Key schedule
Encyclopedia

Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
, the so-called product cipher
Product cipher
In cryptography, a product cipher combines two or more transformations in a manner intending that the resulting cipher is more secure than the individual components to make it resistant to cryptanalysis. The product cipher combines a sequence of simple transformations such as substitution,...
s are a certain kind of ciphers, where the (de-)ciphering of data is done in "rounds". The general setup of each round is the same, except for some hard-coded parameters and a part of the cipher key
Key (cryptography)
In cryptography, a key is a piece of information that determines the functional output of a cryptographic algorithm or cipher. Without a key, the algorithm would produce no useful result. In encryption, a key specifies the particular transformation of plaintext into ciphertext, or vice versa...
, called a subkey. A key schedule is an algorithm that, given the key, calculates the subkeys for these rounds.
Some types of key schedules
- Some ciphers have simple key schedules. For example, the block cipher TEATiny Encryption AlgorithmIn cryptography, the Tiny Encryption Algorithm is a block cipher notable for its simplicity of description and implementation, typically a few lines of code...
simply splits the 128-bit key into four 32-bit pieces and uses them repeatedly in successive rounds.
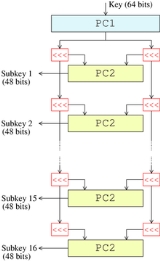
- DESData Encryption StandardThe Data Encryption Standard is a block cipher that uses shared secret encryption. It was selected by the National Bureau of Standards as an official Federal Information Processing Standard for the United States in 1976 and which has subsequently enjoyed widespread use internationally. It is...
uses a key schedule where the 56 bit key is divided into two 28-bit halves; each half is thereafter treated separately. In successive rounds, both halves are rotated left by one or two bits (specified for each round), and then 48 subkey bits are selected by Permuted Choice 2 (PC-2) — 24 bits from the left half, and 24 from the right. The rotations mean that a different set of bits is used in each subkey; each bit is used in approximately 14 out of the 16 subkeys.
- In an effort to avoid simple relationships between the cipher key and the subkeys, to resist such forms of cryptanalysisCryptanalysisCryptanalysis is the study of methods for obtaining the meaning of encrypted information, without access to the secret information that is normally required to do so. Typically, this involves knowing how the system works and finding a secret key...
as related-key attackRelated-key attackIn cryptography, a related-key attack is any form of cryptanalysis where the attacker can observe the operation of a cipher under several different keys whose values are initially unknown, but where some mathematical relationship connecting the keys is known to the attacker...
s and slide attackSlide attackThe slide attack is a form of cryptanalysis designed to deal with the prevailing idea that even weak ciphers can become very strong by increasing the number of rounds, which can ward off a differential attack. The slide attack works in such a way as to make the number of rounds in a cipher irrelevant...
s, many modern ciphers use much more elaborate key schedules, algorithms that use a one-way functionOne-way functionIn computer science, a one-way function is a function that is easy to compute on every input, but hard to invert given the image of a random input. Here "easy" and "hard" are to be understood in the sense of computational complexity theory, specifically the theory of polynomial time problems...
to generate an "expanded key" from which subkeys are drawn. Some ciphers, such as Rijndael (AES)Rijndael key scheduleAES uses a key schedule to expand a short key into a number of separate round keys. This is known as the Rijndael key schedule.- Common operations :...
and BlowfishBlowfish (cipher)Blowfish is a keyed, symmetric block cipher, designed in 1993 by Bruce Schneier and included in a large number of cipher suites and encryption products. Blowfish provides a good encryption rate in software and no effective cryptanalysis of it has been found to date...
, use parts of the cipher algorithm itself for this key expansion, sometimes initialized with some "nothing up my sleeve numberNothing up my sleeve numberIn cryptography, nothing up my sleeve numbers are any numbers which, by their construction, are above suspicion of hidden properties. They are used in creating cryptographic functions such as hashes and ciphers. These algorithms often need randomized constants for mixing or initialization purposes...
s". Other ciphers, such as RC5RC5In cryptography, RC5 is a block cipher notable for its simplicity. Designed by Ronald Rivest in 1994, RC stands for "Rivest Cipher", or alternatively, "Ron's Code"...
, expand keys with functions that are somewhat or completely different from the encryption functions.

