
Enhanced Interior Gateway Routing Protocol
Encyclopedia
Enhanced Interior Gateway Routing Protocol - (EIGRP) is a Cisco proprietary
routing protocol
loosely based on their original IGRP. EIGRP is an advanced distance-vector routing protocol
, with optimizations to minimize both the routing
instability incurred after topology changes, as well as the use of bandwidth and processing power in the router. Routers that support EIGRP will automatically redistribute route information to IGRP neighbors by converting the 32 bit EIGRP metric to the 24 bit IGRP metric.
Most of the routing optimizations are based on the Diffusing Update Algorithm
(DUAL) work from SRI
, which guarantees loop
-free operation and provides a mechanism for fast convergence.
Unlike most other distance vector protocols, EIGRP does not rely on periodic route dumps in order to maintain its topology table. Routing information is exchanged only upon the establishment of new neighbor adjacencies, after which only changes are sent. Also, it uses route tagging.
Router>show ip eigrp topology 10.0.0.1 255.255.255.255
IP-EIGRP topology entry for 10.0.0.1/32
State is Passive, Query origin flag is 1, 1 Successor(s) , FD is 40640000
Routing Descriptor Blocks:
10.0.0.1 (Serial0/0/0) , from 10.0.0.1, Send flag is 0x0
Composite metric is (40640000/128256) , Route is Internal
Vector metric:
Minimum bandwidth is 64 Kbit
Total delay is 25000 microseconds
Reliability is 255/255
Load is 197/255
Minimum MTU is 576
Hop count is 1
Bandwidth
Load
Delay
Reliability
MTU
Hop Count
The K Values
There are five (5) K values used in the Composite metric calculation - K1 through K5. The K values only act as multipliers or modifiers in the composite metric calculation. K1 is not equal to Bandwidth, etc.
By default, only total delay and minimum bandwidth are considered when EIGRP is started on a router, but an administrator can enable or disable all the K values as needed to consider the other Vector metrics.
For the purposes of comparing routes, these are combined together in a weighted formula to produce a single overall metric:
Proprietary protocol
In telecommunications, a proprietary protocol is a communications protocol owned by a single organization or individual.-Enforcement:Proprietors may enforce restrictions through patents and by keeping the protocol specification a trade secret...
routing protocol
Routing protocol
A routing protocol is a protocol that specifies how routers communicate with each other, disseminating information that enables them to select routes between any two nodes on a computer network, the choice of the route being done by routing algorithms. Each router has a priori knowledge only of...
loosely based on their original IGRP. EIGRP is an advanced distance-vector routing protocol
Distance-vector routing protocol
In computer communication theory relating to packet-switched networks, a distance-vector routing protocol is one of the two major classes of routing protocols, the other major class being the link-state protocol...
, with optimizations to minimize both the routing
Routing
Routing is the process of selecting paths in a network along which to send network traffic. Routing is performed for many kinds of networks, including the telephone network , electronic data networks , and transportation networks...
instability incurred after topology changes, as well as the use of bandwidth and processing power in the router. Routers that support EIGRP will automatically redistribute route information to IGRP neighbors by converting the 32 bit EIGRP metric to the 24 bit IGRP metric.
Most of the routing optimizations are based on the Diffusing Update Algorithm
Diffusing update algorithm
DUAL, the Diffusing Update ALgorithm, is the algorithm used by Cisco's EIGRP routing protocol to ensure that a given route is recalculated globally whenever it might cause a routing loop. It was developed by J.J. Garcia-Luna-Aceves at SRI International. According to Cisco, the full name of the...
(DUAL) work from SRI
SRI International
SRI International , founded as Stanford Research Institute, is one of the world's largest contract research institutes. Based in Menlo Park, California, the trustees of Stanford University established it in 1946 as a center of innovation to support economic development in the region. It was later...
, which guarantees loop
Routing loop problem
A routing loop is a common problem with various types of networks, particularly computer networks. They are formed when an error occurs in the operation of the routing algorithm, and as a result, in a group of nodes, the path to a particular destination forms a loop.In the simplest version, a...
-free operation and provides a mechanism for fast convergence.
Basic operation
EIGRP stores data in three tables:- Neighbor Table: Stores data about the neighboring routers, i.e. those directly accessible through directly connected interfaces.
- Topology TableTopology tableA topology table is used by routers that route traffic in a network. It consists of all routing tables inside the Autonomous System where the router is positioned. Each router using the routing protocol EIGRP then maintains a topology table for each configured network protocol — all routes learned,...
: Confusingly named, this table does not store an overview of the complete network topology; rather, it effectively contains only the aggregation of the routing tables gathered from all directly connected neighbors. This table contains a list of destination networks in the EIGRP-routed network together with their respective metrics. Also for every destination, a successor and a feasible successor are identified and stored in the table if they exist. Every destination in the topology table can be marked either as "Passive", which is the state when the routingRoutingRouting is the process of selecting paths in a network along which to send network traffic. Routing is performed for many kinds of networks, including the telephone network , electronic data networks , and transportation networks...
has stabilized and the router knows the route to the destination, or "Active" when the topology has changed and the router is in the process of (actively) updating its route to that destination.
- Routing tableRouting tableIn computer networking a routing table, or Routing Information Base , is a data table stored in a router or a networked computer that lists the routes to particular network destinations, and in some cases, metrics associated with those routes. The routing table contains information about the...
: Stores the actual routes to all destinations; the routing table is populated from the topology table with every destination network that has its successor and optionally feasible successor identified (if unequal-cost load-balancing is enabled using the variance command). The successors and feasible successors serve as the next hop routers for these destinations.
Unlike most other distance vector protocols, EIGRP does not rely on periodic route dumps in order to maintain its topology table. Routing information is exchanged only upon the establishment of new neighbor adjacencies, after which only changes are sent. Also, it uses route tagging.
EIGRP Composite and Vector metrics
EIGRP associates six (6) different vector metrics with each route and considers only four (4) of the vector metrics in computing the Composite metric:Router>show ip eigrp topology 10.0.0.1 255.255.255.255
IP-EIGRP topology entry for 10.0.0.1/32
State is Passive, Query origin flag is 1, 1 Successor(s) , FD is 40640000
Routing Descriptor Blocks:
10.0.0.1 (Serial0/0/0) , from 10.0.0.1, Send flag is 0x0
Composite metric is (40640000/128256) , Route is Internal
Vector metric:
Minimum bandwidth is 64 Kbit
Total delay is 25000 microseconds
Reliability is 255/255
Load is 197/255
Minimum MTU is 576
Hop count is 1
Bandwidth
- Minimum Bandwidth (in kilobits per second) along the path from router to destination network
Load
- Load (number in range 1 to 255; 255 being saturated)
Delay
- Total Delay (in 10s of microseconds) along the path from router to destination network
Reliability
- Reliability (number in range 1 to 255; 255 being the most reliable)
MTU
- Minimum path Maximum Transmission UnitMaximum transmission unitIn computer networking, the maximum transmission unit of a communications protocol of a layer is the size of the largest protocol data unit that the layer can pass onwards. MTU parameters usually appear in association with a communications interface...
(MTU) (never used in the metric calculation)
Hop Count
- Number of routers a packet passes through when routing to a remote network, used to limit the EIGRP AS.
The K Values
There are five (5) K values used in the Composite metric calculation - K1 through K5. The K values only act as multipliers or modifiers in the composite metric calculation. K1 is not equal to Bandwidth, etc.
By default, only total delay and minimum bandwidth are considered when EIGRP is started on a router, but an administrator can enable or disable all the K values as needed to consider the other Vector metrics.
For the purposes of comparing routes, these are combined together in a weighted formula to produce a single overall metric:
-

where the various constants (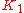 through
through 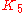 ) can be set by the user to produce varying behaviors. An important and totally non-obvious fact is that if
) can be set by the user to produce varying behaviors. An important and totally non-obvious fact is that if 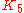 is set to zero, the term
is set to zero, the term  is not used (i.e. taken as 1).
is not used (i.e. taken as 1).
The default is for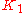 and
and 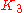 to be set to 1, and the rest to zero, effectively reducing the above formula to (Bandwidth + Delay) * 256.
to be set to 1, and the rest to zero, effectively reducing the above formula to (Bandwidth + Delay) * 256.
Obviously, these constants must be set to the same value on all routers in an EIGRP system, or permanent routing loops will probably result. Cisco routers running EIGRP will not form an EIGRP adjacency and will complain about K-values mismatch until these values are identical on these routers.
EIGRP scales Bandwidth and Delay metrics with following calculations:- Bandwidth for EIGRP = 107 / Interface Bandwidth
- Delay for EIGRP = Interface Delay / 10
On Cisco routers, the interface bandwidth is a configurable static parameter expressed in kilobits per second (setting this only affects metric calculation and not actual line bandwidth). Dividing a value of 107 kbit/s (i.e. 10 Gbit/s) by the interface bandwidth statement yields a value that is used in the weighted formula. Analogously, the interface delay is a configurable static parameter expressed in microseconds. Dividing this interface delay value by 10 yields a delay in units of tens of microseconds that is used in the weighted formula.
IGRP uses the same basic formula for computing the overall metric, the only difference is that in IGRP, the formula does not contain the scaling factor of 256. In fact, this scaling factor was introduced as a simple means to facilitate backward compatility between EIGRP and IGRP: In IGRP, the overall metric is a 24-bit value while EIGRP uses a 32-bit value to express this metric. By multiplying a 24-bit value with the factor of 256 (effectively bit-shifting it 8 bits to the left), the value is extended into 32 bits, and vice versa. This way, redistributing information between EIGRP and IGRP involves simply dividing or multiplying the metric value by a factor of 256, which is done automatically.
EIGRP also maintains a hop count for every route, however, the hop count is not used in metric calculation. It is only verified against a predefined maximum on an EIGRP router (by default it is set to 100 and can be changed to any value between 1 and 255). Routes having a hop count higher than the maximum will be advertised as unreachable by an EIGRP router.
Successor
A successor for a particular destination is a next hop router that satisfies these two conditions:- it provides the least distance to that destination
- it is guaranteed not to be a part of some routing loop
The first condition can be satisfied by comparing metrics from all neighboring routers that advertise that particular destination, increasing the metrics by the cost of the link to that respective neighbor, and selecting the neighbor that yields the least total distance. The second condition can be satisfied by testing a so-called Feasibility Condition for every neighbor advertising that destination. There can be multiple successors for a destination, depending on the actual topology.
The successors for a destination are recorded in the topology tableTopology tableA topology table is used by routers that route traffic in a network. It consists of all routing tables inside the Autonomous System where the router is positioned. Each router using the routing protocol EIGRP then maintains a topology table for each configured network protocol — all routes learned,...
and afterwards they are used to populate the routing table as next-hops for that destination.
Feasible Successor
A feasible successor for a particular destination is a next hop router that satisfies this condition:- it is guaranteed not to be a part of some routing loop
This condition is also verified by testing the Feasibility Condition.
Thus, every successor is also a feasible successor. However, in most references about EIGRP the term "feasible successor" is used to denote only those routers which provide a loop-free path but which are not successors (i.e. they do not provide the least distance). From this point of view, for a reachable destination there is always at least one successor, however, there might not be any feasible successors.
A feasible successor provides a working route to the same destination, although with a higher distance. At any time, a router can send a packet to a destination marked "Passive" through any of its successors or feasible successors without alerting them in the first place, and this packet will be delivered properly. Feasible successors are also recorded in the topology tableTopology tableA topology table is used by routers that route traffic in a network. It consists of all routing tables inside the Autonomous System where the router is positioned. Each router using the routing protocol EIGRP then maintains a topology table for each configured network protocol — all routes learned,...
.
The feasible successor effectively provides a backup route in the case that existing successors die. Also, when performing unequal-cost load-balancing (balancing the network traffic in inverse proportion to the cost of the routes), the feasible successors are used as next hops in the routing table for the load-balanced destination.
By default, the total count of successors and feasible successors for a destination stored in the routing table is limited to four. This limit can be changed in the range from 1 to 6. In more recent versions of Cisco IOS (e.g. 12.4), this range is between 1 and 16.
Active and Passive State
A destination in the topology table can be marked either as Passive or Active. A Passive state is a state when the router has identified the successor(s) for the destination. The destination changes to Active state when current successor no longer satisfies the Feasibility Condition and there are no feasible successors identified for that destination (i.e. no backup routes are available). The destination changes back from Active to Passive when the router received replies to all queries it has sent to its neighbors. Notice that if a successor stops satisfying the Feasibility Condition but there is at least one feasible successor available, the router will promote a feasible successor with the lowest total distance (the distance as reported by the feasible successor plus the cost of the link to this neighbor) to a new successor and the destination remains in the Passive state.
Reported Distance and Feasible Distance
Reported Distance (RD) is the total metric along a path to a destination network as advertised by an upstream neighbor. This distance is sometimes also called a Advertised Distance (AD) and is equal to the current lowest total distance through a successor for a neighboring router.
A Feasible Distance (FD) is the lowest known distance from a router to a particular destination. This is the Reported Distance (RD) + the cost to reach the neighboring router from which the RD was sent. It is important to note that this metric represents the last time the route went from Active to Passive state. It can be expressed in other words as a historically lowest known distance to a particular destination. While a route remains in Passive state, the FD is updated only if the actual distance to the destination decreases, otherwise it stays at its present value. On the other hand, if a router needs to enter Active state for that destination, the FD will be updated with a new value after the router transitions back from Active to Passive state. This is the only case when the FD can be increased. The transition from Active to Passive state in effect marks the start of a new history for that route.
For example, if the route to a newly discovered destination X went from Active to Passive state with a total distance of 10, the router sets the RD and FD to 10. Later this distance decreases from 10 to 8. The distance remains in the Passive state (because distance decrease never violates the Feasibility Condition) and the router updates the RD and FD to 8. Even later, the distance increases to 12 but in such a way that there is still a valid successor or feasible successor available. In this case, the RD gets updated to 12, however, the FD will remain at the value of 8. Therefore, the values of RD and FD can be different. Finally, the actual successor fails and no other feasible successor is currently identified. Therefore, the router has to transition to Active state and ask its neighbors for a new route to the destination X. Assuming that the newly found path to that destination has a total distance of 10, the router will transition back to Passive state and update both its RD and FD to the new shortest path length, in this case, 10.
Feasibility Condition
The feasibility condition is a sufficient condition for loop freedom in EIGRP-routed network. It is used to select the successors and feasible successors that are guaranteed to be on a loop-free route to a destination. Its simplified formulation is strikingly simple:
If, for a destination, a neighbor router advertises a distance that is strictly lower than our feasible distance, then this neighbor lies on a loop-free route to this destination.
or in other words,
If, for a destination, a neighbor router tells us that it is closer to the destination than we have ever been, then this neighbor lies on a loop-free route to this destination.
In exact terms, every neighbor that satisfies the relation RD < FD for a particular destination is on a loop-free route to that destination.
This condition is also called the Source Node Condition and is one of more equivalent conditions that were proposed and proven by Dr. J. J. Garcia-Luna-Aceves at SRISRI InternationalSRI International , founded as Stanford Research Institute, is one of the world's largest contract research institutes. Based in Menlo Park, California, the trustees of Stanford University established it in 1946 as a center of innovation to support economic development in the region. It was later...
. The paper proposing the Source Node Condition and the Diffusing Update AlgorithmDiffusing update algorithmDUAL, the Diffusing Update ALgorithm, is the algorithm used by Cisco's EIGRP routing protocol to ensure that a given route is recalculated globally whenever it might cause a routing loop. It was developed by J.J. Garcia-Luna-Aceves at SRI International. According to Cisco, the full name of the...
algorithm itself can be found here.
It is important to realize that this condition is a sufficient, not a necessary condition. That means that neighbors which satisfy this condition are guaranteed to be on a loop-free path to some destination, however, there may be also other neighbors on a loop-free path which do not satisfy this condition. However, such neighbors do not provide the shortest path to a destination, therefore, not using them does not present any significant impairment of the network functionality. These neighbors will be re-evaluated for possible usage if the router transitions to Active state for that destination.
EIGRP classification as a distance-vector
In the past, EIGRP was described in various Cisco marketing materials as a balanced hybrid routing protocol, allegedly combining the best features from link-state and distance-vector protocols. This description is not correct from a principal point of view. By definition:
- Distance-vector routing protocols are based on a distributed form of Bellman-Ford algorithmBellman-Ford algorithmThe Bellman–Ford algorithm computes single-source shortest paths in a weighted digraph.For graphs with only non-negative edge weights, the faster Dijkstra's algorithm also solves the problem....
to find shortest paths. They work by exchanging a vector of distances to all destinations known to each node. No further topological information is ever exchanged. Thus, each node knows about all destinations present in the network and it knows the resulting distance to each destination via every of the node's neighbors. However, the node does not have any idea of the actual network topology, nor does the node need it. - Link-state routing protocols are based on algorithms to find shortest paths in a graph (the most often used algorithm is Dijkstra's algorithmDijkstra's algorithmDijkstra's algorithm, conceived by Dutch computer scientist Edsger Dijkstra in 1956 and published in 1959, is a graph search algorithm that solves the single-source shortest path problem for a graph with nonnegative edge path costs, producing a shortest path tree...
). They work by exchanging a description of each node and its exact connections to its neighbors (in essence, each node describes its adjacencies to neighboring nodes and this information is flooded throughout the network). Therefore, each node knows the exact network topology, i.e. it has a graph representation of the network. Using this graph, each node computes the shortest paths from itself to each available destination.
The EIGRP routers exchange messages that contain information about bandwidth, delay, load, reliability and MTUMaximum transmission unitIn computer networking, the maximum transmission unit of a communications protocol of a layer is the size of the largest protocol data unit that the layer can pass onwards. MTU parameters usually appear in association with a communications interface...
of the path to each destination as known by the advertising router. Each router uses these parameters to compute the resulting distance to a destination. No further topological information is present in the messages. This principle fully corresponds to the operation of distance-vector protocols. Therefore, EIGRP is in essence a distance-vector protocol.
It is true that EIGRP uses a number of techniques not present in native distance-vector protocols, notably
- the use of explicit hello packets to discover and maintain adjacencies between routers;
- the use of a reliable protocol to transport routing updates;
- the use of a feasibility condition to select a loop-free path;
- the use of diffusing computations to involve the affected part of network into computing a new shortest path.
None of these techniques, however, makes any difference to the basic principles of EIGRP, which exchanges a vector of distances to each known destination network without full knowledge of the network topology, and, as a matter of fact, similar techniques have been used in other distance-vector protocols (notably DSDV, AODV and BabelBabel (protocol)The Babel routing protocol is a distance-vector routing protocol for Internet Protocol packet-switched networks that is designed to be robust and efficient on both wireless mesh networks and wired networks....
). While EIGRP is indeed an advanced distance-vector routing protocol, it is not a hybrid protocol.
Other details
EIGRP supports Classless Inter-Domain RoutingClassless Inter-Domain RoutingClassless Inter-Domain Routing is a method for allocating IP addresses and routing Internet Protocol packets. The Internet Engineering Task Force introduced CIDR in 1993 to replace the previous addressing architecture of classful network design in the Internet...
(CIDR), allowing the use of variable-length subnet masks—one of the protocol's improvements over its predecessor.
EIGRP is not usable in applications where routers need to know the exact network topology (for example, traffic engineeringTraffic engineeringTraffic engineering can mean:* traffic engineering , a branch of civil engineering* teletraffic engineering, a field of statistical techniques used in telecommunications...
in MPLSMultiprotocol Label SwitchingMultiprotocol Label Switching is a mechanism in high-performance telecommunications networks that directs data from one network node to the next based on short path labels rather than long network addresses, avoiding complex lookups in a routing table. The labels identify virtual links between...
).
EIGRP can run separate routingRoutingRouting is the process of selecting paths in a network along which to send network traffic. Routing is performed for many kinds of networks, including the telephone network , electronic data networks , and transportation networks...
processes for Internet ProtocolInternet ProtocolThe Internet Protocol is the principal communications protocol used for relaying datagrams across an internetwork using the Internet Protocol Suite...
(IP), IPv6IPv6Internet Protocol version 6 is a version of the Internet Protocol . It is designed to succeed the Internet Protocol version 4...
, IPXIPXInternetwork Packet Exchange is the OSI-model Network layer protocol in the IPX/SPX protocol stack.The IPX/SPXM protocol stack is supported by Novell's NetWare network operating system. Because of Netware's popularity through the late 1980s into the mid 1990s, IPX became a popular internetworking...
and AppleTalkAppleTalkAppleTalk is a proprietary suite of protocols developed by Apple Inc. for networking computers. It was included in the original Macintosh released in 1984, but is now unsupported as of the release of Mac OS X v10.6 in 2009 in favor of TCP/IP networking...
through the use of protocol-dependent moduleProtocol-dependent moduleProtocol-dependent modules are used by the routing protocol EIGRP to make decisions about adding routes learned from other sources; for example other routers or routing protocols to the routing table. The PDM is also capable of carrying information from the routing table to the topology table....
s (PDMs). However, this does not facilitate translation between protocols.
Example of setting up EIGRP on a Cisco IOS router for a private networkPrivate networkIn the Internet addressing architecture, a private network is a network that uses private IP address space, following the standards set by RFC 1918 and RFC 4193. These addresses are commonly used for home, office, and enterprise local area networks , when globally routable addresses are not...
. The 0.0.15.255 wildcardWildcard character-Telecommunication:In telecommunications, a wildcard character is a character that may be substituted for any of a defined subset of all possible characters....
in this example indicates a subnetwork with a maximum of 4094 hosts—it is the bitwise complement of the subnet mask 255.255.240.0. The no auto-summary command prevents automatic route summarization on classful boundaries, which would otherwise result in routing loops in discontiguous networks.
Router> enable
Router# config terminal
Router(config)# router eigrp 1
Router(config-router)# network 10.201.96.0 ?
A.B.C.D EIGRP wild card bits
Router(config-router)# network 10.201.96.0 0.0.15.255
Router(config-router)# no auto-summary
Router(config-router)# end
External links
- Cisco IOS IPv6 Configuration Guide, Release 12.4: Implementing EIGRP for IPv6
- EIGRP—A Fast Routing Protocol Based on Distance Vectors
- IGRP Metric
- Loop-free Routing Using Diffusing Computations
- Termination Detection for Diffusing Computations
- What you need to know about EIGRP
- EIGRP IP default network command
- EIGRP route selection animation

