
Norton AntiVirus
Encyclopedia
Norton AntiVirus, developed and distributed by Symantec Corporation
, provides malware
prevention and removal during a subscription period. It uses signatures and heuristics to identify viruses
. Other features include e-mail spam
filtering and phishing
protection.
Symantec distributes the product as a download, a box copy, and as OEM software. Norton AntiVirus and Norton Internet Security
, a related product, held a 61% US retail market share for security suites as of the first half of 2007. Competitors, in terms of market share in this study, include antivirus products from CA, Trend Micro
, and Kaspersky Lab
.
Norton AntiVirus runs on Microsoft Windows
and Mac OS X
. Windows 7 support is in development for versions 2006 through 2008. Version 2009 has Windows 7 supported update already. Versions 2010, 2011, and 2012 all natively support Windows 7, without needing an update. Version 12 is the only version fully compatible with Mac OS X Lion
.
(SAM). SAM 2.0, released March 1990, incorporated technology allowing users to easily update SAM to intercept and eliminate new viruses, including many that didn't exist at the time of the program's release.
In August 1990 Symantec acquired Peter Norton Computing
from Peter Norton
. Norton and his company developed various DOS
utilities
including the Norton Utilities
, which did not include antivirus features. Symantec continued the development of acquired technologies. The technologies are marketed under the name of "Norton", with the tagline
"from Symantec". Norton's crossed-arm pose, a registered U.S. trademark, was traditionally featured on Norton product packaging. However, his pose was later moved to the spine of the packaging, and eventually dropped altogether.
By early 1991, U.S. computers were invaded by hundreds of foreign virus strains and corporate PC infection was becoming a serious problem. Symantec's Norton Group launched Norton AntiVirus 1.0 (NAV) for PC and compatible computers. Ads for the product, with suggested retail $129, featured Norton in his crossed-arm pose, wearing a pink shirt and surgical mask covering his nose and mouth.
With the 1998 version 5.0 update, SAM was renamed Norton AntiVirus (NAV) for Macintosh.
was introduced in Norton AntiVirus 2004, addressing the estimated 3.6 million counterfeit Norton products sold. An alphanumeric
code is generated to identify a computer's configuration, which ties in with the product key. Users are allowed to activate their product five times with the same product key. Spyware
and adware
detection and removal was introduced to the 2005 version, with the tagline "Antispyware Edition". The tagline was dropped in later releases. However, Norton AntiVirus 2009 Classic does not include spyware or adware detection. The Classic edition is marketed alongside Norton AntiVirus 2009, which does include spyware and adware detection.
Existing users of the 2006, 2007, 2008 and 2009 versions can upgrade to the latest 2010 version without buying a new subscription. Upgrading will preserve the number of days left on a user's subscription.
aggregates information in a central user interface. CNET
reports the Norton Protection Center, while useful, attempts to advertise additional products. To further facilitate detection of zero-day malware, Bloodhound disassembles a variety of programming languages, and scans code for malicious instructions using predefined algorithms. Internet Explorer homepage hijacking
protection was introduced in this release as well; however notably missing is search engine
hijacking protection. CNET highlighted Norton AntiVirus 2006's noticeable impact on system performance.
Operating system requirements call for Windows 2000 Service Pack 3
or Windows XP. 150 MB of free space and a 300 MHz processor is required under either operating system. 128 MB of RAM is required under Windows 2000, while 256 MB is required in Windows XP.
compatibility was introduced in this release as well. Despite having about 80% of the code rewritten, CNET
reports mixed results in performance testing. New features include a tabbed interface, eliminating the need to have separate windows open for the Norton Protection Center and for configuring the settings. Symantec extended its Veritas
VxMS rootkit
detection technology, allowing Norton AntiVirus 2007 to inspect files within directories to files on the volume level, detecting abnormalities or inconsistencies.
Windows 2000 compatibility was dropped from this release. Compatibility with 32-bit versions of Windows Vista
was added to this release with a patch from Symantec. Hardware requirements under Vista call for 150 MB free space, a 800 MHz processor and 512 MB RAM. Requirements under Windows XP similarly call for 150 MB free space, a 300 MHz processor, and 256 MB of RAM.
, which looks for suspicious application behavior. This release adds real-time exploit
protection, preventing attackers from leveraging common browser and application vulnerabilities.
When installed in 32-bit versions of Windows XP Service Pack 2, 300 MB of free space, a 300 MHz processor, and 256 MB of RAM is required. When installed in 32-bit and 64-bit versions of Windows Vista, 300 MB of free space, a 800 MHz processor, and 256 MB of RAM is needed.
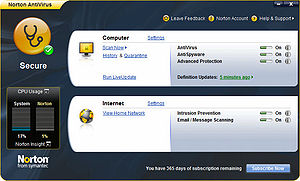 Norton AntiVirus 2009 was released on September 8, 2008. Addressing performance issues, over 300 changes were made, with a "zero-impact" goal. Benchmarking
Norton AntiVirus 2009 was released on September 8, 2008. Addressing performance issues, over 300 changes were made, with a "zero-impact" goal. Benchmarking
conducted by Passmark Software PTY LTD highlights its 47 second install time, 32 second scan time, and 5 MB memory utilization. It should be noted Symantec funded the benchmark test and provided some scripts used to benchmark each participating antivirus software
.
The security status and settings are now displayed in a single main interface. A CPU usage monitor displays the total CPU utilization and Norton's CPU usage in the main interface. Other features include Norton Insight
, a whitelisting technology which cuts scanning times by mapping known safe files using information from an online database. To address malware response times, updates are delivered updates 5 to 15 minutes. However, such updates are not tested by Symantec, and may cause false positives, or incorrectly identify files as malicious. The exploit scanner found in the 2007 and 2008 versions was dropped from this release.
When installed in 32-bit versions of Windows XP Service Pack 2, 150 MB of free space, a 300 MHz processor, and 256 MB of RAM is required. When installed in 32-bit or 64-bit versions of Windows Vista, 150 MB of free space, a 800 MHz processor, and 512 MB of RAM is required.
The Classic edition cannot find or remove adware
and spyware
.
, now dubbed SONAR 2. It now uses more information to determine if an application is truly malicious. Norton Insight
can present users with information about the origins, activities, and performance of applications along with reputation data. A new feature codenamed Autospy helps users understand what Norton did when malware was found. Previous releases removed threats on sight and quietly warned users, potentially confusing when users are deceived in downloading rogue security software. Much of this information is placed on the back of the main window; a toggle button switches between the sides.
Symantec has also added Windows 7 support. Aside from that, Symantec has also added the Norton Download Insight
to prevent drive by drive downloads.
also released an application that "scans" the user's Facebook
feed for any malware links. This application does not require a valid subscription. In a test sponsored by Symantec, Norton Internet Security 2011 was the only security suite to ever achieve a 100 percent protection score in a new third-party test from Dennis Labs. Improved reputation scan provides the user with an easy to understand interface on files stored on the user's computer. Marking them as trusted, good, poor, or bad. The final version of Norton Internet Security 2011 was released on August 31, 2010. New features in version 2011 also include Norton Rescue Tools. These tools include Norton Bootable Recovery tool and Norton Power Eraser.
On December 9, 2010, Symantec released the 18.5 version through Norton LiveUpdate
. However, this update was later pulled due to numerous reports on the Norton forums that the update is causing system instability and freeze ups during system scans (both full and quick scans). This issue only affect some customers. Users affected by this update are advised to uninstall the product, run the Norton Removal Tool, and reinstall the 18.1 version from http://www.norton.com/nis11. Norton later fixed the bugs and re-released the update.
Following the acquisition of VeriSign Security by Norton's parent company Symantec
, several of VeriSign's features were incorporated into the 2011 edition. The new product features a new Norton logo which uses the VeriSign checkmark formerly seen in VeriSign's own logo, as well as several new icon changes to the Norton Safe Web
and Norton Identity Safe features.
2.0, which not only monitor files for safety but also the stability of a given file. That means that If a file is stable on Windows 7, but unstable on Windows XP, XP users will be notified for the instability of the file.
Also, integration with specialised removal tools is added, for better cleanup of already infected systems. A new smaller and more effective version of Norton power eraser is launched to assist in removal of fake antivirus software and other deeply-embedded threats that are otherwise hard to remove. A new tool called Norton Management helps manage different computers and devices equipped with Norton software from a single location.
Another feature added with this release is Sonar 4
. Another welcome change is that identity Safe and Safe Web
are finally compatible with Google Chrome
and all the passwords and notes can be stored in the cloud should the user wishes.
The user interface is also simplified with only three buttons. The third button opens a more advanced and complicated UI, where the user is able to manage settings and access different product features. The CPU meter, a long-time supported and loved feature, that was removed from Norton 2011, also makes a return (only on the "advanced screen").
Combining the netbook and desktop line, Norton Internet Security intergrates Bandwidth metering, which controls product's traffic usage and takes it down to minimum if necessary. This is ideal for networks with limited traffic. Also, the user interface window adjust accordingly to the size of the computer screen.
This version of Norton Internet Security includes several easter eggs. Pressing Shift+1, 2, 3 or 4 would change the theme to default background (plain black), ray, animals, and floral respectively. Also holding CTRL + WinKey + Alt while pressing "performance buton
" to activate "Crazy Flip", which will make the window flip head over heels. The effect would continue until the main window is closed and reopened.
In addition scans are no-longer scheduled through the Windows Task Scheduler, but through the Symantec's more advanced one, which waits for the user to stop using the keyboard and mouse (e.g. leaves the PC) and then performs tasks.
platform, with the capability to detect both Macintosh and Windows
malware. Other features include a vulnerability scanner, which blocks attackers from leveraging software exploits. Norton AntiVirus 11 also includes the ability to scan within compressed or archived files, such as Time Capsule
volumes. Operating requirements call for Mac OS X Tiger. A PowerPC
or an Intel Core
processor, 128 MB of RAM, and 100 MB of free hard disk space are also required. Norton AntiVirus Dual Protection for Mac is intended for Macintosh users with Windows running on their systems, using Boot Camp or virtualization
software such as VMWare Fusion
. It provides a license for both Norton AntiVirus 11 with Norton AntiVirus 2009.
According to PassMark Security Benchmark 2012 Norton AntiVirus and Norton Internet Security are the lightest suites available. Av-comparatives.org also tested these products and give similar results.
PCMag recognises 2011 and 2012 lines as the fastest and strongest in protection.
PCWorld's tests of security software put Norton Internet Security 2009 on the 1-st place.
In 2011's test of PCWorld Norton Internet Security was the winner. Av-test.org certifies Norton, putting it on a second place after BitDefender. Kaspersky detected less, but then blocked more thoroughly. . Many other reputable sources like Dennis Technology Labs confirm the performance and effectivness of Norton 2011 and 2012 lines.
confirmed the active development of Magic Lantern
, a keylogger
intended to obtain passwords to encrypted e-mail and other documents during criminal investigations. Magic Lantern was first reported in the media by Bob Sullivan
of MSNBC
on 20 November 2001 and by Ted Bridis of the Associated Press
. The FBI intends to deploy Magic Lantern in the form of an e-mail attachment
. When the attachment is opened, it installs a trojan horse
on the suspect's computer, which is activated when the suspect uses PGP
encryption, often used to increase the security of sent e-mail messages. When activated, the trojan will log the PGP password, which allows the FBI to decrypt user communications. Symantec and other major antivirus vendors have whitelisted the Magic Lantern trojan, rendering their antivirus products, including Norton AntiVirus, incapable of detecting it. Concerns around this whitelisting include uncertainties about Magic Lantern's full surveillance potential and whether hackers could subvert it and redeploy it for purposes outside of law enforcement.
Graham Cluley, a technology consultant from Sophos
, said "We have no way of knowing if it was written by the FBI, and even if we did, we wouldn’t know whether it was being used by the FBI or if it had been commandeered by a third party". Another reaction came from Marc Maiffret, chief technology officer and cofounder of eEye Digital Security who states: "Our customers are paying us for a service, to protect them from all forms of malicious code. It is not up to us to do law enforcement's job for them so we do not, and will not, make any exceptions for law enforcement malware or other tools."
Proponents of Magic Lantern argue the technology would allow law enforcement to efficiently and quickly decrypt time-sensitive messages protected by encryption schemes. Implementing Magic Lantern does not require physical access to a suspect's computer, unlike Carnivore, a predecessor to Magic Lantern, since physical access to a computer would require a court order. FBI spokesman Paul Bresson, in response to a question about whether Magic Lantern also needed a court order to deploy, would only say "Like all technology projects or tools deployed by the FBI it would be used pursuant to the appropriate legal process."
Anti-virus update marked Spotify
as a Trojan Horse
disabling the software across millions of PCs.
http://aka-community.symantec.com/connect/forums/spotify-detected-trojan-horse
http://getsatisfaction.com/spotify/topics/spotify_defined_as_a_trojan_by_symantec
Another incident occurred in May 2007, when Norton Antivirus flagged components of the Pegasus
e-mail
client as malicious, rendering the program corrupted. Symantec customer service addressed the problem by running through a checklist of troubleshooting steps which were not always successful.
, which updates Norton-branded software, separately. The user must uninstall both Norton AntiVirus and the LiveUpdate component manually. The LiveUpdate component is purposely left behind to update other Norton-branded products, if present. In response, Symantec developed the Norton Removal Tool to remove leftover registry
keys and values along with files and folders. However, neither route of uninstallation will remove subscription data, preserved to prevent users from installing multiple trial copies.
warning stating a Norton-associated file, "PIFTS.exe", was trying to connect to the Internet
. Although this file was revealed to be a harmless diagnostic patch, the program gained attention in the media when Symantec removed posts from their forum concerning PIFTS. With no information available about the purpose of the program there was speculation that the program was malware
or a backdoor.
The SANS Internet Storm Center claimed to have spoken to a Symantec employee who has confirmed that "the program is theirs, part of the update process and not intended to do harm." Graham Cluley, a consultant from antivirus vendor Sophos
found PIFTS connected to a Symantec server, forwarding product and computer information.
On March 10, Symantec made an official response to the PIFTS program, claiming posts in the support forum were deleted due to forum spam
rules; however the deletion of PIFTS-related posts began before the spam attacks. Symantec stated PIFTS itself was a diagnostic patch. Cole stated the purpose of the update was to help determine how many customers would need to be migrated to Windows 7-compatible versions of Norton AntiVirus. PIFTS apparently was released without a digital signature
to verify its identity, causing firewalls to prompt for permission when it attempted to connect to the Internet.
Symantec
Symantec Corporation is the largest maker of security software for computers. The company is headquartered in Mountain View, California, and is a Fortune 500 company and a member of the S&P 500 stock market index.-History:...
, provides malware
Malware
Malware, short for malicious software, consists of programming that is designed to disrupt or deny operation, gather information that leads to loss of privacy or exploitation, or gain unauthorized access to system resources, or that otherwise exhibits abusive behavior...
prevention and removal during a subscription period. It uses signatures and heuristics to identify viruses
Computer virus
A computer virus is a computer program that can replicate itself and spread from one computer to another. The term "virus" is also commonly but erroneously used to refer to other types of malware, including but not limited to adware and spyware programs that do not have the reproductive ability...
. Other features include e-mail spam
E-mail spam
Email spam, also known as junk email or unsolicited bulk email , is a subset of spam that involves nearly identical messages sent to numerous recipients by email. Definitions of spam usually include the aspects that email is unsolicited and sent in bulk. One subset of UBE is UCE...
filtering and phishing
Phishing
Phishing is a way of attempting to acquire information such as usernames, passwords, and credit card details by masquerading as a trustworthy entity in an electronic communication. Communications purporting to be from popular social web sites, auction sites, online payment processors or IT...
protection.
Symantec distributes the product as a download, a box copy, and as OEM software. Norton AntiVirus and Norton Internet Security
Norton Internet Security
Norton Internet Security, developed by Symantec Corporation, provides malware prevention and removal during subscription period and uses signatures and heuristics to identify viruses. Other features include a software firewall, e-mail spam filtering, and phishing protection.Symantec distributes...
, a related product, held a 61% US retail market share for security suites as of the first half of 2007. Competitors, in terms of market share in this study, include antivirus products from CA, Trend Micro
Trend Micro
Trend Micro Inc. is a computer security company. It is headquartered in Tokyo, Japan and markets Trend Micro Internet Security, Trend Micro Worry-Free Business Security, OfficeScan, and other related security products and services...
, and Kaspersky Lab
Kaspersky Lab
Kaspersky Lab is a Russian computer security company, co-founded by Natalia Kaspersky and Eugene Kaspersky in 1997, offering anti-virus, anti-spyware, anti-spam, and anti-intrusion products...
.
Norton AntiVirus runs on Microsoft Windows
Microsoft Windows
Microsoft Windows is a series of operating systems produced by Microsoft.Microsoft introduced an operating environment named Windows on November 20, 1985 as an add-on to MS-DOS in response to the growing interest in graphical user interfaces . Microsoft Windows came to dominate the world's personal...
and Mac OS X
Mac OS X
Mac OS X is a series of Unix-based operating systems and graphical user interfaces developed, marketed, and sold by Apple Inc. Since 2002, has been included with all new Macintosh computer systems...
. Windows 7 support is in development for versions 2006 through 2008. Version 2009 has Windows 7 supported update already. Versions 2010, 2011, and 2012 all natively support Windows 7, without needing an update. Version 12 is the only version fully compatible with Mac OS X Lion
Mac OS X Lion
Mac OS X Lion is the eighth and current major release of Mac OS X, Apple's desktop and server operating system for Macintosh computers....
.
Origins
In May 1989, Symantec launched Symantec Antivirus for the MacintoshMacintosh
The Macintosh , or Mac, is a series of several lines of personal computers designed, developed, and marketed by Apple Inc. The first Macintosh was introduced by Apple's then-chairman Steve Jobs on January 24, 1984; it was the first commercially successful personal computer to feature a mouse and a...
(SAM). SAM 2.0, released March 1990, incorporated technology allowing users to easily update SAM to intercept and eliminate new viruses, including many that didn't exist at the time of the program's release.
In August 1990 Symantec acquired Peter Norton Computing
Peter Norton Computing
Peter Norton Computing, Inc., was a software company founded by Peter Norton. The first and most notable software package it produced is the Norton Utilities. Another very popular software was Norton Commander, especially the DOS version. In 1990, the company was acquired by Symantec. The...
from Peter Norton
Peter Norton
Peter Norton is an American programmer, software publisher, author, and philanthropist. He is best known for the computer programs and books that bear his name. Norton sold his PC-Software business to Symantec Corporation in 1990....
. Norton and his company developed various DOS
DOS
DOS, short for "Disk Operating System", is an acronym for several closely related operating systems that dominated the IBM PC compatible market between 1981 and 1995, or until about 2000 if one includes the partially DOS-based Microsoft Windows versions 95, 98, and Millennium Edition.Related...
utilities
Utility software
Utility software is system software designed to help analyze, configure, optimize or maintain a computer. A single piece of utility software is usually called a utility or tool....
including the Norton Utilities
Norton Utilities
Norton Utilities is a utility software suite designed to help analyze, configure, optimize and maintain the computer. The current version 15 of Norton Utilities Premier Edition for Windows XP/Vista/7 was released December 27, 2010....
, which did not include antivirus features. Symantec continued the development of acquired technologies. The technologies are marketed under the name of "Norton", with the tagline
Tagline
A tagline is a variant of a branding slogan typically used in marketing materials and advertising. The idea behind the concept is to create a memorable phrase that will sum up the tone and premise of a brand or product , or to reinforce the audience's memory of a product...
"from Symantec". Norton's crossed-arm pose, a registered U.S. trademark, was traditionally featured on Norton product packaging. However, his pose was later moved to the spine of the packaging, and eventually dropped altogether.
By early 1991, U.S. computers were invaded by hundreds of foreign virus strains and corporate PC infection was becoming a serious problem. Symantec's Norton Group launched Norton AntiVirus 1.0 (NAV) for PC and compatible computers. Ads for the product, with suggested retail $129, featured Norton in his crossed-arm pose, wearing a pink shirt and surgical mask covering his nose and mouth.
With the 1998 version 5.0 update, SAM was renamed Norton AntiVirus (NAV) for Macintosh.
Windows edition
Product activationProduct activation
Product activation is a license validation procedure required by some proprietary computer software programs. In one form, product activation refers to a method invented by Ric Richardson and patented by Uniloc where a software application hashes hardware serial numbers and an ID number specific...
was introduced in Norton AntiVirus 2004, addressing the estimated 3.6 million counterfeit Norton products sold. An alphanumeric
Alphanumeric
Alphanumeric is a combination of alphabetic and numeric characters, and is used to describe the collection of Latin letters and Arabic digits or a text constructed from this collection. There are either 36 or 62 alphanumeric characters. The alphanumeric character set consists of the numbers 0 to...
code is generated to identify a computer's configuration, which ties in with the product key. Users are allowed to activate their product five times with the same product key. Spyware
Spyware
Spyware is a type of malware that can be installed on computers, and which collects small pieces of information about users without their knowledge. The presence of spyware is typically hidden from the user, and can be difficult to detect. Typically, spyware is secretly installed on the user's...
and adware
Adware
Adware, or advertising-supported software, is any software package which automatically plays, displays, or downloads advertisements to a computer. These advertisements can be in the form of a pop-up. They may also be in the user interface of the software or on a screen presented to the user during...
detection and removal was introduced to the 2005 version, with the tagline "Antispyware Edition". The tagline was dropped in later releases. However, Norton AntiVirus 2009 Classic does not include spyware or adware detection. The Classic edition is marketed alongside Norton AntiVirus 2009, which does include spyware and adware detection.
Existing users of the 2006, 2007, 2008 and 2009 versions can upgrade to the latest 2010 version without buying a new subscription. Upgrading will preserve the number of days left on a user's subscription.
Version 2006 (13.0)
The redesigned main graphical user interfaceGui
Gui or guee is a generic term to refer to grilled dishes in Korean cuisine. These most commonly have meat or fish as their primary ingredient, but may in some cases also comprise grilled vegetables or other vegetarian ingredients. The term derives from the verb, "gupda" in Korean, which literally...
aggregates information in a central user interface. CNET
CNET
CNET is a tech media website that publishes news articles, blogs, and podcasts on technology and consumer electronics. Originally founded in 1994 by Halsey Minor and Shelby Bonnie, it was the flagship brand of CNET Networks and became a brand of CBS Interactive through CNET Networks' acquisition...
reports the Norton Protection Center, while useful, attempts to advertise additional products. To further facilitate detection of zero-day malware, Bloodhound disassembles a variety of programming languages, and scans code for malicious instructions using predefined algorithms. Internet Explorer homepage hijacking
Browser hijacking
Browser hijacking is the modification of a web browser's settings by malware. The term "hijacking" is used as the changes are performed without the user's permission. Some browser hijacking can be easily reversed, while other instances may be difficult to reverse. Various software packages exist...
protection was introduced in this release as well; however notably missing is search engine
Web search engine
A web search engine is designed to search for information on the World Wide Web and FTP servers. The search results are generally presented in a list of results often referred to as SERPS, or "search engine results pages". The information may consist of web pages, images, information and other...
hijacking protection. CNET highlighted Norton AntiVirus 2006's noticeable impact on system performance.
Operating system requirements call for Windows 2000 Service Pack 3
Windows 2000
Windows 2000 is a line of operating systems produced by Microsoft for use on personal computers, business desktops, laptops, and servers. Windows 2000 was released to manufacturing on 15 December 1999 and launched to retail on 17 February 2000. It is the successor to Windows NT 4.0, and is the...
or Windows XP. 150 MB of free space and a 300 MHz processor is required under either operating system. 128 MB of RAM is required under Windows 2000, while 256 MB is required in Windows XP.
Version 2007 (14.0)
Norton AntiVirus was released on September 12, 2006. Symantec revised Norton AntiVirus with the goal of reducing high system resource utilization. Windows VistaWindows Vista
Windows Vista is an operating system released in several variations developed by Microsoft for use on personal computers, including home and business desktops, laptops, tablet PCs, and media center PCs...
compatibility was introduced in this release as well. Despite having about 80% of the code rewritten, CNET
CNET
CNET is a tech media website that publishes news articles, blogs, and podcasts on technology and consumer electronics. Originally founded in 1994 by Halsey Minor and Shelby Bonnie, it was the flagship brand of CNET Networks and became a brand of CBS Interactive through CNET Networks' acquisition...
reports mixed results in performance testing. New features include a tabbed interface, eliminating the need to have separate windows open for the Norton Protection Center and for configuring the settings. Symantec extended its Veritas
VERITAS Software
Veritas Software Corp. was an international software company that was founded in 1983 as Tolerant Systems, renamed Veritas Software Corp. in 1989, and merged with Symantec in 2005. It was headquartered in Mountain View, California...
VxMS rootkit
Rootkit
A rootkit is software that enables continued privileged access to a computer while actively hiding its presence from administrators by subverting standard operating system functionality or other applications...
detection technology, allowing Norton AntiVirus 2007 to inspect files within directories to files on the volume level, detecting abnormalities or inconsistencies.
Windows 2000 compatibility was dropped from this release. Compatibility with 32-bit versions of Windows Vista
Windows Vista
Windows Vista is an operating system released in several variations developed by Microsoft for use on personal computers, including home and business desktops, laptops, tablet PCs, and media center PCs...
was added to this release with a patch from Symantec. Hardware requirements under Vista call for 150 MB free space, a 800 MHz processor and 512 MB RAM. Requirements under Windows XP similarly call for 150 MB free space, a 300 MHz processor, and 256 MB of RAM.
Version 2008 (15.0)
Norton AntiVirus 2008 was released on August 28, 2007. Emphasizing malware prevention, new features include SONARSONAR (Symantec)
SONAR is the abbreviation for Symantec Online Network for Advanced Response. Unlike virus signatures, SONAR examines the behavior of applications to decide whether they are malicious...
, which looks for suspicious application behavior. This release adds real-time exploit
Exploit (computer security)
An exploit is a piece of software, a chunk of data, or sequence of commands that takes advantage of a bug, glitch or vulnerability in order to cause unintended or unanticipated behavior to occur on computer software, hardware, or something electronic...
protection, preventing attackers from leveraging common browser and application vulnerabilities.
When installed in 32-bit versions of Windows XP Service Pack 2, 300 MB of free space, a 300 MHz processor, and 256 MB of RAM is required. When installed in 32-bit and 64-bit versions of Windows Vista, 300 MB of free space, a 800 MHz processor, and 256 MB of RAM is needed.
Version 2009 (16.0)

Benchmark (computing)
In computing, a benchmark is the act of running a computer program, a set of programs, or other operations, in order to assess the relative performance of an object, normally by running a number of standard tests and trials against it...
conducted by Passmark Software PTY LTD highlights its 47 second install time, 32 second scan time, and 5 MB memory utilization. It should be noted Symantec funded the benchmark test and provided some scripts used to benchmark each participating antivirus software
Antivirus software
Antivirus or anti-virus software is used to prevent, detect, and remove malware, including but not limited to computer viruses, computer worm, trojan horses, spyware and adware...
.
The security status and settings are now displayed in a single main interface. A CPU usage monitor displays the total CPU utilization and Norton's CPU usage in the main interface. Other features include Norton Insight
Norton Insight
Norton Insight whitelists files based on reputation. Norton-branded antivirus software then leverage the data to skip known files during virus scans. Symantec claims quicker scans and more accurate detection with the use of the technology.-Development:...
, a whitelisting technology which cuts scanning times by mapping known safe files using information from an online database. To address malware response times, updates are delivered updates 5 to 15 minutes. However, such updates are not tested by Symantec, and may cause false positives, or incorrectly identify files as malicious. The exploit scanner found in the 2007 and 2008 versions was dropped from this release.
When installed in 32-bit versions of Windows XP Service Pack 2, 150 MB of free space, a 300 MHz processor, and 256 MB of RAM is required. When installed in 32-bit or 64-bit versions of Windows Vista, 150 MB of free space, a 800 MHz processor, and 512 MB of RAM is required.
Gaming and Classic editions
Two variations on Norton AntiVirus 2009 are also marketed by Symantec. The Gaming edition provides finer control over when Norton downloads updates and allows components of the suite to be disabled either manually or automatically when the computer enters full-screen mode.The Classic edition cannot find or remove adware
Adware
Adware, or advertising-supported software, is any software package which automatically plays, displays, or downloads advertisements to a computer. These advertisements can be in the form of a pop-up. They may also be in the user interface of the software or on a screen presented to the user during...
and spyware
Spyware
Spyware is a type of malware that can be installed on computers, and which collects small pieces of information about users without their knowledge. The presence of spyware is typically hidden from the user, and can be difficult to detect. Typically, spyware is secretly installed on the user's...
.
Version 2010 (17.0)
Version 17.0 was released on September 9, 2009. Several features have been updated in this release, including SONARSONAR (Symantec)
SONAR is the abbreviation for Symantec Online Network for Advanced Response. Unlike virus signatures, SONAR examines the behavior of applications to decide whether they are malicious...
, now dubbed SONAR 2. It now uses more information to determine if an application is truly malicious. Norton Insight
Norton Insight
Norton Insight whitelists files based on reputation. Norton-branded antivirus software then leverage the data to skip known files during virus scans. Symantec claims quicker scans and more accurate detection with the use of the technology.-Development:...
can present users with information about the origins, activities, and performance of applications along with reputation data. A new feature codenamed Autospy helps users understand what Norton did when malware was found. Previous releases removed threats on sight and quietly warned users, potentially confusing when users are deceived in downloading rogue security software. Much of this information is placed on the back of the main window; a toggle button switches between the sides.
Symantec has also added Windows 7 support. Aside from that, Symantec has also added the Norton Download Insight
Norton Download Insight
Norton Download Insight provides the reputation information of any executable file that you download using the Internet Explorer 6 or Firefox 3.0 browsers or later. Download Insight supports only downloads using hypertext transfer protocol...
to prevent drive by drive downloads.
Version 2011 (18.0)
Norton Internet Security 2011 was released for Beta testing on April 21, 2010. Changes include a new user interface and improved scanning of internet sites for malware. With the 2011 version, SymantecSymantec
Symantec Corporation is the largest maker of security software for computers. The company is headquartered in Mountain View, California, and is a Fortune 500 company and a member of the S&P 500 stock market index.-History:...
also released an application that "scans" the user's Facebook
Facebook
Facebook is a social networking service and website launched in February 2004, operated and privately owned by Facebook, Inc. , Facebook has more than 800 million active users. Users must register before using the site, after which they may create a personal profile, add other users as...
feed for any malware links. This application does not require a valid subscription. In a test sponsored by Symantec, Norton Internet Security 2011 was the only security suite to ever achieve a 100 percent protection score in a new third-party test from Dennis Labs. Improved reputation scan provides the user with an easy to understand interface on files stored on the user's computer. Marking them as trusted, good, poor, or bad. The final version of Norton Internet Security 2011 was released on August 31, 2010. New features in version 2011 also include Norton Rescue Tools. These tools include Norton Bootable Recovery tool and Norton Power Eraser.
On December 9, 2010, Symantec released the 18.5 version through Norton LiveUpdate
Norton LiveUpdate
Norton LiveUpdate is an application developed by Symantec Corporation that downloads and installs security updates and software patches. LiveUpdate can only apply updates for a particular version of Norton; it cannot however upgrade a version of Norton to a later version...
. However, this update was later pulled due to numerous reports on the Norton forums that the update is causing system instability and freeze ups during system scans (both full and quick scans). This issue only affect some customers. Users affected by this update are advised to uninstall the product, run the Norton Removal Tool, and reinstall the 18.1 version from http://www.norton.com/nis11. Norton later fixed the bugs and re-released the update.
Following the acquisition of VeriSign Security by Norton's parent company Symantec
Symantec
Symantec Corporation is the largest maker of security software for computers. The company is headquartered in Mountain View, California, and is a Fortune 500 company and a member of the S&P 500 stock market index.-History:...
, several of VeriSign's features were incorporated into the 2011 edition. The new product features a new Norton logo which uses the VeriSign checkmark formerly seen in VeriSign's own logo, as well as several new icon changes to the Norton Safe Web
Norton Safe Web
Norton Safe Web is a service developed by Symantec Corporation that is designed to help users identify malicious websites. Safe Web delivers information about websites based on automated analysis and user feedback....
and Norton Identity Safe features.
Version 2012 (19.0)
Released on September 6, 2011, Norton Internet Security 2012 brought new features. One of the new features that was included with the new program is Download InsightNorton Download Insight
Norton Download Insight provides the reputation information of any executable file that you download using the Internet Explorer 6 or Firefox 3.0 browsers or later. Download Insight supports only downloads using hypertext transfer protocol...
2.0, which not only monitor files for safety but also the stability of a given file. That means that If a file is stable on Windows 7, but unstable on Windows XP, XP users will be notified for the instability of the file.
Also, integration with specialised removal tools is added, for better cleanup of already infected systems. A new smaller and more effective version of Norton power eraser is launched to assist in removal of fake antivirus software and other deeply-embedded threats that are otherwise hard to remove. A new tool called Norton Management helps manage different computers and devices equipped with Norton software from a single location.
Another feature added with this release is Sonar 4
SONAR (Symantec)
SONAR is the abbreviation for Symantec Online Network for Advanced Response. Unlike virus signatures, SONAR examines the behavior of applications to decide whether they are malicious...
. Another welcome change is that identity Safe and Safe Web
Norton Safe Web
Norton Safe Web is a service developed by Symantec Corporation that is designed to help users identify malicious websites. Safe Web delivers information about websites based on automated analysis and user feedback....
are finally compatible with Google Chrome
Google Chrome
Google Chrome is a web browser developed by Google that uses the WebKit layout engine. It was first released as a beta version for Microsoft Windows on September 2, 2008, and the public stable release was on December 11, 2008. The name is derived from the graphical user interface frame, or...
and all the passwords and notes can be stored in the cloud should the user wishes.
The user interface is also simplified with only three buttons. The third button opens a more advanced and complicated UI, where the user is able to manage settings and access different product features. The CPU meter, a long-time supported and loved feature, that was removed from Norton 2011, also makes a return (only on the "advanced screen").
Combining the netbook and desktop line, Norton Internet Security intergrates Bandwidth metering, which controls product's traffic usage and takes it down to minimum if necessary. This is ideal for networks with limited traffic. Also, the user interface window adjust accordingly to the size of the computer screen.
This version of Norton Internet Security includes several easter eggs. Pressing Shift+1, 2, 3 or 4 would change the theme to default background (plain black), ray, animals, and floral respectively. Also holding CTRL + WinKey + Alt while pressing "performance buton
Norton System Insight
- Overview :The Norton System Insight is part of Performance monitoring system, found in Norton 2010-2012 lines. It monitors and displays information about downloaded files, installed applications, scans and detected security risks. It also shows the number of Performance alerts...
" to activate "Crazy Flip", which will make the window flip head over heels. The effect would continue until the main window is closed and reopened.
In addition scans are no-longer scheduled through the Windows Task Scheduler, but through the Symantec's more advanced one, which waits for the user to stop using the keyboard and mouse (e.g. leaves the PC) and then performs tasks.
Overall Blocking and Removal of Malware
Pc mag tested 2012 on 9/26/11. They gave it a Pc Editor's choice award though the users gave it a 2 star software. The readers said that Norton Antivirus usually gets an award, but due to many false positives, not thorough removal of easy malware, and high updates Av Test gave it an okay score making it go below Panda Pro 2012, Kaspersky Antivirus 2012, and Bitdefender Plus 2012 in detection and blocking of malware. Norton blocked 89% of active zero day threats, but users couldn't tell whether the malware was neutrilized or not because of the interface.Macintosh edition
Norton AntiVirus 11 for Mac introduced support for Mac OS X v10.5 LeopardMac OS X v10.5
Mac OS X Leopard is the sixth major release of Mac OS X, Apple's desktop and server operating system for Macintosh computers. Leopard was released on 26 October 2007 as the successor of Tiger , and is available in two variants: a desktop version suitable for personal computers, and a...
platform, with the capability to detect both Macintosh and Windows
Microsoft Windows
Microsoft Windows is a series of operating systems produced by Microsoft.Microsoft introduced an operating environment named Windows on November 20, 1985 as an add-on to MS-DOS in response to the growing interest in graphical user interfaces . Microsoft Windows came to dominate the world's personal...
malware. Other features include a vulnerability scanner, which blocks attackers from leveraging software exploits. Norton AntiVirus 11 also includes the ability to scan within compressed or archived files, such as Time Capsule
Time Capsule (Apple)
The Time Capsule is a wireless network-attached storage device combined with a wireless residential gateway router made by Apple Inc. It is described as a "Backup Appliance", designed to work in tandem with the Time Machine backup utility, introduced in Mac OS X 10.5 "Leopard".The device includes a...
volumes. Operating requirements call for Mac OS X Tiger. A PowerPC
PowerPC
PowerPC is a RISC architecture created by the 1991 Apple–IBM–Motorola alliance, known as AIM...
or an Intel Core
Intel Core
Yonah was the code name for Intel's first generation of 65 nm process mobile microprocessors, based on the Banias/Dothan-core Pentium M microarchitecture. SIMD performance has been improved through the addition of SSE3 instructions and improvements to SSE and SSE2 implementations, while integer...
processor, 128 MB of RAM, and 100 MB of free hard disk space are also required. Norton AntiVirus Dual Protection for Mac is intended for Macintosh users with Windows running on their systems, using Boot Camp or virtualization
Full virtualization
In computer science, full virtualization is a virtualization technique used to provide a certain kind of virtual machine environment, namely, one that is a complete simulation of the underlying hardware...
software such as VMWare Fusion
VMware Fusion
VMware Fusion is a virtual machine software product developed by VMware for Macintosh computers with Intel processors. Fusion allows Intel-based Macs to run x86 and x86-64 "guest" operating systems, such as Microsoft Windows, Linux, NetWare and Solaris as virtual machines simultaneously with Mac OS...
. It provides a license for both Norton AntiVirus 11 with Norton AntiVirus 2009.
Performance and protection capabilites
From the 2009 to 2012 editions, Symantec made huge changes to their products' speed and performance. Norton products now have only 2 running processes, using about 24 mb of RAM.According to PassMark Security Benchmark 2012 Norton AntiVirus and Norton Internet Security are the lightest suites available. Av-comparatives.org also tested these products and give similar results.
PCMag recognises 2011 and 2012 lines as the fastest and strongest in protection.
PCWorld's tests of security software put Norton Internet Security 2009 on the 1-st place.
In 2011's test of PCWorld Norton Internet Security was the winner. Av-test.org certifies Norton, putting it on a second place after BitDefender. Kaspersky detected less, but then blocked more thoroughly. . Many other reputable sources like Dennis Technology Labs confirm the performance and effectivness of Norton 2011 and 2012 lines.
FBI cooperation
The FBIFederal Bureau of Investigation
The Federal Bureau of Investigation is an agency of the United States Department of Justice that serves as both a federal criminal investigative body and an internal intelligence agency . The FBI has investigative jurisdiction over violations of more than 200 categories of federal crime...
confirmed the active development of Magic Lantern
Magic Lantern (software)
Magic Lantern is keystroke logging software developed by the United States' Federal Bureau of Investigation. Magic Lantern was first reported in a column by Bob Sullivan of MSNBC on 20 November 2001 and by Ted Bridis of the Associated Press.-How it works:...
, a keylogger
Keystroke logging
Keystroke logging is the action of tracking the keys struck on a keyboard, typically in a covert manner so that the person using the keyboard is unaware that their actions are being monitored...
intended to obtain passwords to encrypted e-mail and other documents during criminal investigations. Magic Lantern was first reported in the media by Bob Sullivan
Bob Sullivan (journalist)
Bob Sullivan is an award winning American online journalist, author and one of the founding members of msnbc.com...
of MSNBC
MSNBC
MSNBC is a cable news channel based in the United States available in the US, Germany , South Africa, the Middle East and Canada...
on 20 November 2001 and by Ted Bridis of the Associated Press
Associated Press
The Associated Press is an American news agency. The AP is a cooperative owned by its contributing newspapers, radio and television stations in the United States, which both contribute stories to the AP and use material written by its staff journalists...
. The FBI intends to deploy Magic Lantern in the form of an e-mail attachment
E-mail attachment
An email attachment is a computer file sent along with an email message. One or more files can be attached to any email message, and be sent along with it to the recipient. This is typically used as a simple method to share documents and images...
. When the attachment is opened, it installs a trojan horse
Trojan horse (computing)
A Trojan horse, or Trojan, is software that appears to perform a desirable function for the user prior to run or install, but steals information or harms the system. The term is derived from the Trojan Horse story in Greek mythology.-Malware:A destructive program that masquerades as a benign...
on the suspect's computer, which is activated when the suspect uses PGP
Pretty Good Privacy
Pretty Good Privacy is a data encryption and decryption computer program that provides cryptographic privacy and authentication for data communication. PGP is often used for signing, encrypting and decrypting texts, E-mails, files, directories and whole disk partitions to increase the security...
encryption, often used to increase the security of sent e-mail messages. When activated, the trojan will log the PGP password, which allows the FBI to decrypt user communications. Symantec and other major antivirus vendors have whitelisted the Magic Lantern trojan, rendering their antivirus products, including Norton AntiVirus, incapable of detecting it. Concerns around this whitelisting include uncertainties about Magic Lantern's full surveillance potential and whether hackers could subvert it and redeploy it for purposes outside of law enforcement.
Graham Cluley, a technology consultant from Sophos
Sophos
Sophos is a developer and vendor of security software and hardware, including anti-virus, anti-spyware, anti-spam, network access control, encryption software and data loss prevention for desktops, servers, email systems and other network gateways....
, said "We have no way of knowing if it was written by the FBI, and even if we did, we wouldn’t know whether it was being used by the FBI or if it had been commandeered by a third party". Another reaction came from Marc Maiffret, chief technology officer and cofounder of eEye Digital Security who states: "Our customers are paying us for a service, to protect them from all forms of malicious code. It is not up to us to do law enforcement's job for them so we do not, and will not, make any exceptions for law enforcement malware or other tools."
Proponents of Magic Lantern argue the technology would allow law enforcement to efficiently and quickly decrypt time-sensitive messages protected by encryption schemes. Implementing Magic Lantern does not require physical access to a suspect's computer, unlike Carnivore, a predecessor to Magic Lantern, since physical access to a computer would require a court order. FBI spokesman Paul Bresson, in response to a question about whether Magic Lantern also needed a court order to deploy, would only say "Like all technology projects or tools deployed by the FBI it would be used pursuant to the appropriate legal process."
Updates kill legitimate software
On January 28, 2010 SymantecSymantec
Symantec Corporation is the largest maker of security software for computers. The company is headquartered in Mountain View, California, and is a Fortune 500 company and a member of the S&P 500 stock market index.-History:...
Anti-virus update marked Spotify
Spotify
Spotify is a Swedish-founded, UK-headquartered DRM-based music streaming service offering streaming of selected music from a range of major and independent record labels, including Sony, EMI, Warner Music Group, and Universal. Launched in October 2008 by Swedish startup Spotify AB, the service had...
as a Trojan Horse
Trojan horse (computing)
A Trojan horse, or Trojan, is software that appears to perform a desirable function for the user prior to run or install, but steals information or harms the system. The term is derived from the Trojan Horse story in Greek mythology.-Malware:A destructive program that masquerades as a benign...
disabling the software across millions of PCs.
http://aka-community.symantec.com/connect/forums/spotify-detected-trojan-horse
http://getsatisfaction.com/spotify/topics/spotify_defined_as_a_trojan_by_symantec
Product support
Retail customers report slow and indifferent service on bugs. Examples include a faulty error message stating current subscriptions had expired. Users received an error stating "Your virus protection cannot be updated." This error occurred after an update to the software and refused to allow daily updates. Though the bug was reported in 2004, it was not corrected for the 2005 or 2006 versions.Another incident occurred in May 2007, when Norton Antivirus flagged components of the Pegasus
Pegasus Mail
Pegasus Mail is a donationware , proprietary, email client that is developed and maintained by David Harris and his team. It was originally released in 1990 for internal and external mail on Netware networks with MS-DOS clients, and was subsequently ported to Microsoft Windows...
E-mail
Electronic mail, commonly known as email or e-mail, is a method of exchanging digital messages from an author to one or more recipients. Modern email operates across the Internet or other computer networks. Some early email systems required that the author and the recipient both be online at the...
client as malicious, rendering the program corrupted. Symantec customer service addressed the problem by running through a checklist of troubleshooting steps which were not always successful.
Faulty update
On July 25, 2006, Symantec released a faulty update for Norton AntiVirus 2006 users. Users reported an onscreen message stating "Norton AntiVirus 2006 does not support the repair feature. Please uninstall and reinstall.". Symantec claimed the faulty update was downloaded to customers between 1:00 PM and 7:00 PM on July 25, 2006. Symantec developed a workaround tool and has listed troubleshooting steps, available here. The company released a statement, stating they expected to deliver a repair patch to affected users by Monday, July 31, 2006."Uninstallation
Norton AntiVirus has been criticized for refusing to uninstall completely, leaving unnecessary files behind. Another issue is versions prior to 2009 installed LiveUpdateNorton LiveUpdate
Norton LiveUpdate is an application developed by Symantec Corporation that downloads and installs security updates and software patches. LiveUpdate can only apply updates for a particular version of Norton; it cannot however upgrade a version of Norton to a later version...
, which updates Norton-branded software, separately. The user must uninstall both Norton AntiVirus and the LiveUpdate component manually. The LiveUpdate component is purposely left behind to update other Norton-branded products, if present. In response, Symantec developed the Norton Removal Tool to remove leftover registry
Windows registry
The Windows Registry is a hierarchical database that stores configuration settings and options on Microsoft Windows operating systems. It contains settings for low-level operating system components as well as the applications running on the platform: the kernel, device drivers, services, SAM, user...
keys and values along with files and folders. However, neither route of uninstallation will remove subscription data, preserved to prevent users from installing multiple trial copies.
Incompatibilities with ZoneAlarm
Norton AntiVirus 2007 will not install alongside ZoneAlarm. This incompatibility has caused annoyance for Norton customers who purchased Norton AntiVirus 2007 with no prior warning or notice of the incompatibility. Symantec recommends removing ZoneAlarm, then reinstalling it with its Internet Worm Protection feature disabled, which controls what applications can access the Internet and which protocols they can use to do so.PIFTS.exe
On March 9, 2009, some users of Norton AntiVirus 2006 and 2007 experienced a firewallFirewall (computing)
A firewall is a device or set of devices designed to permit or deny network transmissions based upon a set of rules and is frequently used to protect networks from unauthorized access while permitting legitimate communications to pass....
warning stating a Norton-associated file, "PIFTS.exe", was trying to connect to the Internet
Internet
The Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
. Although this file was revealed to be a harmless diagnostic patch, the program gained attention in the media when Symantec removed posts from their forum concerning PIFTS. With no information available about the purpose of the program there was speculation that the program was malware
Malware
Malware, short for malicious software, consists of programming that is designed to disrupt or deny operation, gather information that leads to loss of privacy or exploitation, or gain unauthorized access to system resources, or that otherwise exhibits abusive behavior...
or a backdoor.
The SANS Internet Storm Center claimed to have spoken to a Symantec employee who has confirmed that "the program is theirs, part of the update process and not intended to do harm." Graham Cluley, a consultant from antivirus vendor Sophos
Sophos
Sophos is a developer and vendor of security software and hardware, including anti-virus, anti-spyware, anti-spam, network access control, encryption software and data loss prevention for desktops, servers, email systems and other network gateways....
found PIFTS connected to a Symantec server, forwarding product and computer information.
On March 10, Symantec made an official response to the PIFTS program, claiming posts in the support forum were deleted due to forum spam
Forum spam
Forum spam is the creating of messages that are advertisements, abusive, or otherwise unwanted on Internet forums. It is generally done by automated spambots.- Types of spam :...
rules; however the deletion of PIFTS-related posts began before the spam attacks. Symantec stated PIFTS itself was a diagnostic patch. Cole stated the purpose of the update was to help determine how many customers would need to be migrated to Windows 7-compatible versions of Norton AntiVirus. PIFTS apparently was released without a digital signature
Digital signature
A digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender, and that it was not altered in transit...
to verify its identity, causing firewalls to prompt for permission when it attempted to connect to the Internet.

