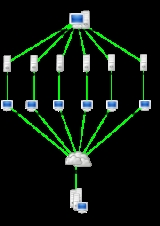
Denial-of-service attack
Encyclopedia
Internet
The Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
site
Website
A website, also written as Web site, web site, or simply site, is a collection of related web pages containing images, videos or other digital assets. A website is hosted on at least one web server, accessible via a network such as the Internet or a private local area network through an Internet...
or service
Web service
A Web service is a method of communication between two electronic devices over the web.The W3C defines a "Web service" as "a software system designed to support interoperable machine-to-machine interaction over a network". It has an interface described in a machine-processable format...
from functioning efficiently or at all, temporarily or indefinitely.
Perpetrators of DoS attacks typically target sites or services hosted on high-profile web server
Web server
Web server can refer to either the hardware or the software that helps to deliver content that can be accessed through the Internet....
s such as banks, credit card
Credit card
A credit card is a small plastic card issued to users as a system of payment. It allows its holder to buy goods and services based on the holder's promise to pay for these goods and services...
payment gateways, and even root nameserver
Root nameserver
A root name server is a name server for the Domain Name System's root zone. It directly answers requests for records in the root zone and answers other requests returning a list of the designated authoritative name servers for the appropriate top-level domain...
s. The term is generally used relating to computer network
Computer network
A computer network, often simply referred to as a network, is a collection of hardware components and computers interconnected by communication channels that allow sharing of resources and information....
s, but is not limited to this field; for example, it is also used in reference to CPU resource management.
One common method of attack involves saturating the target machine with external communications requests, such that it cannot respond to legitimate traffic, or responds so slowly as to be rendered effectively unavailable. Such attacks usually lead to a server overload
Server hog
A server hog is a user, program or system that places excessive load on a server such that the server performance as experienced by other clients is degraded, or such that the server itself is so heavily loaded that it fails to perform routine housekeeping for its own maintenance.-History:The term...
. In general terms, DoS attacks are implemented by either forcing the targeted computer(s) to reset, or consuming its resources
Resource (computer science)
A resource, or system resource, is any physical or virtual component of limited availability within a computer system. Every device connected to a computer system is a resource. Every internal system component is a resource...
so that it can no longer provide its intended service or obstructing the communication media between the intended users and the victim so that they can no longer communicate adequately.
Denial-of-service attacks are considered violations of the IAB
Internet Architecture Board
The Internet Architecture Board is the committee charged with oversight of the technical and engineering development of the Internet by the Internet Society ....
's Internet proper use policy
Internet ethics
In January 1989 the Internet Architecture Board issued a statement of policy concerning Internet ethics. This document is referred to as RFC 1087 'Ethics and the Internet'.An extract of RFC 1087 follows:...
, and also violate the acceptable use policies
Acceptable use policy
An acceptable use policy is a set of rules applied by the owner/manager of a network, website or large computer system that restrict the ways in which the network site or system may be used...
of virtually all Internet service provider
Internet service provider
An Internet service provider is a company that provides access to the Internet. Access ISPs directly connect customers to the Internet using copper wires, wireless or fiber-optic connections. Hosting ISPs lease server space for smaller businesses and host other people servers...
s. They also commonly constitute violations of the laws of individual nations.
When the DoS Attacker sends many packets of information and requests to a single network adapter, each computer in the network would experience effects from the DoS attack.
Symptoms and manifestations
The United States Computer Emergency Readiness TeamUnited States Computer Emergency Readiness Team
The United States Computer Emergency Readiness Team is part of the National Cyber Security Division of the United States' Department of Homeland Security....
(US-CERT) defines symptoms of denial-of-service attacks to include:
- Unusually slow network performanceNetwork performanceNetwork performance refers to the service quality of a telecommunications product as seen by the customer. It should not be seen merely as an attempt to get "more through" the network....
(opening files or accessing web sites) - Unavailability of a particular web site
- Inability to access any web site
- Dramatic increase in the number of spam emails received—(this type of DoS attack is considered an e-mail bombE-mail bombIn Internet usage, an email bomb is a form of net abuse consisting of sending huge volumes of email to an address in an attempt to overflow the mailbox or overwhelm the server where the email address is hosted in a denial-of-service attack....
)
Denial-of-service attacks can also lead to problems in the network 'branches' around the actual computer being attacked. For example, the bandwidth
Bandwidth (computing)
In computer networking and computer science, bandwidth, network bandwidth, data bandwidth, or digital bandwidth is a measure of available or consumed data communication resources expressed in bits/second or multiples of it .Note that in textbooks on wireless communications, modem data transmission,...
of a router between the Internet and a LAN
Local area network
A local area network is a computer network that interconnects computers in a limited area such as a home, school, computer laboratory, or office building...
may be consumed by an attack, compromising not only the intended computer, but also the entire network.
If the attack is conducted on a sufficiently large scale, entire geographical regions of Internet connectivity can be compromised without the attacker's knowledge or intent by incorrectly configured or flimsy network infrastructure equipment.
Methods of attack
A "denial-of-service" attack is characterized by an explicit attempt by attackers to prevent legitimate users of a service from using that service. There are two general forms of DoS attacks: those that crash services and those that flood services.A DoS attack can be perpetrated in a number of ways. The five basic types of attack are:
- Consumption of computational resources, such as bandwidth, disk space, or processorCentral processing unitThe central processing unit is the portion of a computer system that carries out the instructions of a computer program, to perform the basic arithmetical, logical, and input/output operations of the system. The CPU plays a role somewhat analogous to the brain in the computer. The term has been in...
time. - Disruption of configuration information, such as routingRoutingRouting is the process of selecting paths in a network along which to send network traffic. Routing is performed for many kinds of networks, including the telephone network , electronic data networks , and transportation networks...
information. - Disruption of state information, such as unsolicited resetting of TCP sessions.
- Disruption of physical network components.
- Obstructing the communication media between the intended users and the victim so that they can no longer communicate adequately.
A DoS attack may include execution of malware
Malware
Malware, short for malicious software, consists of programming that is designed to disrupt or deny operation, gather information that leads to loss of privacy or exploitation, or gain unauthorized access to system resources, or that otherwise exhibits abusive behavior...
intended to:
- Max out the processorMicroprocessorA microprocessor incorporates the functions of a computer's central processing unit on a single integrated circuit, or at most a few integrated circuits. It is a multipurpose, programmable device that accepts digital data as input, processes it according to instructions stored in its memory, and...
's usage, preventing any work from occurring. - Trigger errors in the microcodeMicrocodeMicrocode is a layer of hardware-level instructions and/or data structures involved in the implementation of higher level machine code instructions in many computers and other processors; it resides in special high-speed memory and translates machine instructions into sequences of detailed...
of the machine. - Trigger errors in the sequencing of instructions, so as to force the computer into an unstable state or lock-up.
- Exploit errors in the operating system, causing resource starvationResource starvationIn computer science, starvation is a multitasking-related problem, where a process is perpetually denied necessary resources. Without those resources, the program can never finish its task....
and/or thrashing, i.e. to use up all available facilities so no real work can be accomplished. - Crash the operating system itself.
ICMP flood
A smurf attackSmurf attack
The Smurf attack is a way of generating significant computer network traffic on a victim network. This is a type of denial-of-service attack that floods a target system via spoofed broadcast ping messages....
is one particular variant of a flooding DoS attack on the public Internet. It relies on misconfigured network devices that allow packets to be sent to all computer hosts on a particular network via the broadcast address
Broadcast address
A broadcast address is a logical address at which all devices connected to a multiple-access communications network are enabled to receive datagrams...
of the network, rather than a specific machine. The network then serves as a smurf amplifier. In such an attack, the perpetrators will send large numbers of IP
Internet Protocol
The Internet Protocol is the principal communications protocol used for relaying datagrams across an internetwork using the Internet Protocol Suite...
packets with the source address faked to appear to be the address of the victim. The network's bandwidth is quickly used up, preventing legitimate packets from getting through to their destination. To combat Denial of Service attacks on the Internet, services like the Smurf Amplifier Registry
Smurf Amplifier Registry
The Smurf Amplifier Registry is a blacklist of networks on the Internet which have been misconfigured in such a way that they can be used as smurf amplifiers for smurf denial of service attacks....
have given network service provider
Network service provider
A network service provider is a business or organization that sells bandwidth or network access by providing direct backbone access to the Internet and usually access to its network access points...
s the ability to identify misconfigured networks and to take appropriate action such as filtering.
Ping flood
Ping flood
A ping flood is a simple denial-of-service attack where the attacker/s overwhelms the victim with ICMP Echo Request packets. It is most successful if the attacker has more bandwidth than the victim...
is based on sending the victim an overwhelming number of ping
Ping
Ping is a computer network administration utility used to test the reachability of a host on an Internet Protocol network and to measure the round-trip time for messages sent from the originating host to a destination computer...
packets, usually using the "ping" command from unix-like hosts (the -t flag on Windows
Microsoft Windows
Microsoft Windows is a series of operating systems produced by Microsoft.Microsoft introduced an operating environment named Windows on November 20, 1985 as an add-on to MS-DOS in response to the growing interest in graphical user interfaces . Microsoft Windows came to dominate the world's personal...
systems has a far less malignant function). It is very simple to launch, the primary requirement being access to greater bandwidth
Bandwidth (computing)
In computer networking and computer science, bandwidth, network bandwidth, data bandwidth, or digital bandwidth is a measure of available or consumed data communication resources expressed in bits/second or multiples of it .Note that in textbooks on wireless communications, modem data transmission,...
than the victim.
Ping of death
Ping of death
A ping of death is a type of attack on a computer that involves sending a malformed or otherwise malicious ping to a computer. A ping is normally 32 bytes in size ; historically, many computer systems could not handle a ping packet larger than the maximum IPv4 packet size, which is 65,535 bytes...
is based on sending the victim a malformed ping
Ping
Ping is a computer network administration utility used to test the reachability of a host on an Internet Protocol network and to measure the round-trip time for messages sent from the originating host to a destination computer...
packet, which might lead to a system crash.
SYN flood
A SYN floodSYN flood
A SYN flood is a form of denial-of-service attack in which an attacker sends a succession of SYN requests to a target's system in an attempt to consume enough server resources to make the system unresponsive to legitimate traffic.-Technical details:...
occurs when a host sends a flood of TCP/SYN packets, often with a forged sender address. Each of these packets is handled like a connection request, causing the server to spawn a half-open connection
Half-open connection
The term half-open refers to TCP connections which state is out of synchronization between the two communicating hosts, possibly due to crash of one side...
, by sending back a TCP/SYN-ACK packet(Acknowledge), and waiting for a packet in response from the sender address(response to the ACK Packet). However, because the sender address is forged, the response never comes. These half-open connections saturate the number of available connections the server is able to make, keeping it from responding to legitimate requests until after the attack ends.
Teardrop attacks
A Teardrop attack involves sending mangledMangled packet
In computer networking, a mangled or invalid packet is a packet — especially IP packet — that either lacks order or self-coherence, or contains code aimed to confuse or disrupt computers, firewalls, routers, or any service present on the network....
IP
Internet Protocol
The Internet Protocol is the principal communications protocol used for relaying datagrams across an internetwork using the Internet Protocol Suite...
fragments with overlapping, over-sized payloads to the target machine. This can crash various operating systems due to a bug in their TCP/IP fragmentation re-assembly code. Windows 3.1x
Windows 3.1x
Windows 3.1x is a series of 16-bit operating systems produced by Microsoft for use on personal computers. The series began with Windows 3.1, which was first sold during March 1992 as a successor to Windows 3.0...
, Windows 95
Windows 95
Windows 95 is a consumer-oriented graphical user interface-based operating system. It was released on August 24, 1995 by Microsoft, and was a significant progression from the company's previous Windows products...
and Windows NT
Windows NT
Windows NT is a family of operating systems produced by Microsoft, the first version of which was released in July 1993. It was a powerful high-level-language-based, processor-independent, multiprocessing, multiuser operating system with features comparable to Unix. It was intended to complement...
operating systems, as well as versions of Linux
Linux
Linux is a Unix-like computer operating system assembled under the model of free and open source software development and distribution. The defining component of any Linux system is the Linux kernel, an operating system kernel first released October 5, 1991 by Linus Torvalds...
prior to versions 2.0.32 and 2.1.63 are vulnerable to this attack.
Around September 2009, a vulnerability in Windows Vista
Windows Vista
Windows Vista is an operating system released in several variations developed by Microsoft for use on personal computers, including home and business desktops, laptops, tablet PCs, and media center PCs...
was referred to as a "teardrop attack", but the attack targeted SMB2
Server Message Block
In computer networking, Server Message Block , also known as Common Internet File System operates as an application-layer network protocol mainly used to provide shared access to files, printers, serial ports, and miscellaneous communications between nodes on a network. It also provides an...
which is a higher layer than the TCP packets that teardrop used.
Low-rate Denial-of-Service attacks
The Low-rate DoS (LDoS) attack exploits TCP’s slow-time-scale dynamics of retransmission time-out (RTO) mechanisms to reduce TCP throughput. Basically, an attacker can cause a TCP flow to repeatedly enter a RTO state by sending high-rate, but short-duration bursts, and repeating periodically at slower RTO time-scales. The TCP throughput at the attacked node will be significantly reduced while the attacker will have low average rate making it difficult to be detected.Peer-to-peer attacks
Attackers have found a way to exploit a number of bugs in peer-to-peerPeer-to-peer
Peer-to-peer computing or networking is a distributed application architecture that partitions tasks or workloads among peers. Peers are equally privileged, equipotent participants in the application...
servers to initiate DDoS attacks. The most aggressive of these peer-to-peer-DDoS attacks exploits DC++
DC++
DC++ is a free and open-source, peer-to-peer file-sharing client that can be used to connect to the Direct Connect network or to the ADC protocol...
. Peer-to-peer attacks are different from regular botnet
Botnet
A botnet is a collection of compromised computers connected to the Internet. Termed "bots," they are generally used for malicious purposes. When a computer becomes compromised, it becomes a part of a botnet...
-based attacks. With peer-to-peer there is no botnet and the attacker does not have to communicate with the clients it subverts. Instead, the attacker acts as a "puppet master," instructing clients of large peer-to-peer file sharing
File sharing
File sharing is the practice of distributing or providing access to digitally stored information, such as computer programs, multimedia , documents, or electronic books. It may be implemented through a variety of ways...
hubs to disconnect from their peer-to-peer network and to connect to the victim's website instead. As a result, several thousand computers may aggressively try to connect to a target website. While a typical web server can handle a few hundred connections per second before performance begins to degrade, most web servers fail almost instantly under five or six thousand connections per second. With a moderately large peer-to-peer attack, a site could potentially be hit with up to 750,000 connections in short order. The targeted web server will be plugged up by the incoming connections.
While peer-to-peer attacks are easy to identify with signatures, the large number of IP addresses that need to be blocked (often over 250,000 during the course of a large-scale attack) means that this type of attack can overwhelm mitigation defenses. Even if a mitigation device can keep blocking IP addresses, there are other problems to consider. For instance, there is a brief moment where the connection is opened on the server side before the signature itself comes through. Only once the connection is opened to the server can the identifying signature be sent and detected, and the connection torn down. Even tearing down connections takes server resources and can harm the server.
This method of attack can be prevented by specifying in the peer-to-peer protocol which ports are allowed or not. If port 80
Hypertext Transfer Protocol
The Hypertext Transfer Protocol is a networking protocol for distributed, collaborative, hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web....
is not allowed, the possibilities for attack on websites can be very limited.
Asymmetry of resource utilization in starvation attacks
An attack which is successful in consuming resources on the victim computer must be either:- carried out by an attacker with great resources, by either:
- controlling a computer with great computation power or, more commonly, large network bandwidth
- controlling a large number of computers and directing them to attack as a group. A DDOS attack is the primary example of this.
- taking advantage of a property of the operating system or applications on the victim system which enables an attack consuming vastly more of the victim's resources than the attacker's (an asymmetric attack). Smurf attackSmurf attackThe Smurf attack is a way of generating significant computer network traffic on a victim network. This is a type of denial-of-service attack that floods a target system via spoofed broadcast ping messages....
, SYN floodSYN floodA SYN flood is a form of denial-of-service attack in which an attacker sends a succession of SYN requests to a target's system in an attempt to consume enough server resources to make the system unresponsive to legitimate traffic.-Technical details:...
, SockstressSockstressSockstress is a method that is used to attack servers on the Internet and other networks utilizing TCP, including Windows, Mac, Linux, BSD and any router or other internet appliance that accepts TCP connections...
and NAPTHA are all asymmetric attacks.
An attack may utilize a combination of these methods in order to magnify its power.
Permanent denial-of-service attacks
A permanent denial-of-service (PDoS), also known loosely as phlashing, is an attack that damages a system so badly that it requires replacement or reinstallation of hardware. Unlike the distributed denial-of-service attack, a PDoS attack exploits security flaws which allow remote administration on the management interfaces of the victim's hardware, such as routers, printers, or other networking hardwareNetworking hardware
Networking hardware typically refers to equipment facilitating the use of a computer network. Typically, this includes routers, switches, hubs, gateways, access points, network interface cards, Networking cables, network bridges, modems, ISDN adapters, firewalls and other equipments.In the most...
. The attacker uses these vulnerabilities to replace a device's firmware
Firmware
In electronic systems and computing, firmware is a term often used to denote the fixed, usually rather small, programs and/or data structures that internally control various electronic devices...
with a modified, corrupt, or defective firmware image—a process which when done legitimately is known as flashing. This therefore "bricks
Brick (electronics)
When used in reference to consumer electronics, "brick" describes a device that cannot function in any capacity . This usage derives from the fact that some electronic devices are vaguely brick-shaped, and so those which do not function are useful only as actual bricks. The term can also be used...
" the device, rendering it unusable for its original purpose until it can be repaired or replaced.
The PDoS is a pure hardware targeted attack which can be much faster and requires fewer resources than using a botnet in a DDoS attack. Because of these features, and the potential and high probability of security exploits on Network Enabled Embedded Devices (NEEDs), this technique has come to the attention of numerous hacker
Hacker (computer security)
In computer security and everyday language, a hacker is someone who breaks into computers and computer networks. Hackers may be motivated by a multitude of reasons, including profit, protest, or because of the challenge...
communities.
PhlashDance is a tool created by Rich Smith (an employee of Hewlett-Packard's Systems Security Lab) used to detect and demonstrate PDoS vulnerabilities at the 2008 EUSecWest Applied Security Conference in London.
Application-level floods
On IRCInternet Relay Chat
Internet Relay Chat is a protocol for real-time Internet text messaging or synchronous conferencing. It is mainly designed for group communication in discussion forums, called channels, but also allows one-to-one communication via private message as well as chat and data transfer, including file...
, IRC floods are a common electronic warfare
Electronic warfare
Electronic warfare refers to any action involving the use of the electromagnetic spectrum or directed energy to control the spectrum, attack an enemy, or impede enemy assaults via the spectrum. The purpose of electronic warfare is to deny the opponent the advantage of, and ensure friendly...
weapon .
Various DoS-causing exploits
Exploit (computer security)
An exploit is a piece of software, a chunk of data, or sequence of commands that takes advantage of a bug, glitch or vulnerability in order to cause unintended or unanticipated behavior to occur on computer software, hardware, or something electronic...
such as buffer overflow
Buffer overflow
In computer security and programming, a buffer overflow, or buffer overrun, is an anomaly where a program, while writing data to a buffer, overruns the buffer's boundary and overwrites adjacent memory. This is a special case of violation of memory safety....
can cause server-running software to get confused and fill the disk space or consume all available memory or CPU time
CPU time
CPU time is the amount of time for which a central processing unit was used for processing instructions of a computer program, as opposed to, for example, waiting for input/output operations. The CPU time is often measured in clock ticks or as a percentage of the CPU's capacity...
.
Other kinds of DoS rely primarily on brute force, flooding the target with an overwhelming flux of packets, oversaturating its connection bandwidth or depleting the target's system resources. Bandwidth-saturating floods rely on the attacker having higher bandwidth available than the victim; a common way of achieving this today is via Distributed Denial of Service, employing a botnet
Botnet
A botnet is a collection of compromised computers connected to the Internet. Termed "bots," they are generally used for malicious purposes. When a computer becomes compromised, it becomes a part of a botnet...
. Other floods may use specific packet types or connection requests to saturate finite resources by, for example, occupying the maximum number of open connections or filling the victim's disk space with logs.
A "banana attack" is another particular type of DoS. It involves redirecting outgoing messages from the client back onto the client, preventing outside access, as well as flooding the client with the sent packets.
An attacker with shell-level access to a victim's computer may slow it until it is unusable or crash it by using a fork bomb
Fork bomb
In computing, the fork bomb is a form of denial-of-service attack against a computer system which makes use of the fork operation whereby a running process can create another running process...
.
Nuke
A Nuke is an old denial-of-service attack against computer networks consisting of fragmented or otherwise invalid ICMPInternet Control Message Protocol
The Internet Control Message Protocol is one of the core protocols of the Internet Protocol Suite. It is chiefly used by the operating systems of networked computers to send error messages indicating, for example, that a requested service is not available or that a host or router could not be...
packets sent to the target, achieved by using a modified ping
Ping
Ping is a computer network administration utility used to test the reachability of a host on an Internet Protocol network and to measure the round-trip time for messages sent from the originating host to a destination computer...
utility to repeatedly send this corrupt data, thus slowing down the affected computer until it comes to a complete stop.
A specific example of a nuke attack that gained some prominence is the WinNuke
WinNuke
The term WinNuke refers to a remote denial-of-service attack that affected the Microsoft Windows 95, Microsoft Windows NT and Microsoft Windows 3.1x computer operating systems. It is responsible for the famous "blue screen of death"...
, which exploited the vulnerability in the NetBIOS
NetBIOS
NetBIOS is an acronym for Network Basic Input/Output System. It provides services related to the session layer of the OSI model allowing applications on separate computers to communicate over a local area network. As strictly an API, NetBIOS is not a networking protocol...
handler in Windows 95
Windows 95
Windows 95 is a consumer-oriented graphical user interface-based operating system. It was released on August 24, 1995 by Microsoft, and was a significant progression from the company's previous Windows products...
. A string of out-of-band data was sent to TCP
Transmission Control Protocol
The Transmission Control Protocol is one of the core protocols of the Internet Protocol Suite. TCP is one of the two original components of the suite, complementing the Internet Protocol , and therefore the entire suite is commonly referred to as TCP/IP...
port 139 of the victim's machine, causing it to lock up and display a Blue Screen of Death
Blue Screen of Death
To forse a BSOD Open regedit.exe,Then search: HKLM\SYSTEM\CurrentControlSet\services\i8042prt\ParametersThen make a new DWORD called "CrashOnCtrlScroll" And set the value to 1....
(BSOD).
R-U-Dead-Yet?
This attack is one of the two web application DoS tools available to directly attack web applications by starvation of available sessions on the web server. Much like SlowlorisSlowloris
Slowloris is a piece of software written by Robert "RSnake" Hansen which allows a single machine to take down another machine's web server with minimal bandwidth and side effects on unrelated services and ports....
, RUDY keeps sessions at halt using never-ending POST transmissions and sending an arbitrarily large content-length header value.
RUDY was written by Raviv Raz from Hybrid Security.
Distributed attack
A distributed denial of service attack (DDoS) occurs when multiple systems flood the bandwidth or resources of a targeted system, usually one or more web servers. These systems are compromised by attackers using a variety of methods.Malware can carry DDoS attack mechanisms; one of the better-known examples of this was MyDoom. Its DoS mechanism was triggered on a specific date and time. This type of DDoS involved hardcoding the target IP address prior to release of the malware and no further interaction was necessary to launch the attack.
A system may also be compromised with a trojan
Trojan horse (computing)
A Trojan horse, or Trojan, is software that appears to perform a desirable function for the user prior to run or install, but steals information or harms the system. The term is derived from the Trojan Horse story in Greek mythology.-Malware:A destructive program that masquerades as a benign...
, allowing the attacker to download a zombie agent
Zombie computer
In computer science, a zombie is a computer connected to the Internet that has been compromised by a cracker, computer virus or trojan horse and can be used to perform malicious tasks of one sort or another under remote direction. Botnets of zombie computers are often used to spread e-mail spam...
(or the trojan may contain one). Attackers can also break into systems using automated tools that exploit flaws in programs that listen for connections from remote hosts. This scenario primarily concerns systems acting as servers on the web.
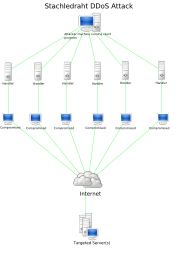
Stacheldraht
Stacheldraht
Stacheldraht is a piece of software written by Random for Linux and Solaris systems which acts as a distributed denial of service agent...
is a classic example of a DDoS tool. It utilizes a layered structure where the attacker uses a client program
Client (computing)
A client is an application or system that accesses a service made available by a server. The server is often on another computer system, in which case the client accesses the service by way of a network....
to connect to handlers, which are compromised systems that issue commands to the zombie agents
Zombie computer
In computer science, a zombie is a computer connected to the Internet that has been compromised by a cracker, computer virus or trojan horse and can be used to perform malicious tasks of one sort or another under remote direction. Botnets of zombie computers are often used to spread e-mail spam...
, which in turn facilitate the DDoS attack. Agents are compromised via the handlers by the attacker, using automated routines to exploit vulnerabilities in programs that accept remote connections running on the targeted remote hosts. Each handler can control up to a thousand agents.
These collections of systems compromisers are known as botnet
Botnet
A botnet is a collection of compromised computers connected to the Internet. Termed "bots," they are generally used for malicious purposes. When a computer becomes compromised, it becomes a part of a botnet...
s. DDoS tools like Stacheldraht
Stacheldraht
Stacheldraht is a piece of software written by Random for Linux and Solaris systems which acts as a distributed denial of service agent...
still use classic DoS attack methods centered on IP spoofing and amplification like smurf attack
Smurf attack
The Smurf attack is a way of generating significant computer network traffic on a victim network. This is a type of denial-of-service attack that floods a target system via spoofed broadcast ping messages....
s and fraggle attack
Fraggle attack
In computer security a fraggle attack is a type of denial-of-service attack where an attacker sends a large amount of UDP echo traffic to IP broadcast addresses, all of it having a fake source address...
s (these are also known as bandwidth consumption attacks). SYN floods (also known as resource starvation attacks) may also be used. Newer tools can use DNS servers for DoS purposes. See next section.
Simple attacks such as SYN floods may appear with a wide range of source IP addresses, giving the appearance of a well distributed DoS. These flood attacks do not require completion of the TCP three way handshake and attempt to exhaust the destination SYN queue or the server bandwidth. Because the source IP addresses can be trivially spoofed, an attack could come from a limited set of sources, or may even originate from a single host. Stack enhancements such as syn cookies
SYN cookies
SYN Cookies are the key element of a technique used to guard against SYN flood attacks. Daniel J. Bernstein, the technique's primary inventor, defines SYN Cookies as "particular choices of initial TCP sequence numbers by TCP servers." In particular, the use of SYN Cookies allows a server to avoid...
may be effective mitigation against SYN queue flooding, however complete bandwidth exhaustion may require involvement.
Unlike MyDoom's DDoS mechanism, botnets can be turned against any IP address. Script kiddies use them to deny the availability of well known websites to legitimate users. More sophisticated attackers use DDoS tools for the purposes of extortion
Extortion
Extortion is a criminal offence which occurs when a person unlawfully obtains either money, property or services from a person, entity, or institution, through coercion. Refraining from doing harm is sometimes euphemistically called protection. Extortion is commonly practiced by organized crime...
— even against their business rivals.
It is important to note the difference between a DDoS and DoS attack. If an attacker mounts an attack from a single host it would be classified as a DoS attack. In fact, any attack against availability would be classed as a Denial of Service attack. On the other hand, if an attacker uses many systems to simultaneously launch attacks against a remote host, this would be classified as a DDoS attack.
The major advantages to an attacker of using a distributed denial-of-service attack are that multiple machines can generate more attack traffic than one machine, multiple attack machines are harder to turn off than one attack machine, and that the behavior of each attack machine can be stealthier, making it harder to track down and shut down. These attacker advantages cause challenges for defense mechanisms. For example, merely purchasing more incoming bandwidth than the current volume of the attack might not help, because the attacker might be able to simply add more attack machines.
It should be noted that in some cases a machine may become part of a DDoS attack with the owner's consent. An example of this is the 2010 DDoS attack against major credit card companies by supporters of WikiLeaks
Wikileaks
WikiLeaks is an international self-described not-for-profit organisation that publishes submissions of private, secret, and classified media from anonymous news sources, news leaks, and whistleblowers. Its website, launched in 2006 under The Sunshine Press organisation, claimed a database of more...
. In cases such as this, supporters of a movement (in this case, those opposing the arrest of WikiLeaks founder Julian Assange
Julian Assange
Julian Paul Assange is an Australian publisher, journalist, writer, computer programmer and Internet activist. He is the editor in chief of WikiLeaks, a whistleblower website and conduit for worldwide news leaks with the stated purpose of creating open governments.WikiLeaks has published material...
) choose to download and run DDoS software.
Reflected attack
A distributed reflected denial of service attack (DRDoS) involves sending forged requests of some type to a very large number of computers that will reply to the requests. Using Internet Protocol address spoofingIP address spoofing
In computer networking, the term IP address spoofing or IP spoofing refers to the creation of Internet Protocol packets with a forged source IP address, called spoofing, with the purpose of concealing the identity of the sender or impersonating another computing system.-Background:The basic...
, the source address is set to that of the targeted victim, which means all the replies will go to (and flood) the target.
ICMP Echo Request attacks (Smurf Attack
Smurf attack
The Smurf attack is a way of generating significant computer network traffic on a victim network. This is a type of denial-of-service attack that floods a target system via spoofed broadcast ping messages....
) can be considered one form of reflected attack, as the flooding host(s) send Echo Requests to the broadcast addresses of mis-configured networks, thereby enticing many hosts to send Echo Reply packets to the victim. Some early DDoS programs implemented a distributed form of this attack.
Many services can be exploited to act as reflectors, some harder to block than others. DNS amplification attacks involve a new mechanism that increased the amplification effect, using a much larger list of DNS servers than seen earlier.
Degradation-of-service attacks
"Pulsing" zombies are compromised computers that are directed to launch intermittent and short-lived floodings of victim websites with the intent of merely slowing it rather than crashing it. This type of attack, referred to as "degradation-of-service" rather than "denial-of-service", can be more difficult to detect than regular zombie invasions and can disrupt and hamper connection to websites for prolonged periods of time, potentially causing more disruption than concentrated floods. Exposure of degradation-of-service attacks is complicated further by the matter of discerning whether the attacks really are attacks or just healthy and likely desired increases in website traffic.Unintentional denial of service
This describes a situation where a website ends up denied, not due to a deliberate attack by a single individual or group of individuals, but simply due to a sudden enormous spike in popularity. This can happen when an extremely popular website posts a prominent link to a second, less well-prepared site, for example, as part of a news story. The result is that a significant proportion of the primary site's regular users — potentially hundreds of thousands of people — click that link in the space of a few hours, having the same effect on the target website as a DDoS attack. A VIPDoS is the same, but specifically when the link was posted by a celebrity.An example of this occurred when Michael Jackson died
Death of Michael Jackson
On June 25, 2009, American singer Michael Jackson died of acute propofol intoxication after he suffered a respiratory arrest at his home in the Holmby Hills neighborhood in Los Angeles. His personal physician, Conrad Murray, said he found Jackson in his room, not breathing, but with a faint pulse,...
in 2009. Websites such as Google and Twitter slowed down or even crashed. Many sites' servers thought the requests were from a virus or spyware trying to cause a Denial of Service attack, warning users that their queries looked like "automated requests from a computer virus
Computer virus
A computer virus is a computer program that can replicate itself and spread from one computer to another. The term "virus" is also commonly but erroneously used to refer to other types of malware, including but not limited to adware and spyware programs that do not have the reproductive ability...
or spyware application".
News sites and link sites — sites whose primary function is to provide links to interesting content elsewhere on the Internet — are most likely to cause this phenomenon. The canonical example is the Slashdot effect
Slashdot effect
The Slashdot effect, also known as slashdotting, occurs when a popular website links to a smaller site, causing a massive increase in traffic. This overloads the smaller site, causing it to slow down or even temporarily close. The name stems from the huge influx of web traffic that results from...
. Sites such as Digg
Digg
Digg is a social news website. Prior to Digg v4, its cornerstone function consisted of letting people vote stories up or down, called digging and burying, respectively. Digg's popularity prompted the creation of copycat social networking sites with story submission and voting systems...
, the Drudge Report
Drudge Report
The Drudge Report is a news aggregation website. Run by Matt Drudge with the help of Joseph Curl and Charles Hurt, the site consists mainly of links to stories from the United States and international mainstream media about politics, entertainment, and current events as well as links to many...
, Fark
Fark
Fark is a community website created by Drew Curtis that allows members to comment on a daily batch of news articles and other items from various websites. As of June 2009, the site boasts approximately four million unique visitors per month, which puts it among the top 100 English language websites...
, Something Awful
Something Awful
Something Awful, often abbreviated to SA, is a comedy website housing a variety of content, including blog entries, forums, feature articles, digitally edited pictures, and humorous media reviews. It was created by Richard "Lowtax" Kyanka in 1999 as a largely personal website, but as it grew, so...
, and the webcomic Penny Arcade
Penny Arcade (webcomic)
Penny Arcade is a webcomic focused on video games and video game culture, written by Jerry Holkins and illustrated by Mike Krahulik. The comic debuted in 1998 on the website loonygames.com. Since then, Holkins and Krahulik have established their own site, which is typically updated with a new comic...
have their own corresponding "effects", known as "the Digg effect", being "drudged", "farking", "goonrushing" and "wanging"; respectively.
Routers have also been known to create unintentional DoS attacks, as both D-Link
D-Link
D-Link Corporation was founded in June 1986 in Taipei as Datex Systems Inc. It began as a network adapter vendor and has gone on to become a designer, developer, and manufacturer of networking solutions for both the consumer and business markets.In 2007, it was the leading networking company in...
and Netgear
Netgear
Netgear is a U.S. manufacturer of computer networking equipment and other computer hardware....
routers have created NTP vandalism by flooding NTP servers without respecting the restrictions of client types or geographical limitations.
Similar unintentional denials of service can also occur via other media, e.g. when a URL is mentioned on television. If a server is being indexed by Google
Google
Google Inc. is an American multinational public corporation invested in Internet search, cloud computing, and advertising technologies. Google hosts and develops a number of Internet-based services and products, and generates profit primarily from advertising through its AdWords program...
or another search engine
Search engine
A search engine is an information retrieval system designed to help find information stored on a computer system. The search results are usually presented in a list and are commonly called hits. Search engines help to minimize the time required to find information and the amount of information...
during peak periods of activity, or does not have a lot of available bandwidth while being indexed, it can also experience the effects of a DoS attack.
Legal action has been taken in at least one such case. In 2006, Universal Tube & Rollform Equipment Corporation
Universal Tube & Rollform Equipment
Universal Tube & Rollform Equipment Corporation is an American manufacturer and supplier of metal machine tubes and pipes, founded in 1985. The company specializes in buying and selling tube mills, pipe mills and rollforming machines...
sued YouTube
YouTube
YouTube is a video-sharing website, created by three former PayPal employees in February 2005, on which users can upload, view and share videos....
: massive numbers of would-be youtube.com users accidentally typed the tube company's URL, utube.com. As a result, the tube company ended up having to spend large amounts of money on upgrading their bandwidth.
Denial-of-Service Level II
The goal of DoS L2 (possibly DDoS) attack is to cause a launching of a defense mechanism which blocks the network segment from which the attack originated.In case of distributed attack or IP header modification (that depends on the kind of security behavior) it will fully block the attacked network from Internet, but without system crash.
Performing DoS-attacks
A wide array of programs are used to launch DoS-attacks. Most of these programs are completely focused on performing DoS-attacks, while others are also true Packet injectors, thus able to perform other tasks as well.Some examples of such tools are hping
Hping
hping is a free packet generator and analyzer for the TCP/IP protocol distributed by Salvatore Sanfilippo .Hping is one of the de facto tools for security auditing and testing of firewalls and networks, and was used to exploit the idle scan scanning technique , and now implemented in the Nmap...
and socket
Internet socket
In computer networking, an Internet socket or network socket is an endpoint of a bidirectional inter-process communication flow across an Internet Protocol-based computer network, such as the Internet....
programming but these are not the only programs capable of such attacks. Such tools are intended for benign use, but they can also be utilized in launching attacks on victim networks
Firewalls
FirewallsFirewall (computing)
A firewall is a device or set of devices designed to permit or deny network transmissions based upon a set of rules and is frequently used to protect networks from unauthorized access while permitting legitimate communications to pass....
have simple rules such as to allow or deny protocols, ports or IP addresses. Some DoS attacks are too complex for today's firewalls, e.g. if there is an attack on port 80 (web service), firewalls cannot prevent that attack because they cannot distinguish good traffic from DoS attack traffic. Additionally, firewalls are too deep in the network hierarchy. Routers may be affected even before the firewall gets the traffic. Nonetheless, firewalls can effectively prevent users from launching simple flooding type attacks from machines behind the firewall.
Some stateful firewall
Stateful firewall
In computing, a stateful firewall is a firewall that keeps track of the state of network connections traveling across it. The firewall is programmed to distinguish legitimate packets for different types of connections...
s, like OpenBSD's pf(4)
PF (firewall)
PF is a BSD licensed stateful packet filter, a central piece of software for firewalling. It is comparable to iptables, ipfw and ipfilter...
packet filter, can act as a proxy for connections: the handshake is validated (with the client) instead of simply forwarding the packet to the destination. It is available for other BSDs as well. In that context, it is called "synproxy".
Switches
Most switches have some rate-limiting and ACLAccess control list
An access control list , with respect to a computer file system, is a list of permissions attached to an object. An ACL specifies which users or system processes are granted access to objects, as well as what operations are allowed on given objects. Each entry in a typical ACL specifies a subject...
capability. Some switches provide automatic and/or system-wide rate limiting
Rate limiting
In computer networks, rate limiting is used to control the rate of traffic sent or received on a network interface. Traffic that is less than or equal to the specified rate is sent, whereas traffic that exceeds the rate is dropped or delayed...
, traffic shaping
Traffic shaping
Traffic shaping is the control of computer network traffic in order to optimize or guarantee performance, improve latency, and/or increase usable bandwidth for some kinds of packets by delaying other kinds of packets that meet certain criteria...
, delayed binding
Delayed binding
Delayed binding, also called TCP connection splicing, is the postponement of the connection between the client and the server in order to obtain sufficient information to make a routing decision. Some application switches and routers delay binding the client session to the server until the proper...
(TCP splicing), deep packet inspection
Deep packet inspection
Deep Packet Inspection is a form of computer network packet filtering that examines the data part of a packet as it passes an inspection point, searching for protocol non-compliance, viruses, spam, intrusions or predefined criteria to decide if the packet can...
and Bogon filtering
Bogon filtering
A bogon is a bogus IP address, and an informal name for an IP packet on the public Internet that claims to be from an area of the IP address space reserved, but not yet allocated or delegated by the Internet Assigned Numbers Authority or a delegated Regional Internet Registry...
(bogus IP filtering) to detect and remediate denial of service attacks through automatic rate filtering and WAN Link failover and balancing.
These schemes will work as long as the DoS attacks are something that can be prevented by using them. For example SYN flood can be prevented using delayed binding or TCP splicing. Similarly content based DoS can be prevented using deep packet inspection. Attacks originating from dark addresses or going to dark addresses can be prevented using Bogon filtering. Automatic rate filtering can work as long as you have set rate-thresholds correctly and granularly. Wan-link failover will work as long as both links have DoS/DDoS prevention mechanism.
Routers
Similar to switches, routers have some rate-limiting and ACLAccess control list
An access control list , with respect to a computer file system, is a list of permissions attached to an object. An ACL specifies which users or system processes are granted access to objects, as well as what operations are allowed on given objects. Each entry in a typical ACL specifies a subject...
capability. They, too, are manually set. Most routers can be easily overwhelmed under DoS attack. If you add rules to take flow statistics out of the router during the DoS attacks, they further slow down and complicate the matter. Cisco IOS
Cisco IOS
Cisco IOS is the software used on the vast majority of Cisco Systems routers and current Cisco network switches...
has features that prevent flooding, i.e. example settings.
Application front end hardware
Application front end hardware is intelligent hardware placed on the network before traffic reaches the servers. It can be used on networks in conjunction with routers and switches. Application front end hardware analyzes data packets as they enter the system, and then identifies them as priority, regular, or dangerous. There are more than 25 bandwidth managementBandwidth management
Bandwidth management is the process of measuring and controlling the communications on a network link, to avoid filling the link to capacity or overfilling the link, which would result in network congestion and poor performance of the network.- Management :Bandwidth management mechanisms may be...
vendors. Hardware acceleration
Hardware acceleration
In computing, Hardware acceleration is the use of computer hardware to perform some function faster than is possible in software running on the general-purpose CPU...
is key to bandwidth management.
IPS based prevention
Intrusion-prevention systemIntrusion-prevention system
Intrusion Prevention Systems , also known as Intrusion Detection and Prevention Systems , are network security appliances that monitor network and/or system activities for malicious activity. The main functions of intrusion prevention systems are to identify malicious activity, log information...
s (IPS) are effective if the attacks have signatures associated with them. However, the trend among the attacks is to have legitimate content but bad intent. Intrusion-prevention systems which work on content recognition cannot block behavior-based DoS attacks.
An ASIC
ASIC
ASIC may refer to:* Application-specific integrated circuit, an integrated circuit developed for a particular use, as opposed to a customised general-purpose device.* ASIC programming language, a dialect of BASIC...
based IPS can detect and block denial of service attacks because they have the processing power
Clock rate
The clock rate typically refers to the frequency that a CPU is running at.For example, a crystal oscillator frequency reference typically is synonymous with a fixed sinusoidal waveform, a clock rate is that frequency reference translated by electronic circuitry into a corresponding square wave...
and the granularity to analyze the attacks and act like a circuit breaker
Circuit breaker
A circuit breaker is an automatically operated electrical switch designed to protect an electrical circuit from damage caused by overload or short circuit. Its basic function is to detect a fault condition and, by interrupting continuity, to immediately discontinue electrical flow...
in an automated way.
A rate-based IPS (RBIPS) must analyze traffic granularly and continuously monitor the traffic pattern and determine if there is traffic anomaly. It must let the legitimate traffic flow while blocking the DoS attack traffic.
DDS based defense
More focused on the problem than IPS, a DoS Defense System (DDS) is able to block connection-based DoS attacks and those with legitimate content but bad intent. A DDS can also address both protocol attacks (such as Teardrop and Ping of death) and rate-based attacks (such as ICMP floods and SYN floods).Like IPS, a purpose-built system, such as the well-known Top Layer IPS products, can detect and block denial of service attacks at much nearer line speed than a software based system.
Blackholing and sinkholing
With blackholing, all the traffic to the attacked DNS or IP address is sent to a "black hole" (null interface, non-existent server, ...). To be more efficient and avoid affecting your network connectivity, it can be managed by the ISP.Sinkholing routes to a valid IP address which analyzes traffic and rejects bad ones. Sinkholing is not efficient for most severe attacks.
Clean pipes
All traffic is passed through a "cleaning center" via a proxy, which separates "bad" traffic (DDoS and also other common internet attacks) and only sends good traffic beyond to the server. The provider needs central connectivity to the Internet to manage this kind of service.Prolexic , Tata Communications
Tata Communications
Tata Communications Limited ) is a telecommunications company located in Mumbai. They own a submarine cable network, a Tier-1 IP network, and also rent data center and colocation space. They operate India's largest data center in Pune...
and Verisign
VeriSign
Verisign, Inc. is an American company based in Dulles, Virginia that operates a diverse array of network infrastructure, including two of the Internet's thirteen root nameservers, the authoritative registry for the .com, .net, and .name generic top-level domains and the .cc and .tv country-code...
are examples of providers of this service.
Backscatter
In computer network security, backscatter is a side-effect of a spoofed denial of service (DoS) attack. In this kind of attack, the attacker spoofs (or forges) the source address in IPInternet Protocol
The Internet Protocol is the principal communications protocol used for relaying datagrams across an internetwork using the Internet Protocol Suite...
packets sent to the victim. In general, the victim machine cannot distinguish between the spoofed packets and legitimate packets, so the victim responds to the spoofed packets as it normally would. These response packets are known as backscatter.
If the attacker is spoofing source addresses randomly, the backscatter response packets from the victim will be sent back to random destinations. This effect can be used by network telescope
Network telescope
A network telescope is an Internet system that allows one to observe different large-scale events taking place on the Internet. The basic idea is to observe traffic targeting the dark address-space of the network...
s as indirect evidence of such attacks.
The term "backscatter analysis" refers to observing backscatter packets arriving at a statistically significant portion of the IP address
IP address
An Internet Protocol address is a numerical label assigned to each device participating in a computer network that uses the Internet Protocol for communication. An IP address serves two principal functions: host or network interface identification and location addressing...
space to determine characteristics of DoS attacks and victims.
Legality
In the Police and Justice Act 2006Police and Justice Act 2006
The Police and Justice Act 2006 is an Act of the Parliament of the United Kingdom. As at August 2007 many of the provisions are not yet in force...
, the United Kingdom
United Kingdom
The United Kingdom of Great Britain and Northern IrelandIn the United Kingdom and Dependencies, other languages have been officially recognised as legitimate autochthonous languages under the European Charter for Regional or Minority Languages...
specifically outlawed denial-of-service attacks and set a maximum penalty of 10 years in prison.
In the US, there can be a serious federal crime under the Computer Fraud and Abuse Act
Computer Fraud and Abuse Act
The Computer Fraud and Abuse Act is a law passed by the United States Congress in 1986, intended to reduce cracking of computer systems and to address federal computer-related offenses...
with penalties that include years of imprisonment. Many other countries have similar laws.
The US situation is under court ruling with a case in California.
See also
- Billion laughsBillion laughsIn computer security, a billion laughs attack is a type of denial-of-service attack which is aimed at parsers of XML documents.It's also referred to as an XML bomb or as an exponential entity expansion attack....
- Black faxBlack faxThe term black fax refers to a prank fax transmission, consisting of one or more pages entirely filled with a uniform black tone. The sender's intention is typically to consume as much of the recipient's fax ink, toner or thermal paper or disk space as possible, thus costing the recipient money...
- CybercrimeCyberCrimeCyberCrime was an innovative, weekly America television program on TechTV that focused on the dangers facing computer users. Filmed in San Francisco, California, the show was hosted by Alex Wellen and Jennifer London...
- DosnetDosnetA DoSnet is a type of botnet/malware and mostly used as a term for malicious botnets while benevolent botnets often simply are referred to as botnets...
- Industrial espionageIndustrial espionageIndustrial espionage, economic espionage or corporate espionage is a form of espionage conducted for commercial purposes instead of purely national security purposes...
- Intrusion-detection systemIntrusion-detection systemAn intrusion detection system is a device or software application that monitors network and/or system activities for malicious activities or policy violations and produces reports to a Management Station. Some systems may attempt to stop an intrusion attempt but this is neither required nor...
- LANDLANDA LAND attack is a DoS attack that consists of sending a special poison spoofed packet to a computer, causing it to lock up...
- Network intrusion detection systemNetwork intrusion detection systemA Network Intrusion Detection System is an intrusion detection system that tries to detect malicious activity such as denial of service attacks, port scans or even attempts to crack into computers by Network Security Monitoring of network traffic.A NIDS reads all the incoming packets and tries to...
- Regular expression Denial of Service
- Wireless signal jammerWireless signal jammerWireless signal jammers are devices used to disrupt radio signals. The low cost of manufacture of wireless signal jammers and their damaging effects have added to their popularity and frequent use.-Use for denial of service:...
- LOICLOICLOIC is an open source network stress testing application, written in C#. A JavaScript version has also been created enabling a DoS from a web browser and also a Qt edition called loiq written in C++ exists...
- SlowlorisSlowlorisSlowloris is a piece of software written by Robert "RSnake" Hansen which allows a single machine to take down another machine's web server with minimal bandwidth and side effects on unrelated services and ports....
- Virtual sit-inVirtual sit-inA virtual sit-in is a form of electronic civil disobedience deriving its name from the sit-ins popular during the civil rights movement of the 1960s. The virtual sit-in attempts to recreate that same action digitally using a distributed denial-of-service attack. During a virtual sit-in, hundreds of...
External links
- RFC 4732 Internet Denial-of-Service Considerations
- W3C The World Wide Web Security FAQ
- DoS-Attacks A Blog/News Site Covering DDoS Attacks
- DDOS attacks counter measures A Blog post about DDoS Attacks counter measures with Iptables / Netfilter
- Understanding and surviving DDoS attacks
- cert.org CERT's Guide to DoS attacks.
- ATLAS Summary Report - Real-time global report of DDoS attacks.
- linuxsecurity.com An article on preventing DDoS attacks.
- Is Your PC a Zombie?, About.com.
- Report: Distributed Denial of Service Attacks Against Independent Media and Human Rights Sites Berkman Center for Internet and Society Report on DDOS

