Onion routing
Encyclopedia
Onion routing is a technique for anonymous
communication over a computer network
. Messages are repeatedly encrypted and then sent through several network nodes called onion routers. Like someone unpeeling an onion
, each onion router removes a layer of encryption to uncover routing instructions, and sends the message to the next router where this is repeated. This prevents these intermediary nodes from knowing the origin, destination, and contents of the message.
Onion routing was developed by Michael G. Reed (formerly of Extreme Networks), Paul F. Syverson, and David M. Goldschlag, and patented by the United States Navy
in (1998). , Tor
is the predominant technology that employs onion routing.
Onion routing accomplishes this according to the principle of Chaum's mix cascades
: messages travel from source to destination via a sequence of proxies ("onion routers"), which re-route messages in an unpredictable path. To prevent an adversary from eavesdropping
on message content, messages are encrypted between routers. The advantage of onion routing (and mix cascades in general) is that it is not necessary to trust each cooperating router; if any router is compromised, anonymous communication can still be achieved. This is because each router in an OR network accepts messages, re-encrypts them, and transmits to another onion router. An attacker with the ability to monitor every onion router in a network might be able to trace the path of a message through the network, but an attacker with more limited capabilities will have difficulty even if he or she controls routers on the message's path.
Onion routing does not provide perfect sender or receiver anonymity against all possible eavesdroppers—that is, it is possible for a local eavesdropper to observe that an individual has sent or received a message. It does provide for a strong degree of unlinkability, the notion that an eavesdropper cannot easily determine both the sender and receiver of a given message. Even within these confines, onion routing does not provide any guarantee of privacy; rather, it provides a continuum in which the degree of privacy is generally a function of the number of participating routers versus the number of compromised or malicious routers.
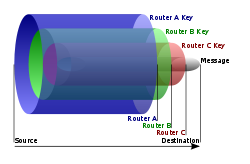 A routing onion (or just onion) is a data structure formed by 'wrapping' a plaintext message with successive layers of encryption, such that each layer can be 'unwrapped' (decrypted) like the layer of an onion by one intermediary in a succession of intermediaries, with the original plaintext message only being viewable by at most:
A routing onion (or just onion) is a data structure formed by 'wrapping' a plaintext message with successive layers of encryption, such that each layer can be 'unwrapped' (decrypted) like the layer of an onion by one intermediary in a succession of intermediaries, with the original plaintext message only being viewable by at most:
If there is end-to-end encryption between the sender and the recipient, then not even the last intermediary can view the original message; this is similar to a game of 'pass the parcel
'.
An intermediary is traditionally called a node or router.
To create and transmit an onion, the following steps are taken:
Using this approach means each node in the chain is ideally aware of only 2 other nodes:
The peeling away of each layer of the onion makes it difficult or impossible to track the onion without compromising a significant number of nodes.
To initiate a two-way conversation, a sender generates both an onion and a reply onion. The reply onion is transmitted to the last node of the chain, which then uses the reply onion to initiate the return chain for the recipient's response. Because the reply onion is multiply encrypted, it provides little information that might compromise the sender (an attacker must either break the public-key encryption or compromise all of the nodes in the return chain).
Security Symposium, Roger Dingledine, Nick Mathewson, and Paul Syverson presented Tor
, The Second-Generation Onion Router.
Tor is unencumbered by the original onion routing patents, because it uses telescoping circuits. Tor provides perfect forward secrecy
and moves protocol cleaning outside of the onion routing layer, making it a general purpose TCP
transport. It also provides low latency, directory servers, end-to-end integrity checking and variable exit policies for routers. Reply onions have been replaced by a rendezvous system, allowing hidden services and websites. The .onion
pseudo-top-level domain
is used for addresses in the Tor network.
The Tor source code is published under the BSD license. , there are about 2600 publicly accessible onion routers.
A decoy cypher can take the form of noise - sending copious messages of encrypted garbage plaintext. This decreases the signal-to-noise ratio for humans trying to interpret decrypted "plaintext" messages.
A decoy cypher can also take the form of misleading information - for example, in an onion cypher, most of the layers may contain information that when decrypted will produce a message that directly misleads the person reading it - often resulting in them taking actions against their interest - such as signalling that they are evesdropping by responding to a specific false signal, false flag attacks, or causing them to suspect the wrong parties. The actual message can still be contained at some level of the onion - but preferably not the lowest level - which may include an innocuous message so that if all layers are decrypted the core seems innocent. (see noise decoy cypher).
Anonymity
Anonymity is derived from the Greek word ἀνωνυμία, anonymia, meaning "without a name" or "namelessness". In colloquial use, anonymity typically refers to the state of an individual's personal identity, or personally identifiable information, being publicly unknown.There are many reasons why a...
communication over a computer network
Computer network
A computer network, often simply referred to as a network, is a collection of hardware components and computers interconnected by communication channels that allow sharing of resources and information....
. Messages are repeatedly encrypted and then sent through several network nodes called onion routers. Like someone unpeeling an onion
Onion
The onion , also known as the bulb onion, common onion and garden onion, is the most widely cultivated species of the genus Allium. The genus Allium also contains a number of other species variously referred to as onions and cultivated for food, such as the Japanese bunching onion The onion...
, each onion router removes a layer of encryption to uncover routing instructions, and sends the message to the next router where this is repeated. This prevents these intermediary nodes from knowing the origin, destination, and contents of the message.
Onion routing was developed by Michael G. Reed (formerly of Extreme Networks), Paul F. Syverson, and David M. Goldschlag, and patented by the United States Navy
United States Navy
The United States Navy is the naval warfare service branch of the United States Armed Forces and one of the seven uniformed services of the United States. The U.S. Navy is the largest in the world; its battle fleet tonnage is greater than that of the next 13 largest navies combined. The U.S...
in (1998). , Tor
Tor (anonymity network)
Tor is a system intended to enable online anonymity. Tor client software routes Internet traffic through a worldwide volunteer network of servers in order to conceal a user's location or usage from someone conducting network surveillance or traffic analysis...
is the predominant technology that employs onion routing.
Capabilities
The idea of onion routing (OR) is to protect the privacy of the sender and recipient of a message, while also providing protection for message content as it traverses a network.Onion routing accomplishes this according to the principle of Chaum's mix cascades
Mix network
Digital mixes were invented by David Chaum in 1981. Digital mixes create hard-to-trace communications by using a chain of proxy servers. Each message is encrypted to each proxy using public key cryptography; the resulting encryption is layered like a Russian doll with the message as the...
: messages travel from source to destination via a sequence of proxies ("onion routers"), which re-route messages in an unpredictable path. To prevent an adversary from eavesdropping
Eavesdropping
Eavesdropping is the act of secretly listening to the private conversation of others without their consent, as defined by Black's Law Dictionary...
on message content, messages are encrypted between routers. The advantage of onion routing (and mix cascades in general) is that it is not necessary to trust each cooperating router; if any router is compromised, anonymous communication can still be achieved. This is because each router in an OR network accepts messages, re-encrypts them, and transmits to another onion router. An attacker with the ability to monitor every onion router in a network might be able to trace the path of a message through the network, but an attacker with more limited capabilities will have difficulty even if he or she controls routers on the message's path.
Onion routing does not provide perfect sender or receiver anonymity against all possible eavesdroppers—that is, it is possible for a local eavesdropper to observe that an individual has sent or received a message. It does provide for a strong degree of unlinkability, the notion that an eavesdropper cannot easily determine both the sender and receiver of a given message. Even within these confines, onion routing does not provide any guarantee of privacy; rather, it provides a continuum in which the degree of privacy is generally a function of the number of participating routers versus the number of compromised or malicious routers.
Routing onions

- the sender
- the last intermediary
- the recipient
If there is end-to-end encryption between the sender and the recipient, then not even the last intermediary can view the original message; this is similar to a game of 'pass the parcel
Pass the parcel
Pass the parcel is a popular British children's party game in which a parcel is passed from person to person around a circle, somewhat similar in its logistics to musical chairs....
'.
An intermediary is traditionally called a node or router.
To create and transmit an onion, the following steps are taken:
- The sender picks nodes from a list provided by a special node called the directory node (traffic between the sender and the directory node may also be encrypted or otherwise anonymised or decentralised); the chosen nodes are ordered to provide a path through which the message may be transmitted; this ordering of the nodes is called a chain or a circuit.
- Using asymmetric key cryptography, the sender uses the public key of each chosen node to wrap the plaintext message in the necessary layers of encryption: The public keys are retrieved from an advertised list or by on-the-spot negotiation for temporary use, and the layers are applied in reverse order of the message's path from sender to receiver; with each layer, the client includes information for the corresponding node regarding the next node to which the onion should be transmitted.
- As the onion passes to each node in the chain, a layer of encryption is peeled away by the receiving node (using the private key that corresponds to the public key with which the layer was encrypted), and then the newly diminished onion is transmitted to the next node in the chain.
- The last node in the chain peels off the last layer and transmits the original message to the intended recipient.
Using this approach means each node in the chain is ideally aware of only 2 other nodes:
- the preceding node from which the onion was transmitted.
- the proceeding node to which the onion should next be transmitted.
The peeling away of each layer of the onion makes it difficult or impossible to track the onion without compromising a significant number of nodes.
Reply onions
Onion routing also includes a technique allowing recipients to send responses back to the sender without compromising the identity of either party. This is embodied in the concept of a reply onion, which is similar to a normal onion, except that a reply onion encodes a path from the receiver back to the sender of the normal onion.To initiate a two-way conversation, a sender generates both an onion and a reply onion. The reply onion is transmitted to the last node of the chain, which then uses the reply onion to initiate the return chain for the recipient's response. Because the reply onion is multiply encrypted, it provides little information that might compromise the sender (an attacker must either break the public-key encryption or compromise all of the nodes in the return chain).
Weaknesses
- Timing analysis: Incoming and outgoing messages passing through a relatively under-loaded node can be linked by observing how close together in time they are received and re-sent. However, this weakness can be overcome by buffering several messages and then transmitting them using a pseudorandom timing algorithm.
- Intersection attacks: Nodes periodically fail or leave the network; any chain that remains functioning cannot have been routed through either the nodes that left or the nodes that recently joined the network, increasing the chances of a successful traffic analysis.
- Predecessor attacks: A compromised node can keep track of a session as it occurs over multiple chain reformations (chains are periodically torn down and rebuilt). If the same session is observed over the course of enough reformations, the compromised node tends to connect with the particular sender more frequently than any [other] node, increasing the chances of a successful traffic analysis.
- Exit node sniffing: An exit node (the last node in a chain) has complete access to the content being transmitted from the sender to the recipient; Dan Egerstad, a Swedish researcher, used such an attack to collect the passwords of over 100 email accounts related to foreign embassies. However, this weakness can be overcome by employing end-to-end encryption (that is, encryption between the sender and the recipient), such as SSLTransport Layer SecurityTransport Layer Security and its predecessor, Secure Sockets Layer , are cryptographic protocols that provide communication security over the Internet...
.
Tor
On August 13, 2004 at the 13th USENIXUSENIX
-External links:* *...
Security Symposium, Roger Dingledine, Nick Mathewson, and Paul Syverson presented Tor
Tor (anonymity network)
Tor is a system intended to enable online anonymity. Tor client software routes Internet traffic through a worldwide volunteer network of servers in order to conceal a user's location or usage from someone conducting network surveillance or traffic analysis...
, The Second-Generation Onion Router.
Tor is unencumbered by the original onion routing patents, because it uses telescoping circuits. Tor provides perfect forward secrecy
Perfect forward secrecy
In an authenticated key-agreement protocol that uses public key cryptography, perfect forward secrecy is the property that ensures that a session key derived from a set of long-term public and private keys will not be compromised if one of the private keys is compromised in the future.Forward...
and moves protocol cleaning outside of the onion routing layer, making it a general purpose TCP
Transmission Control Protocol
The Transmission Control Protocol is one of the core protocols of the Internet Protocol Suite. TCP is one of the two original components of the suite, complementing the Internet Protocol , and therefore the entire suite is commonly referred to as TCP/IP...
transport. It also provides low latency, directory servers, end-to-end integrity checking and variable exit policies for routers. Reply onions have been replaced by a rendezvous system, allowing hidden services and websites. The .onion
.onion
.onion is a pseudo-top-level domain host suffix designating an anonymous hidden service reachable via the Tor network...
pseudo-top-level domain
Top-level domain
A top-level domain is one of the domains at the highest level in the hierarchical Domain Name System of the Internet. The top-level domain names are installed in the root zone of the name space. For all domains in lower levels, it is the last part of the domain name, that is, the last label of a...
is used for addresses in the Tor network.
The Tor source code is published under the BSD license. , there are about 2600 publicly accessible onion routers.
Decoy Cyphers
The weak link in decryption is the human in the loop. Human computation is slow and expensive. Whenever a cypher needs to be sent to a human for semantic processing, this substantially increases the cost of decryption.A decoy cypher can take the form of noise - sending copious messages of encrypted garbage plaintext. This decreases the signal-to-noise ratio for humans trying to interpret decrypted "plaintext" messages.
A decoy cypher can also take the form of misleading information - for example, in an onion cypher, most of the layers may contain information that when decrypted will produce a message that directly misleads the person reading it - often resulting in them taking actions against their interest - such as signalling that they are evesdropping by responding to a specific false signal, false flag attacks, or causing them to suspect the wrong parties. The actual message can still be contained at some level of the onion - but preferably not the lowest level - which may include an innocuous message so that if all layers are decrypted the core seems innocent. (see noise decoy cypher).
See also
- Garlic routingGarlic routingGarlic routing is a variant of onion routing that encrypts multiple messages together to make it more difficult for attackers to perform traffic analysis....
- Anonymous P2PAnonymous P2PAn anonymous P2P communication system is a peer-to-peer distributed application in which the nodes or participants are anonymous or pseudonymous...
- Tor (anonymity network)Tor (anonymity network)Tor is a system intended to enable online anonymity. Tor client software routes Internet traffic through a worldwide volunteer network of servers in order to conceal a user's location or usage from someone conducting network surveillance or traffic analysis...
- Degree of anonymityDegree of anonymityIn anonymity networks it is important to be able to measure quantitatively the guarantee that is given to the system. The degree of anonymity d is a device that was proposed at the 2002 Privacy Enhancing Technology conference...
- Chaum mixes
- BitblinderBitblinderBitblinder was an open source software program that allows users to share bandwidth and IP addresses in order to anonymously download torrents and browse the internet. It was first released in June 2009. It was developed by Josh Albrecht and Matthew Kaniaris of Innominet...
- Java Anon ProxyJava Anon ProxyJava Anon Proxy, also known as JAP or JonDonym, is a proxy system designed to allow browsing the Web with revocable pseudonymity. It was originally developed as part of a project of the Technische Universität Dresden, the Universität Regensburg and Privacy Commissioner of Schleswig-Holstein...
Further reading
- Email Security, Bruce SchneierBruce SchneierBruce Schneier is an American cryptographer, computer security specialist, and writer. He is the author of several books on general security topics, computer security and cryptography, and is the founder and chief technology officer of BT Managed Security Solutions, formerly Counterpane Internet...
(ISBN 0-471-05318-X) - Computer Privacy Handbook, Andre Bacard (ISBN 1-56609-171-3)
External links
- Onion Routing Publications
- Tor source code, design documents, and publications
- English Tor installation and setup guide for beginners under Windows XP

