Clandestine HUMINT asset recruiting
Encyclopedia
- This article is a subset article under Human IntelligenceHUMINTHUMINT, a syllabic abbreviation of the words HUMan INTelligence, refers to intelligence gathering by means of interpersonal contact, as opposed to the more technical intelligence gathering disciplines such as SIGINT, IMINT and MASINT...
. For a complete hierarchical list of articles, see the intelligence cycle management hierarchy. Concepts here are also associated with counterintelligence. This article deals with the recruiting of human agents. For more general descriptions of human intelligence techniques, see the article on Clandestine HUMINT operational techniquesClandestine HUMINT operational techniquesThe Clandestine HUMINT page deals with the functions of that discipline, including espionage and active counterintelligence. This page deals with Clandestine HUMINT operational techniques, also called "tradecraft". It applies to clandestine operations for espionage, and for a clandestine phase...
.
This section deals with the recruiting of human agents who work for a foreign government, or other targets of intelligence interest. For techniques of detecting and "doubling" host nation intelligence personnel who betray their oaths to work on behalf of a foreign intelligence agency, see counterintelligence.
The term spy
SPY
SPY is a three-letter acronym that may refer to:* SPY , ticker symbol for Standard & Poor's Depositary Receipts* SPY , a satirical monthly, trademarked all-caps* SPY , airport code for San Pédro, Côte d'Ivoire...
refers to human agents that are recruited by intelligence officers of a foreign intelligence agency. The popular use of the term in the media is at variance with its use in a professional context. Spies are not intelligence officers. Spies are recruited by intelligence officers to betray their country and to engage in espionage in favor of a foreign power. Intelligence officers who interact with spies are generally referred to as case officers.
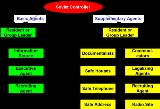
Types of agents
Acquiring information may not involve collecting secret documents, but something as simple as observing the number and types of ships in a port. Even though such information might be readily visible, the laws of many countries would consider reporting it to a foreign power espionage. Other asset roles include support functions such as communications, forgery, disguise, etc.According to Victor Suvorov, a former Soviet GRU
GRU
GRU or Glavnoye Razvedyvatel'noye Upravleniye is the foreign military intelligence directorate of the General Staff of the Armed Forces of the Russian Federation...
(i.e., military intelligence) officer, his service had Soviet officers, under diplomatic or nonofficial cover, handling two kinds of agent: basic and supplementary.

Both operation leaders and the supplementary group must be clandestine in support roles to basic agents. They may be clandestine officers of the FIS, such as Rudolf Abel, recruited in the target country, or recruited in a third country. One of the supplementary functions is communications, which includes clandestine radio transmission, dead drops, couriers, and finding places for secure radio transmissions. Other supplementary functions include people who can "legalise" agents with cover jobs, and specialists that can forge documents or get illicit copies from the actual source. Safe houses, safe mail drops, and safe telephones are other supplementary functions.
Recruitment
Recruiting typically begins with identifying targets - "spotting". The target may be "developed" over a period of time before the approach is made or it could be made "cold". Alternatively the potential agent may approach the agency. Many intelligence assets were not recruited but were "walk-ins" or "write-ins": people who offered information to foreign intelligence services."Spotting" is identifying people who appear to have access to information, or are attractive for some support role. There is research to identify any ties to counterintelligence, and then selection of the most promising candidates and approach method.
Obvious candidates are staff officers under diplomatic cover, or officers under nonofficial contact, have routine contact. Also possible contacts of access agents, existing agents, or through information that suggests they may be compromised.
Surveillance of targets (e.g., military or other establishments, open source or compromised reference documents) sometimes reveals people with potential access to information, but no clear means of approaching them. With this group, a secondary survey is in order. Headquarters may be able to suggest an approach, perhaps through a third country or through resources not known to the field station.
Recruiting people that may have access to the activities of non-state groups will be much harder, since these groups tend to be much more clandestine, and often operate on a cell system composed of relatives and people who have known one another for years. Access agents may be especially important here, and it may be worth the effort to spot potential access agents.
The deliberate spotting process complements more obvious candidates, but candidates who are also more likely to be compromised by counterintelligence, such as walk-ins and write-ins.
According to Suvorov, the Soviet GRU was not always able to collect enough material, principally from open sources, to understand the candidate's motivations and vulnerabilities. It was GRU doctrine, therefore, to use every meeting to continue to elicit this information. Other intelligence authorities also see eliciting information as a continuing process.
That continued meetings both provide substantive intelligence, as well as knowledge about the asset, are not incompatible with security. Agent handlers still observe all the rules of clandestinity while developing the agent relationship. Knowledge of meetings, and indeed knowledge of the existence of the asset, must be on a strict need-to-know basis.
Persons with access to technology
After the selection of a candidate for recruitment, the first stage, tracing and cultivating, commences. Details are collected about the candidate, details which may be obtained through reference, books, telephone directories, the press, and other recruited agents. Further definition of motives which will be used in the actual recruitment of the person are cultivated and weaknesses are exacerbated.Persons with access to knowledgeable people
Especially when the case officer is of a different culture than the one whose people he is targeting, the recruitment process begins not necessarily with a person that has the desired information. Instead, the first recruit may be someone well-connected in the local culture. Such a person may be called a principal agent or an access agent, who may simply arrange introductions, or actually run the operations of subagents. Some agents of this type may be able to help in the pre-recruitment stages of assessment and development, or may only be involved in finding possible assets.Indeed, an access agent may arrange introductions without being completely witting that the purpose of meeting the target is to find people who will participate in espionage. A well-respected technical professional, or a professor, often will make introductions within their field. Such introductions are perfectly reasonable in non-espionage contexts, such as looking for jobs or people to fill them. The process of personnel recruiting for industry is not completely dissimilar from recruiting spies. Both may use personal networks, and, in industrialized countries, computer-assisted personal "networking" (for example, through websites such as LinkedIn
LinkedIn
LinkedIn is a business-related social networking site. Founded in December 2002 and launched in May 2003, it is mainly used for professional networking. , LinkedIn reports more than 120 million registered users in more than 200 countries and territories. The site is available in English, French,...
).
Persons in allied intelligence agencies
A professional intelligence officer may very well obtain contacts through counterparts in the intelligence services of allied countries. The other service may arrange direct contact and then drop out of the process, or may jointly operate an asset such as the joint US-UK operation with Oleg PenkovskyOleg Penkovsky
Oleg Vladimirovich Penkovsky, codenamed HERO ; April 23, 1919, Vladikavkaz, North Ossetia, Soviet Russia, – May 16, 1963, Soviet Union), was a colonel with Soviet military intelligence in the late 1950s and early 1960s who informed the United Kingdom and the United States about the Soviet Union...
. The allied officer may not actually provide access to his assets, but will convey information requests and responses. There is the example of a CIA learned from the Malaysian service about an al-Qaeda
Al-Qaeda
Al-Qaeda is a global broad-based militant Islamist terrorist organization founded by Osama bin Laden sometime between August 1988 and late 1989. It operates as a network comprising both a multinational, stateless army and a radical Sunni Muslim movement calling for global Jihad...
meeting in Kuala Lumpur, something that would have been impossible for a lone CIA case officer to discover.
Targeting recruits based on intelligence information
HUMINT collectors should not forget that the analysts in their own organizations can have a sophisticated understanding of the people, with specialized knowledge, in targeted countries, industries, or other groups. The analyst may or may not know details of the target's personality.Even when no personal details are available, the recruiter, in an intelligence service, may have additional resources to use before the first contact. OSINT research can find the publications of a professional, but also social interests. With due regard to the risks and resources required, SIGINT can tap phone lines or intercept other communications that will give the recruiter more information about the target.
Prioritizing potential recruitment
This step differs from the next one, assessment of potential recruits, in that it is not focused on the recruit himself or herself, the probability of recruitment, etc., but, when there is more than one possible recruit, and a finite amount of case officer time, the discussion here gives criteria to select the most important targets.One analysis, by a US clandestine service officer with good knowledge of the practices of European allies, has five descending priorities in the period between 1957 and 1962. He developed these in the context of being stationed in Europe during the Cold War
Cold War
The Cold War was the continuing state from roughly 1946 to 1991 of political conflict, military tension, proxy wars, and economic competition between the Communist World—primarily the Soviet Union and its satellite states and allies—and the powers of the Western world, primarily the United States...
, with a goal of acquiring HUMINT
HUMINT
HUMINT, a syllabic abbreviation of the words HUMan INTelligence, refers to intelligence gathering by means of interpersonal contact, as opposed to the more technical intelligence gathering disciplines such as SIGINT, IMINT and MASINT...
recruits in the Soviet Union and its satellite nations. His operations were focused on people with the general characteristics:
- They were involved in an embassy, legation, consulate, trade mission, and news bureau that constituted the "were instrumentalities for that economic penetration, political subversion, and espionage that threatened U.S. interests." That focus could be considered one of counter-intelligenceCounter-intelligenceCounterintelligence or counter-intelligence refers to efforts made by intelligence organizations to prevent hostile or enemy intelligence organizations from successfully gathering and collecting intelligence against them. National intelligence programs, and, by extension, the overall defenses of...
as well as espionageEspionageEspionage or spying involves an individual obtaining information that is considered secret or confidential without the permission of the holder of the information. Espionage is inherently clandestine, lest the legitimate holder of the information change plans or take other countermeasures once it...
. - They were outside "their iron curtainIron CurtainThe concept of the Iron Curtain symbolized the ideological fighting and physical boundary dividing Europe into two separate areas from the end of World War II in 1945 until the end of the Cold War in 1989...
s for extended periods of time, two to five years,", so recruitment could involve a wide range of US, and possibly allied, intelligence resources.
Among this group, the priorities were:
-
- The most valuable recruit had regular access to "current political and economic intelligence from the installation in question." Ideally, the asset would be in the highest-priority country and have access to "the minutes of Politburo meetings" or equally critical military, scientific, or other data. In the case of countries that either dominate countries (e.g., the satellites of the former Soviet Union) or client states of another power, officials of the client country, or of the patron country's representatives in the client, may be easier to recruit than officials in the home country.
- Nearly as important is an agent who will continue the relationship once he returns to his home country, be that the Soviet Union or a satellite. Recruitment is harder to detect with the less intense counterintelligence surveillance of an independent or satellite country. "Installation penetration thus becomes a means of establishing long-range assets in the Satellites by recruiting, testing, and training them while they are abroad". In other words, the priority is to recruit a defector in place, continuing to report. "The Satellite diplomat, foreign trade official, journalist, or intelligence officer who has been useful to us abroad will be even more valuable when he goes back home at the end of his tour, not just because he is then inside the target country, but because the intelligence to which he has access in a ministry headquarters has greater scope and depth.
- The third priority involves offensive counterintelligence/counterespionage: by observation of intelligence activities operated from embassies of country X, a counterintelligence service can deduce characteristic recruiting and agent handling practices for country X. Because these officers and techniques affect many hostile targets in the country of operations, once this information is known, the foreign intelligence service (FIS) agents can be neutralized in a variety of ways, including police action, convincing the asset in the country of operations to stop cooperating with the FIS, or, ideally, "recruiting the hostile intelligence officer in place."
- The fourth and fifth priorities are considerably less urgent than the first three. The fourth priority is the "defection of senior diplomatic, trade, or intelligence personnel. Defection can obviously yield only those golden eggs already in the nest; it cuts off the continuing intelligence that could be provided by an in-place asset. It may be worthwhile, however, simply to deny a target country the services of an able and experienced officer, and it may produce, in addition to his store of positive intelligence, leads to his former colleagues who are still in place."
- Last in priority is not direct recruitment, but the collection of information to support future recruitment. This begins with obtaining biographical information on "officials abroad who are likely in the future to have other tours of foreign duty somewhere in the world. An official may not be developable for recruitment during his current tour, but six months from now it might be a different story. Political turmoil being what it is within the Satellites, the "ins" can rapidly become the "outs." If we can identify a man as a former "in" who is now "out" we may be able to recruit him. But this kind of identification requires orderly and current biographic indexes of Satellite personnel who travel abroad."
Assessing potential recruits
In deciding whether to recruit a prospect, there needs to be a process to make sure that the person is actively working for the adversary's counterintelligence, is under surveillance by them, or presents other risks that may not make recruitment wise. The assessment process applies both to walk-ins and targeted recruits, but additional assessment needs to apply to the walk-in, who is most likely to be someone sent by a counterintelligence service.Assessing walk-ins
Major intelligence services are very cautious about walk-ins or write-ins, but some of the most important known assets were walk-ins, such as Oleg PenkovskyOleg Penkovsky
Oleg Vladimirovich Penkovsky, codenamed HERO ; April 23, 1919, Vladikavkaz, North Ossetia, Soviet Russia, – May 16, 1963, Soviet Union), was a colonel with Soviet military intelligence in the late 1950s and early 1960s who informed the United Kingdom and the United States about the Soviet Union...
or write-ins (using intelligence tradecraft) such as Robert Hanssen
Robert Hanssen
Robert Philip Hanssen is a former American FBI agent who spied for Soviet and Russian intelligence services against the United States for 22 years from 1979 to 2001...
. Most walk-ins though are rejected.
The US Army defines three classes of people who may present themselves:
-
- Defectors
- Asylum seekers
- Walk-ins: who seek to provide information to the United States; or a disaffected person (one who is discontent and resentful, especially against authority) who presents him- or herself to a U.S. installation in a foreign country and who appears willing to accept recruitment in place or requests asylum or assistance in escaping from the control of his or her government.
A Soviet response, to someone visiting the embassy, was "This is a diplomatic representation and not an espionage centre. Be so kind as to leave the building or we will call the police." According to Suvorov, the police are usually not called but the embassy staff chase the would-be agent out quickly.
Cautious handling of walk-ins was not exclusively a Soviet concern.
U.S. Army procedure is to have military intelligence (MI) or military police (MP) personnel handle all aspects of walk-ins. Under US Army Regulations, military police are not intended to do interrogations, which are the responsibility of military intelligence personnel.
While serious discussion with the contact will be done by counter-intelligence
Counter-intelligence
Counterintelligence or counter-intelligence refers to efforts made by intelligence organizations to prevent hostile or enemy intelligence organizations from successfully gathering and collecting intelligence against them. National intelligence programs, and, by extension, the overall defenses of...
specialists, information about the walk-in must be restricted to people with a "need-to-know." "The information the walk-in provides must be guarded and classified appropriately."
While the interviewers will actually be from MI, the walk-in will never be told the identities of intelligence personnel. If they ask to see an intelligence representative, they will be told none is available. Both these measures are intended to prevent hostile intelligence services learning about the structure or procedure of US intelligence/counterintelligence personnel.
The Soviets showed caution equivalent to the US. Soviet GRU doctrine was that on general, a walk-in is considered only when they can show some evidence of access to valuable material. The best way of doing this is actually bringing a sample of information. Suvorov observes that "this is perhaps the only way to convince the GRU that they can trust the person."
Suvorov describes an ideal; the one-time head of the GRU, Gen. Ivan Serov
Ivan Serov
State Security General Ivan Aleksandrovich Serov was a prominent leader of Soviet security and intelligence agencies, head of the KGB between March 1954 and December 1958, as well as head of the GRU between 1958 and 1963. He was Deputy Commissar of the NKVD under Lavrentiy Beria, and was to play a...
, was willing to explore potential agents who gave plausible information about themselves and their access, or a "write-in" whose potential could be verified before a meeting.
General assessment
It has been the general experience of intelligence agencies that potential recruits, recruits early in the development process, and those currently reporting to a local case officer, still need to be checked against master biographical and other files, which will help spot foreign counterintelligence. This counterintelligence interest could be from their own or third countries.Once an individual is seen to have potential access to information, the recruiting officer or staff considers why a presumably loyal and trusted individual might be willing to betray his own side. A basic set of reasons are the classic MICE motivations, with further insights in attitudes predisposing to cooperation.
Headquarters may have access to information that a field office does not, such as being able to access credit records to identify financial stress, through a cutout that hides the request as having come from country B's service. Another area where a central office can help is to correlate possible penetration attempts by an individual who approaches one's own, or allied, intelligence services in different locations, as, for example, embassies in different cities.
There are both local and headquarters-based means of validation. The case officer should compare information, provided by the agent, with locally known facts, both from overt and covert sources. Some services, especially the Russian/Soviet, may not have formal or extensive OSINT, and either the case officer may need to check such things (or set up checkable requests) within the station/residency.
Some definite warnings, which may come from local or headquarters reporting, include:
- The agent's information contradicts other information believed to be true
- The agent's information has appeared in local open sources
- The information is true, but is too old to be of operational value. This was one of the key techniques of the World War II British Double Cross SystemDouble Cross SystemThe Double Cross System, or XX System, was a World War II anti-espionage and deception operation of the British military intelligence arm, MI5. Nazi agents in Britain - real and false - were captured, turned themselves in or simply announced themselves and were then used by the British to broadcast...
- If there are inconsistencies in the agent's life story, which the case officer can query periodically through social conversation, the truth is usually in the consistent aspects. It is easier to make a mistake in keeping up a lie, than in telling the truth, which is the reason criminal investigators ask a suspect to repeat their statements.
- If the agent makes predictions, be very sure to see if they become true
- In the event that the recruiting officer's service uses technical means of detecting evasion, such as polygraphPolygraphA polygraph measures and records several physiological indices such as blood pressure, pulse, respiration, and skin conductivity while the subject is asked and answers a series of questions...
y, voice stress analysisVoice stress analysisVoice Stress Analysis technology is said to record psychophysiological stress responses that are present in human voice, when a person suffers psychological stress in response to a stimulus and where the consequences may be dire for the subject being 'tested'.In the Detection Of Deception ...
, interviews by psychologists and psychiatrists, and perhaps more in the future, brain imaging, make use of these within the agency policy. Be aware that penetrators may be trained to resist them.
Access agents and access techniques
An access agent does not have significant access to material of intelligence value, but has contact with those who do. Such a person could be as simple as the barber outside a military base, or as complex as a think tank or academic expert (i.e., outside the government) who deals regularly with government personnel with access to sensitive material.Within private and public organizations that handle sensitive material, human resource workers, receptionists, and other seemingly low-level personnel know a great deal about the people with sensitive access. Certain employees, such as guards and janitors, who have no formal access, still may be able to gain access to secured rooms and containers; there is a blurry area between an access agent that might let your collector into an area, and a support employee who can collect information that he may or may not understand.
Love, honeypots and recruitment
US intelligence services, for example, are concerned when their own personnel could be subject to sexual blackmail. This applied to any homosexual relationship until the mid-1990s, and also applied to heterosexual relationships with most foreign nationals. See honeypots in espionage fictionHoneypots in espionage fiction
In espionage terminology, "honeypot" is one of several ways to refer to a recruitment that involves sexual seduction. See Love, honeypots, and recruitment for real-world examples.*North by Northwest has Eva Marie Saint as both the honeypot and a double agent...
for fictional examples. In some cases, especially when the national was a citizen of a friendly nation, the relationship needed to be reported. Failure to do so, even with a friendly nation, could result in dismissal.
One former CIA officer said that while sexual entrapment wasn't generally a good tool to recruit a foreign official, it was sometimes employed successfully to solve short-term problems. Seduction
Seduction
In social science, seduction is the process of deliberately enticing a person to engage. The word seduction stems from Latin and means literally "to lead astray". As a result, the term may have a positive or negative connotation...
is a classic technique; "swallow" was the KGB tradecraft term for women, and "raven" the term for men, trained to seduce intelligence targets.
During the Cold War, the KGB (and allied services, including the East German Stasi
Stasi
The Ministry for State Security The Ministry for State Security The Ministry for State Security (German: Ministerium für Staatssicherheit (MfS), commonly known as the Stasi (abbreviation , literally State Security), was the official state security service of East Germany. The MfS was headquartered...
under Markus Wolf
Markus Wolf
Markus Johannes "Mischa" Wolf was head of the General Intelligence Administration , the foreign intelligence division of East Germany's Ministry for State Security . He was the MfS's number two for 34 years, which spanned most of the Cold War...
, and the Cuban Intelligence Directorate (formerly known as Dirección General de Inteligencia or DGI)) frequently sought to entrap CIA officers. The KGB believed that Americans were sex-obsessed materialists, and that U.S. spies could easily be entrapped by sexual lures. The best-known incident, however, was of Clayton Lonetree, a Marine guard supervisor at the Moscow embassy, who was seduced by a "swallow" who was a translator at the Embassy of the United States in Moscow
Embassy of the United States in Moscow
The Embassy of the United States in Moscow is the diplomatic mission of the United States to the Russian Federation. It is located in the Presnensky District in the city center of Moscow. Its address is: Bolshoy Deviatinsky Pereulok No...
. Once the seduction took place, she put him in touch with a KGB handler. The espionage continued after his transfer to Vienna, although he eventually turned himself in.
The Soviets used sex not only for direct recruitment, but as a contingency where an American officer might need to be compromised in the future. The CIA itself made limited use of sexual recruitment against foreign intelligence services. "Coercive recruitment generally didn't work. We found that offers of money and freedom worked better." If the Agency found a Soviet intelligence officer had a girlfriend, they would try to recruit the girlfriend as an access agent. Once the CIA personnel had access to the Soviet officer, they might attempt to double him.
Examples of people trapped by sexual means include:
- Clayton J. LonetreeClayton J. LonetreeClayton J. Lonetree is a member of the Navajo Nation who served nine years in prison for espionage. During the early 1980s, Lonetree was a Marine Corps Security Guard stationed at the Embassy of the United States in Moscow....
, a US MarineUnited States Marine CorpsThe United States Marine Corps is a branch of the United States Armed Forces responsible for providing power projection from the sea, using the mobility of the United States Navy to deliver combined-arms task forces rapidly. It is one of seven uniformed services of the United States...
Sergeant embassy guard in Moscow, was entrapped by a female SovietSoviet UnionThe Soviet Union , officially the Union of Soviet Socialist Republics , was a constitutionally socialist state that existed in Eurasia between 1922 and 1991....
officer in 1987. He was then blackmailed into handing over documents when he was assigned to ViennaViennaVienna is the capital and largest city of the Republic of Austria and one of the nine states of Austria. Vienna is Austria's primary city, with a population of about 1.723 million , and is by far the largest city in Austria, as well as its cultural, economic, and political centre...
. Lonetree is the first US Marine to be convicted of spying against the United States. - Roy Rhodes, a US ArmyUnited States ArmyThe United States Army is the main branch of the United States Armed Forces responsible for land-based military operations. It is the largest and oldest established branch of the U.S. military, and is one of seven U.S. uniformed services...
NCONon-commissioned officerA non-commissioned officer , called a sub-officer in some countries, is a military officer who has not been given a commission...
serving at the US embassy in Moscow, had a one-night standOne-night standOriginally, a one-night stand was a single theatre performance, usually by a guest performer on tour, as opposed to an ongoing engagement. Today, however, the term is more commonly defined as a single sexual encounter, in which neither participant has any intention or expectation of a relationship...
(or was made to believe he had) with a Soviet agent while drunk. He was later told the agent was pregnant, and that unless he co-operated with the Soviet authorities, this would be revealed to his wife. - Irvin C. ScarbeckIrvin C. ScarbeckIrving C. Scarbeck was a U.S. State Department official who was convicted of giving information to Polish UB during the Cold War, after he became involved in a romantic affair with a Polish woman and was blackmailed by Polish intelligence agents. His case was the first prosecution under Title 50...
, a US diplomat, was entrapped by a female PolishPolandPoland , officially the Republic of Poland , is a country in Central Europe bordered by Germany to the west; the Czech Republic and Slovakia to the south; Ukraine, Belarus and Lithuania to the east; and the Baltic Sea and Kaliningrad Oblast, a Russian exclave, to the north...
officer in 1961, and photographed in a compromising position. He was blackmailed into providing secrets. - Sharon ScranageSharon ScranageSharon Scranage is a former CIA employee who was jailed for revealing the identities of CIA agents.Scranage, who worked in Ghana in the role of Operations Support Assistant, passed classified information to her boyfriend, Michael Soussoudis...
, a CIA employee described by one source as a "shy, naive, country girl", was allegedly seduced by GhanaGhanaGhana , officially the Republic of Ghana, is a country located in West Africa. It is bordered by Côte d'Ivoire to the west, Burkina Faso to the north, Togo to the east, and the Gulf of Guinea to the south...
ian intelligence agent Michael Soussoudis. She later gave him information on CIA operations in Ghana, which was later shared with Soviet-bloc countries. - Mordechai VanunuMordechai VanunuMordechai Vanunu ; is a former Israeli nuclear technician who, citing his opposition to weapons of mass destruction, revealed details of Israel's nuclear weapons program to the British press in 1986. He was subsequently lured to Italy by a Mossad agent, where he was drugged and kidnapped by...
, who had disclosed Israeli nuclear secrets, began an affair with an American MossadMossadThe Mossad , short for HaMossad leModi'in uleTafkidim Meyuchadim , is the national intelligence agency of Israel....
agent, Cheryl BentovCheryl BentovCheryl Ben Tov , born Cheryl Hanin in 1960, is an American real estate agent and former Israeli Mossad agent who became well-known in 1986 when, under the name "Cindy", she persuaded former Israeli nuclear technician Mordechai Vanunu to go with her to Rome, where he was captured, drugged, and...
, operating under the name "Cindy" and masquerading as an American tourist, on September 30, 1986. She persuaded him to fly to Rome, Italy, with her on a holiday. Once in Rome, Mossad agents drugged him and smuggled him to IsraelIsraelThe State of Israel is a parliamentary republic located in the Middle East, along the eastern shore of the Mediterranean Sea...
on a freighter. - John VassallJohn VassallWilliam John Christopher Vassall was a British civil servant who, under pressure of blackmail, spied for the Soviet Union....
, a British civil servant who was guided by the KGBKGBThe KGB was the commonly used acronym for the . It was the national security agency of the Soviet Union from 1954 until 1991, and was the premier internal security, intelligence, and secret police organization during that time.The State Security Agency of the Republic of Belarus currently uses the...
into having sex with multiple male partners while drunk. The KGB then used photographs of this to blackmail Vassall into providing them with secret information. - Bernard BoursicotBernard BoursicotBernard Boursicot is a French diplomat who was caught in a honeypot trap , by Shi Pei Pu, a male Peking opera singer who performed female roles, whom Boursicot believed to be female...
, a French diplomat, was entrapped by Shi Pei PuShi Pei PuShi Pei Pu was a Chinese opera singer from Beijing. He became a spy who obtained secrets during a 20-year long sexual affair in which he convinced an employee in the French Embassy that he was a woman, later producing a child that he insisted had been born through their relations. The story made...
, who was working for the ChineseChinaChinese civilization may refer to:* China for more general discussion of the country.* Chinese culture* Greater China, the transnational community of ethnic Chinese.* History of China* Sinosphere, the area historically affected by Chinese culture...
government. Shi Pei Pu, a male Chinese opera singer, successfully masqueraded as a woman and told Boursicot he was carrying Boursicot's child. The situation was fictionalized into the play M. ButterflyM. ButterflyM. Butterfly is a 1988 play by David Henry Hwang loosely based on the relationship between French diplomat Bernard Boursicot and Shi Pei Pu, a male Peking opera singer....
. - Katrina LeungKatrina LeungKatrina Leung was a former high value Federal Bureau of Investigation and PRC Ministry of State Security agent who, on April 9, 2003, was indicted by the United States Department of Justice for "Unauthorized Copying of National Defense Information with Intent to Injure or Benefit a Foreign...
, indicted as a double agentDouble agentA double agent, commonly abbreviated referral of double secret agent, is a counterintelligence term used to designate an employee of a secret service or organization, whose primary aim is to spy on the target organization, but who in fact is a member of that same target organization oneself. They...
working for both China and the FBI, seduced her FBI handler, James J. Smith, and was able to obtain FBI information of use to China through him. She also had an affair with another FBI officer, William Cleveland. - In 2006, the British Defence Attaché in Islamabad Pakistan, was recalled home, when it emerged that he had been involved in a relationship with a Pakistani woman, who was an intelligence agent. While the British Government deny that secrets were lost, others sources say that several Western operatives and operations within Pakistan were compromised.
- In May 2007 a female officer serving in Sweden's KosovoKosovoKosovo is a region in southeastern Europe. Part of the Ottoman Empire for more than five centuries, later the Autonomous Province of Kosovo and Metohija within Serbia...
force was suspected of having leaked classified informationClassified informationClassified information is sensitive information to which access is restricted by law or regulation to particular groups of persons. A formal security clearance is required to handle classified documents or access classified data. The clearance process requires a satisfactory background investigation...
to her SerbiaSerbiaSerbia , officially the Republic of Serbia , is a landlocked country located at the crossroads of Central and Southeast Europe, covering the southern part of the Carpathian basin and the central part of the Balkans...
n lover who turned out to be a spy. - Won Jeong-hwa, who was arrested by South Korea in 2008 and charged with spying for North Korea, is accused of using this method to obtain information from an army officer.
Spotting through emotional attachment
Yet other factors may apply. True friendship or romance may draw others to become involved with a current agent. John Anthony WalkerJohn Anthony Walker
John Anthony Walker, Jr. is a former United States Navy Chief Warrant Officer and communications specialist convicted of spying for the Soviet Union from 1968 to 1985, at the height of the Cold War...
, who spied for money, recruited friends and relatives. Rosario Ames, wife of Aldrich Ames
Aldrich Ames
Aldrich Hazen Ames is a former Central Intelligence Agency counter-intelligence officer and analyst, who, in 1994, was convicted of spying for the Soviet Union and Russia...
, was brought into her husband's activities.
Katrina Leung
Katrina Leung
Katrina Leung was a former high value Federal Bureau of Investigation and PRC Ministry of State Security agent who, on April 9, 2003, was indicted by the United States Department of Justice for "Unauthorized Copying of National Defense Information with Intent to Injure or Benefit a Foreign...
is one of the more complex cases, who came to the US on a Taiwanese passport, became involved with a PRC activist, on whom she was recruited to report to the FBI. She seduced her FBI case officer, and eventually was recruited by the FBI as a "dangle" to PRC targets, specifically in the Chinese Ministry of State Security
Ministry of State Security
The Ministry of State Security is the security agency of the People's Republic of China...
(MSS). Her first reports were independently confirmed by the CIA. Later, however, she was found to be passing FBI documents to the MSS, while still reporting to the FBI. While she was allowed, at first, to continue, on the belief that the information she provided to the US was more important than that which she was giving to the PRC, she was eventually arrested and charged with a relatively low-level crime. Eventually, that was dismissed for reasons of prosecutorial misconduct, although a subsequent US government appeal resulted in a plea bargain. Her true loyalty was never made public, but, at various times, she appears to have been a dangled mole and a doubled agent, as well as possibly a PRC access agent to FBI personnel.
Development: preparation for actual recruitment
Actual recruiting involves a direct approach by a case officer who has some existing access to the potential recruit, an indirect approach through an access agent or proprietary, or has reason to risk a "cold" approach. Before the direct recruitment, there may be a delicate period of development.The case officer, possibly through an access agent, works on establishing a relationship. This phase, in which the potential agent is called a developmental, has not yet reached the recruiting pitch. "After the cultivation stage, overt contact is established with the candidate under the guise of an official meeting. After the acquaintanceship has ripened and official meetings evolve into personal meetings, the developmental stage begins.
Choosing between "crash" and gradual approaches
Suvorov describes the "crash approach" as the most demanding form of recruitment, which is to be done only if the local rezident, or chief of the GRU unit, convinces GRU headquarters that the risk is worthwhile. "Quite a few examples are known of recruitment at the first meeting, of course following the secret cultivation which has gone on for many months.""The crash approach, or 'love at first sight' in GRU jargon, has a number of irrefutable advantages. Contact with the future agent takes place only once, instead of at meetings over many months, as is the case with the gradual approach. After the first contact the newly recruited agent will himself take action on his own security. He will never talk to his wife, or tell her that he has a charming friend in the Soviet military attaché who is also very interested in stamp collecting."
Compromise during development
Telling one's wife or colleagues about a charming Soviet friend can compromise the entire development. The US is also aware that the Soviet developmental process is, preferably, gradual. "The developmental stage cements the relationship and encourages loyalty to it. The hostile intelligence officer may then, through friendly persuasion, ask for a very innocent and insignificant favor from the candidate and pay him generously for it., thus placing the candidate in a position of obligation. During this stage the future agent becomes accustomed to being asked favors and fulfilling them accurately. The future agent's ambitions, financial and work problems, hobbies, etc., are continuously assessed by an intelligence team to exacerbate weaknesses. The future agent's professional, social, and private personalities are soon stripped away.It is the goal of the case officer, with appropriate support from his organization, to learn vulnerabilities, build trust, and solve problems for the developmental. These are all preparatory steps to asking, perhaps subtly, the developmental to betray his own side.
Information requests begin innocently, usually asking for public information, but to get the development on the path to betrayal. At first, any requests for documents are for open ones, which the case officer gives some pretext for not himself obtaining. A creative task officer may then ask for a technically restricted, but still fairly innocent document, such as an unclassified telephone directory.
The interaction becomes more sensitive, especially when the case officer asks for something technically classified, but with an explanation that lets the potential recruit rationalize that he is not really betraying any trust. During this time, the case officer is building psychological control. In some cases, it may be possible to get useful information without ever asking the developmental to betray his country. These cases may mean the role of the recruit is not to be as a direct agent, but perhaps as an access or a support agent. The recruit may not even be witting of his relationship to a FIS.
Finally, the relationship will move from clandestine to overt, when the foreign service has significant compromising information on the asset. If the asset had been motivated by money, he will find the tasks given him may become more challenging, but the payments reduce, because he is no longer in a position to negotiate.
Recruitment through professional interests
The traditional openness of the scientific community can be exploited to obtain information from an individual with access to commercially, scientifically, or militarily valuable material."There is another important source, peculiar to scientific intelligence. This is the body of experts in particular fields of science available in one's own country for consultation. The phenomena of nature are independent of political boundaries, and the experts are in the position of agents spying on these phenomena insofar as they throw light on the feasibility of a suspected enemy development."
A 1998 document describes typical foreign intelligence recruitment against citizens with access to sensitive technology. "Hostile intelligence services begin the agent recruitment process by scrupulously collecting information on persons who are connected to industry, RDT&E laboratories, government institution staffs, military bases, and design organizations." A candidate for recruitment usually fulfills the following criteria:
- They must be in a position to provide information of real use to the hostile intelligence service, either to steal or copy S&T information, to communicate secret information by word of mouth, or to recruit new agents.
- There must exist motives by means of which an individual can be recruited:
-
-
- Financial Consideration/Greed (Transcends all other motives)
- Revenge/Disaffection
- Blackmail/Hostage Situations (Used in USSR but very infrequently in U. S.)
- Appeal to Emigres National Pride
- Exploitation of an Emotional Involvement
- False Flag Approaches
- Exploitation of an American's Naivete
- Sex
- Ideology (Not the motivation it once was. The Soviet service changed its emphasis to concentrate on sympathy for "persecuted" elements of American, or other targeted, society)
-
Stopping before formal recruitment
"By degrees the tasks become more complicated, but the payment for them grows equally, In many cases the actual recruitment proposal is never made, as the candidate gradually becomes an agent of the hostile intelligence servicewithout fully realizing it.
Recruitment
If the decision is made to make a formal recruitment, the case officer gets the developmental accustomed to meeting in more obscure places and at more unusual times. These can have the function of countersurveillanceCountersurveillance
Countersurveillance refers to measures undertaken to prevent surveillance, including covert surveillance. Countersurveillance may include electronic methods such as bug sweeping, the process of detecting surveillance devices, including covert listening devices and visual surveillance devices...
, during which additional officers may be watching the meeting, and the travel to it, for evidence of "country A" counterintelligence interest. Without the developmental fully realizing it, he is being drawn into increasingly treasonous activity, which would be harder and harder to explain were he caught. It is considered important for the case officer to offer money, perhaps dismissed as covering expenses, but really as a means of compromising the developmental.
Eventually, especially if the recruit is ideologically sympathetic to Country B, the case officer makes the direct recruitment pitch. This may not work, and, in fact, may induce rage. The case officer has to be prepared for physical defense and escape if this becomes necessary. If the case officer can produce compromising photographs, receipts, etc., even an originally ideological subject now moves into the realm of compromise.
Recruiting through business relationships
Most commonly directed at the strategic level (i.e., Scientific & Technical Intelligence—ST&I) of Technical intelligenceTechnical intelligence
In a pure military context, Technical Intelligence is intelligence about weapons and equipment used by the armed forces of foreign nations .The related term, scientific and technical intelligence, addresses information collected at the strategic level.Technical intelligence is intended primarily...
, key business personnel, or even a business itself, might be recruited by a FIS. Both the KGB
KGB
The KGB was the commonly used acronym for the . It was the national security agency of the Soviet Union from 1954 until 1991, and was the premier internal security, intelligence, and secret police organization during that time.The State Security Agency of the Republic of Belarus currently uses the...
and GRU
GRU
GRU or Glavnoye Razvedyvatel'noye Upravleniye is the foreign military intelligence directorate of the General Staff of the Armed Forces of the Russian Federation...
of the Soviet Union carried out such recruitment. The KGB service for such recruitment was called Line X, which reported to Directorate T of the KGB First Chief Directorate, the Soviet civilian foreign intelligence service.
According to Victor Suvorov, the GRU commonly ran such recruitments at industry trade shows:
Before the opening of exhibitions of military electronics, armaments and military technology, ship-building and engine-building conferences, air shows and so on, hundreds of which take place every year, a scientific delegation appears at the GRU residency with a list of everything which is essential for the Soviet military and the armaments industry. The experts of course know that at the exhibition there will be demonstrations of models whose sale to the Soviet Union is categorically prohibited. None the less, the delegation will carry suitcases crammed full of money, with full powers to spend it as they wish. All expenditure is approved and justified. The examination and construction of such samples as they have been able to obtain in the Soviet Union will occupy much more time and money.
The delegation visits the exhibition and looks at the stands of the big corporations only to disguise its real object. At each of these stands these are several salesmen and guides, any one or all of which may be from the security services. The delegation is only really interested in the stands of small firms where the explanations are carried out by the owner or a director himself. The delegation gets into conversation with him and an officer of the local GRU residency acts the part of interpreter. The experts pass themselves off as an official Soviet delegation. At the same time they manage to let the operational officer know that they have arrived at just such a firm as could be of use to them and that the exhibit is not just a model, but an actual piece. The interpreter stays for a few seconds. 'Could I not invite you to dinner this evening in the restaurant?' 'I don't know whether that would be all right. We hardly know each other.' And that is all. Recruitment is accomplished. ...
Suvorov explains that this technique was extremely effective with small firms: "The owner of a small firm, even a very successful one, is always at great risk, always keen to strengthen his situation..... In any case, if he sells his product he can hide the fact from the authorities. It is equally easy for him to hide the money he has received." The businessman, however, may forget that while he might not report the cash transaction to his own government, the GRU certainly has recorded the act of payment, and can use it for subsequent blackmail.
Suvorov explained that while the most strategic information appears to be associated with major firms, there are several reasons why an approach to a smaller company is the place to begin.
-
- In many products, the true breakthroughs are not the entire aircraft or tank, but some subcomponent. An example of such, admittedly made by a British government facility but still a good example of a key technology, is the Chobham armor used on the M1 AbramsM1 AbramsThe M1 Abrams is a third-generation main battle tank produced in the United States. It is named after General Creighton Abrams, former Army Chief of Staff and Commander of US military forces in Vietnam from 1968 to 1972. The M1 is a well armed, heavily armored, and highly mobile tank designed for...
tank. - People recruited in small firms may become access agents for recruitments in large companies. "After he has been milked, the owner of a components manufacturing firm, now turned agent, must turn his attention to the recruitment of other agents in the big firms to which he supplies his parts.
- In many products, the true breakthroughs are not the entire aircraft or tank, but some subcomponent. An example of such, admittedly made by a British government facility but still a good example of a key technology, is the Chobham armor used on the M1 Abrams
Legalising illegal agents
While usual practice is to recruit residents of the country being targeted, there have been instances where the FIS brought illegal agents into that country. Common practice was to have them enter via a third country, and perhaps claim to be immigrants from a fourth.The introduction of an "illegal" might be due to the need to bring a specialist in to carry out some part of the operation. The Soviet KGB
KGB
The KGB was the commonly used acronym for the . It was the national security agency of the Soviet Union from 1954 until 1991, and was the premier internal security, intelligence, and secret police organization during that time.The State Security Agency of the Republic of Belarus currently uses the...
had a Department V, staffed with officers qualified to kill or to carry out sabotage.
Specialists of the FIS might also need legalisation to carry out clandestine intelligence collection. The US has had a group of CIA and NSA specialists who would emplace technical sensors, ranging from telephone taps to specialized devices for measuring weapons tests, into the target country.
Obtaining the documentation and other resources is the role of legalising agents and documentalists. Candidate for this category of agents are sought among officials of the police and passport departments, consular clerks, customs and immigration officials, and small employers of labour. Agent legalisers are subjected to especially thorough vetting, because the fate of illegals is entrusted to them. When a Soviet illegal arrives in a country the task of the legalising agent is to ensure the issue of documents by making the necessary entries in the registration books and to ensure that the illegal is in possession of the necessary documentation.
A common technique was to find birth records of someone known later to have died. The "documentation agent" who did this would not have contact with illegals.
<--
Soviet case studies
These observations are from Ivan SerovIvan Serov
State Security General Ivan Aleksandrovich Serov was a prominent leader of Soviet security and intelligence agencies, head of the KGB between March 1954 and December 1958, as well as head of the GRU between 1958 and 1963. He was Deputy Commissar of the NKVD under Lavrentiy Beria, and was to play a...
, former director of the GRU
GRU
GRU or Glavnoye Razvedyvatel'noye Upravleniye is the foreign military intelligence directorate of the General Staff of the Armed Forces of the Russian Federation...
, the Soviet military intelligence organization.
Soviet case study 1: Potential agent, with financial motivation, successful outcome
Some sources want to minimize or eliminate personal contact with an agent handler, as did Robert HanssenRobert Hanssen
Robert Philip Hanssen is a former American FBI agent who spied for Soviet and Russian intelligence services against the United States for 22 years from 1979 to 2001...
. Even a write-in, however, potentially reveals information that can be checked, with as little information as a callback telephone number that can be checked in a reverse telephone directory, or, if the technical resources are available, wiretapped to find out about other contacts. Early in a recruitment, even with an ostensible "well-wisher", the intelligence service doing the recruiting cannot know if the potential source is actually a loyal foreign intelligence officer trying to penetrate the recruiting service. Serov became somewhat comfortable with the recruit only after the recruit's motivations were understood and worthwhile material was provided by the recruit.
Soviet case study 2: Potential agent, with financial motivation, failure
Well-wishers who contact the recruiting service through non-public channels are apt to be intelligence officers, to have access to that information. It cannot be determined, at first, if the well-wisher is truly offering services or is a penetration, but such approaches are critical to follow, due to the apparent affiliation of the contact. Even if the recruiting service decides the well-wisher is a penetration agent, the interaction offers a potential channel for disinformation. Using the interaction in that manner is relatively low-risk, if the well-wisher already demonstrated some familiarity with the HUMINT officer. attaché was not public, but if it was not, the contact immediately needed to be taken seriously.As is correct tradecraft, the contact was reported to GRU Headquarters, to check the contact against known foreign intelligence officers. Reporting to the center and its extensive files is standard doctrine for all known services, which also is a reason why Aldrich Ames
Aldrich Ames
Aldrich Hazen Ames is a former Central Intelligence Agency counter-intelligence officer and analyst, who, in 1994, was convicted of spying for the Soviet Union and Russia...
and Kim Philby
Kim Philby
Harold Adrian Russell "Kim" Philby was a high-ranking member of British intelligence who worked as a spy for and later defected to the Soviet Union...
, as headquarters personnel with access to new contact information, were so damaging. The initial response was that contact should be continued, and the air attaché obtained a document of value. A second message from headquarters, however, told the GRU officer to drop the contact as risky. The reason the Center warned the local residency to break contact was not strictly that the well-wisher was questionable, but because Center, through other methods, learned that local counterintelligence was aware of the meeting. Better security about the meeting might have let the relationship continue.
Soviet case study 3: Potential agent, with financial motivation, guarded success
A walk-in said that he had documents to sell, and asked for a large sum. The GRU officer interviewing him arranged for a secure meeting, with a backup communications plan using a safe public telephone. The officer researched the contact, before the meeting. and decided to check up on him more thoroughly. As a test, the meeting was cancelled, but other GRU assets kept the meeting place under clandestine surveillane, and confirmed:- The contact arrived at the meeting site, carrying a bundle of documents
- There was no indication of counterintelligence activity
These observations gave confidence to the GRU residency, and they used the agreed telephone to set up a new meeting, at a Soviet building. The building was chosen to give counterintelligence the least chance to stage a provocation, although that Serov later pointed out that if the Soviet building were under counterintelligence surveillance, the agent might become known, and neutralized or doubled.
In this case, the well-wisher brought valuable information and was paid for it. Further meetings produced more material, for which the agent was paid and gave receipts. GRU, however, continued to study the agent through multiple methods, and learned that the well-wisher was an unstable gambler motivated by money. While he was unreliable in meeting, his material was judged so valuable that the risks he presented were justified by the value of the material. "But in working with such a personality the officers of the residency should have been especially circumspect and careful to avoid the slightest mistake." In such a case, even though meeting at a Soviet location worked, it was bad tradecraft.
Soviet case study 4: Potential agent, with financial motivation, guarded success
A US walk-in showed the cover of a TOP SECRETClassified information
Classified information is sensitive information to which access is restricted by law or regulation to particular groups of persons. A formal security clearance is required to handle classified documents or access classified data. The clearance process requires a satisfactory background investigation...
to an overt officer, and the officer said he wanted to see the document, not the cover. The walk-in then produced the document and asked for $50, a small sum that the officer paid.
At a second meeting, at the same office, the GRU decided he was legitimate, and arranged much more secure contact and information transfer mechanisms, which produced valuable documents. Serov said the second meeting should never have been held at the same place, nor did the residency put the man under counter-surveillance to detect possible counterintelligence. Serov observed that counterintelligence might have sacrificed a document to gain credibility for the agent. Indeed, Serov does not mention the possibility that the document was indeed TOP SECRET, but of a highly technical matter that the US, in other documents, realized did not work, and could have caused the Soviets to waste much effort on a bad technique. While value was gained, risk was increased as well.

