
Browser Helper Object
Encyclopedia
Library (computer science)
In computer science, a library is a collection of resources used to develop software. These may include pre-written code and subroutines, classes, values or type specifications....
module designed as a plugin for Microsoft
Microsoft
Microsoft Corporation is an American public multinational corporation headquartered in Redmond, Washington, USA that develops, manufactures, licenses, and supports a wide range of products and services predominantly related to computing through its various product divisions...
's Internet Explorer
Internet Explorer
Windows Internet Explorer is a series of graphical web browsers developed by Microsoft and included as part of the Microsoft Windows line of operating systems, starting in 1995. It was first released as part of the add-on package Plus! for Windows 95 that year...
web browser
Web browser
A web browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web. An information resource is identified by a Uniform Resource Identifier and may be a web page, image, video, or other piece of content...
to provide added functionality. BHOs were introduced in October 1997 with the release of version 4
Internet Explorer 4
Microsoft Internet Explorer 4 is a graphical web browser released in September 1997 by Microsoft, primarily for Microsoft Windows, but also with versions available for Apple Mac OS, Solaris, and HP-UX and marketed as "The Web the Way You Want It".It was one of the main participants of the first...
of Internet Explorer. Most BHOs are loaded once by each new instance of Internet Explorer. However, in the case of Windows Explorer
Windows Explorer
This article is about the Windows file system browser. For the similarly named web browser, see Internet ExplorerWindows Explorer is a file manager application that is included with releases of the Microsoft Windows operating system from Windows 95 onwards. It provides a graphical user interface...
, a new instance is launched for each window.
Implementation
Each time a new instance of Internet Explorer starts, it checks the windows registryWindows registry
The Windows Registry is a hierarchical database that stores configuration settings and options on Microsoft Windows operating systems. It contains settings for low-level operating system components as well as the applications running on the platform: the kernel, device drivers, services, SAM, user...
for the following key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects
If Internet Explorer finds this key in the registry, it looks for a CLSID key listed below the key. The CLSID keys under Browser Helper Objects tell the browser which BHOs to load. Removing the registry key prevents the BHO from being loaded.
For each CLSID that is listed below the BHO key, Internet Explorer calls CoCreateInstance to start the instance of the BHO in the same process space as the browser. If the BHO is started and implements the IObjectWithSite interface, it can control and receive events from Internet Explorer. BHOs can be created in any language that supports COM
Component Object Model
Component Object Model is a binary-interface standard for software componentry introduced by Microsoft in 1993. It is used to enable interprocess communication and dynamic object creation in a large range of programming languages...
.
Examples of BHO
Some modules enable the display of different file formats not ordinarily interpretable by the browser. The Adobe AcrobatAdobe Acrobat
Adobe Acrobat is a family of application software developed by Adobe Systems to view, create, manipulate, print and manage files in Portable Document Format . All members of the family, except Adobe Reader , are commercial software, while the latter is available as freeware and can be downloaded...
plug-in that allows Internet Explorer users to read PDF
Portable Document Format
Portable Document Format is an open standard for document exchange. This file format, created by Adobe Systems in 1993, is used for representing documents in a manner independent of application software, hardware, and operating systems....
files within their browser is a BHO.
Other modules add toolbars to Internet Explorer, such as the Alexa Toolbar
Alexa Toolbar
The Alexa Toolbar, is an application produced by Alexa Internet, and is a Firefox extension and Browser Helper Object for Internet Explorer on Microsoft Windows that is used by Alexa to measure website specific statistics.-Content:...
that provides a list of web sites related to the one you are currently browsing, or the Google Toolbar
Google Toolbar
Google Toolbar is an Internet browser toolbar only available for Internet Explorer and Firefox .-Google Toolbar 1.0 December 11, 2000:New features:*Direct access to the Google search functionality from any web page*Web Site search...
that adds a toolbar with a Google search box to the browser user interface
User interface
The user interface, in the industrial design field of human–machine interaction, is the space where interaction between humans and machines occurs. The goal of interaction between a human and a machine at the user interface is effective operation and control of the machine, and feedback from the...
.
The Conduit toolbars are based on a BHO that can be used on Internet Explorer 7
Internet Explorer 7
Windows Internet Explorer 7 is a web browser released by Microsoft in October 2006. Internet Explorer 7 is part of a long line of versions of Internet Explorer and was the first major update to the browser in more than 5 years...
and up. This BHO provides a search facility that connects to Microsoft
Microsoft
Microsoft Corporation is an American public multinational corporation headquartered in Redmond, Washington, USA that develops, manufactures, licenses, and supports a wide range of products and services predominantly related to computing through its various product divisions...
's Bing
Bing
Bing is a web search engine from Microsoft.Bing may also refer to:* An onomatopœia of a bell sound* Bing cherry, a variety of cherry* Bing , Chinese flatbread* Bing , a German company that manufactured toys and kitchen utensils...
search. However, security firm Sophos
Sophos
Sophos is a developer and vendor of security software and hardware, including anti-virus, anti-spyware, anti-spam, network access control, encryption software and data loss prevention for desktops, servers, email systems and other network gateways....
is of the opinion that this BHO is malware
Malware
Malware, short for malicious software, consists of programming that is designed to disrupt or deny operation, gather information that leads to loss of privacy or exploitation, or gain unauthorized access to system resources, or that otherwise exhibits abusive behavior...
that connects to malware-infected Internet content.
Concerns
The BHO APIApplication programming interface
An application programming interface is a source code based specification intended to be used as an interface by software components to communicate with each other...
exposes hook
Hooking
In computer programming, the term hooking covers a range of techniques used to alter or augment the behavior of an operating system, of applications, or of other software components by intercepting function calls or messages or events passed between software components...
s that allow the BHO to access the Document Object Model
Document Object Model
The Document Object Model is a cross-platform and language-independent convention for representing and interacting with objects in HTML, XHTML and XML documents. Aspects of the DOM may be addressed and manipulated within the syntax of the programming language in use...
(DOM) of the current page and to control navigation. Because BHOs have unrestricted access to the Internet Explorer event model, some forms of malware
Malware
Malware, short for malicious software, consists of programming that is designed to disrupt or deny operation, gather information that leads to loss of privacy or exploitation, or gain unauthorized access to system resources, or that otherwise exhibits abusive behavior...
have also been created as BHOs. For example, the Download.ject
Download.ject
In computing, Download.ject is a malware program for Microsoft Windows servers. When installed on an insecure website running on Microsoft Internet Information Services , it appends malicious JavaScript to all pages served by the site.Download.ject was the first noted case in which users of...
malware installs a BHO that would activate upon detecting a secure HTTP connection to a financial institution, record the user's keystrokes
Keystroke logging
Keystroke logging is the action of tracking the keys struck on a keyboard, typically in a covert manner so that the person using the keyboard is unaware that their actions are being monitored...
(intending to capture passwords) and transmit the information to a website used by Russian computer criminals
Computer crime
Computer crime, or cybercrime, refers to any crime that involves a computer and a network. The computer may have been used in the commission of a crime, or it may be the target. Netcrime refers to criminal exploitation of the Internet. Such crimes may threaten a nation’s security and financial health...
. Other BHOs such as the MyWay Searchbar
MyWay Searchbar
The MyWay Searchbar, also known as the MyWay Speedbar, MyWay Search Assistant, MyWebSearch, MyAllSearch, and MyWeb Searchbar, is adware or toolbar program that replaces an Internet browser's default search engine with MyWay's website...
track users' browsing patterns and pass the information they record to third parties.
Many BHOs introduce visible changes to a browser's interface, such as installing toolbars in Internet Explorer and the like, but others run without any change to the interface. This renders it easy for malicious coders to conceal the actions of their browser add-on, especially since, after being installed, the BHO seldom requires permission before performing further actions. For instance, variants of the ClSpring trojan use BHOs to install scripts to provide a number of instructions to be performed such as adding and deleting registry values and downloading additional executable files, all completely transparently to the user. The DyFuCA spyware even replaces Internet Explorer's general error page with an ad page.
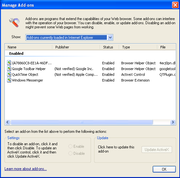
In response to the problems associated with BHOs and similar extensions to Internet Explorer, Microsoft debuted an Add-on Manager in Internet Explorer 6
Internet Explorer 6
Internet Explorer 6 is the sixth major revision of Internet Explorer, a web browser developed by Microsoft for Windows operating systems...
with the release of Service Pack 2 for Windows XP
Windows XP
Windows XP is an operating system produced by Microsoft for use on personal computers, including home and business desktops, laptops and media centers. First released to computer manufacturers on August 24, 2001, it is the second most popular version of Windows, based on installed user base...
(updating it to IE6 Security Version 1, a.k.a. SP2). This utility displays a list of all installed BHOs, browser extension
Browser extension
A browser extension is a computer program that extends the functionality of a web browser in some way. Depending on the browser and the version, the term may be distinct from similar terms such as plug-in or add-on. Mozilla Firefox was designed with the idea of being a small and simple web browser,...
s and ActiveX controls, and allows the user to enable or disable them at will. There are also free tools (such as BHODemon) that list installed BHOs and allow the user to disable malicious extensions. Spybot S&D advanced mode has a similar tool built in to allow the user to disable installed BHOs. Many anti-spyware applications also offer the capability to block the download or install of BHOs identified as malicious.
In IE9 Beta, BHOs and toolbars are not loaded when a link pinned to the taskbar is accessed.
Microsoft sites
- IEHelper-Attaching to Internet Explorer 4.0 by Using a Browser Helper Object
- Control Internet Explorer Add-ons with Add-on Manager - an article on Microsoft.com that explains this new feature of Windows XP Service Pack 2
- Building Browser Helper Objects with Visual Studio 2005 - an October 2006 MSDN article by Tony Schreiner and John Sudds
Listings and examples
- CLSID List - master list created by Tony Klein and others, that attempts to record and identify every BHO available (previously located at - the now defunct - castlecops.comCastleCopsCastleCops was a volunteer security community focused on making the Internet a safer place. All services to the public were free, including malware and rootkit cleanup of infected computers, malware and phish investigations and terminations, and searchable database lists of malware and file hashes...
) - C++ example code for a BHO
- C# example code for a BHO
- PestPatrol - has listings and classifications of BHOs (NOTE: page hasn't been updated since April 7, 2005!)

