Clandestine cell system
Encyclopedia
A clandestine cell structure is a method for organizing a group of people in such a way that it can more effectively resist penetration by an opposing organization. Depending on the group's philosophy
, its operational area, the communications technologies available, and the nature of the mission, it can range from a strict hierarchy to an extremely distributed organization. It is also a method used by criminal organizations
, undercover
operatives, and unconventional warfare (UW) led by special forces
.
Cell structures continue to evolve. Historically, clandestine organizations avoided electronic communications, because signals intelligence, SIGINT, is a strength of conventional militaries and counterintelligence organizations. New communications techniques, such as the Internet and strong encryption, may allow some inter-cell communications that were too dangerous in the past.
In the context of tradecraft
, covert
and clandestine
are not synonymous. The adversary is aware that a covert activity is happening, but does not know who is doing it, and certainly not their sponsorship. Clandestine activities, however, if successful, are completely unknown to the adversary, and their function, such as espionage, would be neutralized if there was any awareness of the activity. A covert cell structure is tantamount to a contradiction in terms, because the point of the cell structure is that its details are completely hidden from the opposition.
A sleeper cell refers to a cell, or isolated grouping of sleeper agent
s that lies dormant until it receives orders or decides to act.
, the modern Provisional Irish Republican Army
(PIRA) has a history going back to Irish revolutionary forces in the early 20th century, but has little external control. Its doctrine and organization have changed over time, given factors such as the independence of 26 of Ireland's 32 counties, the continued British control of Northern Ireland and the simple passage of time and changes in contemporary thinking and technology.
Officially, the PIRA is hierarchical, but, especially as British security forces became more effective, changed to a semiautonomous model for its operational and certain of its support cells (e.g., transportation, intelligence, cover and security). Its leadership sees itself as guiding and consensus-building. The lowest-level cells, typically of 2-5 people, tend to be built by people with an existing personal relationship. British counterinsurgents could fairly easily understand the command structure, but not the workings of the operational cells.
The IRA has an extensive network of inactive or sleeper cells, so new ad hoc organizations may appear for any specific operation.
teams parachuted into occupied France to lead unconventional warfare units. They would be composed of two officers, one American or British, and the other French, the latter preferably from the area into which they landed. The third member of the team was a radio operator.
Especially through the French member, they would contact trusted individuals in the area of operation, and ask them to recruit a team of trusted subordinates (i.e., a subcell). If the team mission were sabotage, reconnaissance, or espionage, there was no need to meet in large units. If the team was to carry out direct action, often an unwise mission unless an appreciable number of the locals had military experience, it would be necessary to assemble into units for combat. Even then, the hideouts of the leadership were known only to subcell leaders. The legitimacy of the Jedburgh team came from its known affiliation with Allied powers, and it was a structure more appropriate for UW than for truly clandestine operations.
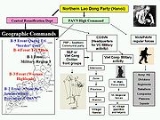
Its command, control, and communication techniques derived from the experiences of these earlier insurgent groups. The group had extensive support from North Vietnam, and, indirectly, from the Soviet Union. It had parallel political and military structures, often overlapping. See Viet Cong and PAVN strategy and tactics.
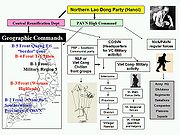 The lowest level consisted of three-person cells who operated quite closely, and engaging in the sort of self-criticism
The lowest level consisted of three-person cells who operated quite closely, and engaging in the sort of self-criticism
common, as a bonding method, to Communist organizations.
. After the war ended, surviving NLF officials held high office.
In the case of the PIRA, its political wing, Sinn Féin
, became increasingly overt, and then a full participant in politics. Hamas
and Hezbollah also have variants of overt political/social service and covert military wings.
The overt political-covert military split avoided the inflexibility of a completely secret organization. Once an active insurgency began, the secrecy could limited freedom of action, distort information about goals and ideals, and restrict communication within the insurgency. In a split organization the public issues can be addressed overtly, while military actions were kept covert and intelligence functions stay clandestine.
External support need not be overt. Certain Shi'a groups in Iraq, for example, do receive assistance from Iran, but this is not a public position of the government of Iran, and may even be limited to factions of that government. Early US support to the Afghan Northern Alliance against the Taliban used clandestine operators from both the CIA and United States Army Special Forces
. As the latter conflict escalated, the US participation became overt.
Note that both unconventional warfare
(UW) (i.e., guerilla operations) and foreign internal defense
(FID) (i.e., counterinsurgency) may be covert and use cellular organization.
In a covert FID mission, only selected host nation (HN) leaders are aware of the foreign support organization. Under Operation White Star
, US personnel gave covert FID assistance to the Royal Lao Army starting in 1959, became overt in 1961, and ceased operations in 1962.
did not run on a cell model.
When considering where cells exist with respect to the existing government, the type of insurgency needs to be considered. One US Army reference was Field Manual 100-20, which has been superseded by FM3-07. Drawing on this work, Nyberg (a United States Marine Corps
officer) extended the ideas to describe four types of cell system, although his descriptions also encompass types of insurgencies that the cell system supports. At present, there is a new type associated with transnational terrorist insurgencies.
, sabotage
, or the organization for unconventional warfare
. When unconventional warfare starts using overt units, the cell system tends to be used only for sensitive leadership and intelligence roles. The examples here will use CIA cryptonym
s as a naming convention used to identify members of the cell system. Cryptonyms begin with a two-letter country or subject name (e.g., AL), followed with an arbitrary word. It is considered elegant to have the code merge with the other letters to form a pronounceable word.
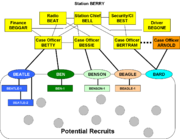 Some recruits, due to the sensitivity of their position or their personalities not being appropriate for cell leadership, might not enter cells but be run as singletons, perhaps by other than the recruiting case officer. Asset BARD is a different sort of highly sensitive singleton, who is a joint asset of the country B, and the country identified by prefix AR. ARNOLD is a case officer from the country AR embassy, who knows only the case officer BERTRAM and the security officer BEST. ARNOLD does not know the station chief of BERRY or any of its other personnel. Other than BELL and BEST, the Station personnel only know BERTRAM as someone authorized to be in the Station, and who is known for his piano playing at embassy parties. He is covered as Cultural Attache, in a country that has very few pianos. Only the personnel involved with BARD know that ARNOLD is other than another friendly diplomat.
Some recruits, due to the sensitivity of their position or their personalities not being appropriate for cell leadership, might not enter cells but be run as singletons, perhaps by other than the recruiting case officer. Asset BARD is a different sort of highly sensitive singleton, who is a joint asset of the country B, and the country identified by prefix AR. ARNOLD is a case officer from the country AR embassy, who knows only the case officer BERTRAM and the security officer BEST. ARNOLD does not know the station chief of BERRY or any of its other personnel. Other than BELL and BEST, the Station personnel only know BERTRAM as someone authorized to be in the Station, and who is known for his piano playing at embassy parties. He is covered as Cultural Attache, in a country that has very few pianos. Only the personnel involved with BARD know that ARNOLD is other than another friendly diplomat.
In contrast, BESSIE and BETTY know one another, and procedures exist for their taking over each others' assets in the event one of the two is disabled.
Some recruits, however, would be qualified to recruit their own subcell, as BEATLE has done. BESSIE knows the identity of BEATLE-1 and BEATLE-2, since he had them checked by headquarters counterintelligence before they were recruited. Note that a cryptonym does not imply anything about its designee, such as gender.
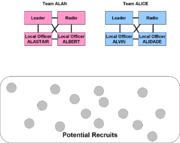 Assume that in team ALAN, ALISTAIR is one of the officers with local contacts, might recruit two cell leaders, ALPINE and ALTITUDE. The other local officer in the team, ALBERT, recruits ALLOVER. When ALPINE recruited two subcell members, they would be referred to as ALPINE-1 and ALPINE-2.
Assume that in team ALAN, ALISTAIR is one of the officers with local contacts, might recruit two cell leaders, ALPINE and ALTITUDE. The other local officer in the team, ALBERT, recruits ALLOVER. When ALPINE recruited two subcell members, they would be referred to as ALPINE-1 and ALPINE-2.
ALPINE and ALTITUDE only know how to reach ALISTAIR, but they are aware of at least some of other team members' identity should ALISTAIR be unavailable, and they would accept a message from ALBERT. Most often, the identity (and location) of the radio operator may not be shared. ALPINE and ALTITUDE, however, do not know one another. They do not know any of the members of team ALICE.
The legitimacy of the subcell structure came from the recruitment process, originally by the case officer and then by the cell leaders. Sometimes, the cell leader would propose subcell member names to the case officer, so the case officer could have a headquarters name check run before bringing the individual into the subcell. In principle, however, the subcell members would know ALPINE, and sometimes the other members of the ALPINE cell if they needed to work together; if ALPINE-1 and ALPINE-2 had independent assignments, they might not know each other. ALPINE-1 and ALPINE-2 certainly would not know ALISTAIR or anyone in the ALTITUDE or ALLOVER cells.
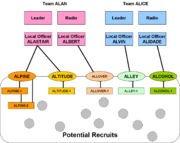 As the networks grow, a subcell leader might create his own cell, so ALPINE-2 might become the leader of the ALIMONY cell.
As the networks grow, a subcell leader might create his own cell, so ALPINE-2 might become the leader of the ALIMONY cell.
If a traditional cell had independent communications with the foreign support organization, headquarters might be able to arrange its reconnection. Another method is to have impersonal communications "side links" between cells, such as a pair of dead drop
s, one for Team ALAN to leave "lost contact" messages to be retrieved by Team ALICE, and another dead drop for Team ALICE to leave messages for Team ALAN.
These links, to be used only on losing contact, do not guarantee a contact. When a team finds a message in its emergency drop, it might do no more than send an alert message to headquarters. Headquarters might determine, through SIGINT
or other sources, that the enemy had captured the leadership and the entire team, and order the other team not to attempt contact. If headquarters can have reasonable confidence that there is a communications failure or partial compromise, it might send a new contact to the survivors.
When the cut-off team has electronic communications, such as the Internet, it has a much better chance of eluding surveillance and getting emergency instructions than by using a dead drop that can be under physical surveillance.
"Such networks function by having their sub-networks provide information and other forms of support (the ‘many-to-one’ model), while the core group supplies ‘truth’ and decisions/directions (the ‘one-to-many’ model). Trust and personal relationships are an essential part of the Al-Qaida network (a limiting factor, even while it provides enhanced security). Even while cell members are trained as ‘replaceable’ units, ‘vetting’ of members occurs during the invited training period under the observation of the core group.
Cells of this structure are built outwards, from an internal leadership core. Superficially, this might be likened to a Western cell structure that emanates from a headquarters, but the Western centrality is bureaucratic, while structures in other non-western cultures builds on close personal relationships, often built over years, perhaps involving family or other in-group linkages. Such in-groups are thus extremely hard to infiltrate; infiltration has a serious chance only outside the in-group. Still, it may be possible for an in-group to be compromised through COMINT or, in rare cases, by compromising a member.
The core group is logically a ring, but is superimposed on an inner hub-and-spoke structure of ideological authority. Each member of the core forms another hub and spoke system (see infrastructure cells, the spokes leading to infrastructure cells under the supervision of the core group member, and possibly to operational groups which the headquarters support. Note that in this organization, there is a point at which the operational cell becomes autonomous of the core. Members surviving the operation may rejoin at various points.
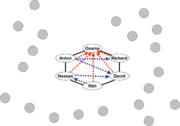 Osama, in this model, has the main responsibility of commanding the organization and being the spokesman on propaganda video and audio messages distributed by the propaganda cell. The other members of the core each command one or more infrastructure cells.
Osama, in this model, has the main responsibility of commanding the organization and being the spokesman on propaganda video and audio messages distributed by the propaganda cell. The other members of the core each command one or more infrastructure cells.
While the tight coupling enhances security, it can limit flexibility and the ability to scale the organization. This in-group, while sharing tight cultural and ideological values, is not committed to a bureaucratic process.
"Members of the core group are under what could be termed ‘positive control’—long relationships
and similar mindsets make ‘control’ not so much of an issue, but there are distinct roles, and position (structural, financial, spiritual in the sense of having the ‘correct’ interpretation of Islam) determines authority, thus making the core group a hierarchy topologically.
In the first example of the core, each member knows how to reach two other members, and also knows the member(s) he considers his ideological superior. Solid lines show basic communication, dotted red arrows show the first level of ideological respect, and dotted blue arrows show a second level of ideological respect.
If Osama, the most respected, died, the core would reconstitute itself. While different members have an individual ideological guide, and these are not the same for all members, the core would reconstitute itself with Richard as most respected.
Assume there are no losses, and Osama can be reached directly only by members of the core group. Members of outer cells and support systems might know him only as "the Commander", or, as in the actual case of al-Qaeda, Osama bin Laden's face is recognizable worldwide, but only a very few people know where he is or even how to contact it.
Other functions include psychological operations, training, and finance.
A national intelligence service
has a support organization to deal with services such as finance, logistics, facilities (e.g., safehouses), information technology, communications, training, weapons and explosives, medical services, etc. Transportation alone is a huge function, including the need to buy tickets without drawing suspicion, and, where appropriate, using private vehicles. Finance includes the need to transfer money without coming under the suspicion of financial security organizations.
Some of these functions, such as finance, are far harder to operate in remote areas such as the FATA
of Pakistan
, than in cities with large numbers of official and unofficial financial institutions, and the communications to support them. If the financial office is distant from the remote headquarters, there is a need for couriers, who must be trusted to some extent, although they may not know the contents of their messages, or the actual identity of sender and/or receiver. The couriers, depending on the balance among type and size of message, security, and technology available, may memorize messages, carry audio or video recordings, or hand-carry computer media.
 "These cells are socially embedded (less so than the core group, however), structurally embedded, functionally embedded (they are specialized into a domain), and knowledge base-specific (there does not seem to be a great deal of cross-training, or lateral mobility in the organization). Such cells are probably subjected to a mixture of positive and negative control ("do this, do these sorts of things, don’t do that")."
"These cells are socially embedded (less so than the core group, however), structurally embedded, functionally embedded (they are specialized into a domain), and knowledge base-specific (there does not seem to be a great deal of cross-training, or lateral mobility in the organization). Such cells are probably subjected to a mixture of positive and negative control ("do this, do these sorts of things, don’t do that")."
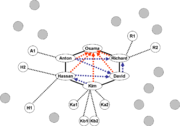
Core Structure of Non-National Group >
Member
Infrastructure commanded
Richard
Finance
Anton
Military training/operations 1
Hassan
Military training/operations 2
David
Transportation
Kim
Communications and propaganda
The leaders of military cells are responsible for training them, and, when an operation is scheduled, selecting the operational commander, giving him the basic objective and arranging whatever support is needed, and then release him from tight control to execute the meeting. Depending on the specific case, the military leaders might have direct, possibly one-way, communications with their cells, or they might have to give Kim the messages to be transmitted, by means that Anton and Hassan have no need to know.
Note that Anton does not have a direct connection to Kim. Under normal circumstances, he sacrifices efficiency for security, by passing communications requests through Anton. The security structure also means that Hassan does not know the members of Anton's cells, and Kim may only know ways to communicate with them, but not their identity.
Kim operates two systems of cells, one for secure communications and one for propaganda. To send out a propaganda message, Osama must pass it to Kim. If Kim were compromised, the core group might have significant problems with any sort of outside communications.
Terrorist networks do not match cleanly to other cell systems that regularly report to a headquarters. The apparent al-Qaeda methodology of letting operational cells decide on their final dates and means of attack exhibit an operational pattern, but not a periodicity that could easily be used for an indications checklist appropriate for a warning center. Such lists depend on seeing a local pattern to give a specific warning..
Note that Hassan has two subordinates that have not yet established operational cells. These subordinates can be considered sleepers, but not necessarily with a sleeper cell.
"Operational cells are not created, but instead ‘seeded’ utilizing individuals spotted or that request assistance (both groups are ‘vetted’ by being trained under the observation of the core group, which dramatically restricts the opportunity for passing off walk-ins under false flag). Categorization of operational cells appears to be by capabilities, region, and then task/operation. Operational cells are composed of members whose worldview has been firmly tested—necessary to front-load, because such cells are dispersed back to their own local control (or negative control—proscribed behavior—with positive control only coming in the form of contact for synchronization or support)."
If operational cells routinely are "released" curved dotted lines on link to military cells to select their final operational parameters, they use a different paradigm than governmental clandestine or covert operations. On a number of cases, US special operations forces had to wait for Presidential authorization to make an attack, or even move to staging areas. Admittedly, a country would have to face the consequences of an inappropriate attack, so it may tend to be overcautious, where a terror network would merely shrug at the world being upset. Assuming that the al-Qaeda operational technique is not to use positive control, their operations may be more random, but also more unpredictable for counterterror forces. If their cells truly need constant control, there are communications links that might be detected by SIGINT, and if their command can be disrupted, the field units could not function. Since there is fairly little downside for terrorists to attack out of synchronization with other activities, the lack of positive control becomes a strength of their approach to cell organization.
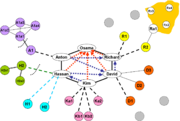 The operational cells need to have continuous internal communication; there is a commander, who may be in touch with infrastructure cells or, less likely from a security standpoint with the core group.
The operational cells need to have continuous internal communication; there is a commander, who may be in touch with infrastructure cells or, less likely from a security standpoint with the core group.
Al-Qaeda's approach, which even differs from that of earlier terrorist organizations, may be very viable for their goals:
"While Al-Qaida has elements of the organization designed to support the structure, but such elements are insufficient in meeting the needs of such an organization, and for security reasons there would be redundant and secondary-/tertiary-networks that are unaware of their connection to Al-Qaida. These networks, primarily related to fundraising and financial activities, as well as technology providers, are in a ‘use’ relationship with Al-Qaida—managed through cut-outs or individuals that do not inform them of the nature of activities, and that may have a cover pretext sufficient to deflect questions or inquiry."
Writing in the U.S. Army journal Military Review, David W. Pendall suggested that a "catch-and-release program for suspected operatives might create reluctance or distrust in such suspects and prevent them from further acts or, perhaps more important, create distrust in the cell leaders of these individuals in the future." The author noted the press release describing Ramzi Binalshib's cooperation with the United States "are sure to prevent reentry into a terrorist cell as a trusted member and most likely limits the further trust and assignments of close cell associates still at large. The captor would determine when to name names and when to remain silent." Indeed, once intelligence learns the name and characteristics of an at-large adversary, as well as some sensitive information that would plausibly be known to him, a news release could be issued to talk about his cooperation. Such a method could not be used too often, but, used carefully, could disturb the critical trust networks. The greatest uncertainty might be associated with throwing doubt onto a key member of an operational cell that has gone autonomous.
Philosophy
Philosophy is the study of general and fundamental problems, such as those connected with existence, knowledge, values, reason, mind, and language. Philosophy is distinguished from other ways of addressing such problems by its critical, generally systematic approach and its reliance on rational...
, its operational area, the communications technologies available, and the nature of the mission, it can range from a strict hierarchy to an extremely distributed organization. It is also a method used by criminal organizations
Organized crime
Organized crime or criminal organizations are transnational, national, or local groupings of highly centralized enterprises run by criminals for the purpose of engaging in illegal activity, most commonly for monetary profit. Some criminal organizations, such as terrorist organizations, are...
, undercover
Undercover
Being undercover is disguising one's own identity or using an assumed identity for the purposes of gaining the trust of an individual or organization to learn secret information or to gain the trust of targeted individuals in order to gain information or evidence...
operatives, and unconventional warfare (UW) led by special forces
Special forces
Special forces, or special operations forces are terms used to describe elite military tactical teams trained to perform high-risk dangerous missions that conventional units cannot perform...
.
Cell structures continue to evolve. Historically, clandestine organizations avoided electronic communications, because signals intelligence, SIGINT, is a strength of conventional militaries and counterintelligence organizations. New communications techniques, such as the Internet and strong encryption, may allow some inter-cell communications that were too dangerous in the past.
In the context of tradecraft
Tradecraft
Tradecraft is a general term that denotes a skill acquired through experience in a trade.The term is also used within the intelligence community as a collective word for the techniques used in modern espionage...
, covert
Covert operation
A covert operation is a military, intelligence or law enforcement operation that is carried clandestinely and, often, outside of official channels. Covert operations aim to fulfill their mission objectives without any parties knowing who sponsored or carried out the operation...
and clandestine
Clandestine operation
A clandestine operation is an intelligence or military operation carried out in such a way that the operation goes unnoticed.The United States Department of Defense Dictionary of Military and Associated Terms defines "clandestine operation" as "An operation sponsored or conducted by governmental...
are not synonymous. The adversary is aware that a covert activity is happening, but does not know who is doing it, and certainly not their sponsorship. Clandestine activities, however, if successful, are completely unknown to the adversary, and their function, such as espionage, would be neutralized if there was any awareness of the activity. A covert cell structure is tantamount to a contradiction in terms, because the point of the cell structure is that its details are completely hidden from the opposition.
A sleeper cell refers to a cell, or isolated grouping of sleeper agent
Sleeper agent
A sleeper agent is a spy who is placed in a target country or organization, not to undertake an immediate mission, but rather to act as a potential asset if activated...
s that lies dormant until it receives orders or decides to act.
Provisional Irish Republican Army
As opposed to the French ResistanceFrench Resistance
The French Resistance is the name used to denote the collection of French resistance movements that fought against the Nazi German occupation of France and against the collaborationist Vichy régime during World War II...
, the modern Provisional Irish Republican Army
Provisional Irish Republican Army
The Provisional Irish Republican Army is an Irish republican paramilitary organisation whose aim was to remove Northern Ireland from the United Kingdom and bring about a socialist republic within a united Ireland by force of arms and political persuasion...
(PIRA) has a history going back to Irish revolutionary forces in the early 20th century, but has little external control. Its doctrine and organization have changed over time, given factors such as the independence of 26 of Ireland's 32 counties, the continued British control of Northern Ireland and the simple passage of time and changes in contemporary thinking and technology.
Officially, the PIRA is hierarchical, but, especially as British security forces became more effective, changed to a semiautonomous model for its operational and certain of its support cells (e.g., transportation, intelligence, cover and security). Its leadership sees itself as guiding and consensus-building. The lowest-level cells, typically of 2-5 people, tend to be built by people with an existing personal relationship. British counterinsurgents could fairly easily understand the command structure, but not the workings of the operational cells.
The IRA has an extensive network of inactive or sleeper cells, so new ad hoc organizations may appear for any specific operation.
World War II French Resistance
In World War II, Operation JedburghOperation Jedburgh
Operation Jedburgh was a clandestine operation during World War II, in which personnel of the British Special Operations Executive, the U.S...
teams parachuted into occupied France to lead unconventional warfare units. They would be composed of two officers, one American or British, and the other French, the latter preferably from the area into which they landed. The third member of the team was a radio operator.
Especially through the French member, they would contact trusted individuals in the area of operation, and ask them to recruit a team of trusted subordinates (i.e., a subcell). If the team mission were sabotage, reconnaissance, or espionage, there was no need to meet in large units. If the team was to carry out direct action, often an unwise mission unless an appreciable number of the locals had military experience, it would be necessary to assemble into units for combat. Even then, the hideouts of the leadership were known only to subcell leaders. The legitimacy of the Jedburgh team came from its known affiliation with Allied powers, and it was a structure more appropriate for UW than for truly clandestine operations.
National Front for the Liberation of South Vietnam
Also known as the Viet Cong, this organization grew from earlier anticolonial groups fighting the French, as well as anti-Japanese guerillas during World War II.Its command, control, and communication techniques derived from the experiences of these earlier insurgent groups. The group had extensive support from North Vietnam, and, indirectly, from the Soviet Union. It had parallel political and military structures, often overlapping. See Viet Cong and PAVN strategy and tactics.

Self-criticism
Self-criticism refers to the pointing out of things critical/important to one's own beliefs, thoughts, actions, behaviour or results; it can form part of private, personal reflection or a group discussion.-Philosophy:...
common, as a bonding method, to Communist organizations.
Parallel organizations
The NLF and PIRA, as well as other movements, have chosen to have parallel political and military organizations. In the case of the NLF, other than some individuals with sanctuary in North Vietnam, the political organization could not be overt during the Vietnam WarVietnam War
The Vietnam War was a Cold War-era military conflict that occurred in Vietnam, Laos, and Cambodia from 1 November 1955 to the fall of Saigon on 30 April 1975. This war followed the First Indochina War and was fought between North Vietnam, supported by its communist allies, and the government of...
. After the war ended, surviving NLF officials held high office.
In the case of the PIRA, its political wing, Sinn Féin
Sinn Féin
Sinn Féin is a left wing, Irish republican political party in Ireland. The name is Irish for "ourselves" or "we ourselves", although it is frequently mistranslated as "ourselves alone". Originating in the Sinn Féin organisation founded in 1905 by Arthur Griffith, it took its current form in 1970...
, became increasingly overt, and then a full participant in politics. Hamas
Hamas
Hamas is the Palestinian Sunni Islamic or Islamist political party that governs the Gaza Strip. Hamas also has a military wing, the Izz ad-Din al-Qassam Brigades...
and Hezbollah also have variants of overt political/social service and covert military wings.
The overt political-covert military split avoided the inflexibility of a completely secret organization. Once an active insurgency began, the secrecy could limited freedom of action, distort information about goals and ideals, and restrict communication within the insurgency. In a split organization the public issues can be addressed overtly, while military actions were kept covert and intelligence functions stay clandestine.
External support
Many cell systems still receive, with due attention to security, support from the outside. This can range from leaders, trainers and supplies (e.g., the Jedburgh assistance to the French Resistance), or a safe haven for overt activities (e.g., NLF spokesmen in Hanoi).External support need not be overt. Certain Shi'a groups in Iraq, for example, do receive assistance from Iran, but this is not a public position of the government of Iran, and may even be limited to factions of that government. Early US support to the Afghan Northern Alliance against the Taliban used clandestine operators from both the CIA and United States Army Special Forces
United States Army Special Forces
The United States Army Special Forces, also known as the Green Berets because of their distinctive service headgear, are a special operations force tasked with six primary missions: unconventional warfare, foreign internal defense, special reconnaissance, direct action, hostage rescue, and...
. As the latter conflict escalated, the US participation became overt.
Note that both unconventional warfare
Unconventional warfare
Unconventional warfare is the opposite of conventional warfare. Where conventional warfare is used to reduce an opponent's military capability, unconventional warfare is an attempt to achieve military victory through acquiescence, capitulation, or clandestine support for one side of an existing...
(UW) (i.e., guerilla operations) and foreign internal defense
Foreign internal defense
Foreign internal defense is a term used by a number of Western militaries, including the United States, France and the United Kingdom, to describe an approach to combating actual or threatened insurgency in a foreign state called the Host Nation . The term counter-insurgency is more commonly used...
(FID) (i.e., counterinsurgency) may be covert and use cellular organization.
In a covert FID mission, only selected host nation (HN) leaders are aware of the foreign support organization. Under Operation White Star
Operation White Star
Operation White Star was the code name for a United States military advisory mission to Laos during the first years of the Second Indochina War, which would eventually become known in the United States as the Vietnam War...
, US personnel gave covert FID assistance to the Royal Lao Army starting in 1959, became overt in 1961, and ceased operations in 1962.
Models of insurgency and associated cell characteristics
While different kinds of insurgency differ in where they place clandestine or covert cells, when certain types of insurgency grow in power, the cell system is deemphasized. Cells still may be used for leadership security, but, if overt violence by organized units becomes significant, cells are less important. In Mao's three-stage doctrine, cells are still useful in Phase II to give cover to part-time guerillas, but, as the insurgency creates full-time military units in Phase III, the main units are the focus, not the cells. The Eighth Route ArmyEighth Route Army
The Eighth Route Army was the larger of the two major Chinese communist forces that formed a unit of the National Revolutionary Army of the Republic of China which fought the Japanese from 1937 to 1945. In contrast to most of the National Revolutionary Army, it was controlled by the Communist...
did not run on a cell model.
When considering where cells exist with respect to the existing government, the type of insurgency needs to be considered. One US Army reference was Field Manual 100-20, which has been superseded by FM3-07. Drawing on this work, Nyberg (a United States Marine Corps
United States Marine Corps
The United States Marine Corps is a branch of the United States Armed Forces responsible for providing power projection from the sea, using the mobility of the United States Navy to deliver combined-arms task forces rapidly. It is one of seven uniformed services of the United States...
officer) extended the ideas to describe four types of cell system, although his descriptions also encompass types of insurgencies that the cell system supports. At present, there is a new type associated with transnational terrorist insurgencies.
- Traditional: the slowest to form, this reflects a principally indigenous insurgency, initially with limited goals. It is more secure than others, as it tends to grow from people with social, cultural or family ties. The insurgents resent a government that has failed to recognize tribal, racial, religious or linguistic groups "who perceive that the government has denied their rights and interests and work to establish or restore them. They seldom seek to overthrow the government or control the whole society; however, they frequently attempt to withdraw from government control through autonomy or semiautonomy." The Mujahideen in Afghanistan, the Liberation Tigers of Tamil EelamLiberation Tigers of Tamil EelamThe Liberation Tigers of Tamil Eelam was a separatist militant organization formerly based in northern Sri Lanka. Founded in May 1976 by Vellupillai Prabhakaran, it waged a violent secessionist and nationalist campaign to create an independent state in the north and east of Sri Lanka for Tamil...
in Sri Lanka, and the Kurdish revolt in Iraq illustrate the traditional pattern of insurgency. al-Qaeda generally operates in this mode, but if they become strong enough in a given area, they may change to the mass-oriented form. - Subversive: Usually driven by an organization that contains at least some of the governing elite, some being sympathizers already in place, and others who penetrate the government. When they use violence, it has a specific purpose, such as coercing voters, intimidating officials, and disrupting and discrediting the government. Typically, there is a political arm (e.g., Sinn FéinSinn FéinSinn Féin is a left wing, Irish republican political party in Ireland. The name is Irish for "ourselves" or "we ourselves", although it is frequently mistranslated as "ourselves alone". Originating in the Sinn Féin organisation founded in 1905 by Arthur Griffith, it took its current form in 1970...
or the National Liberation Front) that directs the military in planning carefully coordinated violence. "Employment of violence is designed to show the system to be incompetent and to provoke the government to an excessively violent response which further undermines its legitimacy." The Nazi rise to power, in the 1930s, is an example of subversion. Nazi members of parliament and street fighters were hardly clandestine, but the overall plan of the Nazi leadership to gain control of the nation was hidden. "A subversive insurgency is suited to a more permissive political environment which allows the insurgents to use both legal and illegal methods to accomplish their goals. Effective government resistance may convert this to a critical-cell model. - Critical-cell: Critical cell is useful when the political climate becomes less permissive than one that allowed shadow cells. While other cell types try to form intelligence cells within the government, this type sets up "shadow governmentShadow governmentShadow government may refer to:*An opposition government in a parliamentary system, see Shadow Cabinet*A term for plans for an emergency government that takes over in the event of a disaster, see continuity of government...
" cells that can seize power once the system is destroyed both by external means and the internal subversion. This model fits the classic coup d'etatCoup d'étatA coup d'état state, literally: strike/blow of state)—also known as a coup, putsch, and overthrow—is the sudden, extrajudicial deposition of a government, usually by a small group of the existing state establishment—typically the military—to replace the deposed government with another body; either...
, and often tries to minimize violence. Variants include the Sandinista takeover of an existing government weakened by external popular revolution. "Insurgents also seek to infiltrate the government's institutions, but their object is to destroy the system from within." Clandestine cells form inside the government. "The use of violence remains covert until the government is so weakened that the insurgency's superior organization seizes power, supported by the armed force. One variation of this pattern is when the insurgent leadership permits the popular revolution to destroy the existing government, then emerges to direct the formation of a new government. Another variation is seen in the CubaCubaThe Republic of Cuba is an island nation in the Caribbean. The nation of Cuba consists of the main island of Cuba, the Isla de la Juventud, and several archipelagos. Havana is the largest city in Cuba and the country's capital. Santiago de Cuba is the second largest city...
n revolution and is referred to as the foco (or Cuban model) insurgency. This model involves a single, armed cell which emerges in the midst of degenerating government legitimacy and becomes the nucleus around which mass popular support rallies. The insurgents use this support to establish control and erect new institutions." - Mass-oriented: where the subversive and covert-cell systems work from within the government, the mass-oriented builds a government completely outside the existing one, with the intention of replacing it. Such "insurgents patiently construct a base of passive and active political supporters, while simultaneously building a large armed element of guerrilla and regular forces. They plan a protracted campaign of increasing violence to destroy the government and its institutions from the outside. They have a well-developed ideology and carefully determine their objectives. They are highly organized and effectively use propaganda and guerrilla action to mobilize forces for a direct political and military challenge to the government." The revolution that produced the Peoples' Republic of China, the American RevolutionAmerican RevolutionThe American Revolution was the political upheaval during the last half of the 18th century in which thirteen colonies in North America joined together to break free from the British Empire, combining to become the United States of America...
, and the Shining PathShining PathShining Path is a Maoist guerrilla terrorist organization in Peru. The group never refers to itself as "Shining Path", and as several other Peruvian groups, prefers to be called the "Communist Party of Peru" or "PCP-SL" in short...
insurgency in Peru are examples of the mass-oriented model. Once established, this type of insurgency is extremely difficult to defeat because of its great depth of organization.
Classic models for cell system operations
Different kinds of cell organizations have been used for different purposes. This section focuses on clandestine cells, as would be used for espionageEspionage
Espionage or spying involves an individual obtaining information that is considered secret or confidential without the permission of the holder of the information. Espionage is inherently clandestine, lest the legitimate holder of the information change plans or take other countermeasures once it...
, sabotage
Sabotage
Sabotage is a deliberate action aimed at weakening another entity through subversion, obstruction, disruption, or destruction. In a workplace setting, sabotage is the conscious withdrawal of efficiency generally directed at causing some change in workplace conditions. One who engages in sabotage is...
, or the organization for unconventional warfare
Unconventional warfare
Unconventional warfare is the opposite of conventional warfare. Where conventional warfare is used to reduce an opponent's military capability, unconventional warfare is an attempt to achieve military victory through acquiescence, capitulation, or clandestine support for one side of an existing...
. When unconventional warfare starts using overt units, the cell system tends to be used only for sensitive leadership and intelligence roles. The examples here will use CIA cryptonym
CIA cryptonym
CIA cryptonyms are code names or code words used by the U.S. Central Intelligence Agency to reference projects, operations, persons, agencies, etc. The cryptonyms as described in this article were in use at least from the 1950s to the 1980s...
s as a naming convention used to identify members of the cell system. Cryptonyms begin with a two-letter country or subject name (e.g., AL), followed with an arbitrary word. It is considered elegant to have the code merge with the other letters to form a pronounceable word.
Operations under official cover
Station BERRY operates, for country B, in target country BE. It has three case officers and several support officers. Espionage operation run by case officers under diplomatic cover, they would have to with the basic recruiting methods described in this article. Case officer BETTY runs the local agents BEN and BEATLE. Case officer BESSIE runs BENSON and BEAGLE.
In contrast, BESSIE and BETTY know one another, and procedures exist for their taking over each others' assets in the event one of the two is disabled.
Some recruits, however, would be qualified to recruit their own subcell, as BEATLE has done. BESSIE knows the identity of BEATLE-1 and BEATLE-2, since he had them checked by headquarters counterintelligence before they were recruited. Note that a cryptonym does not imply anything about its designee, such as gender.
Clandestine presence
The diagram of "initial team presence" shows that two teams, ALAN and ALICE, have successfully entered an area of operation, the country coded AL, but are only aware of a pool of potential recruits, and have not yet actually recruited anyone. They communicate with one another only through headquarters, so compromise of one team will not affect the other.
ALPINE and ALTITUDE only know how to reach ALISTAIR, but they are aware of at least some of other team members' identity should ALISTAIR be unavailable, and they would accept a message from ALBERT. Most often, the identity (and location) of the radio operator may not be shared. ALPINE and ALTITUDE, however, do not know one another. They do not know any of the members of team ALICE.
The legitimacy of the subcell structure came from the recruitment process, originally by the case officer and then by the cell leaders. Sometimes, the cell leader would propose subcell member names to the case officer, so the case officer could have a headquarters name check run before bringing the individual into the subcell. In principle, however, the subcell members would know ALPINE, and sometimes the other members of the ALPINE cell if they needed to work together; if ALPINE-1 and ALPINE-2 had independent assignments, they might not know each other. ALPINE-1 and ALPINE-2 certainly would not know ALISTAIR or anyone in the ALTITUDE or ALLOVER cells.

Fault-tolerant cellular structures
Modern communications theory has introduced methods to increase fault tolerance in cell organizations. In the past, if cell members only knew the cell leader, and the leader was neutralized, the cell was cut off from the rest of the organization. Game theory and graph theory have been applied to the study of optimal covert network design (see Lindelauf, R.H.A. et al. 2009. The influence of secrecy on the communication structure of covert networks. Social Networks 31: 126-137).If a traditional cell had independent communications with the foreign support organization, headquarters might be able to arrange its reconnection. Another method is to have impersonal communications "side links" between cells, such as a pair of dead drop
Dead drop
A dead drop or dead letter box is a method of espionage tradecraft used to pass items between two individuals by using a secret location and thus does not require them to meet directly. Using a dead drop permits a Case Officer and his Agent to exchange objects and information while maintaining...
s, one for Team ALAN to leave "lost contact" messages to be retrieved by Team ALICE, and another dead drop for Team ALICE to leave messages for Team ALAN.
These links, to be used only on losing contact, do not guarantee a contact. When a team finds a message in its emergency drop, it might do no more than send an alert message to headquarters. Headquarters might determine, through SIGINT
SIGINT
Signals intelligence is intelligence-gathering by interception of signals, whether between people , whether involving electronic signals not directly used in communication , or combinations of the two...
or other sources, that the enemy had captured the leadership and the entire team, and order the other team not to attempt contact. If headquarters can have reasonable confidence that there is a communications failure or partial compromise, it might send a new contact to the survivors.
When the cut-off team has electronic communications, such as the Internet, it has a much better chance of eluding surveillance and getting emergency instructions than by using a dead drop that can be under physical surveillance.
Non-traditional models, exemplified by al-Qaeda
Due to cultural differences, assuming the al-Qaeda Training Manual is authentic, Islamist cell structures may differ from the Western mode. "Al-Qaida's minimal core group, only accounting for the leadership, can also be viewed topologically as a ring or chain network, with each leader/node heading their own particular hierarchy."Such networks function by having their sub-networks provide information and other forms of support (the ‘many-to-one’ model), while the core group supplies ‘truth’ and decisions/directions (the ‘one-to-many’ model). Trust and personal relationships are an essential part of the Al-Qaida network (a limiting factor, even while it provides enhanced security). Even while cell members are trained as ‘replaceable’ units, ‘vetting’ of members occurs during the invited training period under the observation of the core group.
Cells of this structure are built outwards, from an internal leadership core. Superficially, this might be likened to a Western cell structure that emanates from a headquarters, but the Western centrality is bureaucratic, while structures in other non-western cultures builds on close personal relationships, often built over years, perhaps involving family or other in-group linkages. Such in-groups are thus extremely hard to infiltrate; infiltration has a serious chance only outside the in-group. Still, it may be possible for an in-group to be compromised through COMINT or, in rare cases, by compromising a member.
The core group is logically a ring, but is superimposed on an inner hub-and-spoke structure of ideological authority. Each member of the core forms another hub and spoke system (see infrastructure cells, the spokes leading to infrastructure cells under the supervision of the core group member, and possibly to operational groups which the headquarters support. Note that in this organization, there is a point at which the operational cell becomes autonomous of the core. Members surviving the operation may rejoin at various points.

While the tight coupling enhances security, it can limit flexibility and the ability to scale the organization. This in-group, while sharing tight cultural and ideological values, is not committed to a bureaucratic process.
"Members of the core group are under what could be termed ‘positive control’—long relationships
and similar mindsets make ‘control’ not so much of an issue, but there are distinct roles, and position (structural, financial, spiritual in the sense of having the ‘correct’ interpretation of Islam) determines authority, thus making the core group a hierarchy topologically.
In the first example of the core, each member knows how to reach two other members, and also knows the member(s) he considers his ideological superior. Solid lines show basic communication, dotted red arrows show the first level of ideological respect, and dotted blue arrows show a second level of ideological respect.
If Osama, the most respected, died, the core would reconstitute itself. While different members have an individual ideological guide, and these are not the same for all members, the core would reconstitute itself with Richard as most respected.
Assume there are no losses, and Osama can be reached directly only by members of the core group. Members of outer cells and support systems might know him only as "the Commander", or, as in the actual case of al-Qaeda, Osama bin Laden's face is recognizable worldwide, but only a very few people know where he is or even how to contact it.
Infrastructure cells
Any clandestine or covert service, especially a non-national one, needs a variety of technical and administrative functions. Some of these services include:- Forged documents and counterfeit currency
- Apartments and hiding places
- Communication means
- Transportation means
- Information
- Arms and ammunition
- Transport
Other functions include psychological operations, training, and finance.
A national intelligence service
has a support organization to deal with services such as finance, logistics, facilities (e.g., safehouses), information technology, communications, training, weapons and explosives, medical services, etc. Transportation alone is a huge function, including the need to buy tickets without drawing suspicion, and, where appropriate, using private vehicles. Finance includes the need to transfer money without coming under the suspicion of financial security organizations.
Some of these functions, such as finance, are far harder to operate in remote areas such as the FATA
Fata
The FATA or FC-ATA is a type of computer hard disk drive. FATA is simply the low cost ATA or SATA disk drive equipped with a small external converter, that changes the interface to Fibre Channel...
of Pakistan
Pakistan
Pakistan , officially the Islamic Republic of Pakistan is a sovereign state in South Asia. It has a coastline along the Arabian Sea and the Gulf of Oman in the south and is bordered by Afghanistan and Iran in the west, India in the east and China in the far northeast. In the north, Tajikistan...
, than in cities with large numbers of official and unofficial financial institutions, and the communications to support them. If the financial office is distant from the remote headquarters, there is a need for couriers, who must be trusted to some extent, although they may not know the contents of their messages, or the actual identity of sender and/or receiver. The couriers, depending on the balance among type and size of message, security, and technology available, may memorize messages, carry audio or video recordings, or hand-carry computer media.

The leaders of military cells are responsible for training them, and, when an operation is scheduled, selecting the operational commander, giving him the basic objective and arranging whatever support is needed, and then release him from tight control to execute the meeting. Depending on the specific case, the military leaders might have direct, possibly one-way, communications with their cells, or they might have to give Kim the messages to be transmitted, by means that Anton and Hassan have no need to know.
Note that Anton does not have a direct connection to Kim. Under normal circumstances, he sacrifices efficiency for security, by passing communications requests through Anton. The security structure also means that Hassan does not know the members of Anton's cells, and Kim may only know ways to communicate with them, but not their identity.
Kim operates two systems of cells, one for secure communications and one for propaganda. To send out a propaganda message, Osama must pass it to Kim. If Kim were compromised, the core group might have significant problems with any sort of outside communications.
Terrorist networks do not match cleanly to other cell systems that regularly report to a headquarters. The apparent al-Qaeda methodology of letting operational cells decide on their final dates and means of attack exhibit an operational pattern, but not a periodicity that could easily be used for an indications checklist appropriate for a warning center. Such lists depend on seeing a local pattern to give a specific warning..
Note that Hassan has two subordinates that have not yet established operational cells. These subordinates can be considered sleepers, but not necessarily with a sleeper cell.
Operational cells
For each mission are created one or more operational cells. If the al-Qaeda signature of multiple concurrent attacks is used, there may be an operational cell for each target location. It will depend on the operation if they will need any support cells in the operational area. For example, it may be more secure to have a local cell build bombs, which will be delivered by cells coming from outside the area."Operational cells are not created, but instead ‘seeded’ utilizing individuals spotted or that request assistance (both groups are ‘vetted’ by being trained under the observation of the core group, which dramatically restricts the opportunity for passing off walk-ins under false flag). Categorization of operational cells appears to be by capabilities, region, and then task/operation. Operational cells are composed of members whose worldview has been firmly tested—necessary to front-load, because such cells are dispersed back to their own local control (or negative control—proscribed behavior—with positive control only coming in the form of contact for synchronization or support)."
If operational cells routinely are "released" curved dotted lines on link to military cells to select their final operational parameters, they use a different paradigm than governmental clandestine or covert operations. On a number of cases, US special operations forces had to wait for Presidential authorization to make an attack, or even move to staging areas. Admittedly, a country would have to face the consequences of an inappropriate attack, so it may tend to be overcautious, where a terror network would merely shrug at the world being upset. Assuming that the al-Qaeda operational technique is not to use positive control, their operations may be more random, but also more unpredictable for counterterror forces. If their cells truly need constant control, there are communications links that might be detected by SIGINT, and if their command can be disrupted, the field units could not function. Since there is fairly little downside for terrorists to attack out of synchronization with other activities, the lack of positive control becomes a strength of their approach to cell organization.

Al-Qaeda's approach, which even differs from that of earlier terrorist organizations, may be very viable for their goals:
- Cells are redundant and distributed, making them difficult to ‘roll up’
- Cells are coordinated, not under "command & control"—this autonomy and local control makes them flexible, and enhances security
- Trust and comcon internally to the cell provide redundancy of potential command (a failure of Palestinian operations in the past), and well as a shared knowledgebase (which may mean, over time, that ‘cross training’ emerges inside a cell, providing redundancy of most critical skills and knowledge).
Indirect support networks
In the above graphic, note the indirect support network controlled by Richard's subcell."While Al-Qaida has elements of the organization designed to support the structure, but such elements are insufficient in meeting the needs of such an organization, and for security reasons there would be redundant and secondary-/tertiary-networks that are unaware of their connection to Al-Qaida. These networks, primarily related to fundraising and financial activities, as well as technology providers, are in a ‘use’ relationship with Al-Qaida—managed through cut-outs or individuals that do not inform them of the nature of activities, and that may have a cover pretext sufficient to deflect questions or inquiry."
A possible countermeasure
In 2002, U.S. News & World Report said that American intelligence is beginning to acquire a sufficiently critical mass of intelligence on al-Qaida indicating "Once thought nearly impossible to penetrate, al Qaeda is proving no tougher a target than the KGB or the Mafia--closed societies that took the U.S. government years to get inside. "We're getting names, the different camps they trained at, the hierarchy, the infighting", says an intelligence official. "It's very promising." The report also said that the collected data has allowed the recruiting of informants.Writing in the U.S. Army journal Military Review, David W. Pendall suggested that a "catch-and-release program for suspected operatives might create reluctance or distrust in such suspects and prevent them from further acts or, perhaps more important, create distrust in the cell leaders of these individuals in the future." The author noted the press release describing Ramzi Binalshib's cooperation with the United States "are sure to prevent reentry into a terrorist cell as a trusted member and most likely limits the further trust and assignments of close cell associates still at large. The captor would determine when to name names and when to remain silent." Indeed, once intelligence learns the name and characteristics of an at-large adversary, as well as some sensitive information that would plausibly be known to him, a news release could be issued to talk about his cooperation. Such a method could not be used too often, but, used carefully, could disturb the critical trust networks. The greatest uncertainty might be associated with throwing doubt onto a key member of an operational cell that has gone autonomous.

