
Internet Protocol
Encyclopedia
Communications protocol
A communications protocol is a system of digital message formats and rules for exchanging those messages in or between computing systems and in telecommunications...
used for relaying datagram
Datagram
A datagram is a basic transfer unit associated with a packet-switched network in which the delivery, arrival time, and order are not guaranteed....
s (packets) across an internetwork using the Internet Protocol Suite
Internet protocol suite
The Internet protocol suite is the set of communications protocols used for the Internet and other similar networks. It is commonly known as TCP/IP from its most important protocols: Transmission Control Protocol and Internet Protocol , which were the first networking protocols defined in this...
. Responsible for routing packets across network boundaries, it is the primary protocol that establishes the Internet
Internet
The Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
.
IP is the primary protocol in the Internet Layer
Internet layer
The internet layer or IP layer is a group of internetworking methods in the Internet protocol suite, commonly also called TCP/IP, which is the foundation of the Internet...
of the Internet Protocol Suite and has the task of delivering datagrams from the source host
Host (network)
A network host is a computer connected to a computer network. A network host may offer information resources, services, and applications to users or other nodes on the network. A network host is a network node that is assigned a network layer host address....
to the destination host solely based on their addresses
IP address
An Internet Protocol address is a numerical label assigned to each device participating in a computer network that uses the Internet Protocol for communication. An IP address serves two principal functions: host or network interface identification and location addressing...
. For this purpose, IP defines addressing methods and structures for datagram encapsulation
Encapsulation (networking)
In computer networking, encapsulation is a method of designing modular communication protocols in which logically separate functions in the network are abstracted from their underlying structures by inclusion or information hiding within higher level objects....
.
Historically, IP was the connectionless datagram service in the original Transmission Control Program introduced by Vint Cerf
Vint Cerf
Vinton Gray "Vint" Cerf is an American computer scientist, who is recognized as one of "the fathers of the Internet", sharing this title with American computer scientist Bob Kahn...
and Bob Kahn
Bob Kahn
Robert Elliot Kahn is an American Internet pioneer, engineer and computer scientist, who, along with Vinton G. Cerf, invented the Transmission Control Protocol and the Internet Protocol , the fundamental communication protocols at the heart of the Internet.-Career:After receiving a B.E.E...
in 1974, the other being the connection-oriented Transmission Control Protocol
Transmission Control Protocol
The Transmission Control Protocol is one of the core protocols of the Internet Protocol Suite. TCP is one of the two original components of the suite, complementing the Internet Protocol , and therefore the entire suite is commonly referred to as TCP/IP...
(TCP). The Internet Protocol Suite is therefore often referred to as TCP/IP.
The first major version of IP, now referred to as Internet Protocol Version 4
IPv4
Internet Protocol version 4 is the fourth revision in the development of the Internet Protocol and the first version of the protocol to be widely deployed. Together with IPv6, it is at the core of standards-based internetworking methods of the Internet...
(IPv4) is the dominant protocol of the Internet, although the successor, Internet Protocol Version 6
IPv6
Internet Protocol version 6 is a version of the Internet Protocol . It is designed to succeed the Internet Protocol version 4...
(IPv6) is in active, growing deployment worldwide.
Function
The Internet Protocol is responsible for addressing hosts and routing datagrams (packets) from a source host to the destination host across one or more IP networks. For this purpose the Internet Protocol defines an addressing system that has two functions. Addresses identify hosts and provide a logical location service. Each packet is tagged with a header that contains the meta-data for the purpose of delivery. This process of tagging is also called encapsulation.Reliability
The design principles of the Internet protocols assume that the network infrastructure is inherently unreliable at any single network element or transmission medium and that it is dynamic in terms of availability of links and nodes. No central monitoring or performance measurement facility exists that tracks or maintains the state of the network. For the benefit of reducing network complexity, the intelligence in the network is purposely mostly located in the end nodes of each data transmission, cf. end-to-end principleEnd-to-end principle
The end-to-end principle is a classic design principle of computer networking which states that application specific functions ought to reside in the end hosts of a network rather than in intermediary nodes, provided they can be implemented "completely and correctly" in the end hosts...
. Routers in the transmission path simply forward packets to the next known local gateway matching the routing prefix for the destination address.
As a consequence of this design, the Internet Protocol only provides best effort delivery
Best effort delivery
Best effort delivery describes a network service in which the network does not provide any guarantees that data is delivered or that a user is given a guaranteed quality of service level or a certain priority...
and its service is characterized as unreliable. In network architectural language it is a connection-less protocol, in contrast to so-called connection-oriented
Connection-oriented
Connection-oriented communication is a data communication mode in telecommunications whereby the devices at the end points use a protocol to establish an end-to-end logical or physical connection before any data may be sent. In case of digital transmission, in-order delivery of a bit stream or...
modes of transmission. The lack of reliability permits various error conditions, such data corruption
Data corruption
Data corruption refers to errors in computer data that occur during writing, reading, storage, transmission, or processing, which introduce unintended changes to the original data...
, packet loss and duplication, as well as out-of-order packet delivery. Since routing is dynamic for every packet and the network maintains no state of the path of prior packets, it is possible that some packets are routed on a longer path to their destination, resulting in improper sequencing at the receiver.
The only assistance that the Internet Protocol provides in Version 4 (IPv4) is to ensure that the IP packet header is error-free through computation of a checksum
Checksum
A checksum or hash sum is a fixed-size datum computed from an arbitrary block of digital data for the purpose of detecting accidental errors that may have been introduced during its transmission or storage. The integrity of the data can be checked at any later time by recomputing the checksum and...
at the routing nodes. This has the side-effect of discarding packets with bad headers on the spot. In this case no notification is required to be sent to either end node, although a facility exists in the Internet Control Message Protocol
Internet Control Message Protocol
The Internet Control Message Protocol is one of the core protocols of the Internet Protocol Suite. It is chiefly used by the operating systems of networked computers to send error messages indicating, for example, that a requested service is not available or that a host or router could not be...
(ICMP) to do so.
IPv6, on the other hand, has abandoned the use of IP header checksums for the benefit of rapid forwarding through routing elements in the network.
The resolution or correction of any of these reliability issues is the responsibility of an upper layer protocol
Upper layer protocol
In computer networking, the term upper layer protocol refers to a more abstract protocol when performing encapsulation, in particular it is often used to describe the protocols above the network layer....
. For example, to ensure in-order delivery the upper layer may have to cache data until it can be passed to the application.
In addition to issues of reliability, this dynamic nature and the diversity of the Internet and its components provide no guarantee that any particular path is actually capable of, or suitable for, performing the data transmission requested, even if the path is available and reliable. One of the technical constraints is the size of data packets allowed on a given link. An application must assure that it uses proper transmission characteristics. Some of this responsibility lies also in the upper layer protocols between application and IP. Facilities exist to examine the maximum transmission unit
Maximum transmission unit
In computer networking, the maximum transmission unit of a communications protocol of a layer is the size of the largest protocol data unit that the layer can pass onwards. MTU parameters usually appear in association with a communications interface...
(MTU) size of the local link, as well as for the entire projected path to the destination when using IPv6. The IPv4 internetworking layer has the capability to automatically fragment
IP fragmentation
The Internet Protocol implements datagram fragmentation, so that packets may be formed that can pass through a link with a smaller maximum transmission unit than the original datagram size....
the original datagram into smaller units for transmission. In this case, IP does provide re-ordering of fragments delivered out-of-order.
Transmission Control Protocol
Transmission Control Protocol
The Transmission Control Protocol is one of the core protocols of the Internet Protocol Suite. TCP is one of the two original components of the suite, complementing the Internet Protocol , and therefore the entire suite is commonly referred to as TCP/IP...
(TCP) is an example of a protocol that will adjust its segment size to be smaller than the MTU. User Datagram Protocol
User Datagram Protocol
The User Datagram Protocol is one of the core members of the Internet Protocol Suite, the set of network protocols used for the Internet. With UDP, computer applications can send messages, in this case referred to as datagrams, to other hosts on an Internet Protocol network without requiring...
(UDP) and Internet Control Message Protocol
Internet Control Message Protocol
The Internet Control Message Protocol is one of the core protocols of the Internet Protocol Suite. It is chiefly used by the operating systems of networked computers to send error messages indicating, for example, that a requested service is not available or that a host or router could not be...
(ICMP) disregard MTU size thereby forcing IP to fragment oversized datagrams.
IP addressing and routing
Perhaps the most complex aspects of IP are IP addressIP address
An Internet Protocol address is a numerical label assigned to each device participating in a computer network that uses the Internet Protocol for communication. An IP address serves two principal functions: host or network interface identification and location addressing...
ing and routing
Routing
Routing is the process of selecting paths in a network along which to send network traffic. Routing is performed for many kinds of networks, including the telephone network , electronic data networks , and transportation networks...
. Addressing refers to how end hosts become assigned IP addresses and how subnetworks of IP host addresses are divided and grouped together. IP routing is performed by all hosts, but most importantly by internetwork routers, which typically use either interior gateway protocol
Interior gateway protocol
An interior gateway protocol is a routing protocol that is used to exchange routing information within an autonomous system ....
s (IGPs) or external gateway protocol
Exterior Gateway Protocol
The Exterior Gateway Protocol is a now obsolete routing protocol for the Internet originally specified in 1982 by Eric C. Rosen of Bolt, Beranek and Newman, and David L. Mills. It was first described in RFC 827 and formally specified in RFC 904...
s (EGPs) to help make IP datagram forwarding decisions across IP connected networks.
IP routing is also common in local networks. For example, Ethernet switches sold today support IP multicast. These switches primarily use IP addresses but also support MAC addresses for compatibility with older layer 2 Ethernet switches.
Version history
In May 1974, the Institute of Electrical and Electronic Engineers (IEEE) published a paper entitled "A Protocol for Packet Network Interconnection." The paper's authors, Vint CerfVint Cerf
Vinton Gray "Vint" Cerf is an American computer scientist, who is recognized as one of "the fathers of the Internet", sharing this title with American computer scientist Bob Kahn...
and Bob Kahn
Bob Kahn
Robert Elliot Kahn is an American Internet pioneer, engineer and computer scientist, who, along with Vinton G. Cerf, invented the Transmission Control Protocol and the Internet Protocol , the fundamental communication protocols at the heart of the Internet.-Career:After receiving a B.E.E...
, described an internetworking protocol for sharing resources using packet-switching among the nodes. A central control component of this model was the "Transmission Control Program" (TCP) that incorporated both connection-oriented links and datagram services between hosts. The monolithic Transmission Control Program was later divided into a modular architecture consisting of the Transmission Control Protocol
Transmission Control Protocol
The Transmission Control Protocol is one of the core protocols of the Internet Protocol Suite. TCP is one of the two original components of the suite, complementing the Internet Protocol , and therefore the entire suite is commonly referred to as TCP/IP...
at the connection-oriented layer and the Internet Protocol at the internetworking (datagram) layer. The model became known informally as TCP/IP, although formally referenced as the Internet Protocol Suite
Internet protocol suite
The Internet protocol suite is the set of communications protocols used for the Internet and other similar networks. It is commonly known as TCP/IP from its most important protocols: Transmission Control Protocol and Internet Protocol , which were the first networking protocols defined in this...
.
The Internet Protocol is one of the determining elements that define the Internet
Internet
The Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
. The dominant internetworking protocol in the Internet Layer
Internet layer
The internet layer or IP layer is a group of internetworking methods in the Internet protocol suite, commonly also called TCP/IP, which is the foundation of the Internet...
in use today is IPv4
IPv4
Internet Protocol version 4 is the fourth revision in the development of the Internet Protocol and the first version of the protocol to be widely deployed. Together with IPv6, it is at the core of standards-based internetworking methods of the Internet...
; with number 4 assigned as the formal protocol version number carried in every IP datagram. IPv4 is described in RFC 791 (1981).
The successor to IPv4 is IPv6
IPv6
Internet Protocol version 6 is a version of the Internet Protocol . It is designed to succeed the Internet Protocol version 4...
. Its most prominent modification from version 4 is the addressing system. IPv4 uses 32-bit
32-bit
The range of integer values that can be stored in 32 bits is 0 through 4,294,967,295. Hence, a processor with 32-bit memory addresses can directly access 4 GB of byte-addressable memory....
addresses (c. 4 billion, or , addresses) while IPv6 uses 128-bit
128-bit
There are currently no mainstream general-purpose processors built to operate on 128-bit integers or addresses, though a number of processors do operate on 128-bit data. The IBM System/370 could be considered the first rudimentary 128-bit computer as it used 128-bit floating point registers...
addresses (c. 340 undecillion, or addresses). Although adoption of IPv6 has been slow, as of June 2008, all United States government systems have demonstrated basic infrastructure support for IPv6 (if only at the backbone level).
Version numbers 0 through 3 were development versions of IPv4 used between 1977 and 1979. Version number 5 was used by the Internet Stream Protocol, an experimental streaming protocol. Version numbers 6 through 9 were proposed for various protocol models designed to replace IPv4: SIPP (Simple Internet Protocol Plus, known now as IPv6), TP/IX (RFC 1475), PIP (RFC 1621) and TUBA (TCP and UDP with Bigger Addresses, RFC 1347). Version number 6 was eventually chosen as the official assignment for the successor Internet protocol, subsequently standardized as IPv6
IPv6
Internet Protocol version 6 is a version of the Internet Protocol . It is designed to succeed the Internet Protocol version 4...
.
A humorous Request for Comments
Request for Comments
In computer network engineering, a Request for Comments is a memorandum published by the Internet Engineering Task Force describing methods, behaviors, research, or innovations applicable to the working of the Internet and Internet-connected systems.Through the Internet Society, engineers and...
that made an IPv9 protocol center of its storyline was published on April 1, 1994 by the IETF. It was intended as an April Fool's Day joke. Other protocol proposals named "IPv9" and "IPv8" have also briefly surfaced, though these came with little or no support from the wider industry and academia.
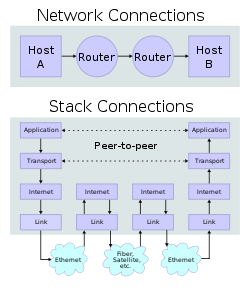
Reference diagrams
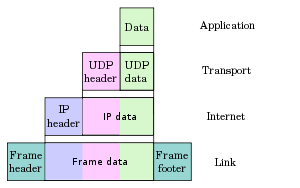 |
Vulnerabilities
The Internet Protocol is vulnerable to a variety of attacks. A thorough vulnerability assessment, along with proposed mitigations, was published in 2008, and is currently being pursued within the IETF.See also
- Outline of the Internet
- List of Internet topics
- All IP
- ATMAsynchronous Transfer ModeAsynchronous Transfer Mode is a standard switching technique designed to unify telecommunication and computer networks. It uses asynchronous time-division multiplexing, and it encodes data into small, fixed-sized cells. This differs from approaches such as the Internet Protocol or Ethernet that...
- Connectionless protocolConnectionless protocolIn telecommunications, connectionless describes communication between two network end points in which a message can be sent from one end point to another without prior arrangement. The device at one end of the communication transmits data addressed to the other, without first ensuring that the...
- Flat IPFlat IPFlat IP architecture provides a way to identify devices using symbolic names, unlike the hierarchical architecture such as that used in "normal" IP addresses...
- Geolocation softwareGeolocation softwareIn computing, geolocation software is used to deduce the geolocation of another party. For example, on the Internet, one geolocation approach is to identify the subject party's IP address, then determine what country , organization, or user the IP address has been assigned to, and finally,...
- IANAInternet Assigned Numbers AuthorityThe Internet Assigned Numbers Authority is the entity that oversees global IP address allocation, autonomous system number allocation, root zone management in the Domain Name System , media types, and other Internet Protocol-related symbols and numbers...
- InternetInternetThe Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
- Internet Protocol SuiteInternet protocol suiteThe Internet protocol suite is the set of communications protocols used for the Internet and other similar networks. It is commonly known as TCP/IP from its most important protocols: Transmission Control Protocol and Internet Protocol , which were the first networking protocols defined in this...
- Internet Stream Protocol
- ipIp (struct)ip is a struct in the C programming language. The ip struct is used as a template to form an IPv4 header in a raw socket. The structure can be found in the default include files of most Unix distributions...
- the ip structure for the C programming languageC (programming language)C is a general-purpose computer programming language developed between 1969 and 1973 by Dennis Ritchie at the Bell Telephone Laboratories for use with the Unix operating system.... - IP addressIP addressAn Internet Protocol address is a numerical label assigned to each device participating in a computer network that uses the Internet Protocol for communication. An IP address serves two principal functions: host or network interface identification and location addressing...
- IP fragmentationIP fragmentationThe Internet Protocol implements datagram fragmentation, so that packets may be formed that can pass through a link with a smaller maximum transmission unit than the original datagram size....
- IPv4IPv4Internet Protocol version 4 is the fourth revision in the development of the Internet Protocol and the first version of the protocol to be widely deployed. Together with IPv6, it is at the core of standards-based internetworking methods of the Internet...
(including packet structure) - IPv4 address exhaustion
- IPv6IPv6Internet Protocol version 6 is a version of the Internet Protocol . It is designed to succeed the Internet Protocol version 4...
(and packet structureIPv6 packetAn IPv6 packet is the smallest message entity exchanged via the Internet Protocol across an Internet Protocol version 6 network.Packets consist of control information for addressing and routing, and a payload consisting of user data. The control information in IPv6 packets is subdivided into a...
) - List of IP protocol numbers
- Packet
- TCP and UDP port numbers
- TDMTime-division multiplexingTime-division multiplexing is a type of digital multiplexing in which two or more bit streams or signals are transferred apparently simultaneously as sub-channels in one communication channel, but are physically taking turns on the channel. The time domain is divided into several recurrent...
- Transmission Control ProtocolTransmission Control ProtocolThe Transmission Control Protocol is one of the core protocols of the Internet Protocol Suite. TCP is one of the two original components of the suite, complementing the Internet Protocol , and therefore the entire suite is commonly referred to as TCP/IP...

