
Cloud computing
Encyclopedia
Computing
Computing is usually defined as the activity of using and improving computer hardware and software. It is the computer-specific part of information technology...
as a service rather than a product
Product (business)
In general, the product is defined as a "thing produced by labor or effort" or the "result of an act or a process", and stems from the verb produce, from the Latin prōdūce ' lead or bring forth'. Since 1575, the word "product" has referred to anything produced...
, whereby shared resources, software, and information are provided to computers and other devices as a utility
Utility computing
Utility computing is the packaging of computing resources, such as computation, storage and services, as a metered service similar to a traditional public utility...
(like the electricity grid) over a network
Computer network
A computer network, often simply referred to as a network, is a collection of hardware components and computers interconnected by communication channels that allow sharing of resources and information....
(typically the Internet
Internet
The Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
).
Overview
Cloud computing is a marketing term for technologies that provide computation, software, data access, and storage services that do not require end-user knowledge of the physical location and configuration of the system that delivers the services. A parallel to this concept can be drawn with the electricity grid, wherein end-users consume power without needing to understand the component devices or infrastructure required to provide the service.Cloud computing describes a new supplement, consumption, and delivery model for IT
Information technology
Information technology is the acquisition, processing, storage and dissemination of vocal, pictorial, textual and numerical information by a microelectronics-based combination of computing and telecommunications...
services based on Internet protocols, and it typically involves provisioning of dynamically scalable
Scalability
In electronics scalability is the ability of a system, network, or process, to handle growing amount of work in a graceful manner or its ability to be enlarged to accommodate that growth...
and often virtualised
Virtualization
Virtualization, in computing, is the creation of a virtual version of something, such as a hardware platform, operating system, a storage device or network resources....
resources. It is a byproduct and consequence of the ease-of-access to remote computing sites provided by the Internet. This may take the form of web-based tools or applications that users can access and use through a web browser
Web browser
A web browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web. An information resource is identified by a Uniform Resource Identifier and may be a web page, image, video, or other piece of content...
as if the programs were installed locally on their own computers.
Cloud computing providers deliver applications
Application software
Application software, also known as an application or an "app", is computer software designed to help the user to perform specific tasks. Examples include enterprise software, accounting software, office suites, graphics software and media players. Many application programs deal principally with...
via the internet, which are accessed from web browsers and desktop and mobile apps, while the business software and data are stored on servers
Server (computing)
In the context of client-server architecture, a server is a computer program running to serve the requests of other programs, the "clients". Thus, the "server" performs some computational task on behalf of "clients"...
at a remote location. In some cases, legacy applications (line of business applications that until now have been prevalent in thin client Windows computing) are delivered via a screen-sharing technology, while the computing resources are consolidated at a remote data center
Data center
A data center is a facility used to house computer systems and associated components, such as telecommunications and storage systems...
location; in other cases, entire business applications have been coded using web-based technologies such as AJAX
Ajax
- Mythology :* Ajax , son of Telamon, ruler of Salamis and a hero in the Trojan War, also known as "Ajax the Great"* Ajax the Lesser, son of Oileus, ruler of Locris and the leader of the Locrian contingent during the Trojan War.- People :...
.
At the foundation of cloud computing is the broader concept of infrastructure convergence (or Converged Infrastructure
Converged Infrastructure
Converged infrastructure packages multiple information technology components into a single, optimized computing solution. Components of a converged infrastructure solution include servers, data storage devices, networking equipment and software for IT infrastructure management, automation and...
) and shared services
Shared services
Shared services refers to the provision of a service by one part of an organization or group where that service had previously been found in more than one part of the organization or group. Thus the funding and resourcing of the service is shared and the providing department effectively becomes an...
. This type of data center environment allows enterprises to get their applications up and running faster, with easier manageability and less maintenance, and enables IT to more rapidly adjust IT resources (such as servers, storage, and networking) to meet fluctuating and unpredictable business demand.
Most cloud computing infrastructures consist of services delivered through shared data-centers and appearing as a single point of access for consumers' computing needs. Commercial offerings may be required to meet service-level agreements (SLAs), but specific terms are less often negotiated by smaller companies.
The tremendous impact of cloud computing on business has prompted the federal United States government to look to the cloud as a means to reorganize their IT infrastructure and decrease their spending budgets. With the advent of the top government official mandating cloud adoption, many agencies already have at least one or more cloud systems online.
Comparison
Cloud computing shares characteristics with:- Autonomic computingAutonomic ComputingAutonomic Computing refers to the self-managing characteristics of distributed computing resources, adapting to unpredictable changes whilst hiding intrinsic complexity to operators and users...
— Computer systems capable of self-managementSelf-management (computer science)Self-Management is the process by which computer systems shall manage their own operation without human intervention. Self-Management technologies are expected to pervade the next generation of network management systems....
. - Client–server model — Client–server computing refers broadly to any distributed applicationDistributed application-Introduction:Where classic software systems of the past century were mostly based on Client–server models and Client-centric application development, both ultimately run on one single computer, be it the client computer or the server....
that distinguishes between service providers (servers) and service requesters (clients). - Grid computingGrid computingGrid computing is a term referring to the combination of computer resources from multiple administrative domains to reach a common goal. The grid can be thought of as a distributed system with non-interactive workloads that involve a large number of files...
— "A form of distributedDistributed computingDistributed computing is a field of computer science that studies distributed systems. A distributed system consists of multiple autonomous computers that communicate through a computer network. The computers interact with each other in order to achieve a common goal...
and parallel computingParallel computingParallel computing is a form of computation in which many calculations are carried out simultaneously, operating on the principle that large problems can often be divided into smaller ones, which are then solved concurrently . There are several different forms of parallel computing: bit-level,...
, whereby a 'super and virtual computer' is composed of a clusterCluster (computing)A computer cluster is a group of linked computers, working together closely thus in many respects forming a single computer. The components of a cluster are commonly, but not always, connected to each other through fast local area networks...
of networked, loosely coupledLoose couplingIn computing and systems design a loosely coupled system is one where each of its components has, or makes use of, little or no knowledge of the definitions of other separate components. The notion was introduced into organizational studies by Karl Weick...
computers acting in concert to perform very large tasks." - Mainframe computerMainframe computerMainframes are powerful computers used primarily by corporate and governmental organizations for critical applications, bulk data processing such as census, industry and consumer statistics, enterprise resource planning, and financial transaction processing.The term originally referred to the...
— Powerful computers used mainly by large organisations for critical applications, typically bulk data processing such as censusCensusA census is the procedure of systematically acquiring and recording information about the members of a given population. It is a regularly occurring and official count of a particular population. The term is used mostly in connection with national population and housing censuses; other common...
, industry and consumer statistics, enterprise resource planningEnterprise resource planningEnterprise resource planning systems integrate internal and external management information across an entire organization, embracing finance/accounting, manufacturing, sales and service, customer relationship management, etc. ERP systems automate this activity with an integrated software application...
, and financial transaction processingTransaction processingIn computer science, transaction processing is information processing that is divided into individual, indivisible operations, called transactions. Each transaction must succeed or fail as a complete unit; it cannot remain in an intermediate state...
. - Utility computingUtility computingUtility computing is the packaging of computing resources, such as computation, storage and services, as a metered service similar to a traditional public utility...
— The "packaging of computing resourcesComputational resourceIn computational complexity theory, a computational resource is a resource used by some computational models in the solution of computational problems....
, such as computation and storage, as a metered service similar to a traditional public utility, such as electricity." - Peer-to-peerPeer-to-peerPeer-to-peer computing or networking is a distributed application architecture that partitions tasks or workloads among peers. Peers are equally privileged, equipotent participants in the application...
— Distributed architecture without the need for central coordination, with participants being at the same time both suppliers and consumers of resources (in contrast to the traditional client–server model).
Characteristics
Cloud computing exhibits the following key characteristics:- EmpowermentEmpowermentEmpowerment refers to increasing the spiritual, political, social, racial, educational, gender or economic strength of individuals and communities...
of end-users of computing resources by putting the provisioning of those resources in their own control, as opposed to the control of a centralized IT service (for example) - AgilityAgility* Agility is a physical trait of an animal or person, and a component of physical fitness. It is the ability to change the body's position and direction with speed and precision.Agility may also refer to:In Sport:...
improves with users' ability to re-provision technological infrastructure resources. - Application programming interfaceApplication programming interfaceAn application programming interface is a source code based specification intended to be used as an interface by software components to communicate with each other...
(API) accessibility to software that enables machines to interact with cloud software in the same way the user interface facilitates interaction between humans and computers. Cloud computing systems typically use RESTRepresentational State TransferRepresentational state transfer is a style of software architecture for distributed hypermedia systems such as the World Wide Web. The term representational state transfer was introduced and defined in 2000 by Roy Fielding in his doctoral dissertation...
-based APIs. - CostCostIn production, research, retail, and accounting, a cost is the value of money that has been used up to produce something, and hence is not available for use anymore. In business, the cost may be one of acquisition, in which case the amount of money expended to acquire it is counted as cost. In this...
is claimed to be reduced and in a public cloud delivery model capital expenditureCapital expenditureCapital expenditures are expenditures creating future benefits. A capital expenditure is incurred when a business spends money either to buy fixed assets or to add to the value of an existing fixed asset with a useful life extending beyond the taxable year...
is converted to operational expenditure. This is purported to lower barriers to entryBarriers to entryIn theories of competition in economics, barriers to entry are obstacles that make it difficult to enter a given market. The term can refer to hindrances a firm faces in trying to enter a market or industry - such as government regulation, or a large, established firm taking advantage of economies...
, as infrastructure is typically provided by a third-party and does not need to be purchased for one-time or infrequent intensive computing tasks. Pricing on a utility computingUtility computingUtility computing is the packaging of computing resources, such as computation, storage and services, as a metered service similar to a traditional public utility...
basis is fine-grained with usage-based options and fewer IT skills are required for implementation (in-house). - DeviceDevice IndependenceDevice independence is the process of making a software application be able to function on a wide variety of devices regardless of the local hardware on which the software is used.- Desktop computing :...
and location independence enable users to access systems using a web browser regardless of their location or what device they are using (e.g., PC, mobile phone). As infrastructure is off-site (typically provided by a third-party) and accessed via the Internet, users can connect from anywhere. - Multi-tenancy enables sharing of resources and costs across a large pool of users thus allowing for:
- Centralisation of infrastructure in locations with lower costs (such as real estate, electricity, etc.)
- Peak-load capacity increases (users need not engineer for highest possible load-levels)
- Utilisation and efficiency improvements for systems that are often only 10–20% utilised.
- ReliabilityReliability (computer networking)In computer networking, a reliable protocol is one that provides reliability properties with respect to the delivery of data to the intended recipient, as opposed to an unreliable protocol, which does not provide notifications to the sender as to the delivery of transmitted data.A reliable...
is improved if multiple redundant sites are used, which makes well-designed cloud computing suitable for business continuityBusiness continuityBusiness continuity is the activity performed by an organization to ensure that critical business functions will be available to customers, suppliers, regulators, and other entities that must have access to those functions. These activities include many daily chores such as project management,...
and disaster recoveryDisaster recoveryDisaster recovery is the process, policies and procedures related to preparing for recovery or continuation of technology infrastructure critical to an organization after a natural or human-induced disaster. Disaster recovery is a subset of business continuity...
. - ScalabilityScalabilityIn electronics scalability is the ability of a system, network, or process, to handle growing amount of work in a graceful manner or its ability to be enlarged to accommodate that growth...
and Elasticity via dynamic ("on-demand") provisioningProvisioningIn telecommunication, provisioning is the process of preparing and equipping a network to allow it to provide services to its users. In NS/EP telecommunications services, "provisioning" equates to "initiation" and includes altering the state of an existing priority service or capability.In a...
of resources on a fine-grained, self-service basis near real-time, without users having to engineer for peak loads. - PerformanceComputer performanceComputer performance is characterized by the amount of useful work accomplished by a computer system compared to the time and resources used.Depending on the context, good computer performance may involve one or more of the following:...
is monitored, and consistent and loosely coupled architectures are constructed using web services as the system interface. - SecurityComputer securityComputer security is a branch of computer technology known as information security as applied to computers and networks. The objective of computer security includes protection of information and property from theft, corruption, or natural disaster, while allowing the information and property to...
could improve due to centralisation of data, increased security-focused resources, etc., but concerns can persist about loss of control over certain sensitive data, and the lack of security for stored kernels. Security is often as good as or better than other traditional systems, in part because providers are able to devote resources to solving security issues that many customers cannot afford. However, the complexity of security is greatly increased when data is distributed over a wider area or greater number of devices and in multi-tenant systems that are being shared by unrelated users. In addition, user access to security audit logs may be difficult or impossible. Private cloud installations are in part motivated by users' desire to retain control over the infrastructure and avoid losing control of information security. - MaintenanceSoftware maintenanceSoftware Maintenance in software engineering is the modification of a software product after delivery to correct faults, to improve performance or other attributes....
of cloud computing applications is easier, because they do not need to be installed on each user's computer.
History
The term "cloud" is used as a metaphor for the Internet, based on the cloud drawing used in the past to represent the telephone network, and later to depict the Internet in computer network diagrams as an abstractionAbstraction
Abstraction is a process by which higher concepts are derived from the usage and classification of literal concepts, first principles, or other methods....
of the underlying infrastructure it represents.
Cloud computing is a natural evolution of the widespread adoption of virtualisation
Hardware virtualization
Computer hardware virtualization is the virtualization of computers or operating systems. It hides the physical characteristics of a computing platform from users, instead showing another abstract computing platform...
, service-oriented architecture
Service-oriented architecture
In software engineering, a Service-Oriented Architecture is a set of principles and methodologies for designing and developing software in the form of interoperable services. These services are well-defined business functionalities that are built as software components that can be reused for...
, autonomic
Autonomic Computing
Autonomic Computing refers to the self-managing characteristics of distributed computing resources, adapting to unpredictable changes whilst hiding intrinsic complexity to operators and users...
, and utility computing. Details are abstracted from end-users, who no longer have need for expertise in, or control over, the technology infrastructure "in the cloud" that supports them.
The underlying concept of cloud computing dates back to the 1960s, when John McCarthy
John McCarthy (computer scientist)
John McCarthy was an American computer scientist and cognitive scientist. He coined the term "artificial intelligence" , invented the Lisp programming language and was highly influential in the early development of AI.McCarthy also influenced other areas of computing such as time sharing systems...
opined that "computation may someday be organised as a public utility
Public utility
A public utility is an organization that maintains the infrastructure for a public service . Public utilities are subject to forms of public control and regulation ranging from local community-based groups to state-wide government monopolies...
." Almost all the modern-day characteristics of cloud computing (elastic provision, provided as a utility, online, illusion of infinite supply), the comparison to the electricity industry and the use of public, private, government, and community forms, were thoroughly explored in Douglas Parkhill
Douglas Parkhill
Douglas F. Parkhill is a Canadian technologist and former research minister, best known for his pioneering work on what is now called cloud computing, and his work on Canada's Telidon videotex project....
's 1966 book, The Challenge of the Computer Utility. Other scholars have shown that cloud computing's roots go all the way back to the 1950s when scientist Herb Grosch
Herb Grosch
Herbert Reuben John Grosch was an early computer scientist, perhaps best known for Grosch's law, which he formulated in 1950. Grosch's Law is an aphorism that states "economy is as the square root of the speed."...
(the author of Grosch's law
Grosch's law
Grosch's law is the following observation about computer performance made by Herb Grosch in 1965:There is a fundamental rule, which I modestly call Grosch's law, giving added economy only as the square root of the increase in speed -- that is, to do a calculation 10 times as cheaply you must do it...
) postulated that the entire world would operate on dumb terminals powered by about 15 large data centers.
The actual term "cloud" borrows from telephony
Telephony
In telecommunications, telephony encompasses the general use of equipment to provide communication over distances, specifically by connecting telephones to each other....
in that telecommunications companies, who until the 1990s offered primarily dedicated point-to-point data circuits, began offering Virtual Private Network
Virtual private network
A virtual private network is a network that uses primarily public telecommunication infrastructure, such as the Internet, to provide remote offices or traveling users access to a central organizational network....
(VPN) services with comparable quality of service but at a much lower cost. By switching traffic to balance utilisation as they saw fit, they were able to utilise their overall network bandwidth more effectively. The cloud symbol was used to denote the demarcation point between that which was the responsibility of the provider and that which was the responsibility of the user. Cloud computing extends this boundary to cover servers as well as the network infrastructure.
After the dot-com bubble
Dot-com bubble
The dot-com bubble was a speculative bubble covering roughly 1995–2000 during which stock markets in industrialized nations saw their equity value rise rapidly from growth in the more...
, Amazon
Amazon.com
Amazon.com, Inc. is a multinational electronic commerce company headquartered in Seattle, Washington, United States. It is the world's largest online retailer. Amazon has separate websites for the following countries: United States, Canada, United Kingdom, Germany, France, Italy, Spain, Japan, and...
played a key role in the development of cloud computing by modernising their data center
Data center
A data center is a facility used to house computer systems and associated components, such as telecommunications and storage systems...
s, which, like most computer networks, were using as little as 10% of their capacity at any one time, just to leave room for occasional spikes. Having found that the new cloud architecture resulted in significant internal efficiency improvements whereby small, fast-moving "two-pizza teams" could add new features faster and more easily, Amazon initiated a new product development effort to provide cloud computing to external customers, and launched Amazon Web Service (AWS)
Amazon Web Services
Amazon Web Services is a collection of remote computing services that together make up a cloud computing platform, offered over the Internet by Amazon.com...
on a utility computing
Utility computing
Utility computing is the packaging of computing resources, such as computation, storage and services, as a metered service similar to a traditional public utility...
basis in 2006.
In early 2008, Eucalyptus
Eucalyptus (computing)
Eucalyptus is a software platform for the implementation of private cloud computing on computer clusters. There is an open-core enterprise edition and an open-source edition. Currently, it exports a user-facing interface that is compatible with the Amazon EC2 and S3 services but the platform is...
became the first open-source, AWS API-compatible platform for deploying private clouds. In early 2008, OpenNebula
OpenNebula
OpenNebula is an open-source cloud computing toolkit for managing heterogeneous distributed data center infrastructures. The OpenNebula toolkit manages a data center's virtual infrastructure to build private, public and hybrid IaaS clouds...
, enhanced in the RESERVOIR European Commission-funded project, became the first open-source software for deploying private and hybrid clouds, and for the federation of clouds. In the same year, efforts were focused on providing QoS guarantees (as required by real-time interactive applications) to cloud-based infrastructures, in the framework of the IRMOS European Commission-funded project, resulting to a real-time cloud environment. By mid-2008, Gartner saw an opportunity for cloud computing "to shape the relationship among consumers of IT services, those who use IT services and those who sell them" and observed that "[o]rganisations are switching from company-owned hardware and software assets to per-use service-based models" so that the "projected shift to cloud computing ... will result in dramatic growth in IT products in some areas and significant reductions in other areas."
Layers
Once an internet protocol connection is established among several computers, it is possible to share services within any one of the following layers.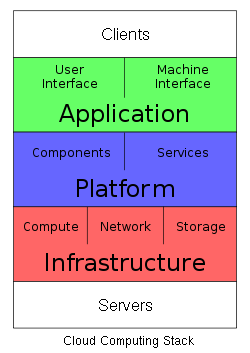
Client
A cloud client consists of computer hardwareComputer hardware
Personal computer hardware are component devices which are typically installed into or peripheral to a computer case to create a personal computer upon which system software is installed including a firmware interface such as a BIOS and an operating system which supports application software that...
and/or computer software
Computer software
Computer software, or just software, is a collection of computer programs and related data that provide the instructions for telling a computer what to do and how to do it....
that relies on cloud computing for application delivery and that is in essence useless without it. Examples include some computers, phones and other devices, operating systems, and browsers.
Application
Cloud application services or "Software as a ServiceSoftware as a Service
Software as a service , sometimes referred to as "on-demand software," is a software delivery model in which software and its associated data are hosted centrally and are typically accessed by users using a thin client, normally using a web browser over the Internet.SaaS has become a common...
(SaaS)" deliver software as a service over the Internet, eliminating the need to install and run the application on the customer's own computers and simplifying maintenance and support.
Platform
Cloud platform services, also known as platform as a servicePlatform as a service
Platform as a service is a category of cloud computing services that provide a computing platform and a solution stack as a service...
(PaaS), deliver a computing platform and/or solution stack
Solution stack
In computing, a solution stack is a set of software subsystems or components needed to deliver a fully functional solution, e.g. a product or service....
as a service, often consuming cloud infrastructure and sustaining cloud applications. It facilitates deployment of applications without the cost and complexity of buying and managing the underlying hardware and software layers. Cloud computing is becoming a major change in our industry, and one of the most important parts of this change is the shift of cloud platforms. Platforms let developers write certain applications that can run in the cloud, or even use services provided by the cloud. There are different names being used for platforms which can include the on-demand platform, or Cloud 9. It's your choice on what you would like to call the platform, but they all have great potential in developing. When development teams create applications for the cloud, they must build its own cloud platform.
Infrastructure
Cloud infrastructure services, also known as "infrastructure as a service" (IaaS), deliver computer infrastructure – typically a platform virtualisation environment – as a service, along with raw (block) storage and networking. Rather than purchasing servers, software, data-center space or network equipment, clients instead buy those resources as a fully outsourced service. Suppliers typically bill such services on a utility computing basis; the amount of resources consumed (and therefore the cost) will typically reflect the level of activity.Server
The servers layer consists of computer hardwareComputer hardware
Personal computer hardware are component devices which are typically installed into or peripheral to a computer case to create a personal computer upon which system software is installed including a firmware interface such as a BIOS and an operating system which supports application software that...
and/or computer software
Computer software
Computer software, or just software, is a collection of computer programs and related data that provide the instructions for telling a computer what to do and how to do it....
products that are specifically designed for the delivery of cloud services, including multi-core processors, cloud-specific operating systems and combined offerings.
Public cloud
A public cloud is one based on the standard cloud computing model, in which a service provider makes resources, such as applications and storage, available to the general public over the Internet. Public cloud services may be free or offered on a pay-per-usage model.Community cloud
Community cloud shares infrastructure between several organizations from a specific community with common concerns (security, compliance, jurisdiction, etc.), whether managed internally or by a third-party and hosted internally or externally. The costs are spread over fewer users than a public cloud (but more than a private cloud), so only some of the benefits of cloud computing are realized.Hybrid cloud
Hybrid cloud is a composition of two or more clouds (private, community, or public) that remain unique entities but are bound together, offering the benefits of multiple deployment models. It can also be defined as multiple cloud systems that are connected in a way that allows programs and data to be moved easily from one deployment system to another.Private cloud
Private cloud is infrastructure operated solely for a single organization, whether managed internally or by a third-party and hosted internally or externally.They have attracted criticism because users "still have to buy, build, and manage them" and thus do not benefit from lower up-front capital costs and less hands-on management,
essentially "[lacking] the economic model that makes cloud computing such an intriguing concept".
Architecture
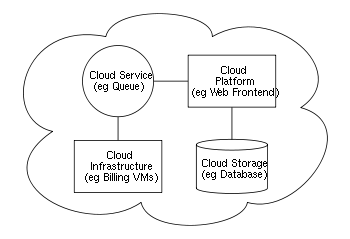
Systems architecture
A system architecture or systems architecture is the conceptual model that defines the structure, behavior, and more views of a system.An architecture description is a formal description and representation of a system, organized in a way that supports reasoning about the structure of the system...
of the software systems involved in the delivery of cloud computing, typically involves multiple cloud components communicating with each other over a loose coupling
Loose coupling
In computing and systems design a loosely coupled system is one where each of its components has, or makes use of, little or no knowledge of the definitions of other separate components. The notion was introduced into organizational studies by Karl Weick...
mechanism such as a messaging queue.
The Intercloud
The Intercloud is an interconnected global "cloud of clouds" and an extension of the InternetInternet
The Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
"network of networks" on which it is based.
Cloud engineering
Cloud engineering is the application of engineeringEngineering
Engineering is the discipline, art, skill and profession of acquiring and applying scientific, mathematical, economic, social, and practical knowledge, in order to design and build structures, machines, devices, systems, materials and processes that safely realize improvements to the lives of...
disciplines to cloud computing. It brings a systematic approach to the high level concerns of commercialisation, standardisation, and governance in conceiving, developing, operating and maintaining cloud computing systems. It is a multidisciplinary method encompassing contributions from diverse areas such as systems
Systems engineering
Systems engineering is an interdisciplinary field of engineering that focuses on how complex engineering projects should be designed and managed over the life cycle of the project. Issues such as logistics, the coordination of different teams, and automatic control of machinery become more...
, software
Software engineering
Software Engineering is the application of a systematic, disciplined, quantifiable approach to the development, operation, and maintenance of software, and the study of these approaches; that is, the application of engineering to software...
, web
Web engineering
The World Wide Web has become a major delivery platform for a variety of complex and sophisticated enterprise applications in several domains. In addition to their inherent multifaceted functionality, these web applications exhibit complex behavior and place some unique demands on their usability,...
, performance
Performance Engineering
Performance engineering within systems engineering, encompasses the set of roles, skills, activities, practices, tools, and deliverables applied at every phase of the Systems Development Life Cycle which ensures that a solution will be designed, implemented, and operationally supported to meet the...
, information
Information engineering
Information engineering or information engineering methodology in software engineering is an approach to designing and developing information systems.-Overview:...
, security
Security engineering
Security engineering is a specialized field of engineering that focuses on the security aspects in the design of systems that need to be able to deal robustly with possible sources of disruption, ranging from natural disasters to malicious acts...
, platform, risk
Risk analysis (engineering)
Risk analysis is the science of risks and their probability and evaluation.Probabilistic risk assessment is one analysis strategy usually employed in science and engineering.-Risk analysis and the risk workshop:...
, and quality
Quality control
Quality control, or QC for short, is a process by which entities review the quality of all factors involved in production. This approach places an emphasis on three aspects:...
engineering.
Privacy
The cloud model has been criticised by privacy advocates for the greater ease in which the companies hosting the cloud services control, thus, can monitor at will, lawfully or unlawfully, the communication and data stored between the user and the host company. Instances such as the secret NSA programRoom 641A
Room 641A is an intercept facility operated by AT&T for the U.S. National Security Agency, beginning in 2003. Room 641A is located in the SBC Communications building at 611 Folsom Street, San Francisco, three floors of which were occupied by AT&T before SBC purchased AT&T...
, working with AT&T
AT&T
AT&T Inc. is an American multinational telecommunications corporation headquartered in Whitacre Tower, Dallas, Texas, United States. It is the largest provider of mobile telephony and fixed telephony in the United States, and is also a provider of broadband and subscription television services...
, and Verizon, which recorded over 10 million phone calls between American citizens, causes uncertainty among privacy advocates, and the greater powers it gives to telecommunication companies to monitor user activity.
While there have been efforts (such as US-EU Safe Harbor) to "harmonise" the legal environment, providers such as Amazon
Amazon Web Services
Amazon Web Services is a collection of remote computing services that together make up a cloud computing platform, offered over the Internet by Amazon.com...
still cater to major markets (typically the United States and the European Union
European Union
The European Union is an economic and political union of 27 independent member states which are located primarily in Europe. The EU traces its origins from the European Coal and Steel Community and the European Economic Community , formed by six countries in 1958...
) by deploying local infrastructure and allowing customers to select "availability zones."
Cloud computing poses privacy concerns basically, because the service provider at any point in time, may access the data that is on the cloud. They could accidentally or deliberately alter or even delete some info.
Compliance
In order to obtain compliance with regulations including FISMA, HIPAA, and SOX in the United States, the Data Protection Directive in the EUEuropean Union
The European Union is an economic and political union of 27 independent member states which are located primarily in Europe. The EU traces its origins from the European Coal and Steel Community and the European Economic Community , formed by six countries in 1958...
and the credit card industry's PCI DSS, users may have to adopt community or hybrid deployment modes that are typically more expensive and may offer restricted benefits. This is how Google
Google
Google Inc. is an American multinational public corporation invested in Internet search, cloud computing, and advertising technologies. Google hosts and develops a number of Internet-based services and products, and generates profit primarily from advertising through its AdWords program...
is able to "manage and meet additional government policy requirements beyond FISMA" and Rackspace Cloud or QubeSpace are able to claim PCI compliance.
Many providers also obtain SAS 70 Type II certification, but this has been criticised on the grounds that the hand-picked set of goals and standards determined by the auditor and the auditee are often not disclosed and can vary widely. Providers typically make this information available on request, under non-disclosure agreement
Non-disclosure agreement
A non-disclosure agreement , also known as a confidentiality agreement , confidential disclosure agreement , proprietary information agreement , or secrecy agreement, is a legal contract between at least two parties that outlines confidential material, knowledge, or information that the parties...
.
Customers in the EU contracting with cloud providers established outside the EU/EEA have to adhere to the EU regulations on export of personal data.
Legal
As can be expected with any revolutionary change in the landscape of global computing, certain legal issues arise; everything from trademark infringement, security concerns to the sharing of propriety data resources.Open source
Open-source softwareOpen-source software
Open-source software is computer software that is available in source code form: the source code and certain other rights normally reserved for copyright holders are provided under a software license that permits users to study, change, improve and at times also to distribute the software.Open...
has provided the foundation for many cloud computing implementations, one prominent example being the Hadoop framework. In November 2007, the Free Software Foundation
Free Software Foundation
The Free Software Foundation is a non-profit corporation founded by Richard Stallman on 4 October 1985 to support the free software movement, a copyleft-based movement which aims to promote the universal freedom to create, distribute and modify computer software...
released the Affero General Public License
Affero General Public License
The Affero General Public License, often abbreviated as Affero GPL and AGPL , refers to two distinct, though historically related, free software licenses:...
, a version of GPLv3
GNU General Public License
The GNU General Public License is the most widely used free software license, originally written by Richard Stallman for the GNU Project....
intended to close a perceived legal loophole
Legal technicality
The term legal technicality is a casual or colloquial phrase referring to a technical aspect of law. The phrase is not a term of art in the law; it has no exact meaning, nor does it have a legal definition. It implies that that strict adherence to the letter of the law has prevented the spirit of...
associated with free software
Free software
Free software, software libre or libre software is software that can be used, studied, and modified without restriction, and which can be copied and redistributed in modified or unmodified form either without restriction, or with restrictions that only ensure that further recipients can also do...
designed to be run over a network.
Open standards
Most cloud providers expose APIsApplication programming interface
An application programming interface is a source code based specification intended to be used as an interface by software components to communicate with each other...
that are typically well-documented (often under a Creative Commons
Creative Commons
Creative Commons is a non-profit organization headquartered in Mountain View, California, United States devoted to expanding the range of creative works available for others to build upon legally and to share. The organization has released several copyright-licenses known as Creative Commons...
license) but also unique to their implementation and thus not interoperable. Some vendors have adopted others' APIs and there are a number of open standards under development, with a view to delivering interoperability and portability.
Security
As cloud computing is achieving increased popularity, concerns are being voiced about the security issues introduced through adoption of this new model. The effectiveness and efficiency of traditional protection mechanisms are being reconsidered as the characteristics of this innovative deployment model differ widely from those of traditional architectures.The relative security of cloud computing services is a contentious issue that may be delaying its adoption. Issues barring the adoption of cloud computing are due in large part to the private and public sectors unease surrounding the external management of security-based services. It is the very nature of cloud computing-based services, private or public, that promote external management of provided services. This delivers great incentive to cloud computing service providers to prioritize building and maintaining strong management of secure services. Security issues have been categorised into sensitive data access, data segregation, privacy, bug exploitation, recovery, accountability, malicious insiders, management console security, account control, and multi-tenancy issues. Solutions to various cloud security issues vary, from cryptography, particularly public key infrastructure (PKI), to use of multiple cloud providers, standardisation of APIs, and improving virtual machine support and legal support.
Sustainability
Although cloud computing is often assumed to be a form of "green computingGreen computing
Green computing or green IT, refers to environmentally sustainable computing or IT. In the article Harnessing Green IT: Principles and Practices, San Murugesan defines the field of green computing as "the study and practice of designing, manufacturing, using, and disposing of computers, servers,...
", there is as of yet no published study to substantiate this assumption. Siting the servers affects the environmental effects of cloud computing. In areas where climate favors natural cooling and renewable electricity is readily available, the environmental effects will be more moderate. (The same holds true for "traditional" data centers.) Thus countries with favorable conditions, such as Finland, Sweden and Switzerland, are trying to attract cloud computing data centers.
Energy efficiency in cloud computing can result from energy-aware scheduling and server consolidation. However, in the case of distributed clouds over data centers with different source of energies including renewable source of energies, a small compromise on energy consumption reduction could result in high carbon footprint reduction.
Abuse
As with privately purchased hardware, crackers posing as legitimate customers can purchase the services of cloud computing for nefarious purposes. This includes password cracking and launching attacks using the purchased services. In 2009, a banking trojanTrojan horse (computing)
A Trojan horse, or Trojan, is software that appears to perform a desirable function for the user prior to run or install, but steals information or harms the system. The term is derived from the Trojan Horse story in Greek mythology.-Malware:A destructive program that masquerades as a benign...
illegally used the popular Amazon service as a command and control channel that issued software updates and malicious instructions to PCs that were infected by the malware.
Research
Many universities, vendors and government organisations are investing in research around the topic of cloud computing:- In October 2007 the Academic Cloud Computing Initiative (ACCI) was announced as a multi-university project designed to enhance students' technical knowledge to address the challenges of cloud computing.
- In July 2011 the High Performance Computing Cloud (HPCCLoud) project was kicked-off aiming at finding out the possibilities of enhancing performance on cloud environments while running the scientific applications - development of HPCCLoud Performance Analysis Toolkit which was funded by CIM-Returning Experts Programme - under the coordination of Prof. Dr. Shajulin Benedict.
- In June 2011 the Telecommunications Industry AssociationTelecommunications Industry AssociationThe Telecommunications Industry Association is accredited by the American National Standards Institute to develop voluntary, consensus-based industry standards for a wide variety of ICT products, and currently represents nearly 400 companies...
developed a Cloud Computing White Paper, to analyze the integration challenges and opportunities between cloud services and traditional U.S. telecommunications standards.
See also
- Cloud computing comparisonCloud computing comparison-General information:-Supported Hosts:-Features:...
- Cloud storageCloud storageCloud storage is a model of networked online storage where data is stored on virtualized pools of storage which are generally hosted by third parties. Hosting companies operate large data centers; and people who require their data to be hosted buy or lease storage capacity from them and use it for...
- Web operating systemWeb operating systemIn metacomputing, WebOS and Web operating system are terms that describe network services for Internet scale distributed computing, as in the WebOS Project at UC Berkeley, and the WOS Project...
- Cloud databaseCloud databaseA cloud database is a database running on Cloud Computing platform, such as Amazon EC2, GoGrid and Rackspace. There are two common deployment models: Users can run databases on the cloud independently, using a Virtual Machine image, or they can purchase access to a database service, maintained by a...
- Mobile Cloud ComputingMobile Cloud ComputingMobile cloud computing is the usage of cloud computing in combination with mobile devices.Cloud computing exists if tasks and data are kept on the internet rather than on individual devices, providing on-demand access....

