Request packets. It is most successful if the attacker has more bandwidth than the victim...
. Flood pinging may be abused as a simple form of denial-of-service attack
Denial-of-service attack
A denial-of-service attack or distributed denial-of-service attack is an attempt to make a computer resource unavailable to its intended users...
, in which the attacker overwhelms the victim with ICMP echo request packets.
History
The ping utility was authored by Mike MuussMike Muuss
Michael John Muuss was the author of the freeware network tool Ping.A graduate of Johns Hopkins University, Muuss was a senior scientist specializing in geometric solid modeling, ray-tracing, MIMD architectures and digital computer networks at the United States Army Research Laboratory at Aberdeen...
in December 1983 as a tool to troubleshoot problems in an IP network. He named it after the sound that sonar
Sonar
Sonar is a technique that uses sound propagation to navigate, communicate with or detect other vessels...
makes, since its methodology is similar to sonar's echo location.
The usefulness of ping in assisting the diagnosis, of Internet connectivity issues was impaired starting in 2003, when a number of Internet service provider
Internet service provider
An Internet service provider is a company that provides access to the Internet. Access ISPs directly connect customers to the Internet using copper wires, wireless or fiber-optic connections. Hosting ISPs lease server space for smaller businesses and host other people servers...
s began filtering out ICMP Type 8 (ICMP Echo Request) messages at their network boundaries. This was partly due to the increasing use of ping for target reconnaissance, for example by Internet worms
Computer worm
A computer worm is a self-replicating malware computer program, which uses a computer network to send copies of itself to other nodes and it may do so without any user intervention. This is due to security shortcomings on the target computer. Unlike a computer virus, it does not need to attach...
such as Welchia that flood the Internet with ping requests in order to locate new computer
Computer
A computer is a programmable machine designed to sequentially and automatically carry out a sequence of arithmetic or logical operations. The particular sequence of operations can be changed readily, allowing the computer to solve more than one kind of problem...
s to infect. Not only did the availability of ping responses leak information to an attacker, it added to the overall load on networks, causing problems for routers across the Internet.
However host discovery or ping scanning or ping sweep
Ping sweep
In computing, a ping sweep is a method that can establish a range of IP addresses which map to live hosts.The classic tool used for ping sweeps is , which traditionally was accompanied by gping to generate the list of hosts for large subnets, although more recent version of fping include that...
is still a part of network scanning tools like nmap
Nmap
Nmap is a security scanner originally written by Gordon Lyon used to discover hosts and services on a computer network, thus creating a "map" ofthe network...
, as it may give basic evidence about the existence of a remote machine.
Although RFC 1122 prescribes that any host must accept an echo-request and issue an echo-reply in return, this has been characterized as a security risk.
ICMP packet
| Bit 0 - 7 | Bit 8 - 15 | Bit 16 - 23 | Bit 24 - 31 | |
|---|---|---|---|---|
| IP Header (20 bytes) |
Version/IHL | Type of service | Length | |
| Identification | flags and offset | |||
| Time To Live (TTL) | Protocol | Checksum | ||
| Source IP address | ||||
| Destination IP address | ||||
| ICMP Payload (8+ bytes) |
Type of message | Code | Checksum | |
| Quench | ||||
| Data (optional) | ||||
Generic composition of an ICMP packet
- Header (in blue):
- Protocol set to 1 and Type of Service set to 0.
- Payload (in red):
- Type of ICMP message (8 bits)
- Code (8 bits)
- Checksum (16 bits), calculated with the ICMP part of the packet (the header is not used). It is the 16-bit one's complement of the one's complement sum of the ICMP message starting with the Type field
- The ICMP 'Quench' (32 bits) field, which in this case (ICMP echo request and replies), will be composed of identifier (16 bits) and sequence number (16 bits).
- Data load for the different kind of answers (Can be an arbitrary length, left to implementation detail. However must be less than the maximum MTUMaximum transmission unitIn computer networking, the maximum transmission unit of a communications protocol of a layer is the size of the largest protocol data unit that the layer can pass onwards. MTU parameters usually appear in association with a communications interface...
of the network ).
- Data Transportation
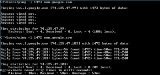
Sample ping test
The following is the output of running ping with the target www.example.com for five probes.
- ping -c 5 www.example.com
PING www.example.com (192.0.43.10) 56(84) bytes of data.
64 bytes from 43-10.any.icann.org (192.0.43.10): icmp_seq=1 ttl=250 time=80.5 ms
64 bytes from 43-10.any.icann.org (192.0.43.10): icmp_seq=2 ttl=250 time=80.4 ms
64 bytes from 43-10.any.icann.org (192.0.43.10): icmp_seq=3 ttl=250 time=80.3 ms
64 bytes from 43-10.any.icann.org (192.0.43.10): icmp_seq=4 ttl=250 time=80.3 ms
64 bytes from 43-10.any.icann.org (192.0.43.10): icmp_seq=5 ttl=250 time=80.4 ms
--- www.example.com ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 4006ms
rtt min/avg/max/mdev = 80.393/80.444/80.521/0.187 ms
The utility summarizes its results after completing the ping probes. The shortest round trip time
Round-trip delay time
In telecommunications, the round-trip delay time or round-trip time is the length of time it takes for a signal to be sent plus the length of time it takes for an acknowledgment of that signal to be received...
was 80.393 ms, the average was 80.444 ms, and the maximum value was 80.521 ms. The measurement had a standard deviation
Standard deviation
Standard deviation is a widely used measure of variability or diversity used in statistics and probability theory. It shows how much variation or "dispersion" there is from the average...
of 0.187 ms.
Echo request
The echo request is an ICMPInternet Control Message Protocol
The Internet Control Message Protocol is one of the core protocols of the Internet Protocol Suite. It is chiefly used by the operating systems of networked computers to send error messages indicating, for example, that a requested service is not available or that a host or router could not be...
message whose data is expected to be received back in an echo reply ("ping"). The host must respond to all echo requests with an echo reply containing the exact data received in the request message.
| 00 | 01 | 02 | 03 | 04 | 05 | 06 | 07 | 08 | 09 | 10 | 11 | 12 | 13 | 14 | 15 | 16 | 17 | 18 | 19 | 20 | 21 | 22 | 23 | 24 | 25 | 26 | 27 | 28 | 29 | 30 | 31 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Type = 8 | Code = 0 | Header Checksum | |||||||||||||||||||||||||||||
| Identifier | Sequence Number | ||||||||||||||||||||||||||||||
| Data ::: | |||||||||||||||||||||||||||||||
- The Identifier and Sequence Number can be used by the client to match the reply with the request that caused the reply. In practice, most Linux systems use a unique identifier for every ping process, and sequence number is an increasing number within that process. Windows uses a fixed identifier, which varies between Windows versions, and a sequence number that is only reset at boot time.
- The data received by the Echo Request must be entirely included in the Echo Reply.
Echo reply
The echo reply is an ICMP message generated in response to an echo request, and is mandatory for all hosts and routers.| 00 | 01 | 02 | 03 | 04 | 05 | 06 | 07 | 08 | 09 | 10 | 11 | 12 | 13 | 14 | 15 | 16 | 17 | 18 | 19 | 20 | 21 | 22 | 23 | 24 | 25 | 26 | 27 | 28 | 29 | 30 | 31 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Type = 0 | Code = 0 | Header Checksum | |||||||||||||||||||||||||||||
| Identifier | Sequence Number | ||||||||||||||||||||||||||||||
| Data ::: | |||||||||||||||||||||||||||||||
- Type and code must be set to 0.
- The identifier and sequence number can be used by the client to determine which echo requests are associated with the echo replies.
- The data received in the echo request must be entirely included in the echo reply.
Possible reply messages include
!H, !N, or !P (host, network or protocol unreachable)
!S (source route failed)
!F (fragmentation needed)
!U or !W (destination network/host unknown)
!I (source host is isolated)
!A (communication with destination network administratively prohibited)
!Z (communication with destination host administratively prohibited)
!Q (for this ToS the destination network is unreachable)
!T (for this ToS the destination host is unreachable)
!X (communication administratively prohibited)
!V (host precedence violation)
!C (precedence cutoff in effect)
!
Other replies
In case of error, destination host or intermediate router will send back an ICMP error message, i.e. host unreachable or TTL exceeded in transit. In addition these messages include the first 8 bytes of original message (in this case header of ICMP echo request, including quench value), so ping utility can match it to originating query.Payload
The payload of the packet is generally filled with ASCIIASCII
The American Standard Code for Information Interchange is a character-encoding scheme based on the ordering of the English alphabet. ASCII codes represent text in computers, communications equipment, and other devices that use text...
characters, as the output of the tcpdump
Tcpdump
tcpdump is a common packet analyzer that runs under the command line. It allows the user to intercept and display TCP/IP and other packets being transmitted or received over a network to which the computer is attached...
utility shows:
16:24:47.966461 IP (tos 0x0, ttl 128, id 15103, offset 0, flags [none],
proto: ICMP (1), length: 60) 192.168.146.22 > 192.168.144.5: ICMP echo request,
id 1, seq 38, length 40
0x0000: 4500 003c 3aff 0000 8001 5c55 c0a8 9216 E..<:.....\U....
0x0010: c0a8 9005 0800 4d35 0001 0026 6162 6364 ......M5...&abcd
0x0020: 6566 6768 696a 6b6c 6d6e 6f70 7172 7374 efghijklmnopqrst
0x0030: 7576 7761 6263 6465 6667 6869 uvwabcdefghi
The payload includes a timestamp of when the message was sent, as well a sequence number. This allows ping to compute the round trip time in a stateless
Stateless server
In computing, a stateless protocol is a communications protocol that treats each request as an independent transaction that is unrelated to any previous request so that the communication consists of independent pairs of requests and responses...
manner without needing to record when packets were sent. In cases of no answer and no error message, most implementations of ping display nothing, or periodically print notifications about timing out.
Other types of pinging
The term ping is commonly used to describe the transmission of any message or signal for the purpose of locating or testing network services or features. For example, a ping may be sent using the User Datagram ProtocolUser Datagram Protocol
The User Datagram Protocol is one of the core members of the Internet Protocol Suite, the set of network protocols used for the Internet. With UDP, computer applications can send messages, in this case referred to as datagrams, to other hosts on an Internet Protocol network without requiring...
(UDP) to a device located behind a network address translator (NAT) to keep the port binding on the NAT from timing out and removing the mapping. Other examples are short or empty instant message
Instant messaging
Instant Messaging is a form of real-time direct text-based chatting communication in push mode between two or more people using personal computers or other devices, along with shared clients. The user's text is conveyed over a network, such as the Internet...
s, emails, voice mails, or missed-call notification to indicate availability.
In various network multi-player games, a video game ping performs a similar function as the ping program for Internet traffic. The game server measures the time required for a game packet to reach a client and a response to be received. This round-trip time is usually reported as the player's ping. It is an effective measurement of the player's latency
Latency (engineering)
Latency is a measure of time delay experienced in a system, the precise definition of which depends on the system and the time being measured. Latencies may have different meaning in different contexts.-Packet-switched networks:...
, with lower ping times being desirable. This style of ping typically does not use ICMP packets.
See also
- KeepaliveKeepaliveA keepalive is a message sent by one device to another to check that the link between the two is operating, or to prevent this link from being broken.-Description:...
- List of DOS commands
- List of Unix utilities
- TracerouteTraceroutetraceroute is a computer network diagnostic tool for displaying the route and measuring transit delays of packets across an Internet Protocol network. Traceroute is available on most operating systems....
- Ping of deathPing of deathA ping of death is a type of attack on a computer that involves sending a malformed or otherwise malicious ping to a computer. A ping is normally 32 bytes in size ; historically, many computer systems could not handle a ping packet larger than the maximum IPv4 packet size, which is 65,535 bytes...
- Smurf attackSmurf attackThe Smurf attack is a way of generating significant computer network traffic on a victim network. This is a type of denial-of-service attack that floods a target system via spoofed broadcast ping messages....

